Microsoft has technical article on SolarWinds hack. microsoft.com/security/blog/… The few innocuous-looking lines in red box are the very lightweight link to malware code. Hard to see anything distinctively CosyBear or Russian in these lines. Maybe attribution is something else. 
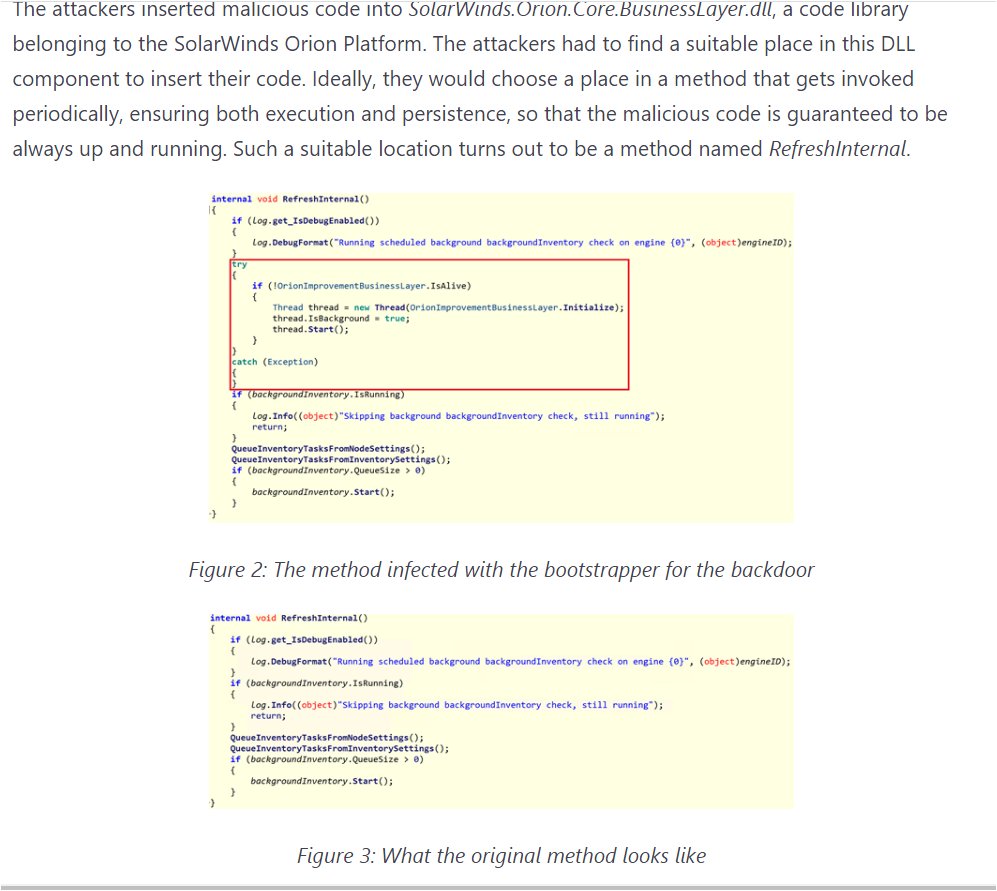
2/ Microsoft observed that the backdoor functionality is invoked by a seemingly innocuous operation Initialize() for OrionImprovementBusinessLayer. 
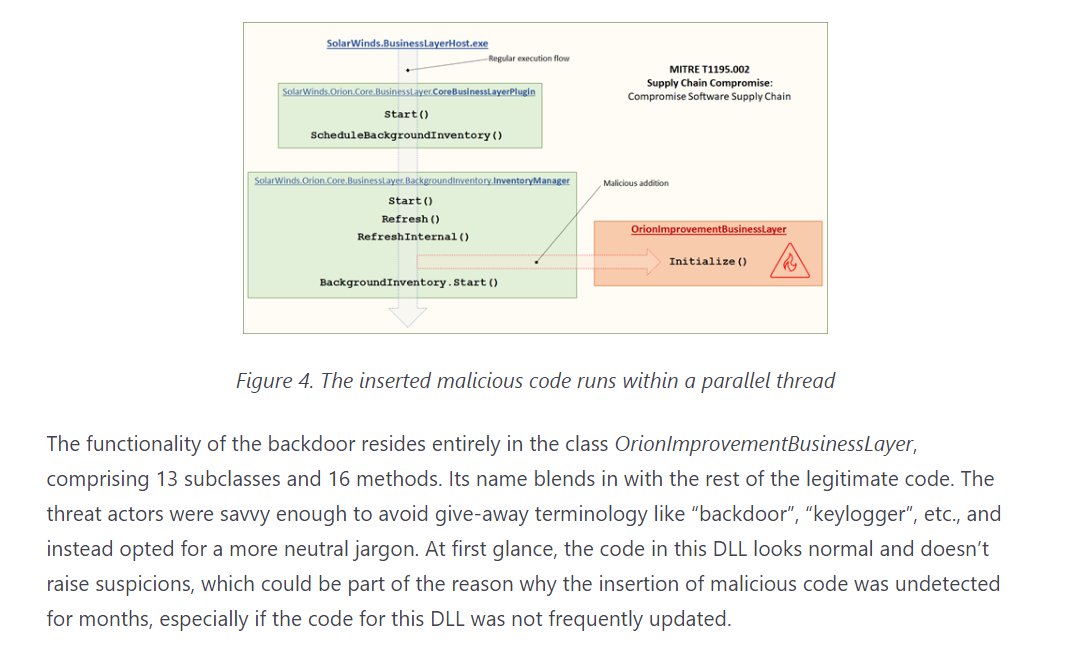
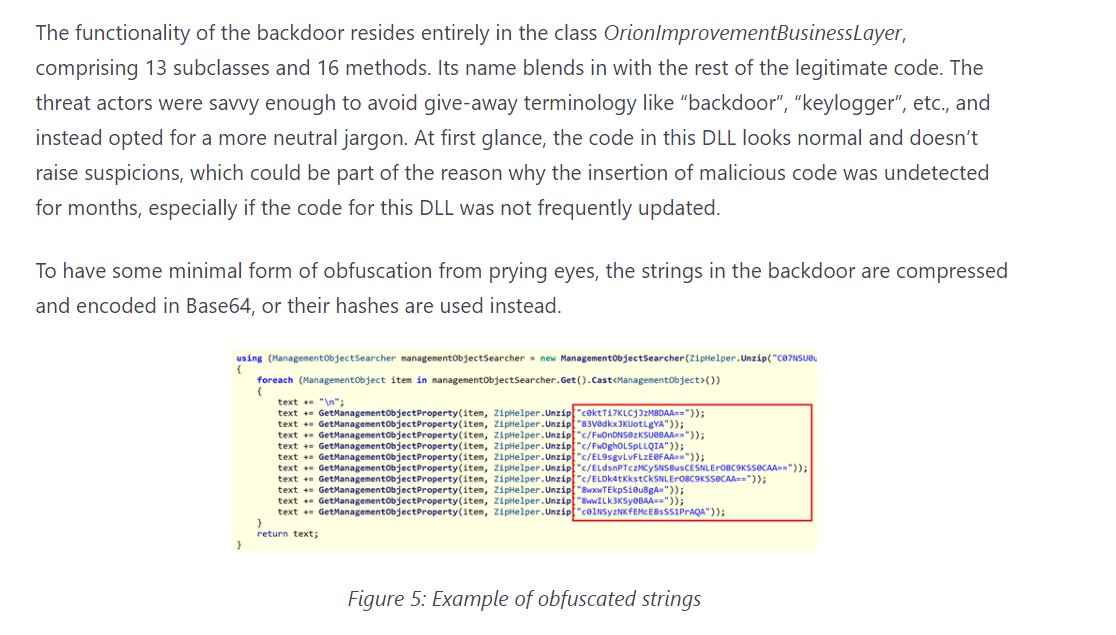
3/ Microsoft said that the "business" end of the hack resides in various subroutines with Base64 encrypted file calls. 
4/ this is completely different from things like grabbing Podesta emails through password theft from a phishing email. Whoever did this had access to the source code in software development. No explanation thus far on how they exclude US-based criminals as suspect class.
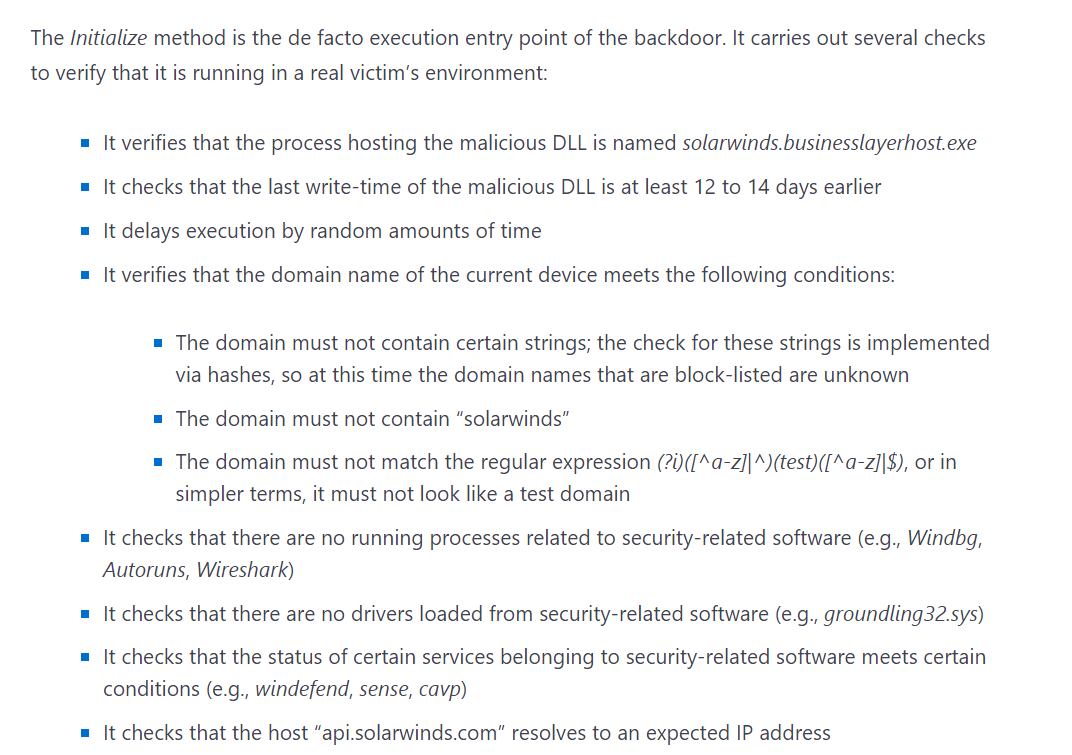
5/ proceeding thru interesting article, they say that malware checks to see that process is not operating in sandbox or has been suspected. 
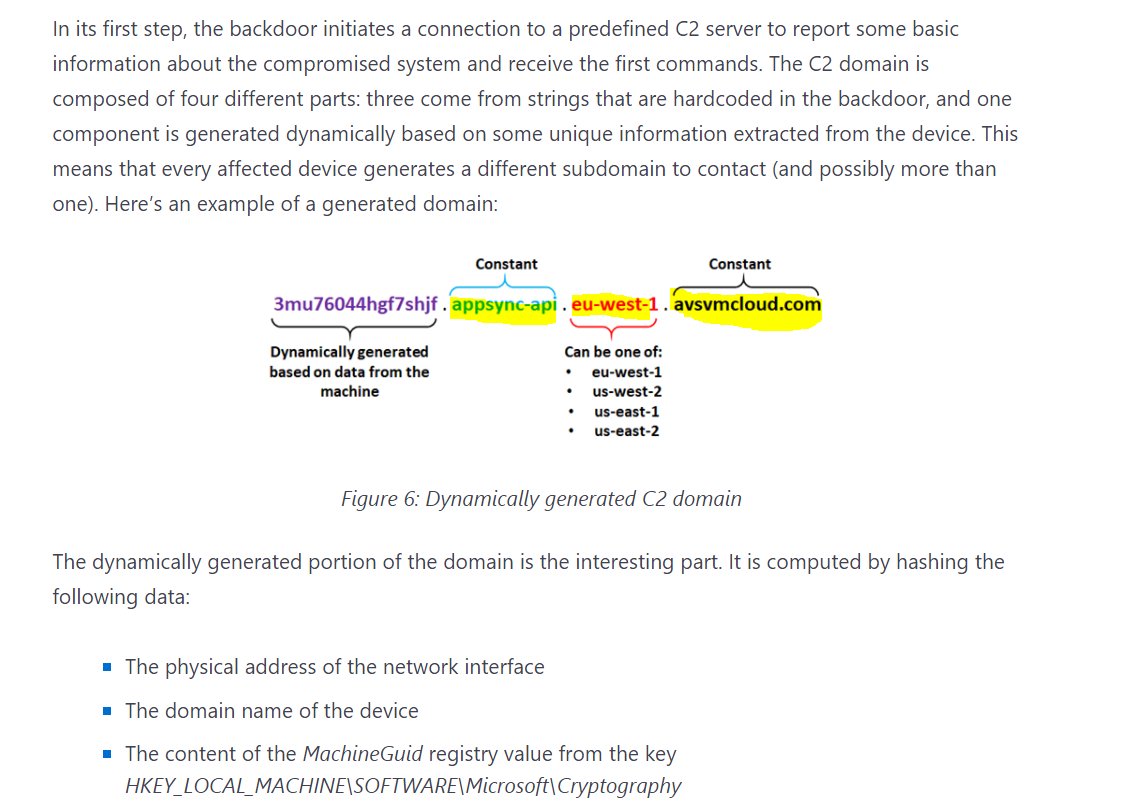
6/ to communicate, malware communicates with unique subdomain of avsvmcloud[.]com - a domain mentioned right at beginning. This domain located in US; nameservers have been GoDaddy and Microsoft. 
7/ after contact established, Microsoft says that hackers follow "standard processes" for escalation of privileges. 
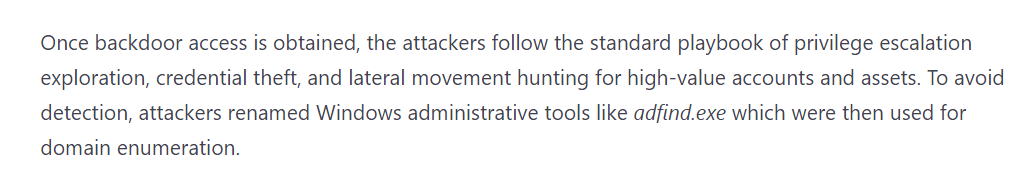
8/ C2 domain was sandboxed on Dec 13. But prior to that C2 domain avsvmcloud[.]com had been hosted on Microsoft itself since Apr 23, 2020 and before that on GoDaddy, neither of which are obvious indicia of a Russian APT. 
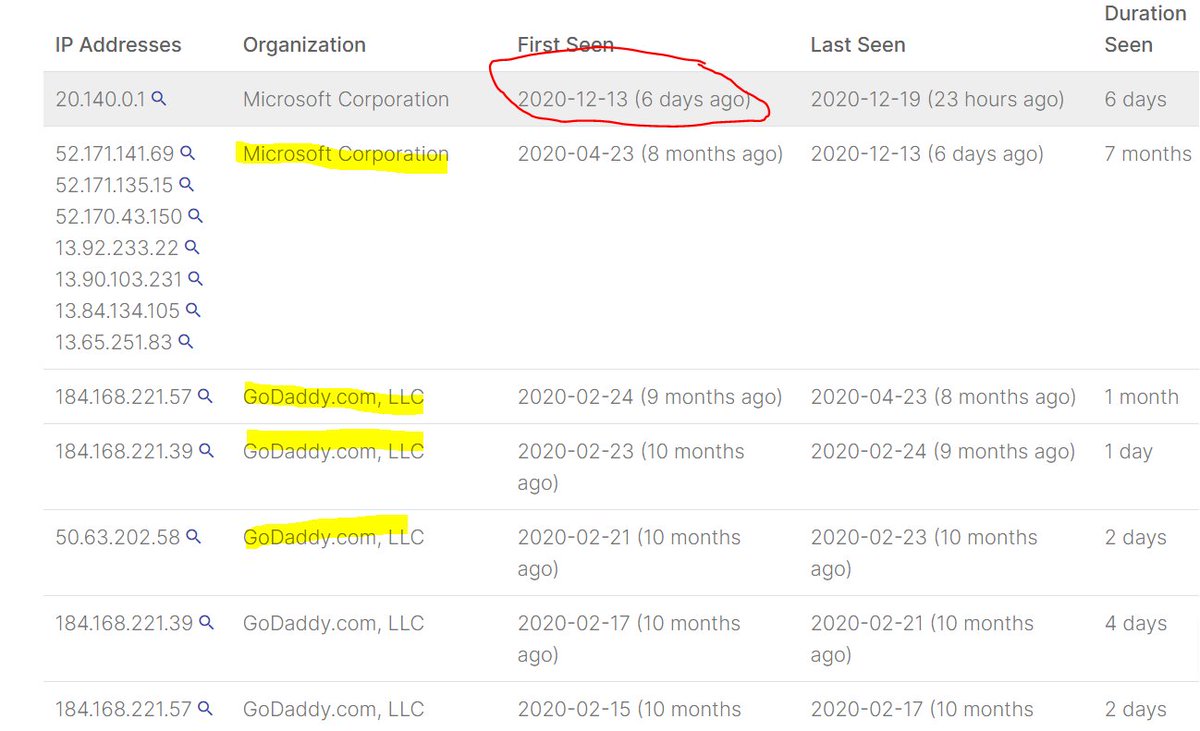
9/ nameserver presumably taken over on Dec 13 as part of sandboxing. Prior to that Microsoft, GoDaddy had provided domains to avsm as its own nameserver. 
10/ excellent article by Volexity last week. They had previously noticed activity by SolarWinds hacker, who they named Dark Halo. They gave several C2 domains and IP addresses, none of which yielded attribution so far. Cited at otx.alienvault.com/pulse/5fd83177… See volexity.com/blog/2020/12/1…
• • •
Missing some Tweet in this thread? You can try to
force a refresh