NEW: LockBit uses automated attack tools to identify tasty targets 🎯
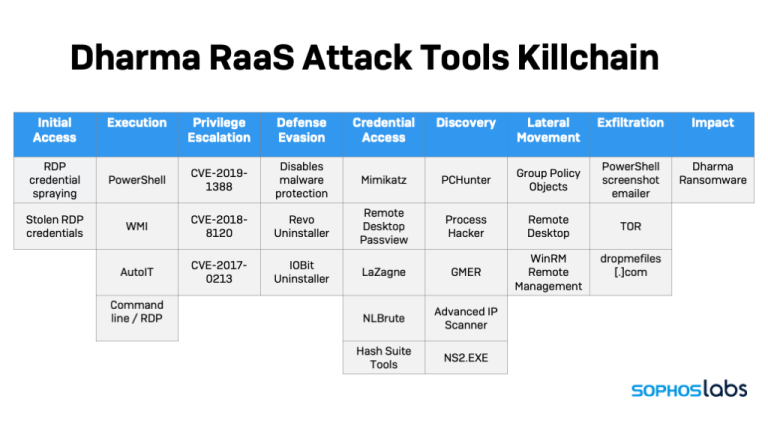
Using renamed copies of PowerShell and Windows’VBscript host and scripts based on PowerShell pen-testing tool, LockBit actors searched for systems with valuable data to hit at small organizations...
1/12
Using renamed copies of PowerShell and Windows’VBscript host and scripts based on PowerShell pen-testing tool, LockBit actors searched for systems with valuable data to hit at small organizations...
1/12

A series of recent attacks detected by Sophos provided us the opportunity to dive deeper into LockBit’s tools, techniques & practices.
Based on some artifacts, we believe that some components of the attack were based on PowerShell Empire.
2/12
Based on some artifacts, we believe that some components of the attack were based on PowerShell Empire.
2/12
The organizations hit in the 8 attacks we analyzed were smaller orgs with only partial malware protection deployed. None of them had public Internet facing systems on their networks, though 1 had an older firewall with ports open for remote administration by HTTP and HTTPS.
3/12
3/12
While analyzing 1 of the attacks, we found traces of a number of PowerShell scripts launched against systems that had malware protection in place.
In the 1st stage, a PowerShell script connects to a Google Docs spreadsheet, retrieving a PowerShell script encoded in Base64.
4/12
In the 1st stage, a PowerShell script connects to a Google Docs spreadsheet, retrieving a PowerShell script encoded in Base64.
4/12

The script fetches the contents of cell B1 & executes it. The retrieved script makes a copy of PowerShell in the system’s TMP folder & executes Base64-encoded contents w/ that copy.
Decoding the script shows it uses a System.Net.ServicePointManager object.
5/12
Decoding the script shows it uses a System.Net.ServicePointManager object.
5/12

Attackers use another form of persistent backdoor: an LNK file dropped into Windows’ startup commands folder. The LNK file launches Microsoft Scripting Host, to run a VBScript, which executes a PowerShell script to read data stored in the link file itself encoded in Base64.
6/12
6/12

The backdoor stub downloads more obfuscated code, creating a proxy connection to the command & control server, & a web request to pull more PowerShell code.
1 of the modules downloaded is a collection of functions for reconnaissance & to disable anti-malware capabilities.
7/12
1 of the modules downloaded is a collection of functions for reconnaissance & to disable anti-malware capabilities.
7/12

Another module downloaded by the backdoor checks for software that may indicate the system is of greater value.
If it's indicated that the system is what the attackers are looking for, the C2 server sends back commands that execute additional code.
8/12
If it's indicated that the system is what the attackers are looking for, the C2 server sends back commands that execute additional code.
8/12

Depending on what responses come back from the C2, the backdoor can execute a number of tasks:
▪️ Force a logoff
▪️ Grab hash tables to apparently exfiltrate for password cracking
▪️ Attempt to configure a VNC connection & create an IPSEC VPN tunnel
9/12
▪️ Force a logoff
▪️ Grab hash tables to apparently exfiltrate for password cracking
▪️ Attempt to configure a VNC connection & create an IPSEC VPN tunnel
9/12

In attacks we analyzed, the PowerShell backdoor was used to launch the Windows Management Interface Provider Host (WmiPrvSE.exe).
Firewall rules were configured to allow WMI commands to be passed to the system from a server by creating a crafted Windows service.
10/12
Firewall rules were configured to allow WMI commands to be passed to the system from a server by creating a crafted Windows service.
10/12
The attackers launched the ransomware via a WMI command, filelessly—without dropping a single file artifact on the disk of the targeted systems. All of the targets were hit within 5 minutes over WMI.
Sophos Intercept X stopped the attack on systems it was installed upon.
11/12
Sophos Intercept X stopped the attack on systems it was installed upon.
11/12
Read the full article by @thepacketrat: news.sophos.com/en-us/2020/10/…
SOPHOSLABS WOULD LIKE TO ACKNOWLEDGE THE CONTRIBUTIONS OF VIKAS SINGH, FELIX WEYNE, RICHARD COHEN AND ANAND AJJAN TO THIS REPORT.
12/12
SOPHOSLABS WOULD LIKE TO ACKNOWLEDGE THE CONTRIBUTIONS OF VIKAS SINGH, FELIX WEYNE, RICHARD COHEN AND ANAND AJJAN TO THIS REPORT.
12/12
• • •
Missing some Tweet in this thread? You can try to
force a refresh