Build and use modern compiler toolchains w/ safety features enabled.
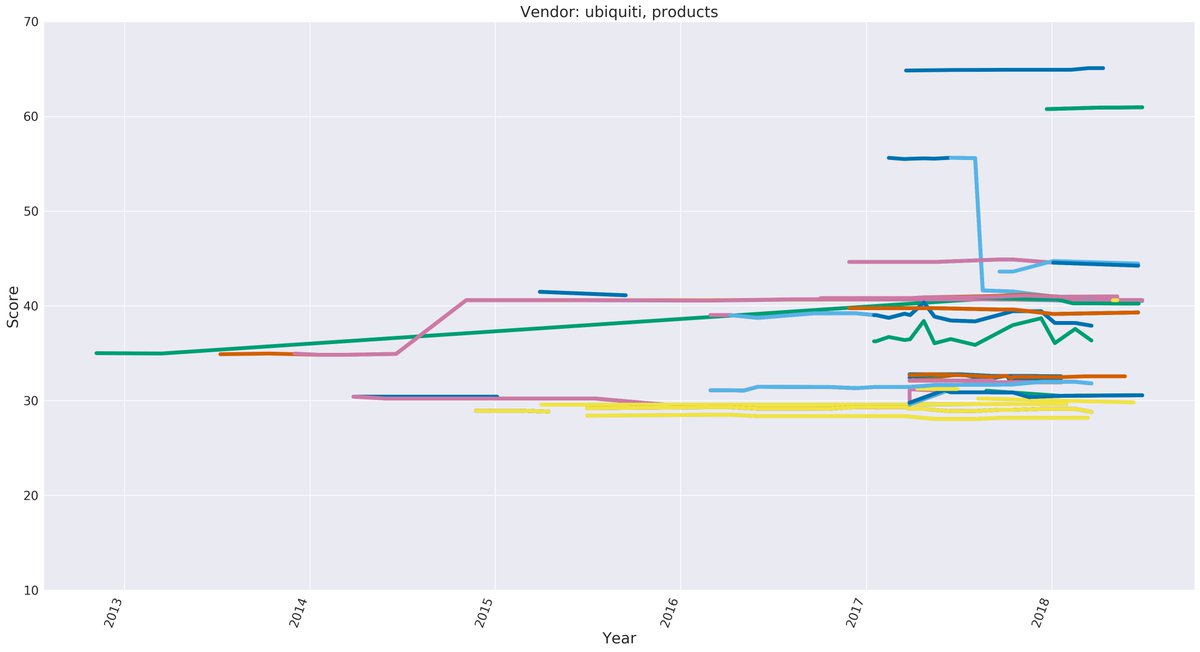
Read the CITL study that evaluated 1.3k IoT products across 15 years; showing the largest poor security issues and downward trends:
cyber-itl.org/2019/08/26/iot…
So you need your IoT device to be at least Linux kernel 2.8 to support this **most basic exploit mitigation**!!
But it gets even trickier...
Unfortunately the kernel fix enabling this introduces a new fixed address RWX mapping... defeating both DEP and ASLR.
It gets trickier. Sigh...
You have a foundation of Linux w/ a kernel of 2.8 or above and you ***rebuild the Kernel removing floating point support*** to address all of this.
Assuming your IoT even works now, you still need a build toolchain.
...
So the toolchain for your commercial product needs to be built from a compiler in the unstable branch(?!).
And,
So you still need to explicitly enable this most basic security feature after all that.
The take away?
And also put in simple unit tests to catch basic safety features being accidentally removed.
Think such unit tests are silly?
Check this out...
Mozilla Firefox for OSX lost ASLR for a while.
The team forgot about the issue and even challenged CITL’s (cyber-itl.org) finding, until they looked for themselves.
They fixed it and I believe have unit tests to spot this going forward now.
Your wireless access points, routers, etc. are runnin on top of these same core systems.
Not to mention more and more medical devices.
EOF