Here's a thread that explains their TTP (tactics, techniques & procedures):

sophos.com/en-us/medialib…
What follows is a summary of some of what we covered in the report

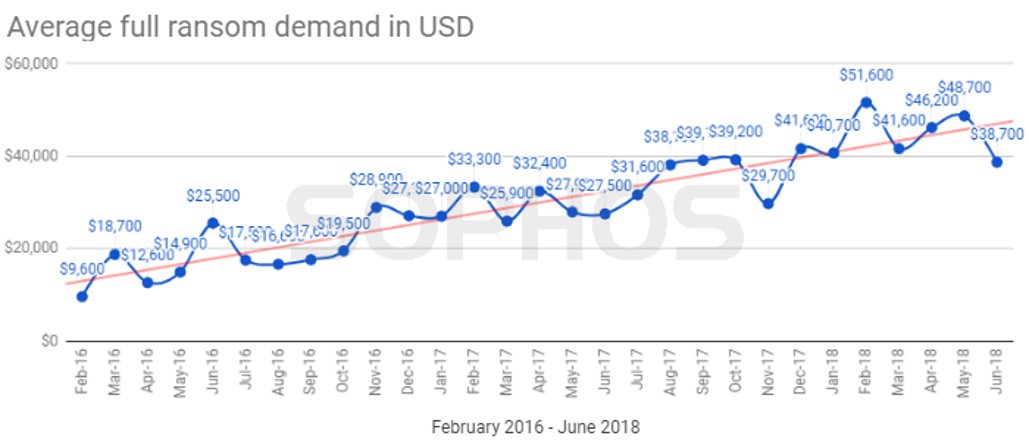
If you have RDP open, please close it now.

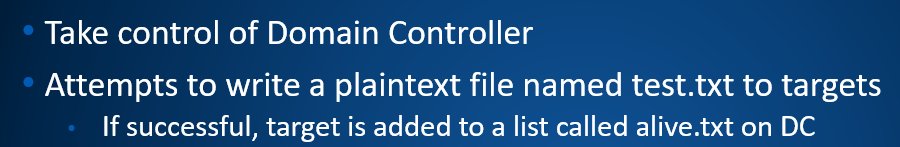
You couldn't just restore from backups. You needed to reimage the disk first. Pure evil.

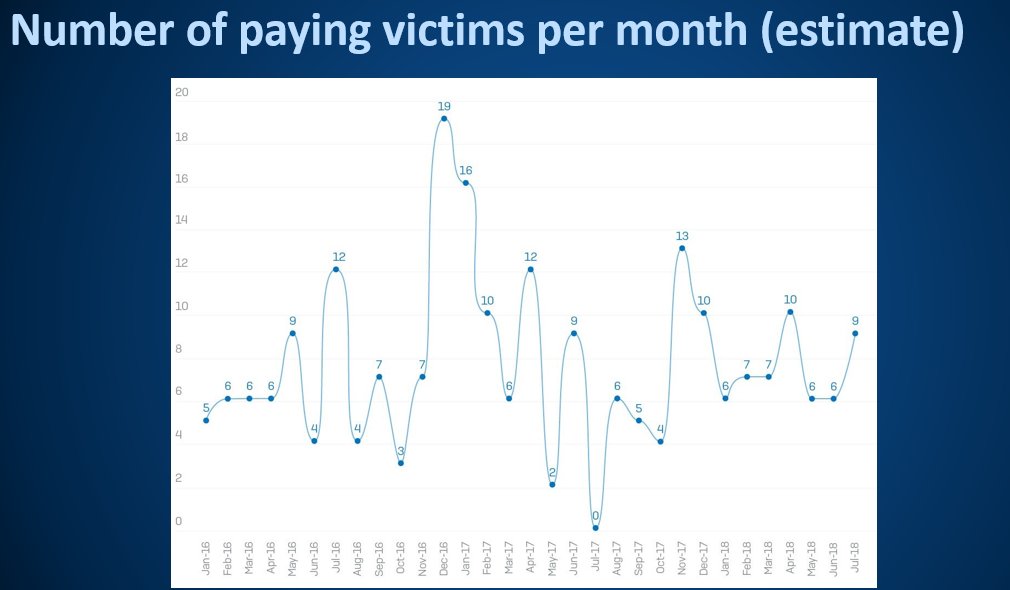
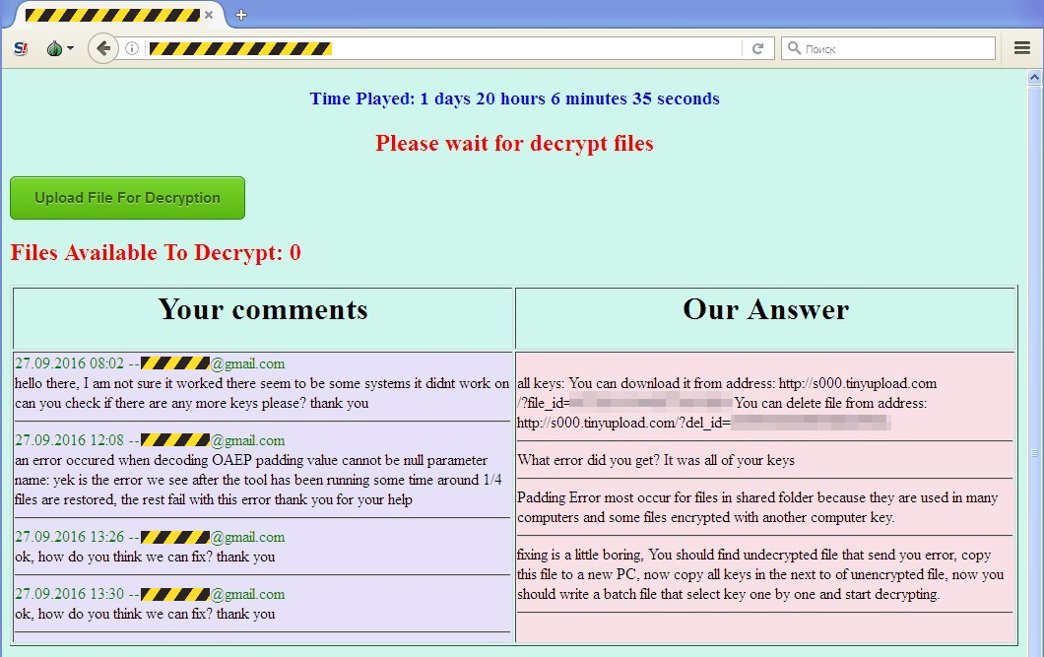
These disappeared as soon as the victim paid. Only a few screenshots exist. Here's one:
All these "silent victims" were large businesses.
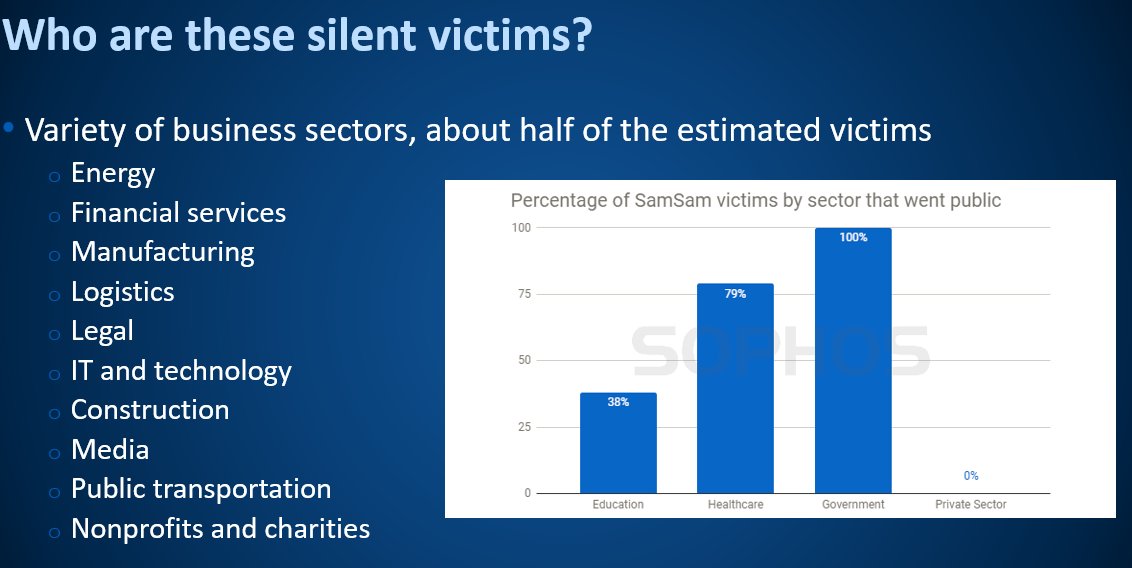
Now that we know who the attackers were, the motivation seems kind of obvious
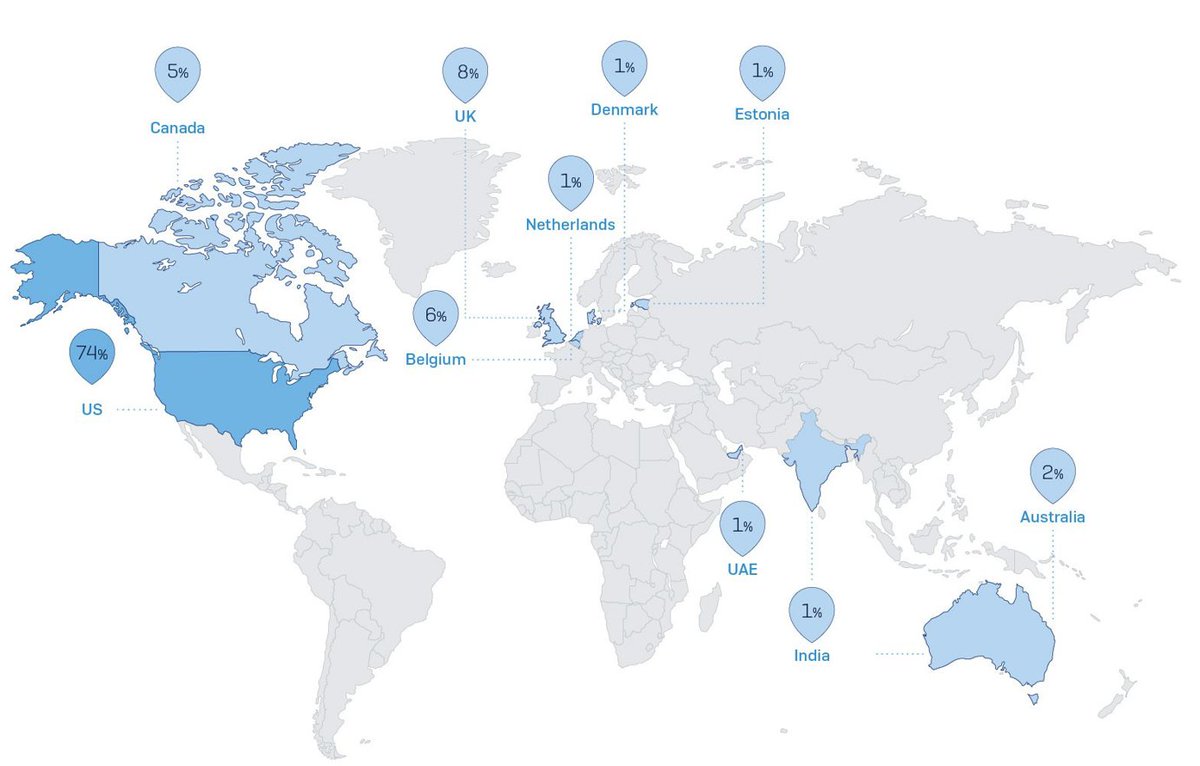
Nobody's been arrested, and there is still a lot of low-hanging fruit out there.
news.sophos.com/en-us/2018/07/…























