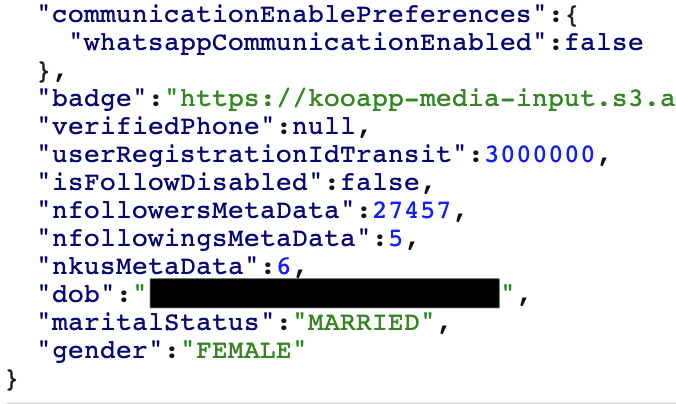
THREAD: I'm looking at a Huawei P20 from China, let see what can I found
The 1st app I reversed is an app called Decision
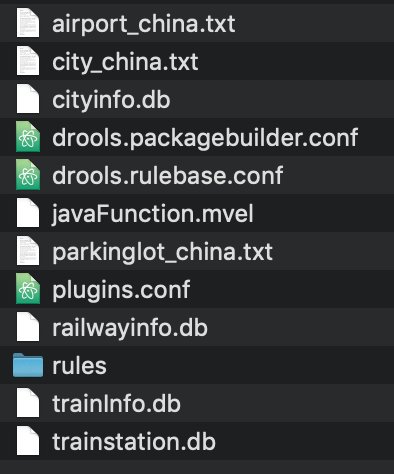
Look at the name of the files contains in the assets folder:
- airport_china.txt
- city_china.txt
- cityinfo.db
- parkinglot_china.txt
- railwayinfo.db
- trainInfo.db
- trainstation.db
Interesting, no?
- airport_china.txt
- city_china.txt
- cityinfo.db
- parkinglot_china.txt
- railwayinfo.db
- trainInfo.db
- trainstation.db
Interesting, no?
I'm a stupid security researcher. For the moment, the keywords are: train, airport, city, geo fence... Do you see where we are going?
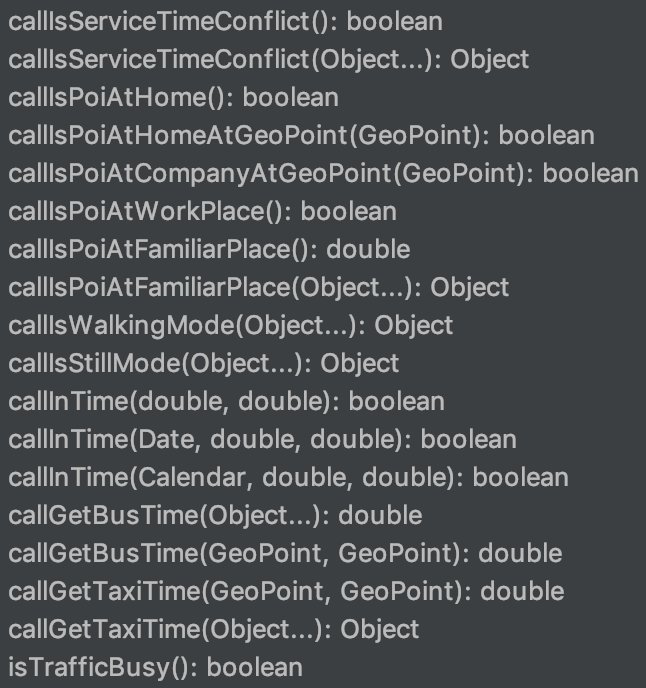
In the data folder, there is a file called CalcMain. Here some of the methods of this class:
- callGetBusTime
- callGetTaxiTime
- isTrafficBusy
- callGetHomeCity
- callHasHotelTicket
- callGetAirportMultiPoi
- callHasGroupBuyingTicket
- ...


- callGetBusTime
- callGetTaxiTime
- isTrafficBusy
- callGetHomeCity
- callHasHotelTicket
- callGetAirportMultiPoi
- callHasGroupBuyingTicket
- ...

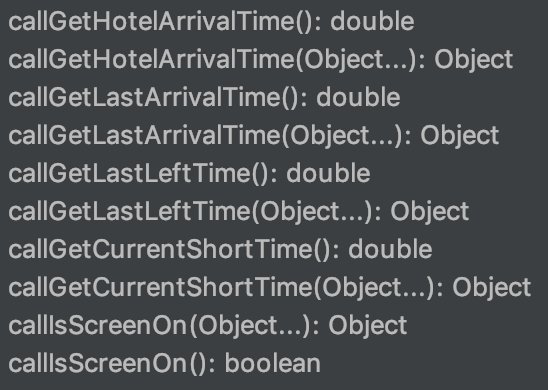
To be clear, this app is composed of 3 background services and 2 services. There is NO UI in this app.
This app doesn't seems to send the data BUT they communicate with another service called HiActionService which is coming from an Huawei app called HiAction 
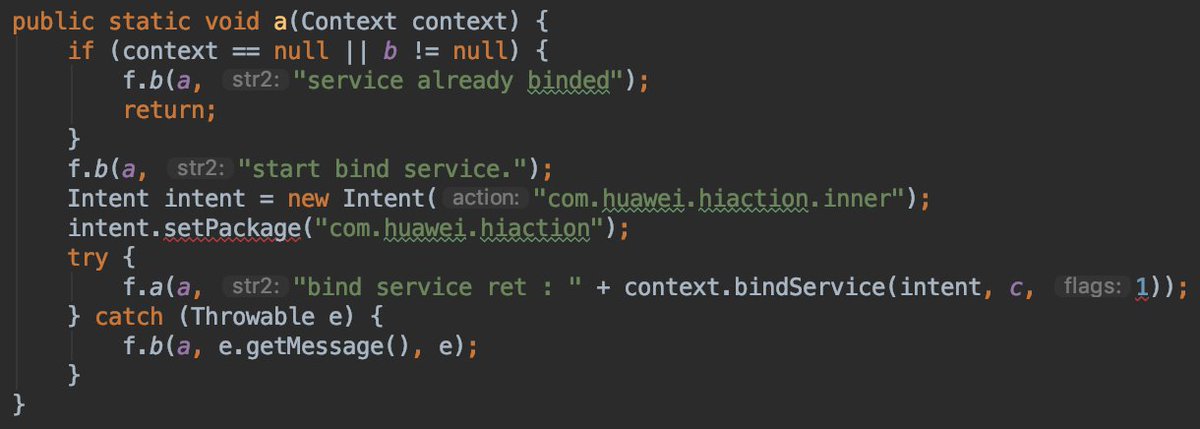
The previous screenshot is from the class called ActionCommonUtil. We can easily that Decision is sending all his events to this service through the methods in this class.
I will study the app HiAction another time but what you have to know is that this app is sending the data to hicloud[.]com, "the Huawei Cloud" 

In order to be more discreet, the OEM dispatch the responsibilities to multiple apps. In this case:
1. An app or the modified Android is getting your location regularly. It will trigger a GEO_ALARM_TRIGGERED to the Decision app
1. An app or the modified Android is getting your location regularly. It will trigger a GEO_ALARM_TRIGGERED to the Decision app
2. Decision app is getting this location and check with his internal databases. If there is a match, it will generate an event
3. Decision will send this event to HiAction
4. HiAction will upload the data to the Huawei cloud
3. Decision will send this event to HiAction
4. HiAction will upload the data to the Huawei cloud
Ugly, no?
Ofc, this is the big picture, I need more time to get all the details.
I started this thread 2 hours ago. Decision app was the first app I checked. I still have a lot of Huawei apps to check
Ofc, I will continue this thread later 😏
If it was not clear enough: DO NOT buy @Huawei phones. NEVER.
*say
Wow my English is really broken when I’m tired
• • •
Missing some Tweet in this thread? You can try to
force a refresh