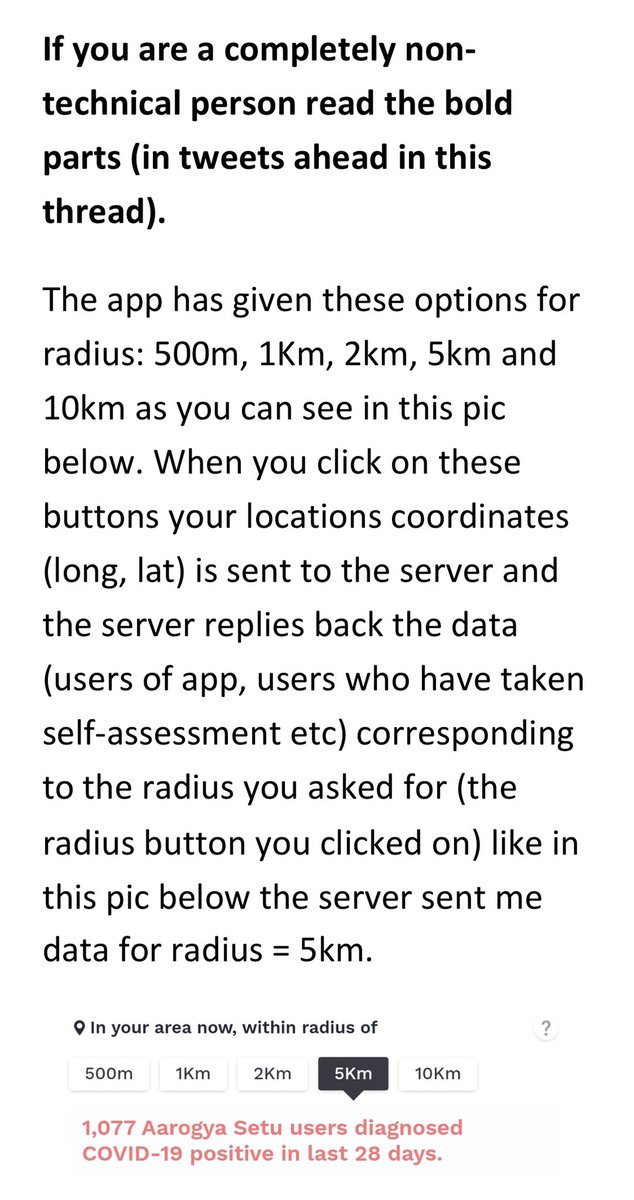
Founder @SecureYourHacks | Ethical Hacker | Trainer | Malware Analyst | R&D on Security Breaches || Digital Forensics | CyberSecurity | Blockchain | OSINT | AI
How to get URL link on X (Twitter) App




 2/ Same is with N470SC no. plane.
2/ Same is with N470SC no. plane.



 2) First thing you need to understand is when you do OSINT you have to find as exact coordinates as possible, and especially cross-check the assumed or found coordinates with several objects in photos/videos, and try the same from different angles.
2) First thing you need to understand is when you do OSINT you have to find as exact coordinates as possible, and especially cross-check the assumed or found coordinates with several objects in photos/videos, and try the same from different angles.
 2/ I mean why does one need a feature in their app’s code that is not intended to be used.
2/ I mean why does one need a feature in their app’s code that is not intended to be used.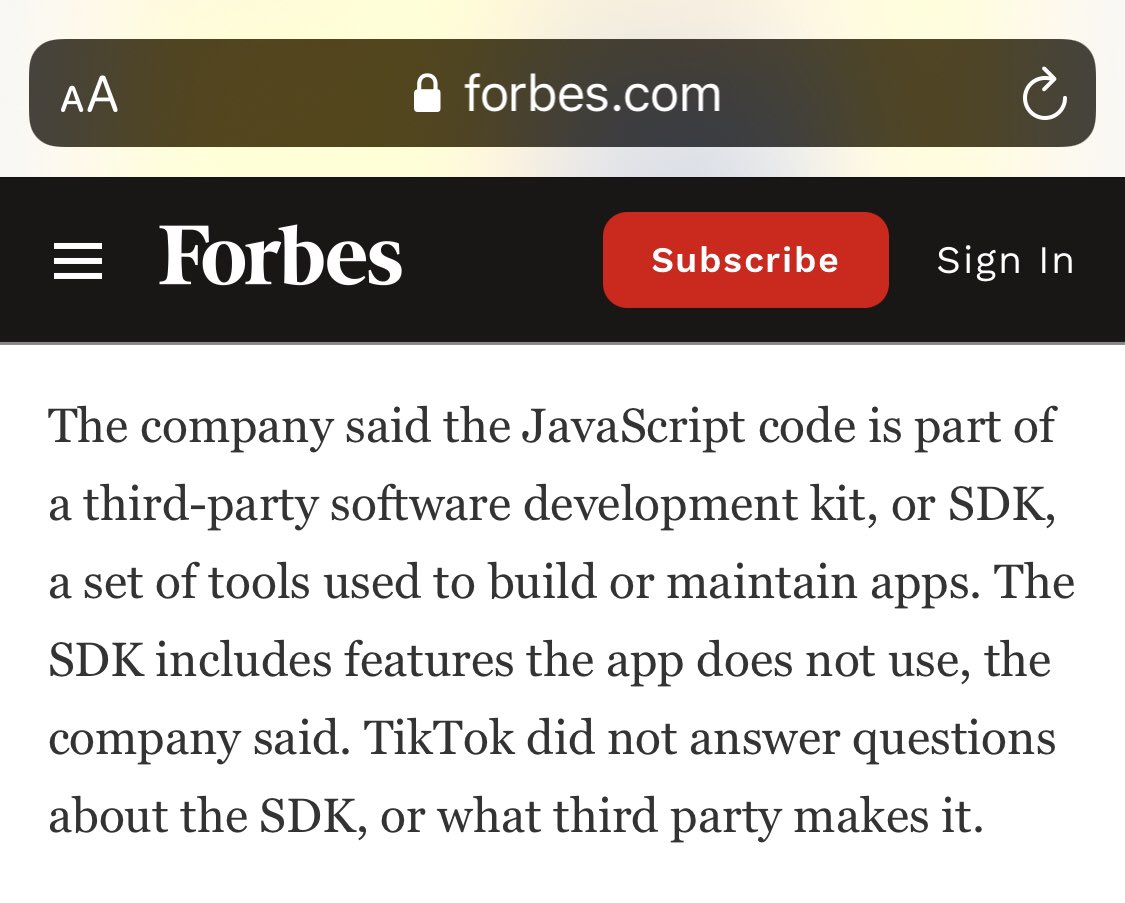
https://twitter.com/the_equalizer0/status/15417471592548638722/ First of as this person said “even if you format 100 times” wait how would that differ from single time format?

 2/ she was using apps like Telegram, Signal (privacy oriented and not co-operating well with authorities in providing required logs) on wi-fi networks of random restaurants, hotels while keeping her phone on aeroplane mode to maintain anonymity. It took lot efforts to track her.
2/ she was using apps like Telegram, Signal (privacy oriented and not co-operating well with authorities in providing required logs) on wi-fi networks of random restaurants, hotels while keeping her phone on aeroplane mode to maintain anonymity. It took lot efforts to track her.