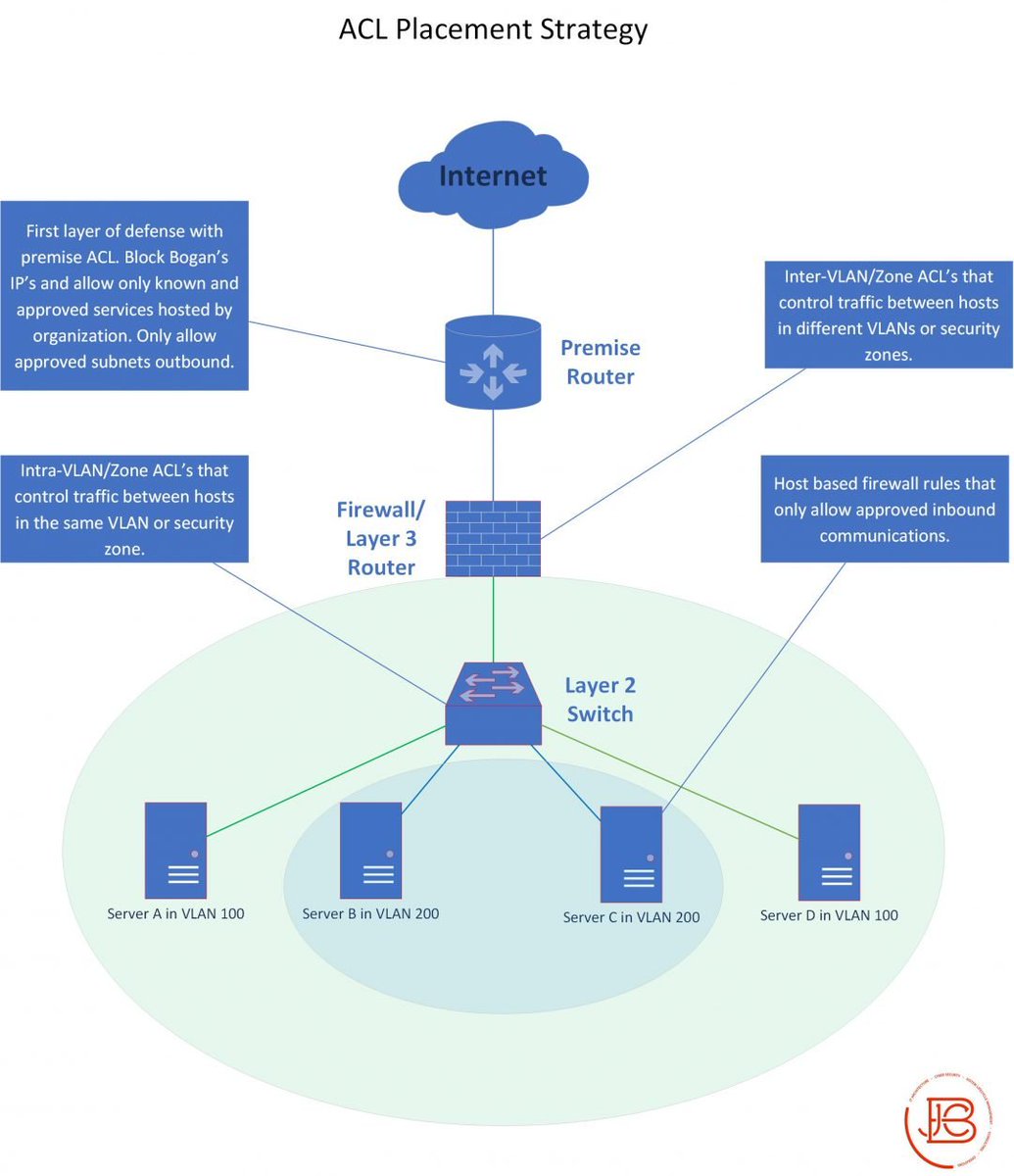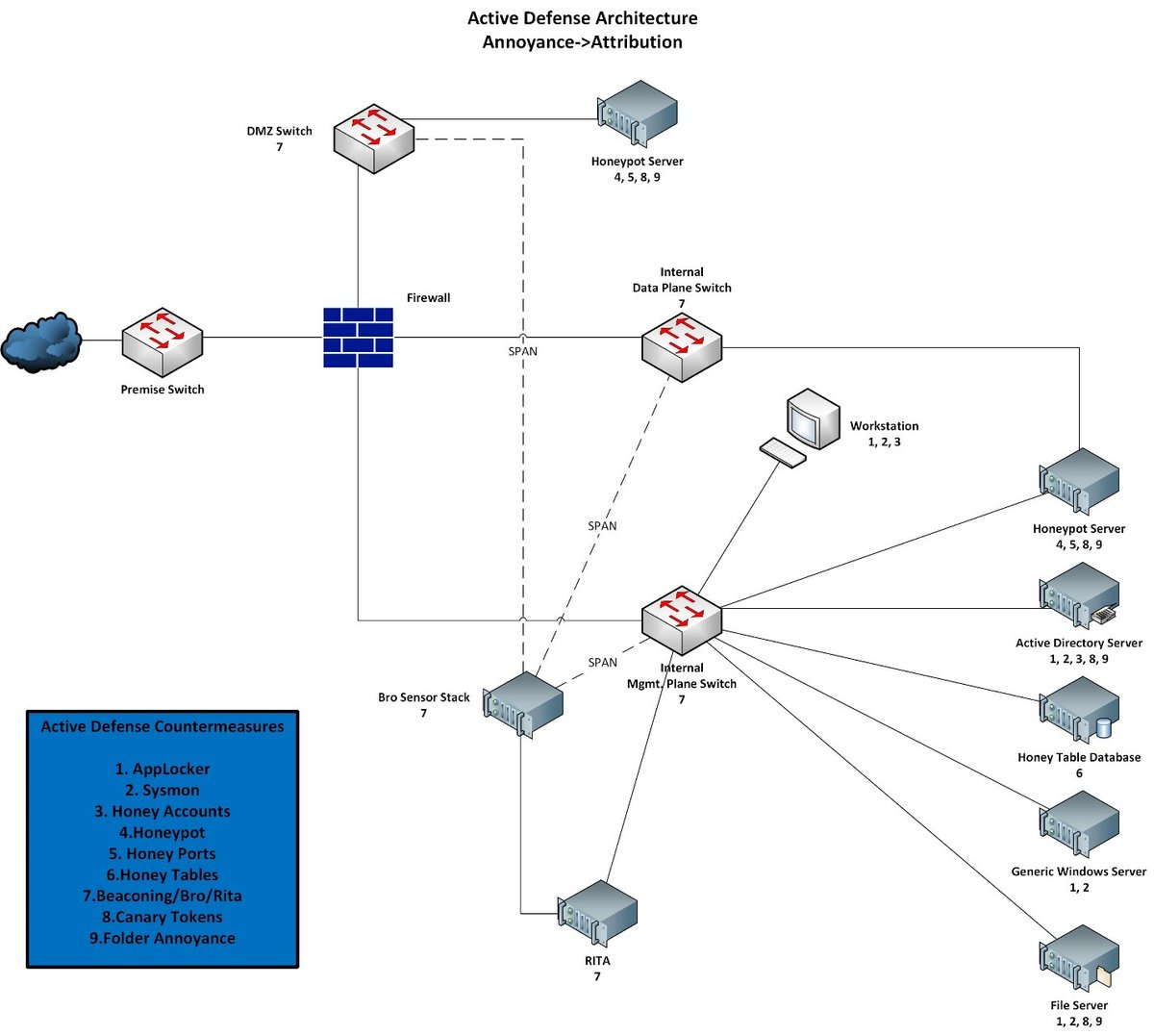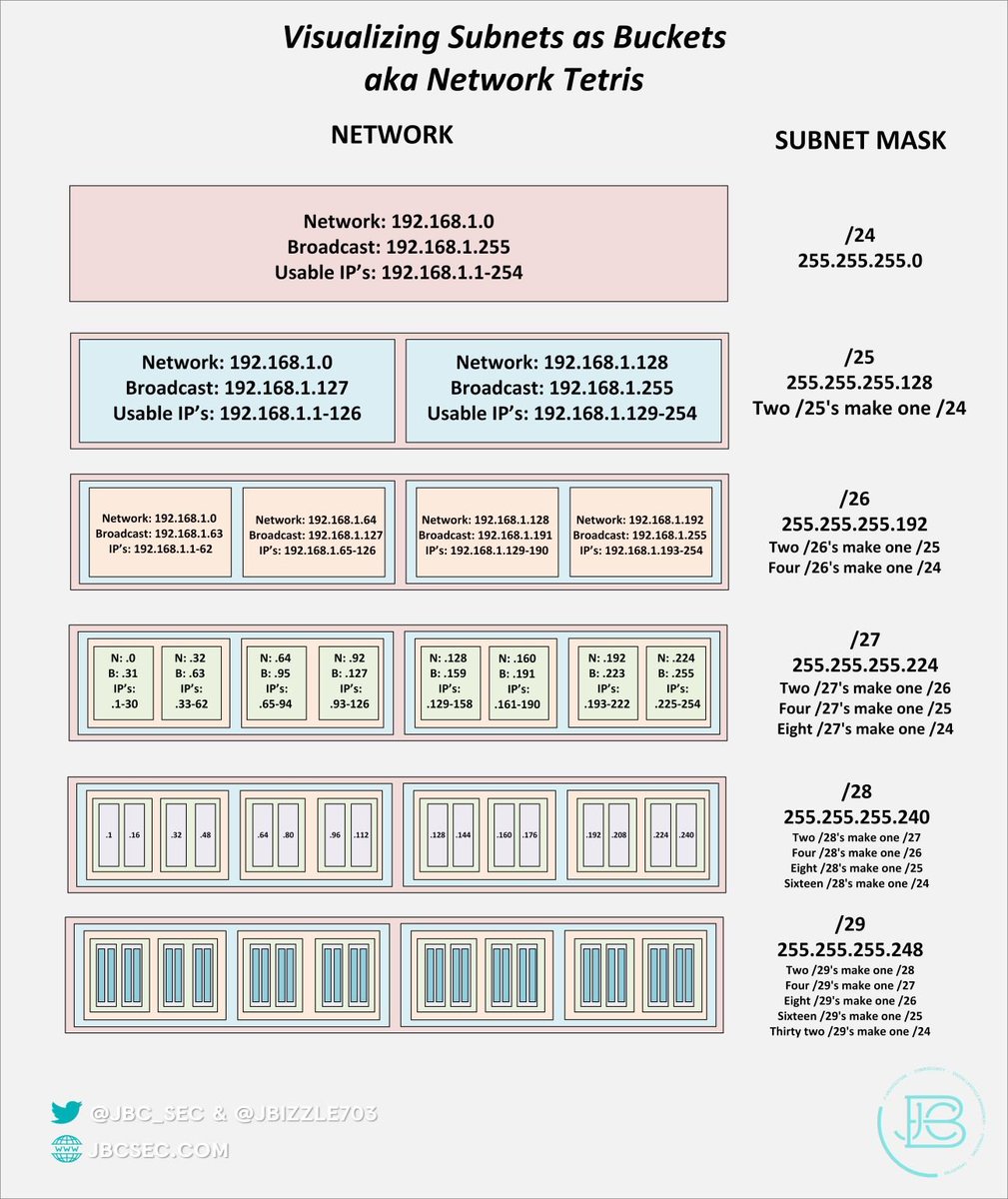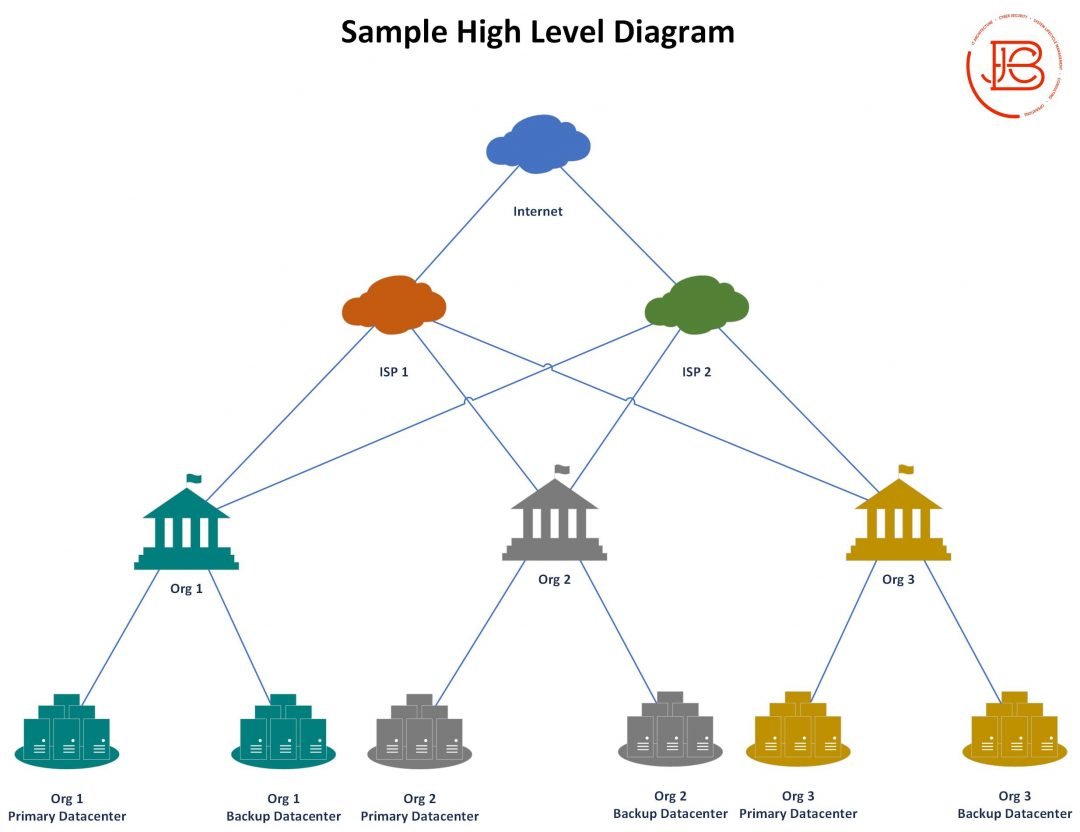
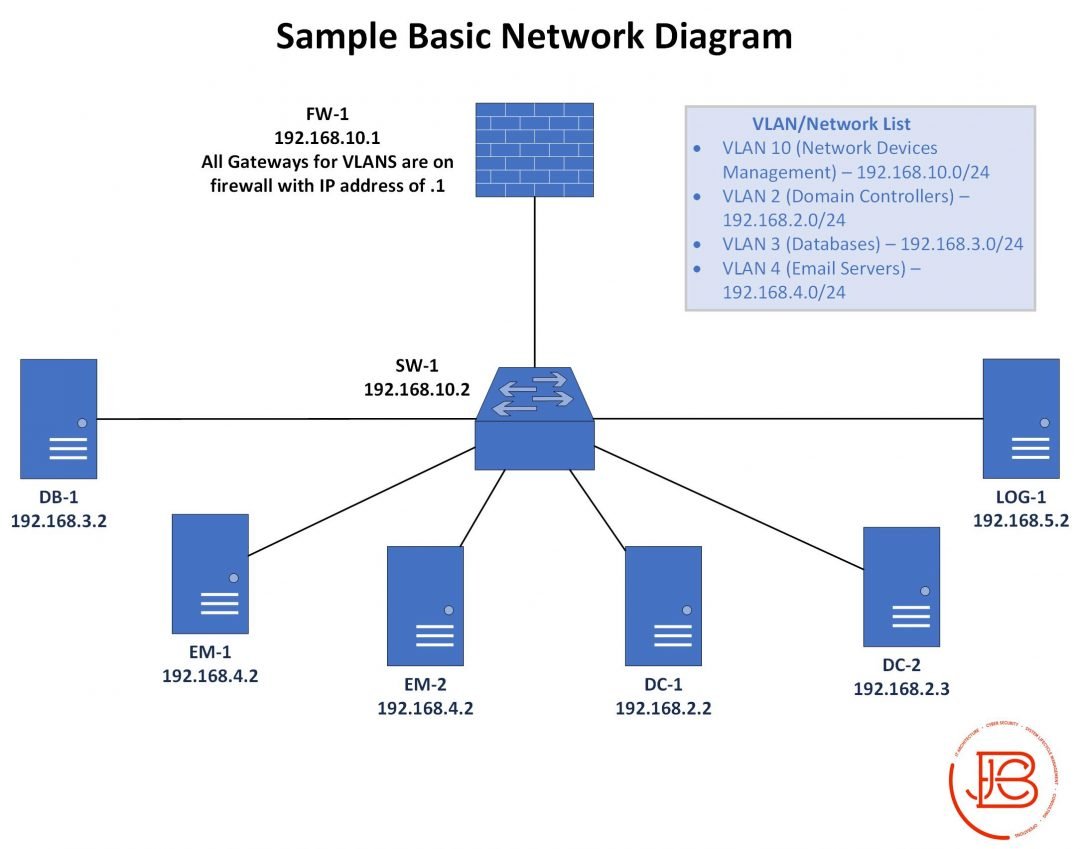
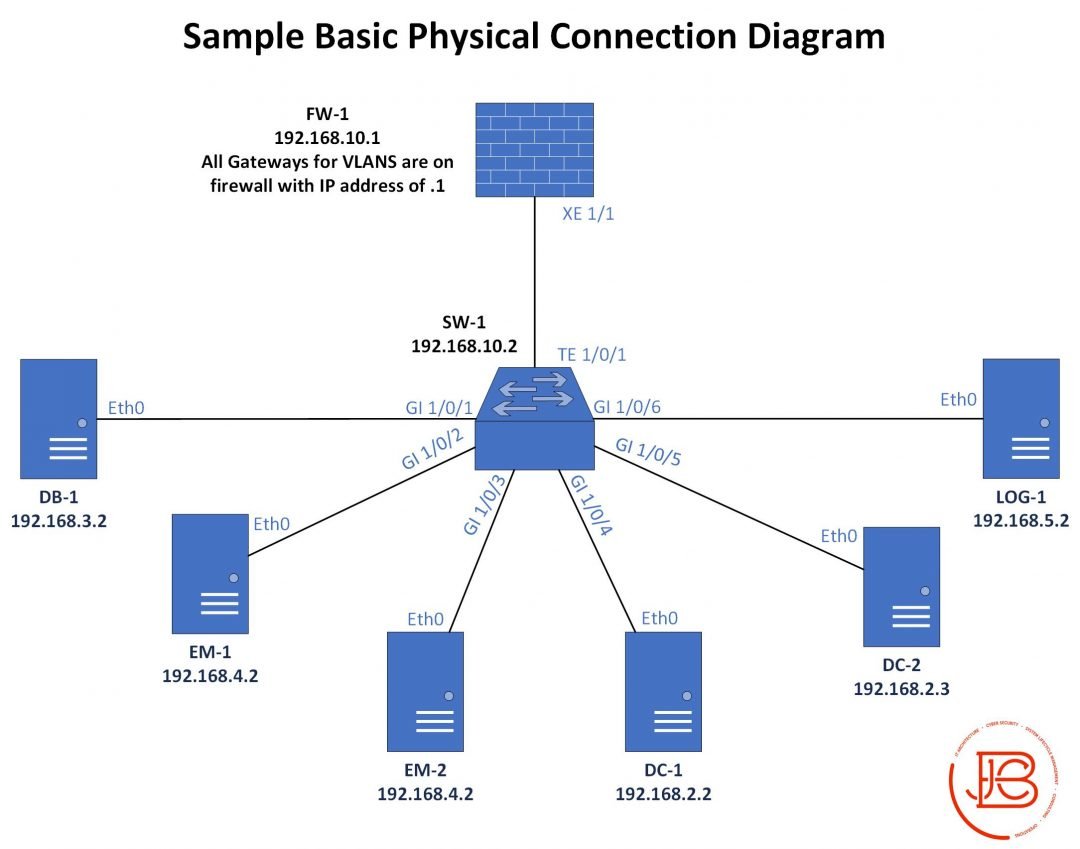
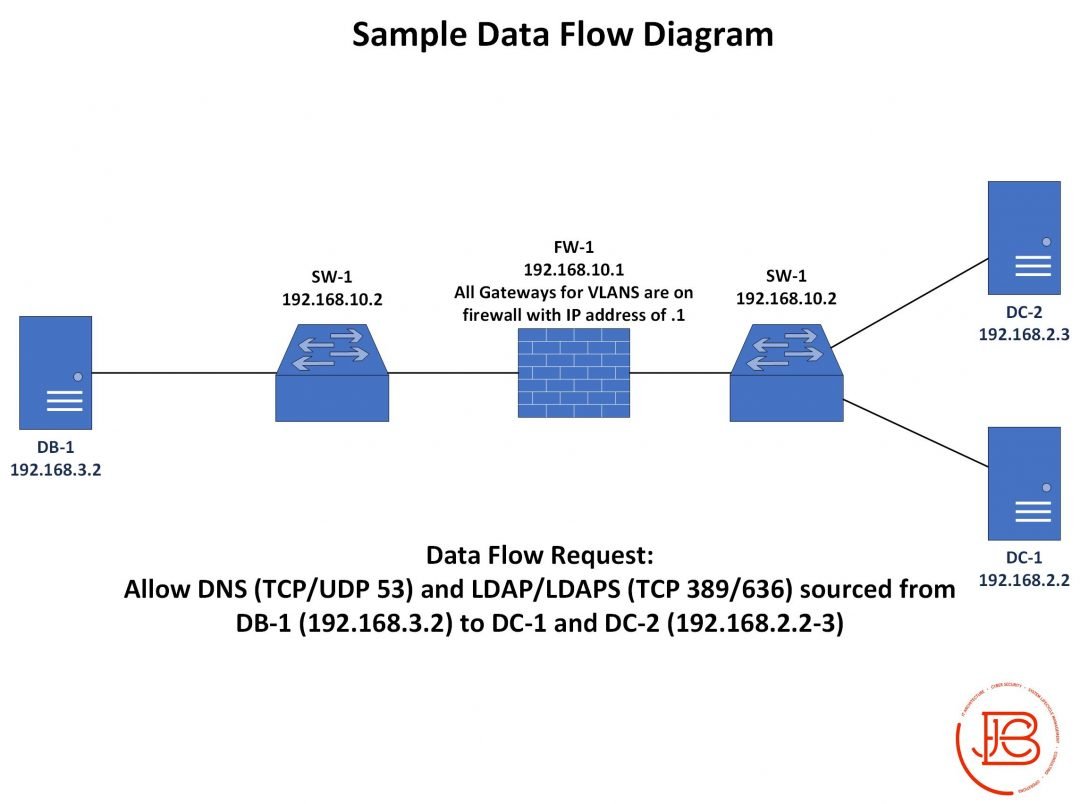
And remember diagrams are only part of the overall documentation you should have (we can go into that more later)!
If you liked this, check out my YouTube channel : youtube.com/c/cyberinsight
Also, sign up for my blog and newsletterThumbs up
mailchi.mp/e7b56addb7fc/c…
@L0Psec
@Teck923
@RyansNotAHacker
@akolsuoicauqol
@JediMammoth
@varcharr
@brianwhelton(you liked the ACL one, this is kind of network security related)