
1/28 Don't take chances rolling the dice.
A thread on verifying @COLDCARDwallet firmware, generating a 24-word seed phrase with dice, verifying the dice rolls, backing up the seed with a 3D printed @blockmit_com jig, and stress testing the backup.
A thread on verifying @COLDCARDwallet firmware, generating a 24-word seed phrase with dice, verifying the dice rolls, backing up the seed with a 3D printed @blockmit_com jig, and stress testing the backup.

2/28 This thread is the short version of a more detailed article, which can be found on my blog here:
econoalchemist.com/post/don-t-tak…
econoalchemist.com/post/don-t-tak…
3/28 Self-custody is an important part of mitigating permissioned relationships, counter party risks, & privacy intrusion. The way 2020 has been going, ever-encroaching laws will wind up turning your normal behavior into illegal activity sooner than later.
4/28 If you're following along at home, make sure you sourced your hardware based on this guide by @blockmit_com and if you don't have a 3D printer, you can get the jig from @CryptoCloaks
blockmit.com/guias/hazlo-tu…
blockmit.com/guias/hazlo-tu…
5/28 Here is a pic of everything you'll need:
The washers are 24mm O.D. x 8mm I.D.
The bolt is M8-1.25x60mm.
The stamp set is a 3mm (1/8") letters & numbers.
All the hardware is stainless steel.
The washers are 24mm O.D. x 8mm I.D.
The bolt is M8-1.25x60mm.
The stamp set is a 3mm (1/8") letters & numbers.
All the hardware is stainless steel.

6/28 Before creating a new seed word, the @COLDCARDwallet firmware should be downloaded, verified, and updated if necessary. The firmware can be downloaded from here: coldcardwallet.com/docs/upgrade 

7/28 Next, you can find the PGP public key under the "Advanced: Verify Your Downloads" section. This can be imported into your PGP software. 







8/28 While importing the PGP public key, you may be prompted to certify it. I used keybase.io/DocHex to verify the fingerprint. 





9/28 Once you have the key imported & certified, navigate back to the @COLDCARDwallet upgrade page, & scroll down to the clear-signed text and save that the same way you saved the PGP key, as an .asc file. 





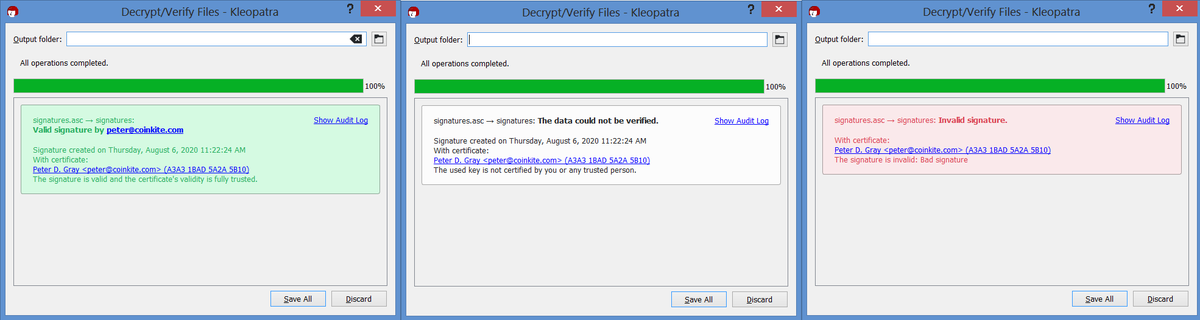
10/28 Then the PGP key will be used to verify the signature. It's important to understand the visual difference between verified from certified key, verified from un-certified key, & failed results. 


11/28 Now the sha256 checksum can be calculated on the downloaded firmware file and then compared to the hash value on the clear-signed text. If it's a match you're all good to upgrade your @COLDCARDwallet 



12/28 After initializing & setting up the PIN on @COLDCARDwallet navigate to Import Existing>Dice Rolls. Once there, the "0 rolls" screen will always be displayed with the hash value, e3b0c...b855. The keys 1-6 can be used to enter the corresponding dice rolls. 





13/28 With a pen & notepad, start rolling the dice, writing down the number, and entering the number on the ColdCard. Repeat 50 times for 128 bits of entropy or 99 times for 256 bits of entropy. Entropy is calculated by using log2(6^99) = 255.9.
14/28 Now that the dice rolls have been copied to the notebook and entered into the ColdCard, let's see what 24-word seed phrase the ColdCard comes up with. This will also be written down.
15/28 A BIP39 passphrase is not necessary to use while simply verifying the dice roll math. But I am going to cover the topic here because I think it is an important added security that should be used often. Consider using this chart as a guide. H/t @wakaizashi 

16/28 You may not want to keep your passphrase stored with your 24-word seed phrase, you may want to store them separately since, combined, they could unlock your funds. Make sure you note the fingerprint!
18/28 Now that the dice rolls have been entered & 24-word seed generated, we want to verify it's authenticity using what was written in the notebook. ColdCard's guide on verifying Dice Roll math can be found here: coldcardwallet.com/docs/verifying…
19/28 Do not use your actual dice rolls on a normal desktop system as that will completely comprise the security of your funds. Just use this as practice to satisfy your curiosity as to whether or not the @COLDCARDwallet is honest.
Run "$ echo -n 123456 | sha256sum"

Run "$ echo -n 123456 | sha256sum"


20/28 Using @torproject, navigate to coldcardwallet.com/docs/rolls.py and save that script and change directory to where you saved it and run: "$ echo 123456 | python3 rolls.py" this will recreate your 24-word seed. 
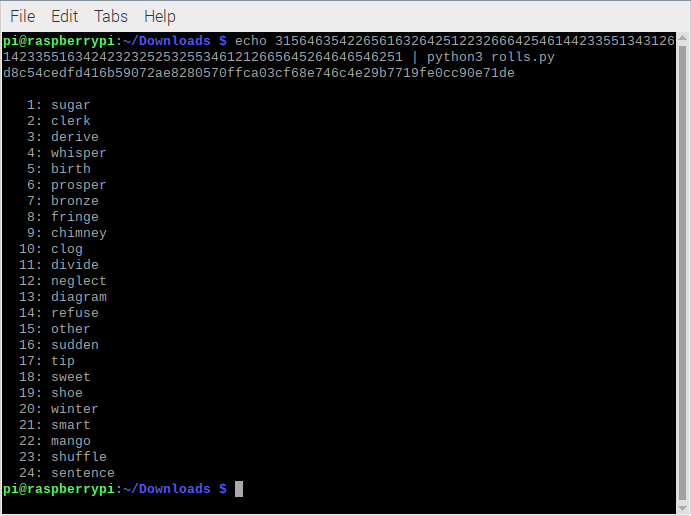
21/28 Now that you know your @COLDCARDwallet isn't up to any funny business, do that all over again with your real dice rolls, but don't type them in a computer this time. Once you have your real seed, stamp it into some washers. 



22/28 H/t to @Multicripto for originally bringing the @blockmit_com jig to my attention. If you don't have a 3D printer, you can purchase these jigs from @CryptoCloaks
23/28 Make sure to source all the materials correctly, this jig was designed to use metric hardware. It is recommended to use double sided tape to keep the washers and jig aligned while stamping. My son helped supervise me to make sure I got the stamping done right.
25/28 I was curious how well a stainless steel washer backup would be able to withstand extreme heat. So I heated up the backup until it was white hot and just starting to melt. Then took the washers apart and found that they were all still totally legible.
27/28 Then I decided to mix up some salt-water and throw the backup into the jar, I'm planning on letting it sit in the salt-water until Christmas (40 days) and then I'll open it and see if any corrosion has occurred. I'm not expecting much, since it is stainless steel. 

28/28 Thanks for reading! I hope this got you thinking about self-custody and seeing the benefits of it as well as how safe it can be. And how cool this @blockmit_com jig is.
Check out the full version of this thread on my blog: econoalchemist.com/post/don-t-tak…
Check out the full version of this thread on my blog: econoalchemist.com/post/don-t-tak…
• • •
Missing some Tweet in this thread? You can try to
force a refresh













