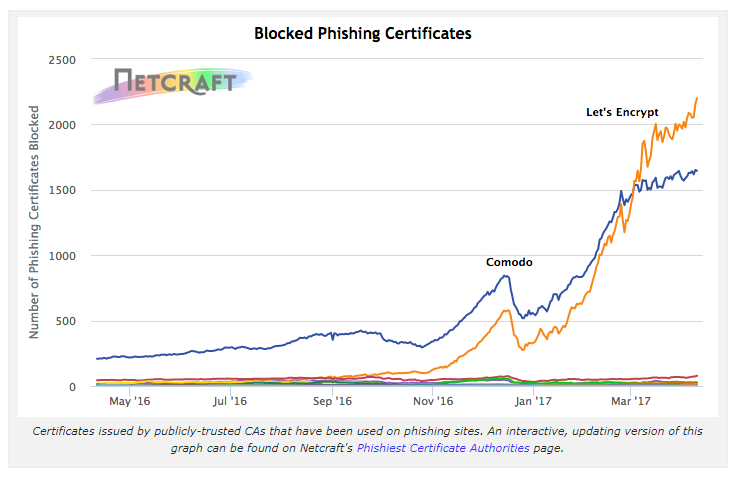
There's been a lot of discussion about OCSP again recently after the Apple incident caused by Big Sur. I've written up some details about what happened and thoughts for what we could/should do about it: scotthelme.co.uk/deja-vu-macos-…
Apple published a support article to address the concerns raised, here are the details and my update based on their comments: scotthelme.co.uk/deja-vu-macos-…
Apple will introduce "A new encrypted protocol for Developer ID certificate revocation checks" but are we talking OCSP over HTTPS or something else?
Apple have promised "Strong protections against server failure" so they're likely going to bolster the OCSP service with a lot more cloud.
Users won't have to block OCSP requests for developer certificates and can instead use "A new preference for users to opt out of these security protections".
• • •
Missing some Tweet in this thread? You can try to
force a refresh