
Smart Contract Audit | Security Monitoring | AML/CFT (KYA/KYT) | Crypto Investigation | @Phalcon_xyz @MetaSleuth @MetaDockTeam 👉TG: https://t.co/owokTLanv5
How to get URL link on X (Twitter) App



 2/
2/ 
https://twitter.com/punk3155/status/1642771856758546434
 2/ The attacker is a validator with a pre-knowledge that he/she will be selected to be the miner of block 16964664. Besides, a vulnerability in the mev-boost-relay will reveal the private transaction in flashbots.
2/ The attacker is a validator with a pre-knowledge that he/she will be selected to be the miner of block 16964664. Besides, a vulnerability in the mev-boost-relay will reveal the private transaction in flashbots.

https://twitter.com/BlockSecTeam/status/1635204706703384577
 2/ Here is the key steps
2/ Here is the key steps

https://twitter.com/MetaSleuth/status/1628310811579150337

 2/ Specifically, users could deposit $DYNA and claim rewards, while the interest will be calculated as follows:
2/ Specifically, users could deposit $DYNA and claim rewards, while the interest will be calculated as follows: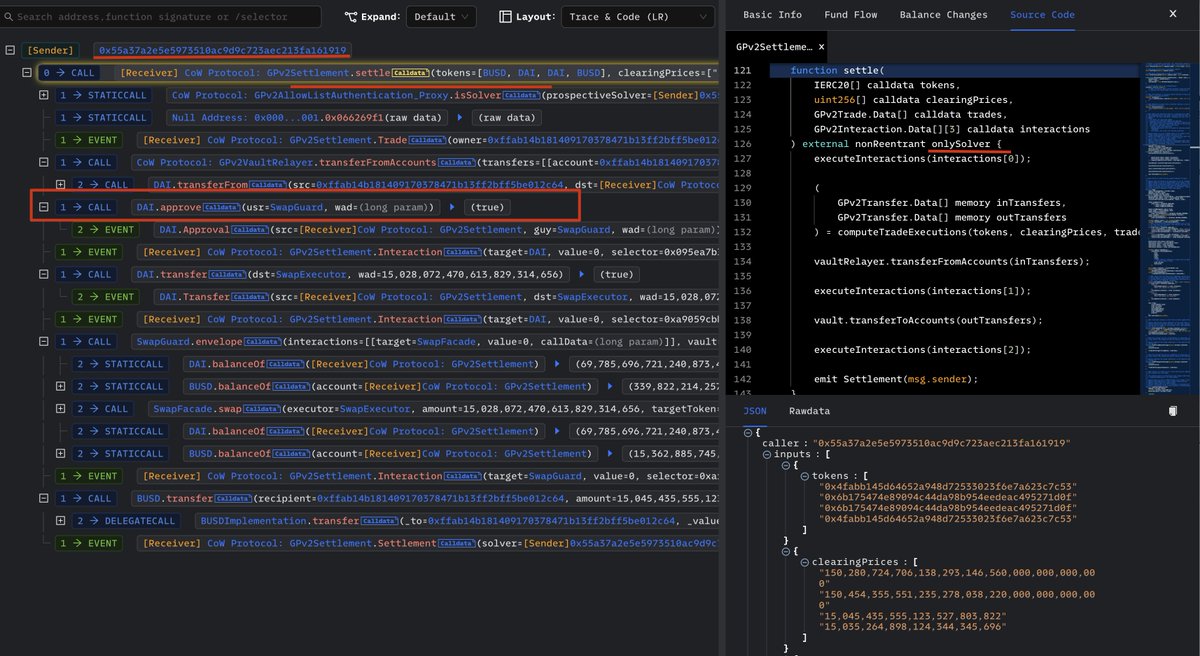
 2/ Since DAI was approved from GPv2Settlement to SwapGuard, then the attacker can ask SwapGuard to transfer DAI from GPv2Settlement to arbitrary addresses.
2/ Since DAI was approved from GPv2Settlement to SwapGuard, then the attacker can ask SwapGuard to transfer DAI from GPv2Settlement to arbitrary addresses.

 2/ Specifically, the reward is calculated by the _Check_reward function according to the deposit duration and amount. However, the duration is derived from the input parameter end_date, whose value is not checked.
2/ Specifically, the reward is calculated by the _Check_reward function according to the deposit duration and amount. However, the duration is derived from the input parameter end_date, whose value is not checked. 


 2/ The attacker repeatedly invoked the skim() function to increase the balance of the pair. Finally, the attacker swapped back WBNB. There are two attacks:
2/ The attacker repeatedly invoked the skim() function to increase the balance of the pair. Finally, the attacker swapped back WBNB. There are two attacks:



 2/ Note that the price of the JAY token is the Ether balance of the JAY contract, divided by the total supply of the JAY token; the JAY contract allows the users to pass arbitrary ERC-721 tokens for the buyJay function.
2/ Note that the price of the JAY token is the Ether balance of the JAY contract, divided by the total supply of the JAY token; the JAY contract allows the users to pass arbitrary ERC-721 tokens for the buyJay function. 








 2/ The exchange contract uses two accounting systems. For addLiquidity, it uses the internal accounting system; while for removeLiquidity, it calculates the tokens to return with the token-balance-based accounting system and reduces the internal accounting reserves.
2/ The exchange contract uses two accounting systems. For addLiquidity, it uses the internal accounting system; while for removeLiquidity, it calculates the tokens to return with the token-balance-based accounting system and reduces the internal accounting reserves. 


 2/ Specifically, the attacker burrowed 8000 BUSD and swapped into AES. After that, the attacker sends the AES to the BNB-AES pool and invokes the skim function repeatedly. In this process, the balance of pool is burned and the swapfee in the AES contract increased.
2/ Specifically, the attacker burrowed 8000 BUSD and swapped into AES. After that, the attacker sends the AES to the BNB-AES pool and invokes the skim function repeatedly. In this process, the balance of pool is burned and the swapfee in the AES contract increased.



 2/ The root cause is in function redeem_skyward (github.com/skyward-financ…), which is used to redeem the treasury from the protocol.
2/ The root cause is in function redeem_skyward (github.com/skyward-financ…), which is used to redeem the treasury from the protocol.

 2/ Rustle can help to locate tens of different vulnerabilities in #NEAR smart contract. We hope Rustle can help to increase the security of the whole #NEAR ecosystem.
2/ Rustle can help to locate tens of different vulnerabilities in #NEAR smart contract. We hope Rustle can help to increase the security of the whole #NEAR ecosystem.


 2/ The attack contract (varg1) forges the function 0x95b81c68, hardcoded in the vulnerable contract. As this contract trusts the value returned by the function 0x95b81c68, it uses this value as the transfer amount to send ~100,499,018 UVTs to the hacker.
2/ The attack contract (varg1) forges the function 0x95b81c68, hardcoded in the vulnerable contract. As this contract trusts the value returned by the function 0x95b81c68, it uses this value as the transfer amount to send ~100,499,018 UVTs to the hacker. 

https://twitter.com/samczsun/status/1578167198203289600).
 2/ Cross-chain bridges usually involve multiple parties in their implementation, including the contracts on both source and target chains and the relays (validators) sitting in the middle. Any vulnerability in either party can cause huge financial loss.
2/ Cross-chain bridges usually involve multiple parties in their implementation, including the contracts on both source and target chains and the relays (validators) sitting in the middle. Any vulnerability in either party can cause huge financial loss. 