Ticketmaster fined £1.25million for security compromise (they were hacked by Magecart group, their website code was altered to steal data during payments), #GDPR breach. ~9.4m customers affected. Payment data stolen, too. ico.org.uk/media/action-w… 

https://twitter.com/lukOlejnik/status/1012262516200824833


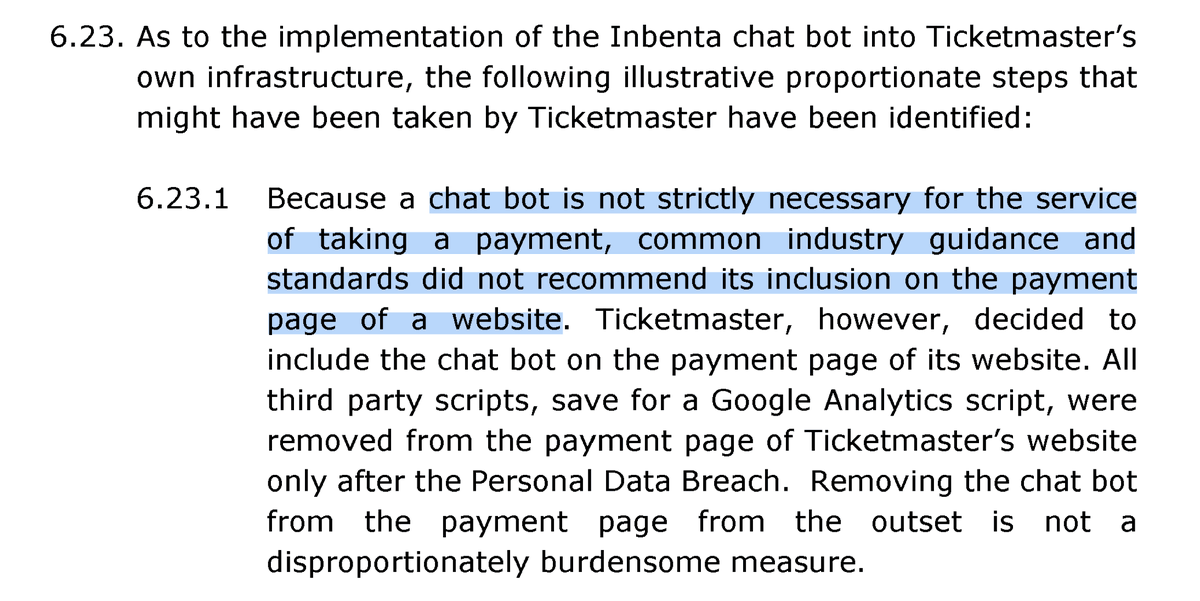
Third-party (chatbot provider) was breached. This spilled to Ticketmaster. Had this functionality not included on the payment site, this breach would not happen (this way, at least). Fun fact: ICO decided to enforce PCI-DSS requirements. #GDPR #ePrivacy 



Ticketmaster says they were unable to use the standard subresource integrity (blog.lukaszolejnik.com/making-third-p…) to protect their site because the software changed too often (but they did not know how often). "ICO views this measure as an appropriate measure to implement" #GDPR 



In sum, deployers of vulnerable software inherit and accept the risk. This case is also a model example well subscribing to how #GDPR fines are calibrated (blog.lukaszolejnik.com/everything-you…) 


• • •
Missing some Tweet in this thread? You can try to
force a refresh