Great overview of permission management in AWS by @bjohnso5y (SEC308)
Lots of tools to secure your AWS environment (maybe that's why it's so hard to get right, lots of things to consider) but I love how it starts with "separate workloads using multiple accounts"
Lots of tools to secure your AWS environment (maybe that's why it's so hard to get right, lots of things to consider) but I love how it starts with "separate workloads using multiple accounts"

SCP for org-wide restrictions (e.g. Deny ec2:* 😉).
IAM perm boundary to stop ppl from creating permissions that exceed their own.
block S3 public access
These are the things that deny access to things (hence guardrails)
Use IAM principal and resource policies to grant perms

IAM perm boundary to stop ppl from creating permissions that exceed their own.
block S3 public access
These are the things that deny access to things (hence guardrails)
Use IAM principal and resource policies to grant perms


"You should be using roles so you can focus on temporary credentials" 👍
Shouldn't be using IAM users and groups anymore, go set up AWS SSO and throw away the password for the root user (and use the forgotten password mechanism if you need to recover access)
Shouldn't be using IAM users and groups anymore, go set up AWS SSO and throw away the password for the root user (and use the forgotten password mechanism if you need to recover access)
Resource policies are great for cross-account access management and for delegating permission management to the resource owner.
All requests start with DENY, and have to pass a whole series of gates to get to ALLOW. This gets complicated sometimes, even for seasoned users... especially when cross-account access is involved.
Memorize this flow.
Memorize this flow.

Brigid demoed creating a SCP in the console.
If you want to IaC your AWS Organization set up and SCPs, then check out org-formation. It lets you use a CloudFormation-like syntax to configure all that, plus creating new accounts, password policies, etc.
github.com/org-formation/…
If you want to IaC your AWS Organization set up and SCPs, then check out org-formation. It lets you use a CloudFormation-like syntax to configure all that, plus creating new accounts, password policies, etc.
github.com/org-formation/…
For example, this is setting up the password policy and SCPs at the root of my AWS Organization
Can't stress how powerful this tool is. You should definitely go check it out! Kudos to @OConijn for such amazing work 👏👏👏


Can't stress how powerful this tool is. You should definitely go check it out! Kudos to @OConijn for such amazing work 👏👏👏



"We all know developers who like to work in the middle of the night. And you want to allow them to do that and let them manage permissions." - so that's why they created permission boundaries! 🤔😂 

mm.. IAM Access Analyzer sounds pretty cool, been meaning to try it out since it was announced at the last re:Invent, especially since it's a free service, and now it even supports AWS Organizations 



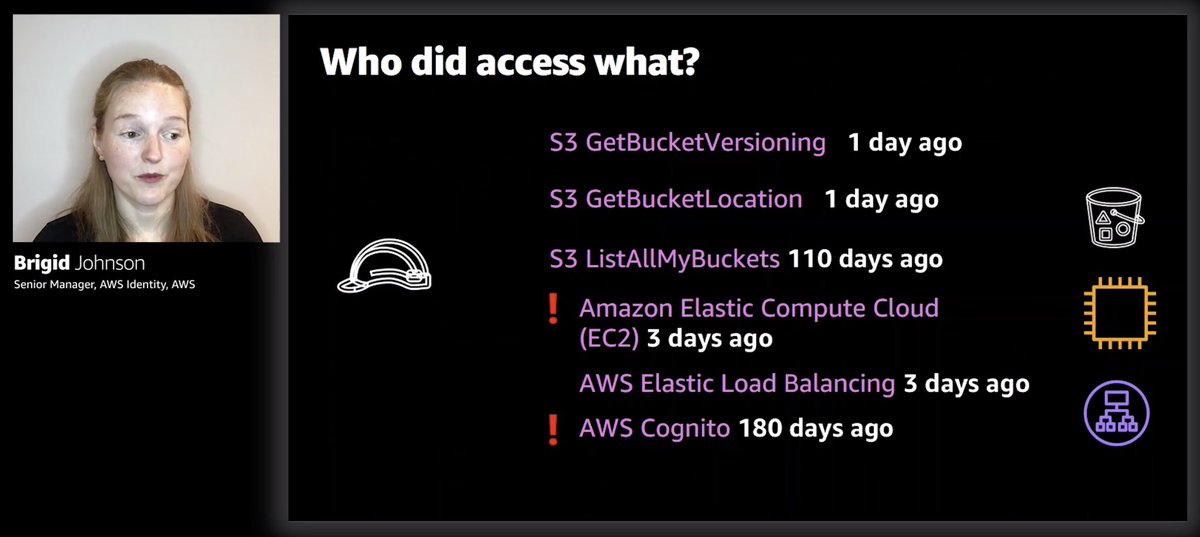
Use last accessed info to remove unused roles and unused permissions from roles 👍
I guess you can (and probably want to!) automate this with Lambda.
ps. who's Marie Kondo?

I guess you can (and probably want to!) automate this with Lambda.
ps. who's Marie Kondo?

Lastly, Brigid talks about ABAC.
In principle, I think ABAC is a great idea, but there're still a lot of gaps in the services that support it.
This post is still very relevant: summitroute.com/blog/2020/11/0…

In principle, I think ABAC is a great idea, but there're still a lot of gaps in the services that support it.
This post is still very relevant: summitroute.com/blog/2020/11/0…


Thank you @bjohnso5y great session as always 👏 

• • •
Missing some Tweet in this thread? You can try to
force a refresh