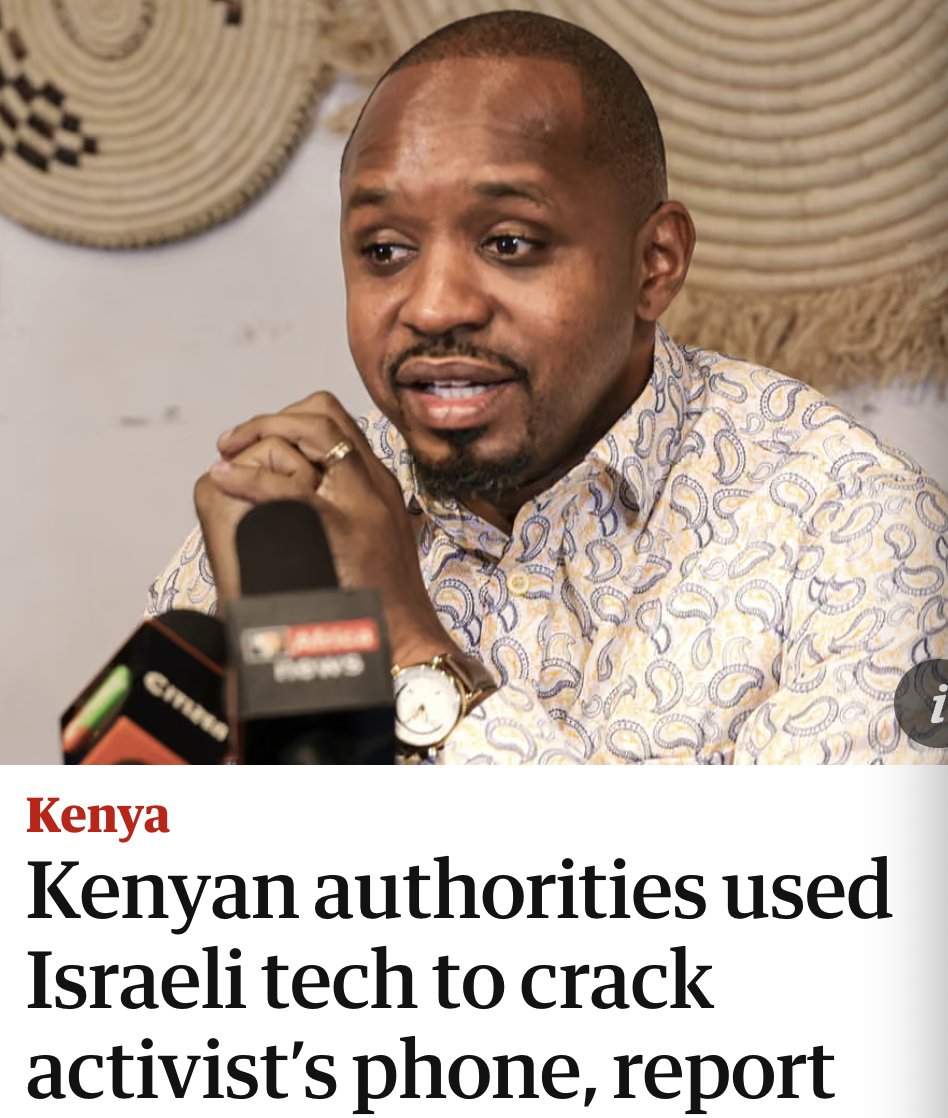
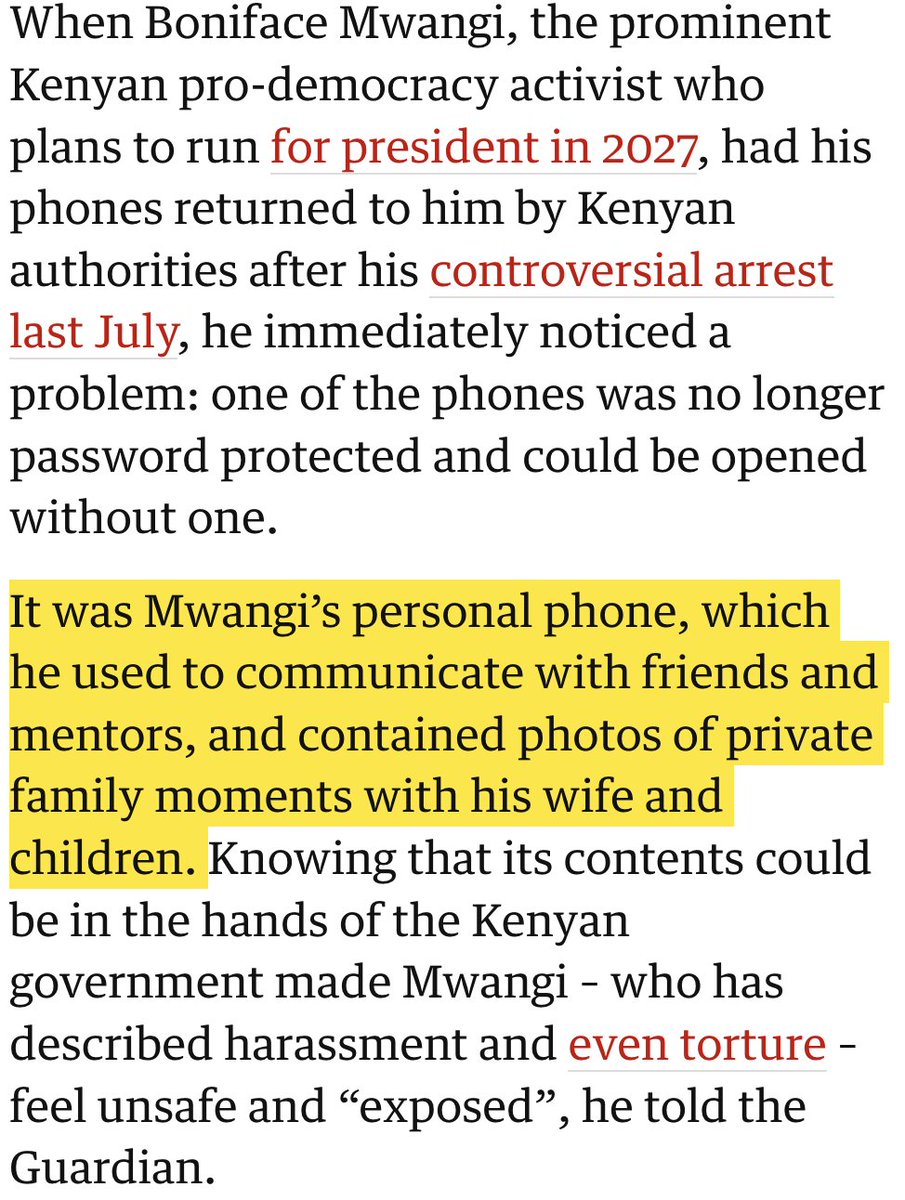
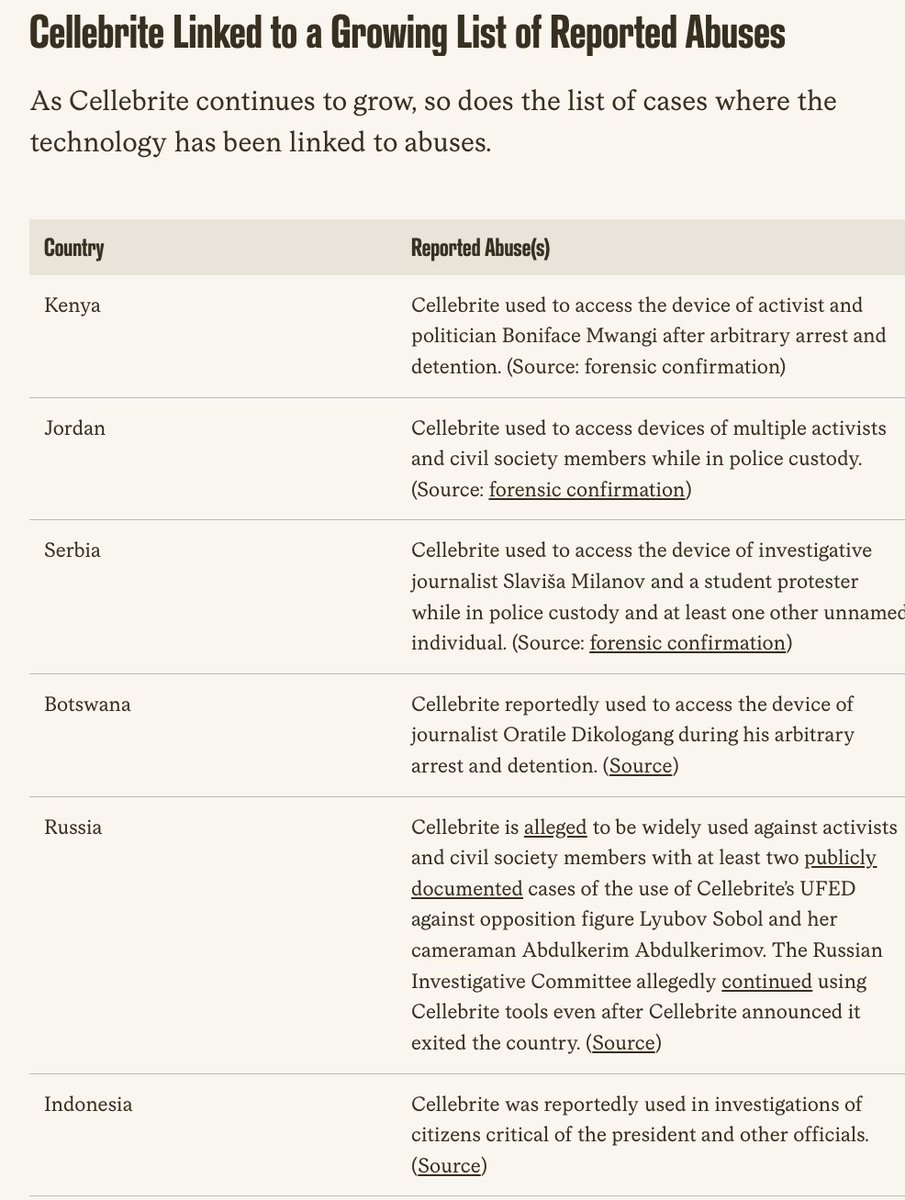
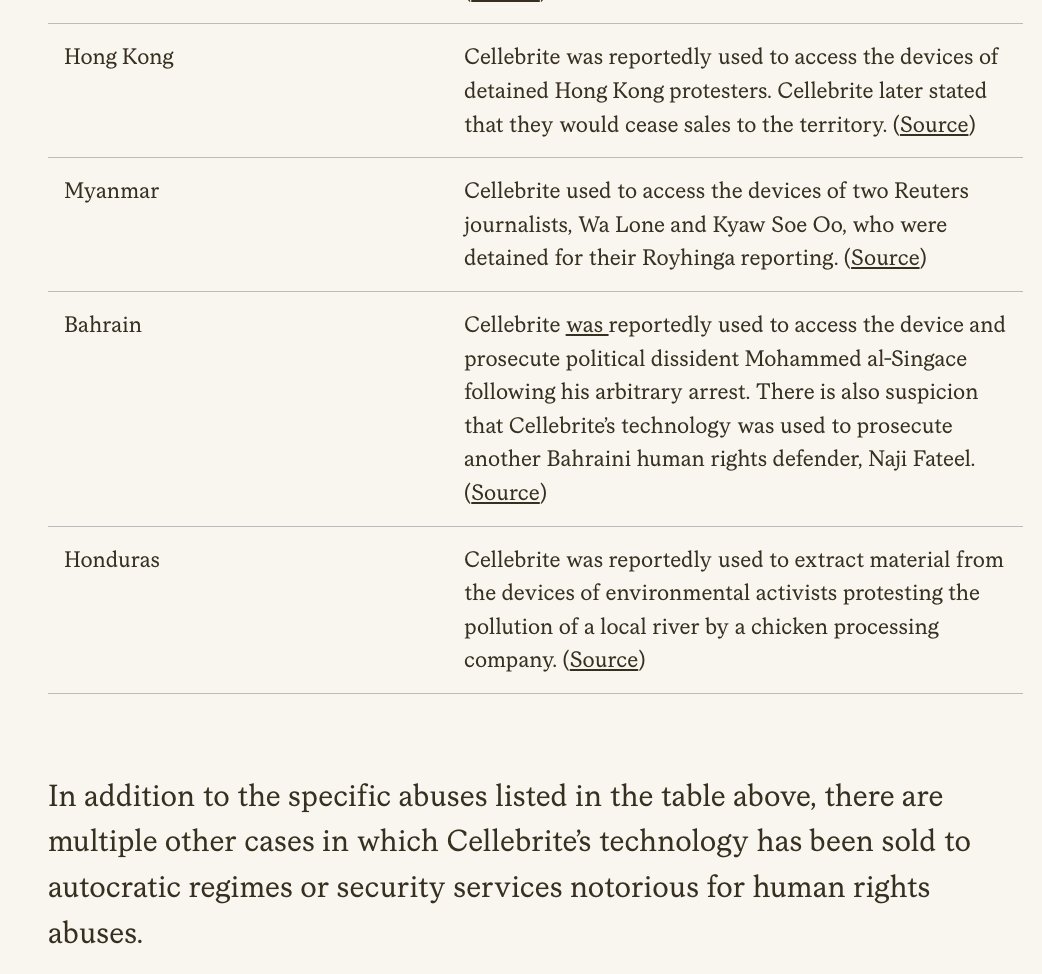
What's happening at the #Titanic site will likely be a tragedy.
@OceanGate's page on why they didn't seek certifications / classing for the Titan submersible & that design safety regulations are slow & constrain innovation... reads differently now.
oceangate.com/news-and-media…


@OceanGate's page on why they didn't seek certifications / classing for the Titan submersible & that design safety regulations are slow & constrain innovation... reads differently now.
oceangate.com/news-and-media…



Imagine if a car manufacturer told you: this car isn't crash certified because it won't prevent people from driving the car badly. 

"No other submersible currently utilizes real-time monitoring...we want to know why"
Hubris from @OceanGate even as they dismiss the existing standards derived from many tragedies that came before.
Hubris from @OceanGate even as they dismiss the existing standards derived from many tragedies that came before.

There's a nuanced, necessary risk balancing whenever you push at edges.
Innovation is hard if you over-constrain yourself to old rules... but scrap them all & you should expect to experience some irreversible lessons.
Nowhere more so than in the sea's unforgiving depths.
Innovation is hard if you over-constrain yourself to old rules... but scrap them all & you should expect to experience some irreversible lessons.
Nowhere more so than in the sea's unforgiving depths.
Exploration & adventure have unavoidable risks.
This is fine.
But I sincerely hope that the souls on that submersible truly understood them, and that @OceanGate objectively explained them *without* being colored by the kind of rhetoric found on their website.
This is fine.
But I sincerely hope that the souls on that submersible truly understood them, and that @OceanGate objectively explained them *without* being colored by the kind of rhetoric found on their website.
"if you are lost so are we"
Comms failed & the #OceanGate submersible was lost for several hours on an earlier #Titanic dive.
Comms failed & the #OceanGate submersible was lost for several hours on an earlier #Titanic dive.
The dark irony of what is unfolding is not lost on maritime historians
https://twitter.com/mercoglianos/status/1671132143513223168
Those familiar w/marine environments will find the consumer grade electronics beyond puzzling.
Salt water, condensation, humidity, etc. are kryptonite to electronics.
And exactly the kinds of things you'd find in a submersible diving into cold places.



Salt water, condensation, humidity, etc. are kryptonite to electronics.
And exactly the kinds of things you'd find in a submersible diving into cold places.




Thinking on @mercoglianos' point that the #Titanic is what got us the first convention on Safety of Life at Sea aka #SOLAS.
It continues to save uncountable lives.
101 years later & an outcome we can hope for is a fresh focus on safety regs for subsurface adventure tourism.



It continues to save uncountable lives.
101 years later & an outcome we can hope for is a fresh focus on safety regs for subsurface adventure tourism.




While the game controller (CEO said they had spares) is something we can all understand...
I think it's important to think of it as a indicator of the overall risk management & minimum-viable-submersible philosophy that seems to have been at work all over.
Pics: ballast.
I think it's important to think of it as a indicator of the overall risk management & minimum-viable-submersible philosophy that seems to have been at work all over.
Pics: ballast.

"#OceanGate offers you the the once-in-a-lifetime opportunity ...[of] SAFELY diving to the Titanic wreckage site"
The breathless 2023 #Titanic dive promotional video puts safety in the first sentence.
The breathless 2023 #Titanic dive promotional video puts safety in the first sentence.
UPDATE: an #OceanGate employee was allegedly fired for refusing to greenlight manned tests over safety concerns.
The details look quite ominous.
By @DanielStrauss4 h/t @ThatVDOVault
newrepublic.com/post/173802/mi…



The details look quite ominous.
By @DanielStrauss4 h/t @ThatVDOVault
newrepublic.com/post/173802/mi…




"the current 'experimental' approach... could result in negative outcomes (from minor to catastrophic) that would have serious consequences for everyone in the industry"
Unanimous letter of concern from @MTSociety to the #OceanGate CEO.
Via @nytimes
int.nyt.com/data/documentt…
Unanimous letter of concern from @MTSociety to the #OceanGate CEO.
Via @nytimes
int.nyt.com/data/documentt…

Correction: these are drop weights.
https://twitter.com/jsrailton/status/1671238383815753731
• • •
Missing some Tweet in this thread? You can try to
force a refresh