
CODE RED Computerized Elections and The War on American Democracy https://t.co/0vhXxVJOVQ Transparent elections, hand-counted, hand-marked paper ballots.
How to get URL link on X (Twitter) App


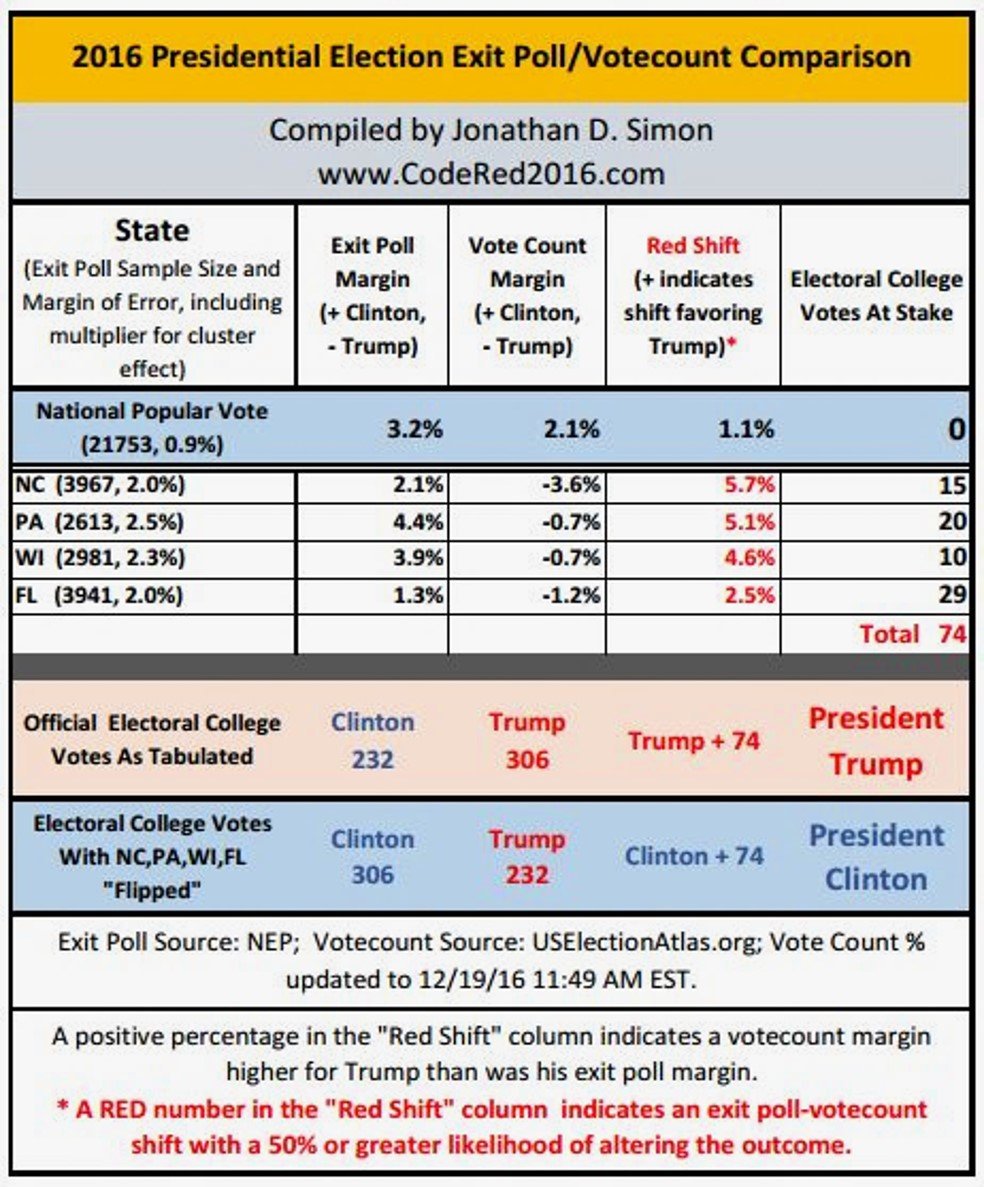
https://twitter.com/APFactCheck/status/1521592563937038336Now add to all that this little chart: 2/




https://twitter.com/dperry913/status/1175638670524735488That recognition should bring both empathy and humility. We have a right to be proud of our Constitution and diligent efforts to tame the Hobbesian beast. But we also would do well to acknowledge our many failures in that endeavor and many cruelties and injustices along the way.
https://twitter.com/AnalyticsEqv/status/1172111163007655936That said, exit polls are certainly not perfect - there's quite a bit of art (the stratification algorithm, e.g.) to go with the science. But when we observe certain pervasive patterns (e.g., accurate for noncompetitive/nonsuspect races, red shift for competitive/suspect)...2/

https://twitter.com/threadreaderapp/status/1167111558671077376Like, for example, seizing on a touchscreen "crisis" to push "paper," while KNOWING that the computerized devices that will mark that paper for the voter are just another open invitation to rig. And like promoting the useless SEA act in place of the effective SAFE act. 2/
https://twitter.com/kmlibra/status/1162022623041265664Butting heads with ES&S and the Kemps of the world over this or that detail isn't going to get that done. It is necessary but not sufficient. We need a huge surge in public awareness and alarm - and a MINDSET SEA CHANGE. Stop expecting it to be done FOR us. Get in there and do!

https://twitter.com/droskill/status/1154536324814295042
 For those wondering why the time stamp is critical, these polls are "adjusted" towards congruence with the votecounts in the minutes and hours after poll closing, as those votecounts become available. So only first postings are (relatively) uncontaminated. 2/
For those wondering why the time stamp is critical, these polls are "adjusted" towards congruence with the votecounts in the minutes and hours after poll closing, as those votecounts become available. So only first postings are (relatively) uncontaminated. 2/
https://twitter.com/DenbrotS/status/1145836577412800512Votes should be CAST in private and COUNTED in public - observably. It's really that simple. Instead, our computerized voting and counting system is DESIGNED FOR CONCEALMENT. 2/
https://twitter.com/jpanzer/status/1144259029235044353Here's how it goes: 1) You take control of the voting equipment industry; 2) You exploit (or manufacture) a crisis in vote-counting (2000) to get virtually all votes counted on the computers you produce & program going forward; 3) You exploit that control to rig key elections; 2/