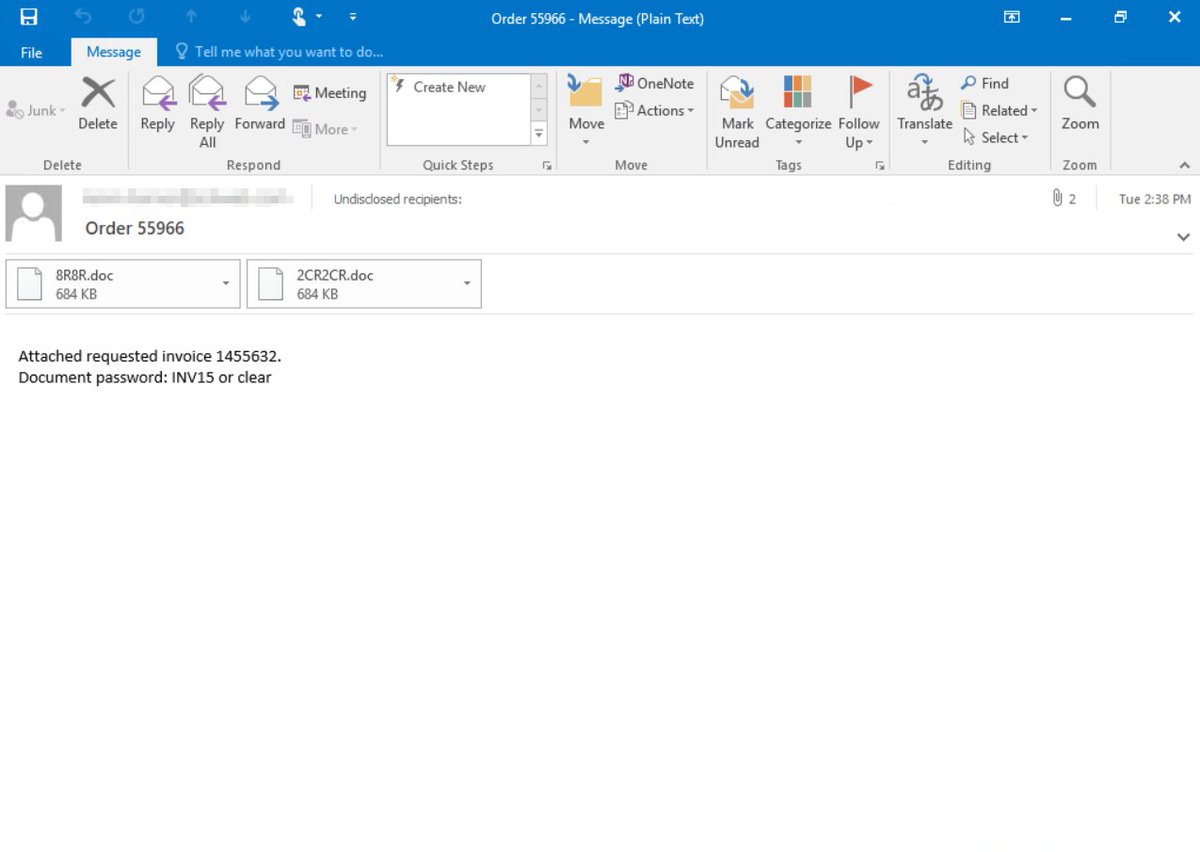
In the past weeks, researchers have noted the increased abuse of legitimate cloud hosting services in malware campaigns. Microsoft threat intelligence shows this trend persists, w/ a number of known malware incl. BazarLoader, Zloader, Lightbot, Hancitor, etc. using the technique.
The email campaigns use a wide range of lures, incl. ones that use threats of job dismissal, exposing illegal activity, other fear tactics. The link leads to a malicious document or archive file hosted on a legitimate service. Downloading & opening the file leads to the payload.
A recent campaign uses password-protected .zip files hosted on Google Drive, with the password (curiously incorrect in this sample) in the email. While other services, incl. those from Microsoft, have been abused, the recent spike in the use of Google services is notable. 



To help protect against these attacks, Microsoft Defender for Office 365 uses machine learning and detonation technology to automatically analyze new and unknown threats in real time, backed by Microsoft researchers closely monitoring the trend to ensure continued coverage.
Sample IoCs: Password-protected .zip files (SHA-256): be20dfd99d49b4639f272761be9d0ea0f89cf77bd62859483113fe3958ed0303, 3a55962a819764fe6a513fe2360a0684be25550a8c844db431198aef75831532
Here’s a sample advanced hunting query that Microsoft 365 Defender customers can run to locate emails that use the techniques we observed in these campaigns: 

• • •
Missing some Tweet in this thread? You can try to
force a refresh