Safely investigating a ransomware hosting site using Censys and GrabbrApp 😄
I'll show how to confirm that a "clean" IP was hosting ransomware. You'll also get to see some cool hunting queries and methods for safely downloading malware files.
Thread 👇
[1/12]
#Censys #malware




I'll show how to confirm that a "clean" IP was hosting ransomware. You'll also get to see some cool hunting queries and methods for safely downloading malware files.
Thread 👇
[1/12]
#Censys #malware




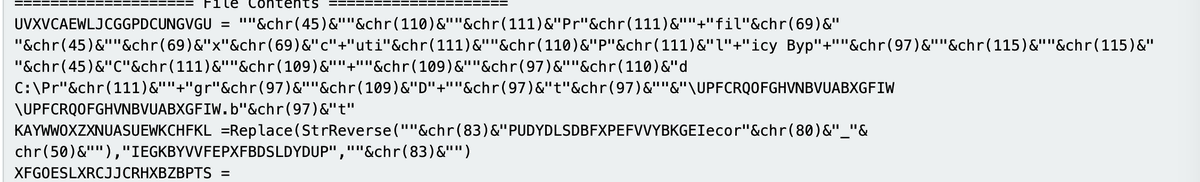
[2/] I started with some @censysio queries that I've previously published on my site.
The query in this case was looking for #powershell scripts contained in #python based open directories. https://t.co/cMwbV3YGShembee-research.ghost.io/shodan-censys-…

The query in this case was looking for #powershell scripts contained in #python based open directories. https://t.co/cMwbV3YGShembee-research.ghost.io/shodan-censys-…

[3/] This query returned 26 results. One of which was based out of Shanghai, China.
180.166.220[.]180
This IP had 0 VT detections as of 11/07/23.
As well as a highly suspicious open directory containing "darkside.bin" and "shell.ps1"
https://t.co/4GlRK6zOrbvirustotal.com/gui/ip-address…


180.166.220[.]180
This IP had 0 VT detections as of 11/07/23.
As well as a highly suspicious open directory containing "darkside.bin" and "shell.ps1"
https://t.co/4GlRK6zOrbvirustotal.com/gui/ip-address…


[4/] The "Darkside.bin" file was interesting and I wanted to obtain a sample.
Typically I would do this with #Powershell (iwr) and a method I've demonstrated on my blog.
Today I'll show a safer and "cleaner" method using @GrabbrAppIO .
(Blog) https://t.co/G5dzsgNhkAembee-research.ghost.io/smokeloader-an…


Typically I would do this with #Powershell (iwr) and a method I've demonstrated on my blog.
Today I'll show a safer and "cleaner" method using @GrabbrAppIO .
(Blog) https://t.co/G5dzsgNhkAembee-research.ghost.io/smokeloader-an…


[5/] My previous powershell method works ok, but it requires interaction with the IP and a "safe" VM/VPN which is not always available.
So I decided to try @GrabbrAppIO by @valhalla_dev.
This tool was designed for the exact purpose of safely retrieving suspicious files.
So I decided to try @GrabbrAppIO by @valhalla_dev.
This tool was designed for the exact purpose of safely retrieving suspicious files.
[6/] I signed up for GrabbrApp (there's a free option) and input the complete url for "darkside.bin".
You can try that here.
https://t.co/ep9iK8MowLgrabbrapp.io

You can try that here.
https://t.co/ep9iK8MowLgrabbrapp.io

[7/] GrabbrApp was able to retrieve the file and presented both a hash and link for safe download.
Checking the SHA256 hash in Virustotal immediately confirmed Darkside ransomware.
(No need to directly interact with the IP or ransomware file)
https://t.co/j7BDr20IvNvirustotal.com/gui/file/151fb…


Checking the SHA256 hash in Virustotal immediately confirmed Darkside ransomware.
(No need to directly interact with the IP or ransomware file)
https://t.co/j7BDr20IvNvirustotal.com/gui/file/151fb…


[8/] There were numerous other files contained in the same open directory.
I was able to safely obtain the remaining files using the same method detailed above.



I was able to safely obtain the remaining files using the same method detailed above.



[9/] There were some cases where the hash was not available on #Virustotal and a manual download was required to investigate.
I was able to do this using GrabbrApp which also has the ability to save a suspicious file.


I was able to do this using GrabbrApp which also has the ability to save a suspicious file.


[10] I'll leave the analysis there as I just wanted to show the tool.
There are likely dozens more files across the remaining 25 results in the @censysio search. As well as the searches in the blog post.
I hope people have some fun and see what they can find😁
There are likely dozens more files across the remaining 25 results in the @censysio search. As well as the searches in the blog post.
I hope people have some fun and see what they can find😁
[11] I've been following @valhalla_dev for a while now and I genuinely think GrabbrApp is a product that I will personally be using.
I can see this saving me a lot of time and effort when doing personal research, particularly malware downloaders and confirming Censys queries.
I can see this saving me a lot of time and effort when doing personal research, particularly malware downloaders and confirming Censys queries.
[12/] There are likely other use cases I haven't encountered yet, and I'll try and share some more as I learn.
For now, here's some links to the queries and tools used.
GrabbrApp:
Queries: https://t.co/t67NIUPWWT
Cont'd....grabbrapp.io
embee-research.ghost.io/shodan-censys-…
For now, here's some links to the queries and tools used.
GrabbrApp:
Queries: https://t.co/t67NIUPWWT
Cont'd....grabbrapp.io
embee-research.ghost.io/shodan-censys-…
[12.1/12]
Censys Search:
VT: https://t.co/zzTrScDmRvsearch.censys.io/search?resourc…
virustotal.com/gui/ip-address…
Censys Search:
VT: https://t.co/zzTrScDmRvsearch.censys.io/search?resourc…
virustotal.com/gui/ip-address…
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter