
A threat of thoughts + actionable detection ideas from the latest Microsoft #Solorigate post...microsoft.com/security/blog/… ... this is a sweet diagram and hopefully helps make clear the different ways you could be impacted. Not every victim makes it past initial C2. 

THIS IS THE MEATY STUFF. HANDS ON KEYBOARD ATTACK. Fewer victims got this far from public reporting. Renamed adfind could be a good hunt/detection opportunity. Hunt for/detect on adfind anyway because of ransomware operators. 

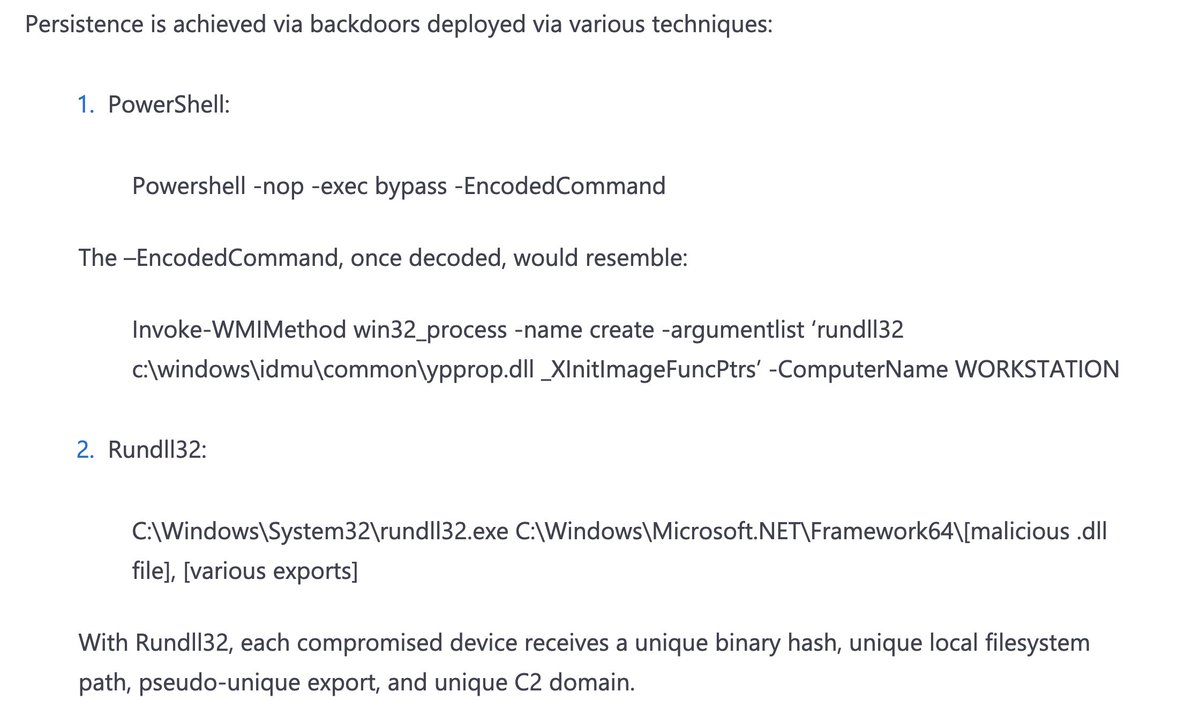
This is also super-actionable for detection and hunting. Encoded PowerShell and rundll32 are excellent opportunities. As always (and with everything in this blog post and everything in general), it might need tuning. 
Several good ideas here on what MS detects. Could be noisy, but worth looking into in your environment. They give you a nice screenshot to provide a process tree to help, too. This list tells us hunting/detecting in ADFS is important. 

Moar hashes. Yeah, go search for them. Some of these have been in previous reports too, some might be new. Not all are in VT from my searches. 

These are nifty hunting and detection ideas too. Remember, just because MS gives these in their language doesn't mean you can't convert the concepts to whatever you use. 

I think we've seen this domain a zillion times by now, but maybe these queries would help you refine searches a bit. 

Based on the file name, pretty sure this is describing what FireEye calls SUPERNOVA. (fireeye.com/blog/threat-re…) 

I hope my brain dump helped you try to make sense of this Friday evening info. A little new, but most this has been seen in reporting earlier this week from my perspective. If you see new nuggets and actionable detection/hunting ideas, please reply!
Important thing a friend pointed out - it appears MS is assessing that this persistence backdoor is LIKELY unrelated to this compromise and used by a different threat actor. This is the FireEye source mentioning the same file name, labeled as SUPERNOVA (github.com/fireeye/sunbur…). 

Hahaha. *Thread 😂😂 I just noticed.
• • •
Missing some Tweet in this thread? You can try to
force a refresh












