If you cannot see the wood for the trees ...
Me talking bullshit (without anybody noticing it).
This thread does not describe an issue caused by cert pinning, but by not running the interception proxy in "transparent" mode.
1/2
Me talking bullshit (without anybody noticing it).
This thread does not describe an issue caused by cert pinning, but by not running the interception proxy in "transparent" mode.
1/2
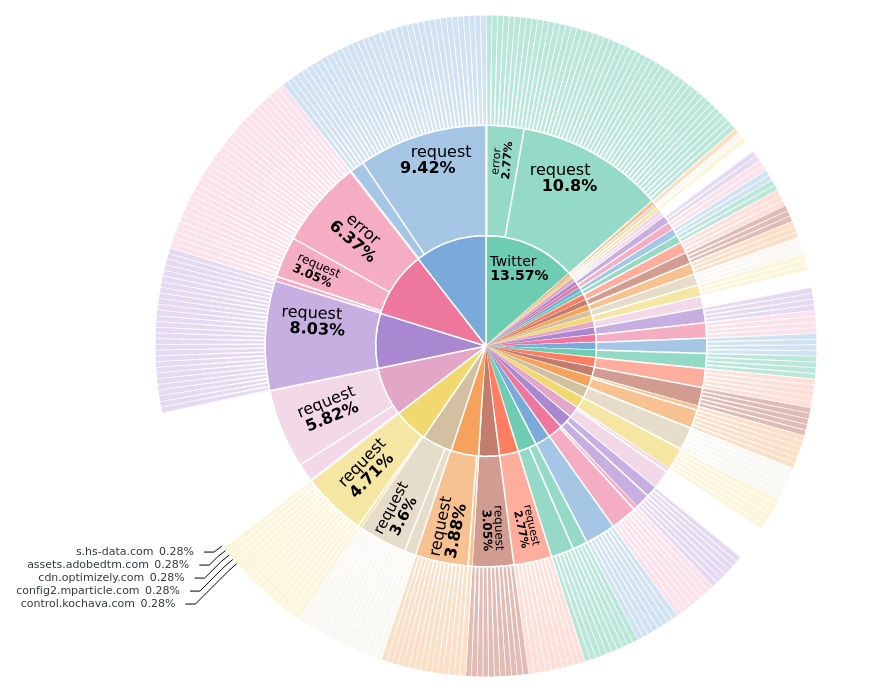
https://twitter.com/mame82/status/1339542553855741952
The real problem is actually highlighted in the example linked above.
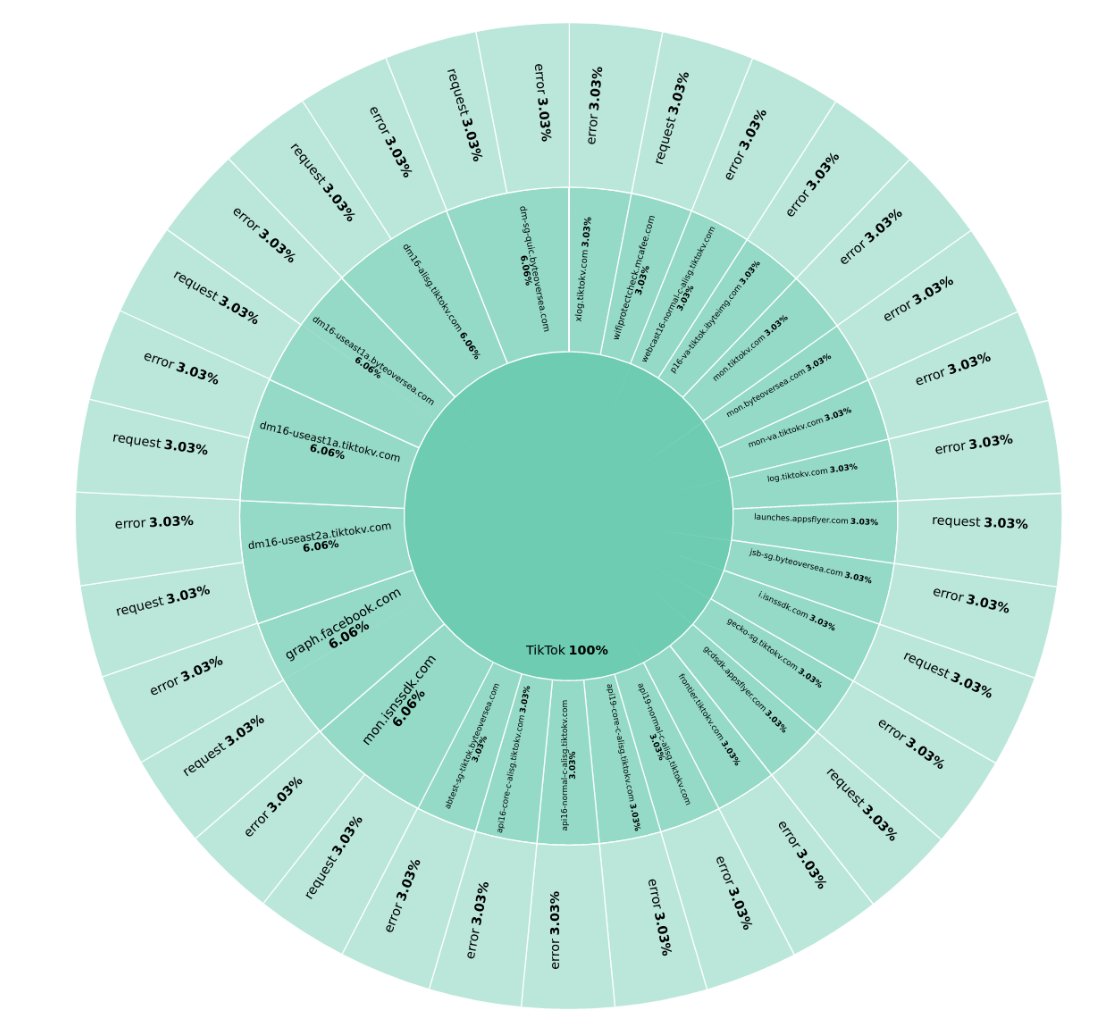
I tried to "unpin" CONNECT requests (not POST/GET/DELETE etc), which occur because my proxy is visible. Of course TikTok wants to establish a raw tunnel through the proxy with CONNECT.
... time for a break
I tried to "unpin" CONNECT requests (not POST/GET/DELETE etc), which occur because my proxy is visible. Of course TikTok wants to establish a raw tunnel through the proxy with CONNECT.
... time for a break
Only failed connections within 24 hours, which used valid HTTP request methods are directed towards the invalid host 'shgw.router' (sent from McAfee Security) 

• • •
Missing some Tweet in this thread? You can try to
force a refresh