
American Mobile, IoT & Crypto Researcher (Malware/Spyware/Forensics) Founder @TheMiladGroup, Doctoral Student - Comp Sci - Digital Espionage
How to get URL link on X (Twitter) App


 2/
2/ 
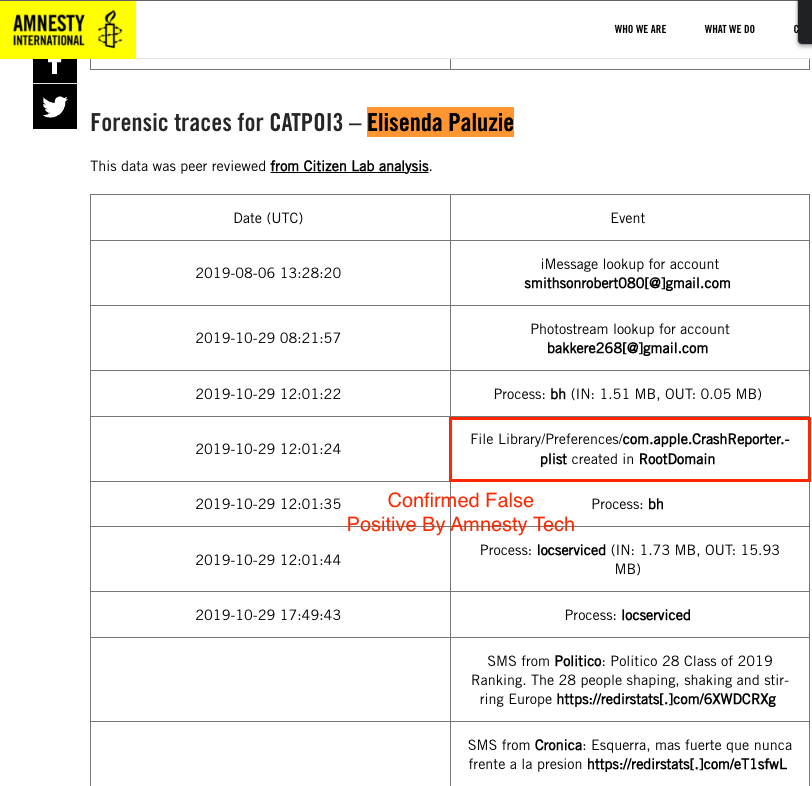
 Meritxell Bonet - Also said to be infected with Pegasus has a false positive result in the Amnesty Tech validation report
Meritxell Bonet - Also said to be infected with Pegasus has a false positive result in the Amnesty Tech validation report 

 (2/4)
(2/4)
https://twitter.com/jonathandata1/status/1520303364759822337?s=20&t=K2XVDZ7pbFCc16JSDDTnFQWhen I brought this to the attention of the world, The radical Citizen Lab supporters started to come out from everywhere and attack me to no end.

https://twitter.com/runasand/status/1566747856261861378Journalist

 It’s shameful to see “prominent” #infosec pros engaged in active harassment, bullying, promotion of defamation, and openly plotting to engage in smear campaigns. Infosec is a modality people dream about joining…but many people have publicly said they now fear it because of 👆
It’s shameful to see “prominent” #infosec pros engaged in active harassment, bullying, promotion of defamation, and openly plotting to engage in smear campaigns. Infosec is a modality people dream about joining…but many people have publicly said they now fear it because of 👆