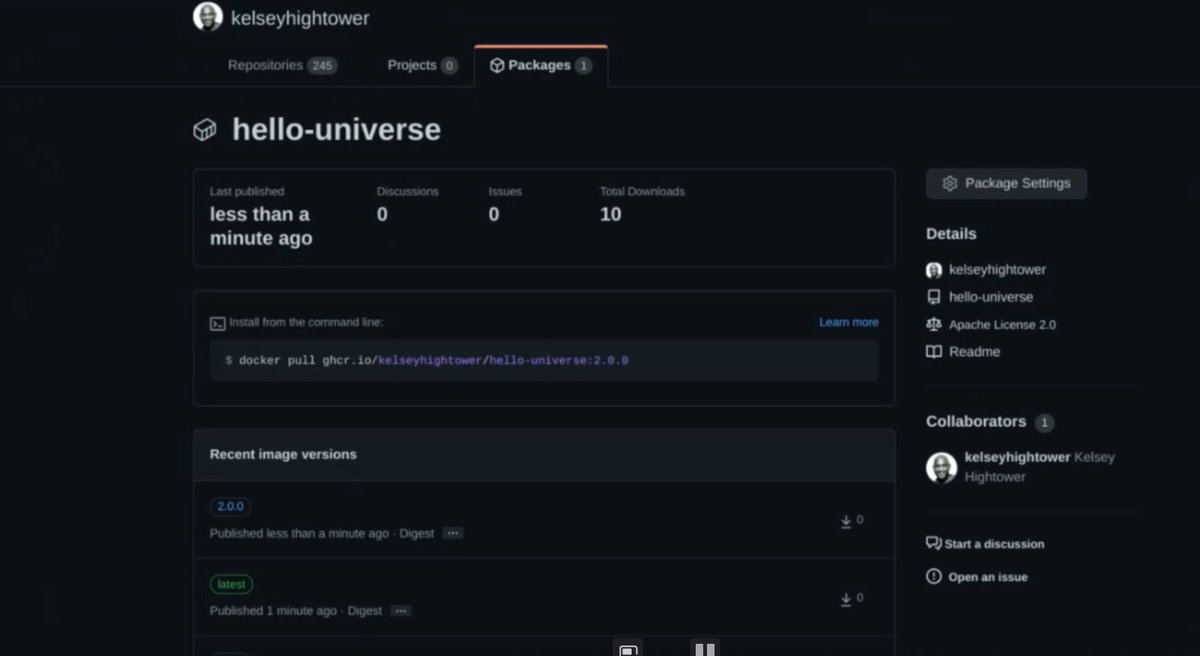
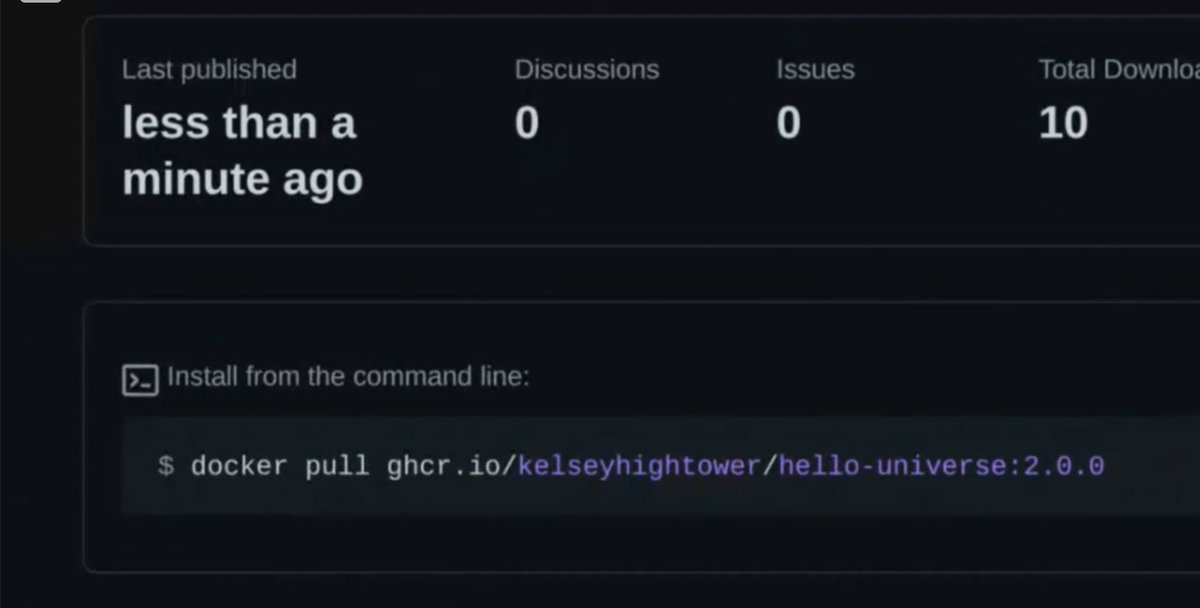
The app config contains Kubernetes manifests used to deploy to the published artifact the target Kubernetes clusters. 



Using config-sync, the config is pulled into the Kubernetes cluster leveraging GH branches to deploy across clusters. Using nomos, Kelsey checks the config status on the clusters 



Pushed v2 to the repo which published a new container which bumps the deployment manifest to the v2 container. That is then rolled out to a canary cluster attached to a canary LB. 


• • •
Missing some Tweet in this thread? You can try to
force a refresh