
CTO at @ledger. Busy securing the blockchain revolution. Cryptography, (Hw) Security, Tech, Blockchain.
Previously built the Donjon (@DonjonLedger)
How to get URL link on X (Twitter) App


 🔹The exploit uses what’s called a “tearing attack”, where cutting the power stops the Tangem card from recording a failed password attempt.
🔹The exploit uses what’s called a “tearing attack”, where cutting the power stops the Tangem card from recording a failed password attempt.
 Launched in 2016, the Ledger Nano S helped define self-custody when BTC was just for HODLing. But nearly a decade later, as crypto and its use cases evolve, so must the hardware that secures it, so we’ve updated our products to meet today’s needs.
Launched in 2016, the Ledger Nano S helped define self-custody when BTC was just for HODLing. But nearly a decade later, as crypto and its use cases evolve, so must the hardware that secures it, so we’ve updated our products to meet today’s needs.

 Our North Star remains the same: security first.
Our North Star remains the same: security first.
 Our Ledger Donjon security research revealed that if a Trezor Safe3 device was stolen, an attacker could theoretically tamper with the device and modify the software running on it, endangering its user’s funds, even if this device uses a Secure Element.
Our Ledger Donjon security research revealed that if a Trezor Safe3 device was stolen, an attacker could theoretically tamper with the device and modify the software running on it, endangering its user’s funds, even if this device uses a Secure Element.



 As you might know, your Ledger devices use a smartcard chip (a Secure Element), implementing tons of hardware countermeasures enabling resistance against high potential attackers even with physical access.
As you might know, your Ledger devices use a smartcard chip (a Secure Element), implementing tons of hardware countermeasures enabling resistance against high potential attackers even with physical access.

 Asymmetric cryptography is a process that uses a pair of keys: public / private key.
Asymmetric cryptography is a process that uses a pair of keys: public / private key.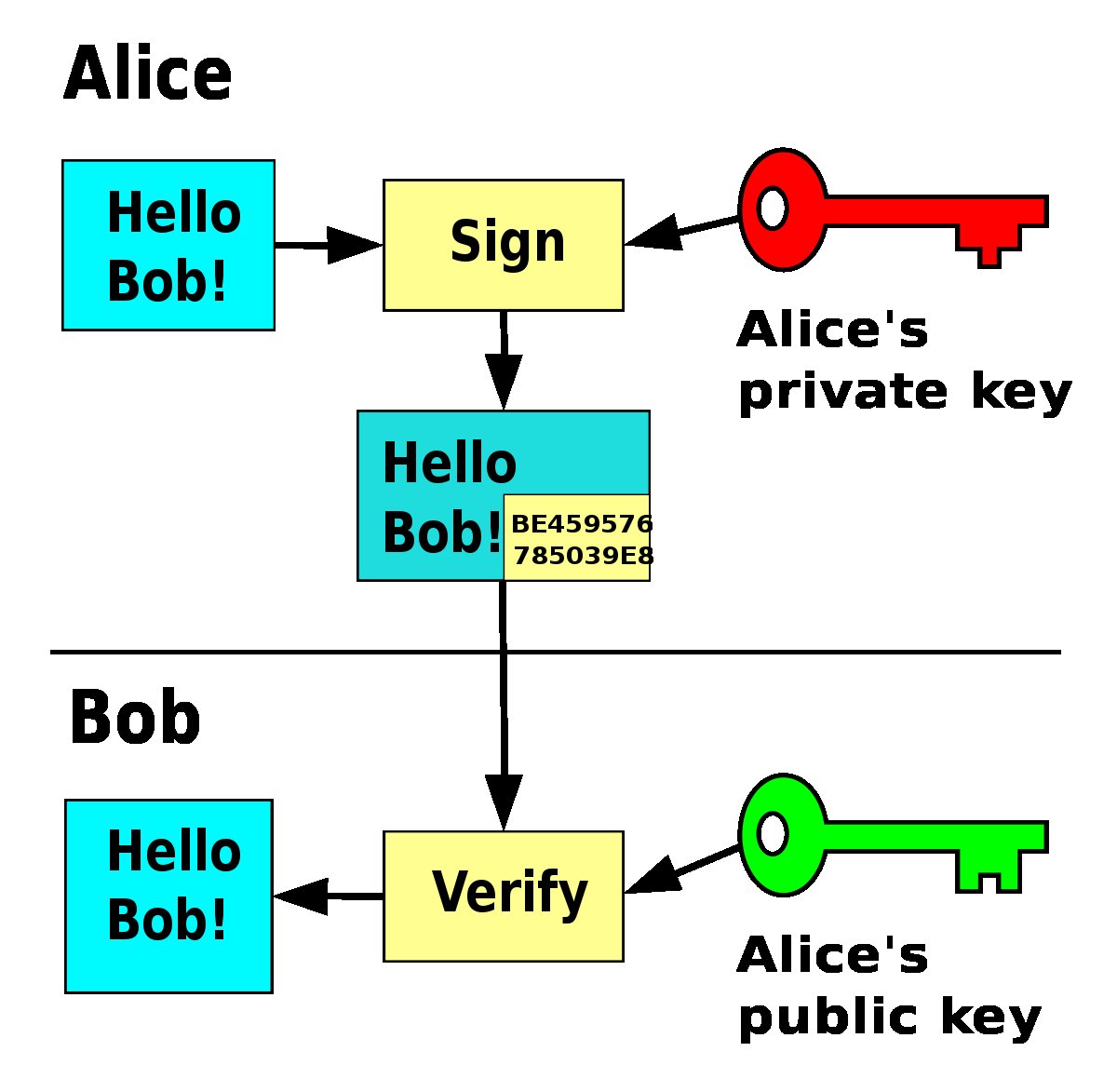

 Ledger Nano devices threat model is quite simple and could be summarized as follows:
Ledger Nano devices threat model is quite simple and could be summarized as follows:
 PLATYPUS is a Side Channel Attack allowing to _remotely_ extract secrets from Intel CPU incl. SGX enclave and AES-NI.
PLATYPUS is a Side Channel Attack allowing to _remotely_ extract secrets from Intel CPU incl. SGX enclave and AES-NI. 