
#SocialEngineering, #Psychology, #HUMINT & #OSINT intertwined for the sake of security. Exec Board @OSINTCurious
How to get URL link on X (Twitter) App



 "A basic finding of cognitive psychology is that people have no conscious experience of most of what happens in the human mind. Many functions associated with perception ,memory and information processing are conducted prior to and independently of any conscious direction."
"A basic finding of cognitive psychology is that people have no conscious experience of most of what happens in the human mind. Many functions associated with perception ,memory and information processing are conducted prior to and independently of any conscious direction."


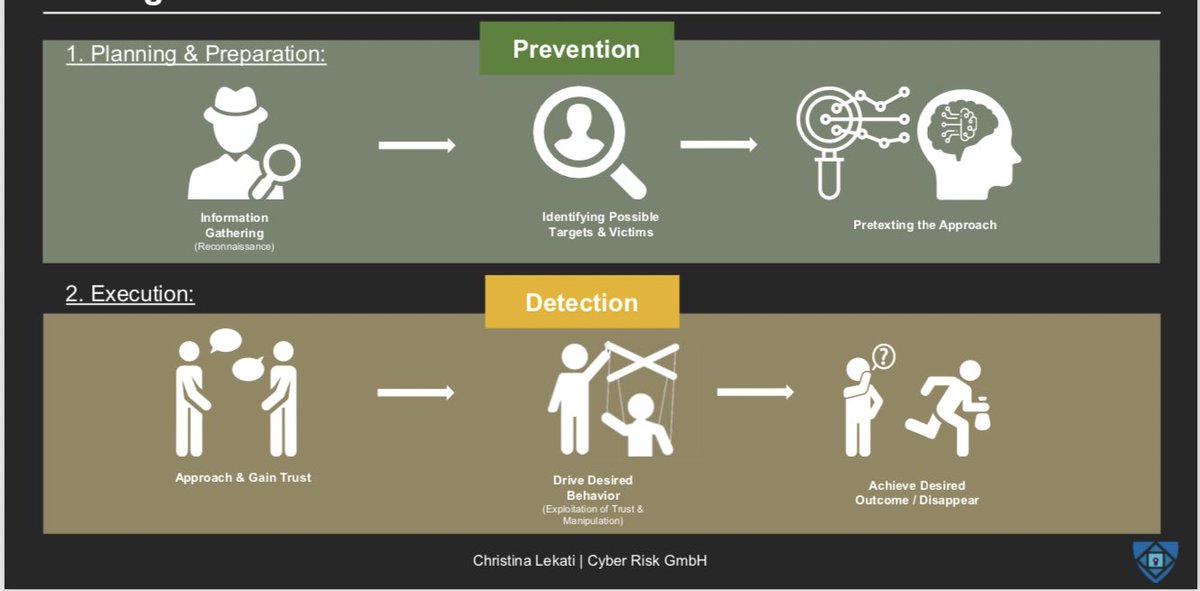
 Phase 1:
Phase 1: