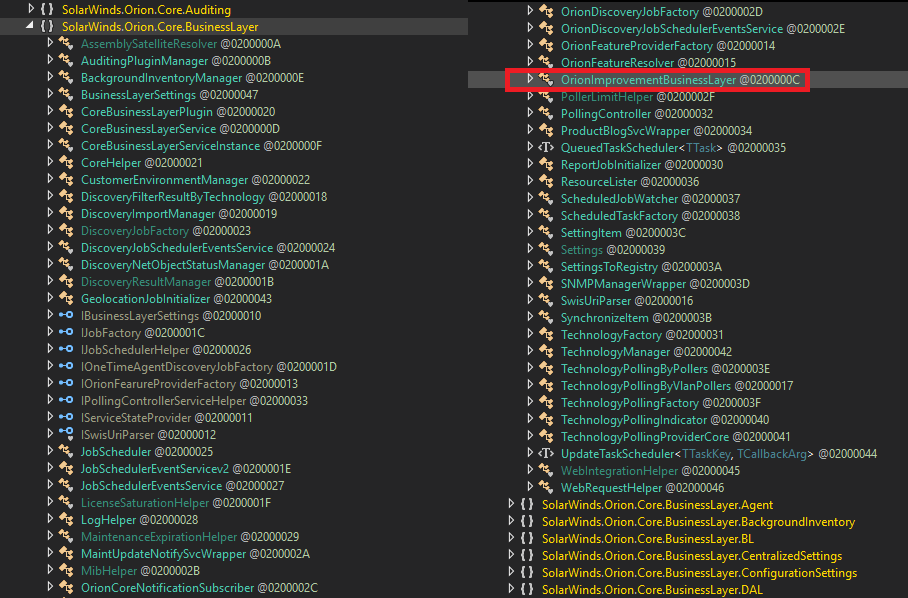
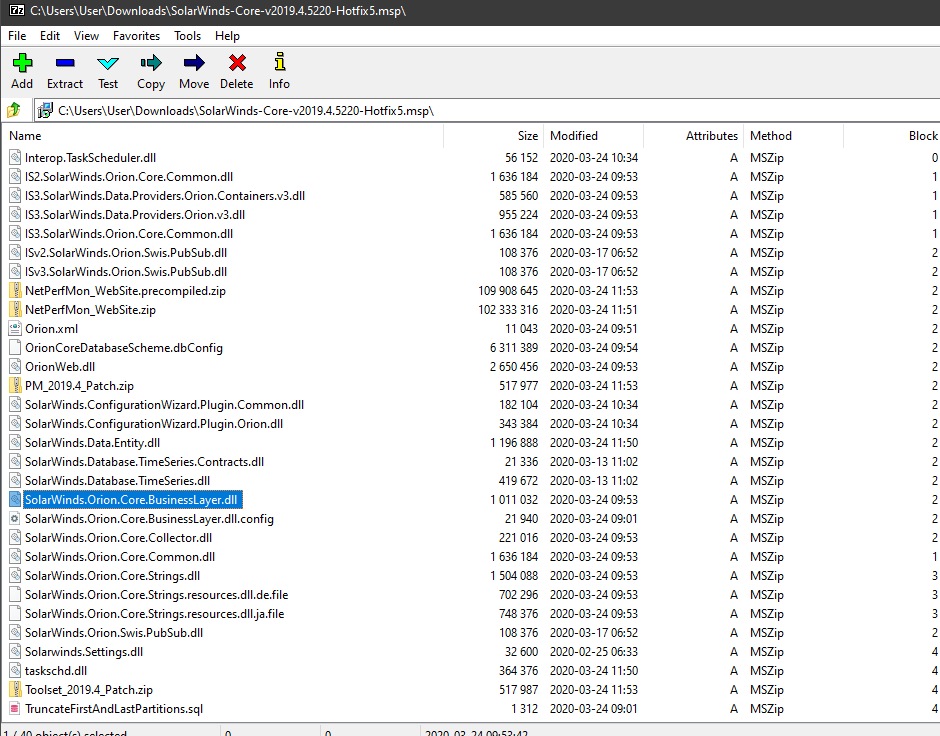
Was just shown the SolarWinds.Orion.Core.BusinessLayer.dll is included in n-Central's Probe installer by @KelvinTegelaar. WindowsProbeSetup.exe is signed by the same certificate. However the DLL backdoored with #SUNBURST is not signed and appears to be a 2014 version. #Looking 

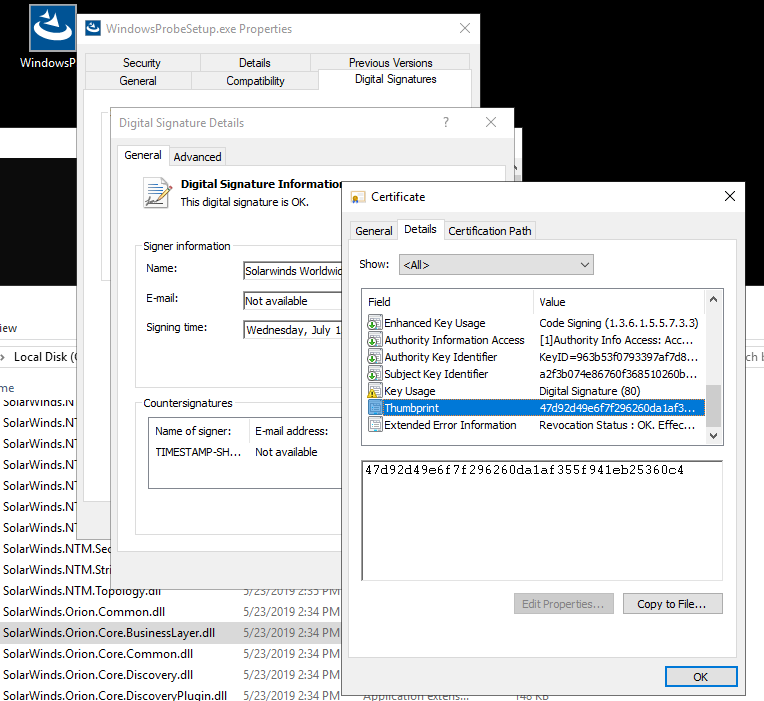

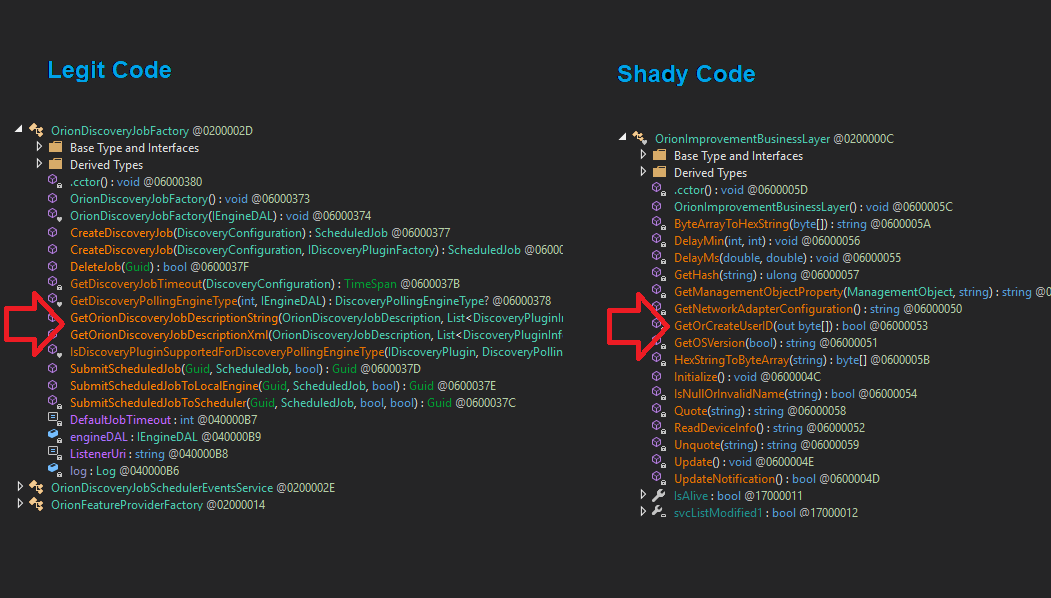
The unsigned SolarWinds.Orion.Core.BusinessLayer.dll binary from my copy of the Windows probe installer had hash B9CE678F9DAF32C526211EDEA88B5EC104538C75FAD13767EA44309E9F81DBFC. No OrionImprovementBusinessLayer class within this version (comparison screens attached). 



The default installation directory for this binary is "C:\Program Files (x86)\N-able Technologies\Windows Software Probe\bin". Going to have the team do a quick survey across all hosts to see if anything shakes up. Will report back what we find (hoping nothing 😅) 

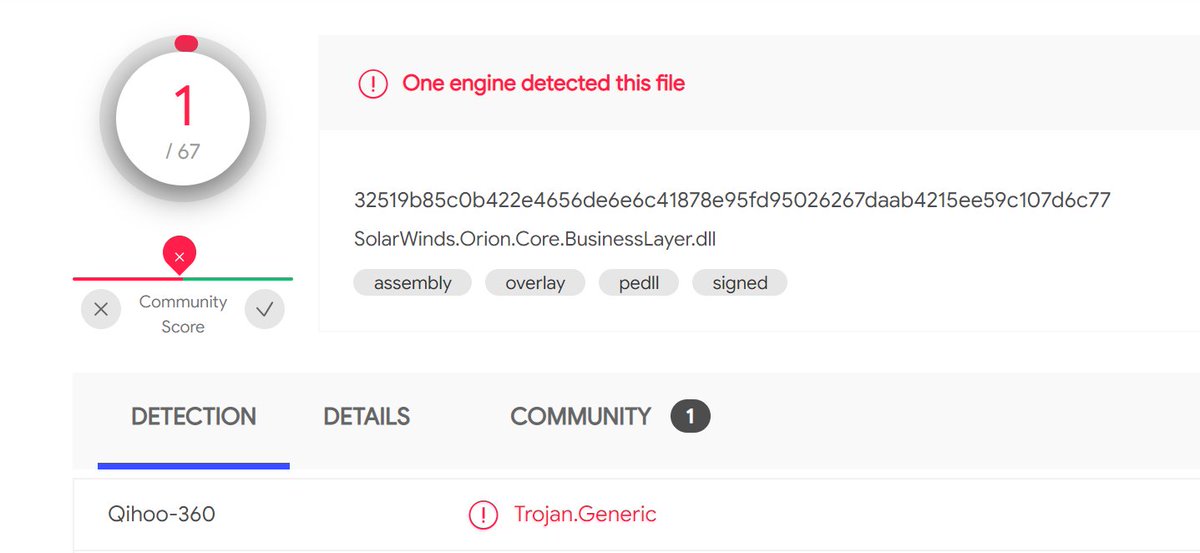
Found another unsigned version of SolarWinds.Orion.Core.BusinessLayer.dll out there. Confirmed there is not an OrionImprovementBusinessLayer class within this version. virustotal.com/gui/file/b9ce6… 



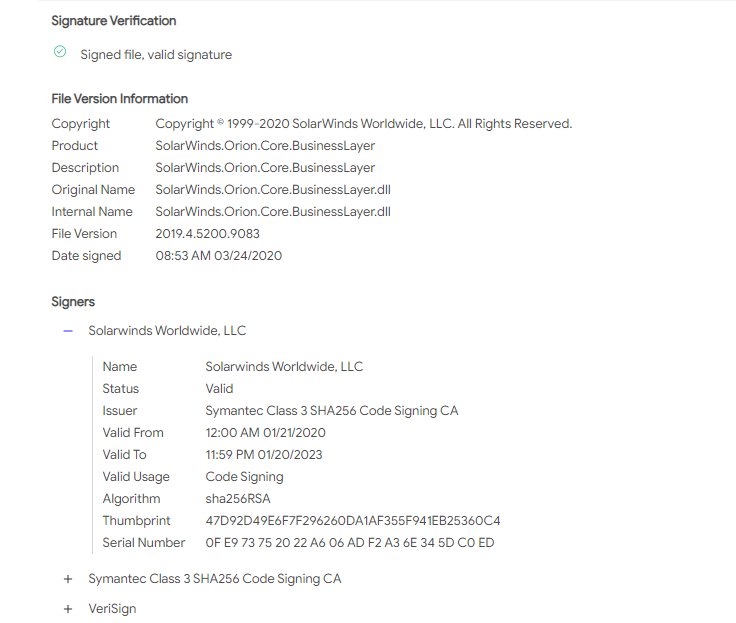
.@cannedmanatee found a SolarWinds.Orion.Core.BusinessLayer.dll signed August 11, 2020 5:41:59 AM that I confirmed doesn't have the OrionImprovementBusinessLayer class. Might provide timeline insight if the SolarWinds CI/CD pipeline was pwned. virustotal.com/gui/file/b9ce6… 





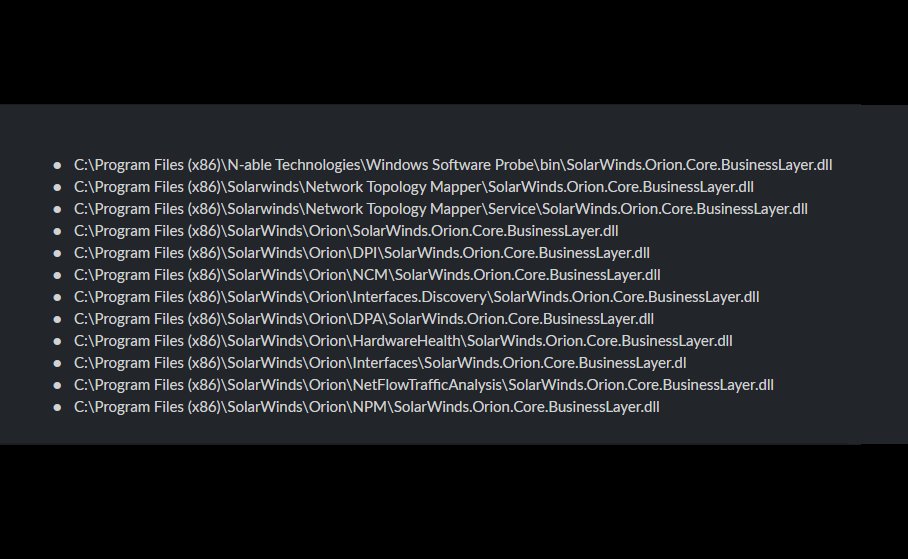
I've had a bunch of requests for path information on SolarWinds.Orion.Core.BusinessLayer.dll. TL;DR - it can be in a boat load of locations. Thankfully, my team and fellow security junky/MSP hero @_mbmy has put together a great list of places to check: gist.github.com/KyleHanslovan/… 
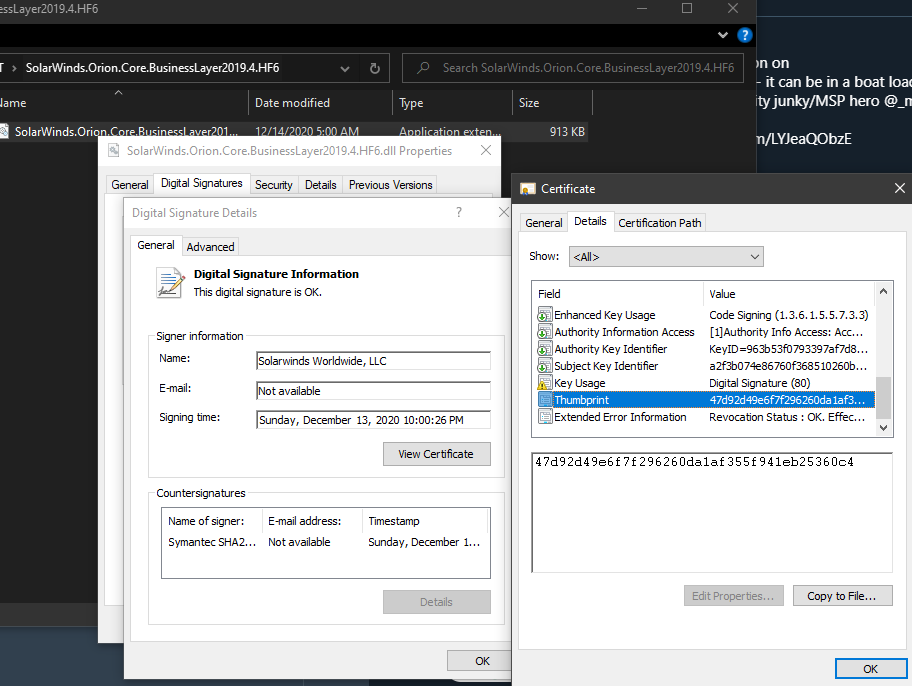
Was notified by @alex4652 the 2019.4 Hotfix 6 DLL is 1/70 in VirusTotal. After analyzing the binary, I've confirmed there is no OrionImprovementBusinessLayer class present and is likely a @Webroot false positive. Still signing w/47D92... cert thumbprint. virustotal.com/gui/file/8dfe6… 




• • •
Missing some Tweet in this thread? You can try to
force a refresh