Today, a pro-Trump journalist was arrested while releasing a new doco exposing major US intel & military figures, based on materials from 2 ex-employee whistleblowers.
I have just viewed the doco. Its content is significant & I will now analyse it in full below.
1. The documentary opens with a 'Drain The Swamp' animation. It's cute, but I can tell you for a fact that the swamp is a transnational operation, spanning more than 100 countries worldwide, and is not confined to any US political body. Sadly.
Cuts to Lindsay Graham & other politicians talking about "Russian interference".
Voiceover: "Both parties are equally guilty of covering up what should turn out to be an even bigger scandal: Shadowgate..."
"The tactical and operational role the shadow government played behind the scenes carrying out the coup against Pres. Trump. We're going to be looking behind the puppets at who the real puppet master string-pullers are."
The above concludes the introduction section of the documentary. My thoughts next:
"...who both worked extensively within the shadow govt as contractors have come forward with revelations that may be part of the biggest whistleblowing event to date."
Almost faded out at the bottom of the document, the words: "programs, products & actions that shape emotions, motives, reasons & behaviours.."
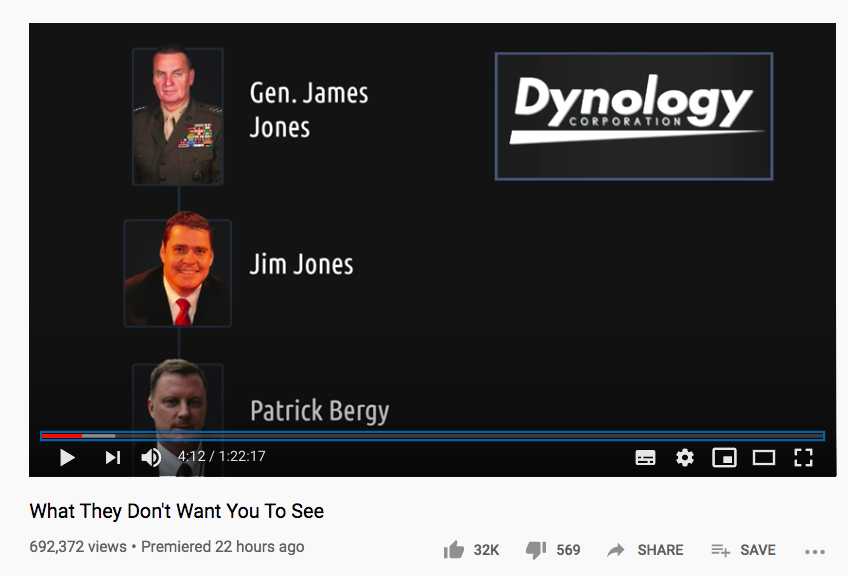
The Dynology product credit at the bottom is dated 2009. So the contract was 2007 and the deployment of this version of the application was two years later (which is normal)
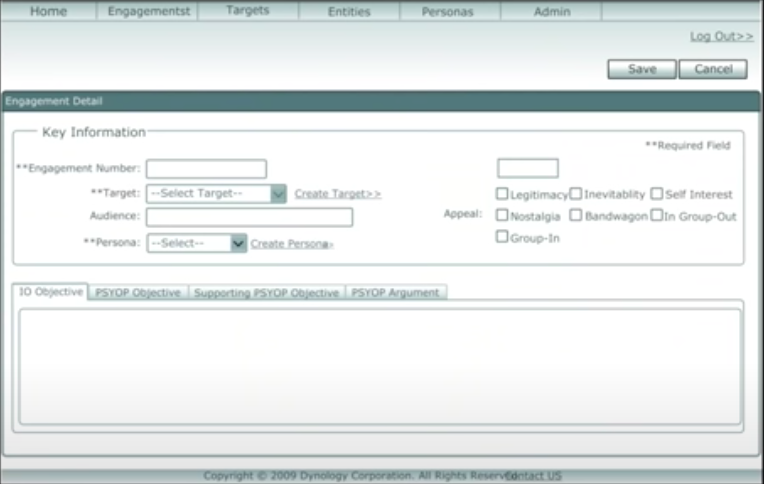
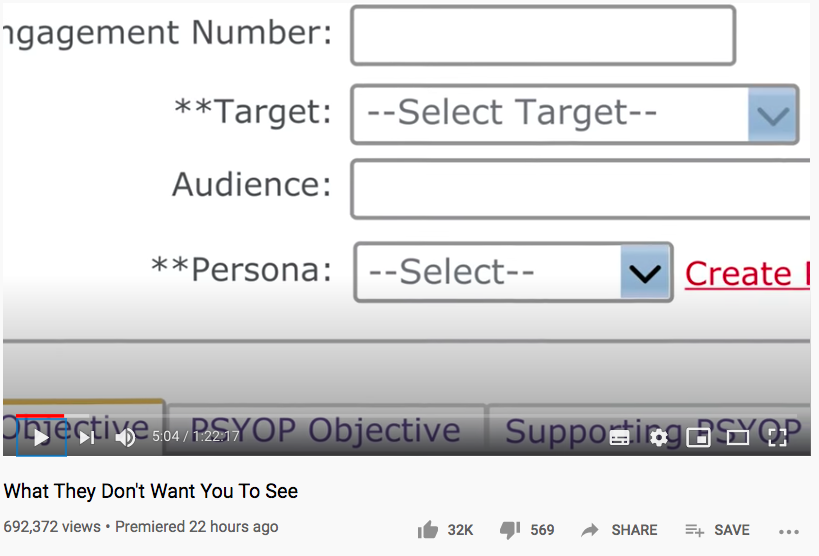
"Engagements" - these are likely jobs, tasks, or the record of interactions
"Targets" - list of their victims
"Entities" - likely classes of targets, groupings like organisations or hashtags
"Personas" - the spy's sock puppets/fake identities
(Spies themselves are ginormous internal targets and many literally live a life of fear like their targets. It's karmic & sad)
Under "Key Information":
A dropdown to select the target (yep, we really are names in their dropdown list)
A dropdown to select the fake identity they use to scam us with
They can also create targets and create personas
In a for-profit surveillance industry, making more money and having more workload requires MORE TARGETS.
Every year, they need more targets than the year before
It's the angles by which they craft their attempt to influence us. Their ins. Designed to trigger emotion & mirror human social behaviour
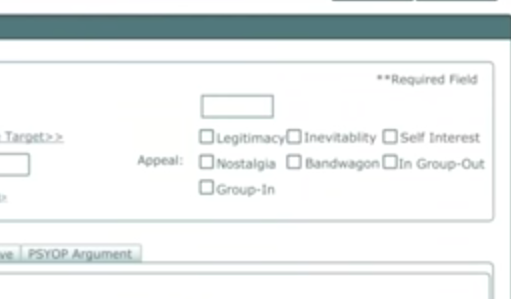
Their manipulation options read:
Legitimacy
Inevitability
Self Interest
Nostalgia
Bandwagon
In Group-Out
Group-In
"I was a contractor for various intelligence agencies that were privately created... because unlike what most people think, our intelligence doesn't stay within our borders or within federal buildings."
Bergy: "You understand enough about someone.. you can use their anxieties"
Tore: "What Bergy created was a program that was based off the strategies that we [intelligence agencies] used in person..."
At 9:42, Bergy: "The database component allows you to build behavioural profiles on individual targets. Through those you can implement reflexive control."
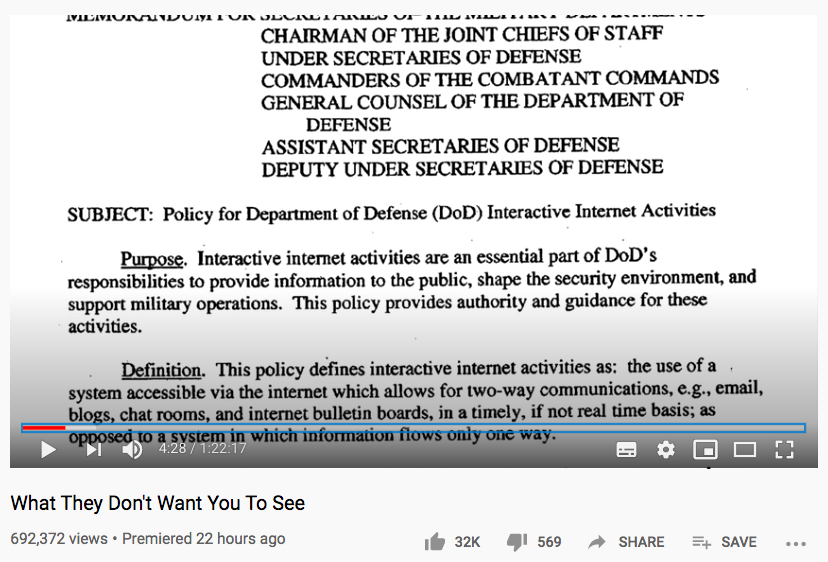
This doco is proof that the full suite of intelligence agency targeting functions and psychological warfare capabilities are now operating in the private sector.
This doco proves that the private sector has access to the same technology, and is using it.
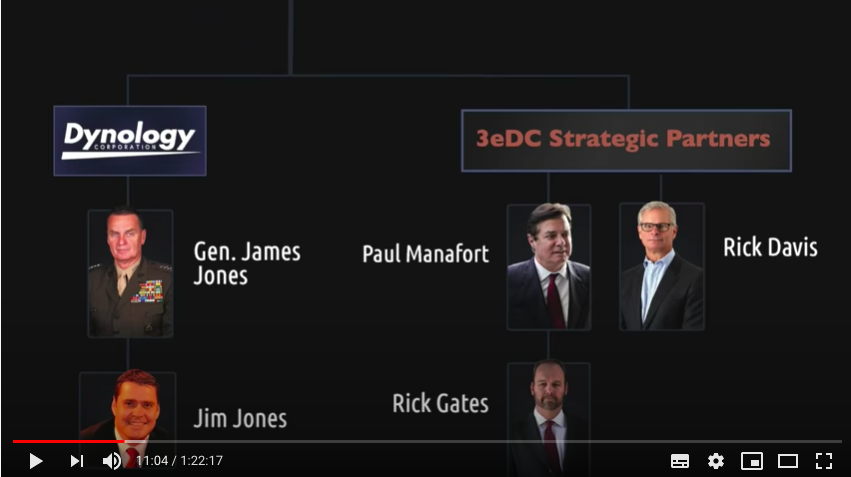
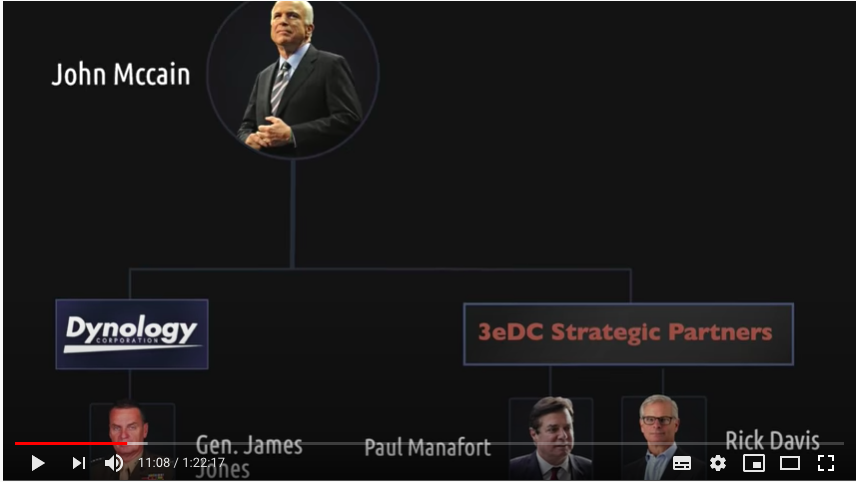
COMING UP: we get into who exactly started these companies, and the very famous names they've been targeting (not just Trump!)
Having extensively studied their disclosures, I completely disagree with this. I suspect its poor wording on the doco's part.
They would just make a request for the intelligence and get it served up on a platter
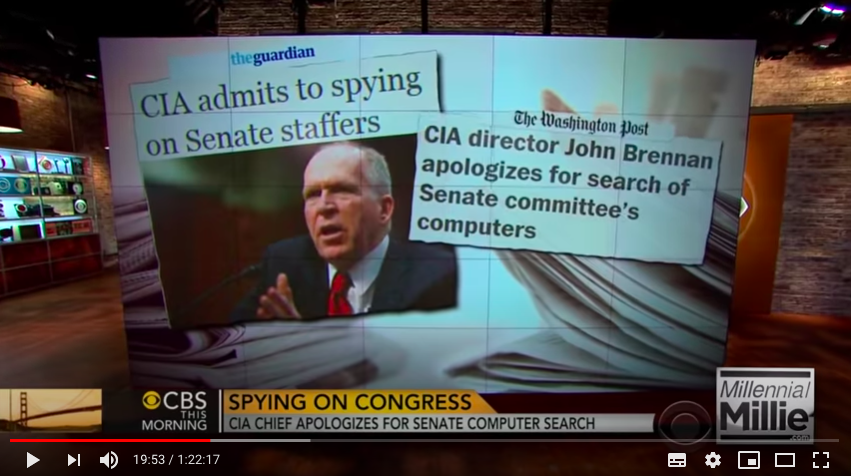
"Tore alleges that she worked for John Brennan at The Analysis Corporation and Global Strategies Group."
This is where things start to get even more interesting.
Tore claims that the "hacks" were cover stories for what was really going on.
Tore details how, in the course of her job, she was instructed to exfiltrate data from the State Department, then was shocked to hear it later being deemed a "hack"
Tore: "I mean that's kind of what Snowden did too."
Snowden has talked about how he created a program to bridge multiple databases for NSA. Snowden *was* a contractor. HOWEVER..
My opinion is that this is misleading. Snowden worked for Booz Allen Hamilton, not Brennan. Snowden & Brennan did not work for CIA at the same time...
The following quote at 18:51 from Tore is edited as if its a follow-on but she's just explaining a full-take.
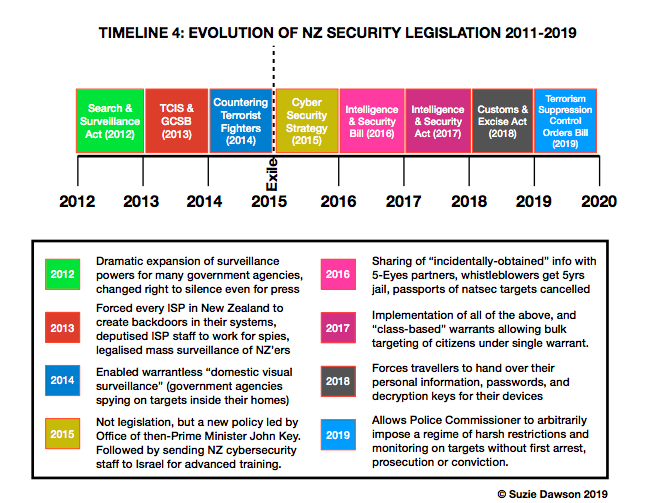
I disagree. US citizens were already being spied on. What it kicked off is excuses
I totally disagree with this idea of blaming the messenger.
Bergy says he complained about it, and the CKMS contract was then awarded to a cut-out/shell company 1 mile away from Dynology's offices.
ie. the inner workings/relationships of Republican party operatives - the U.S. coup in Ukraine - etc.
As for what I personally think? I believe Julian Assange:
Here is the fundraiser for the filmmaker, who was arrested today:
END