Are you looking for cleaning services in Riyadh? Don't worry, there's a botnet for that. #SaturdaySpam
cc: @ZellaQuixote
cc: @ZellaQuixote

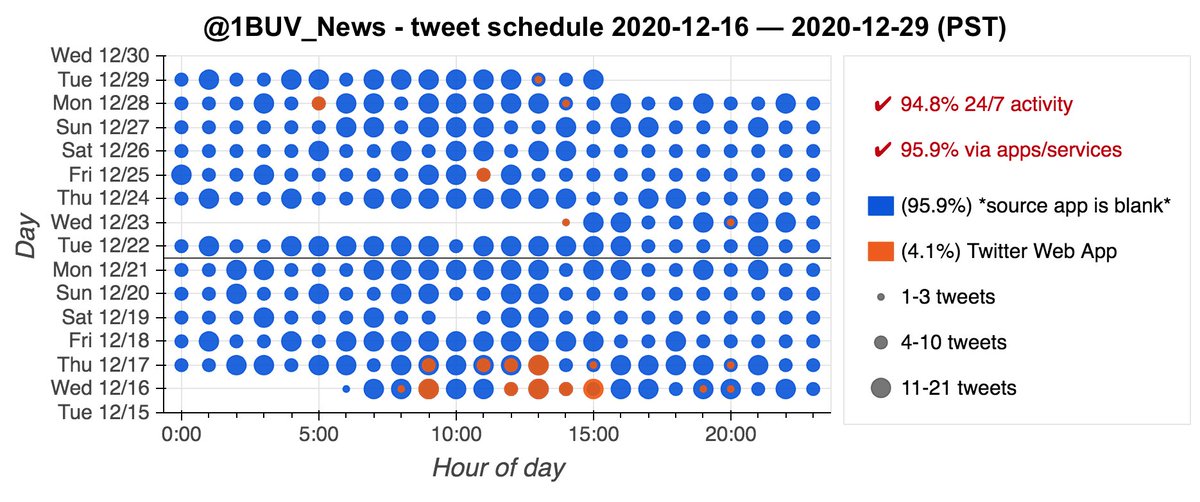
This botnet consists of 50 Arabic-language accounts, all created between December 18th, 2020 and January 1st, 2021. These accounts tend to all activate simultaneously and all (allegedly) tweet via the Twitter Web App. 


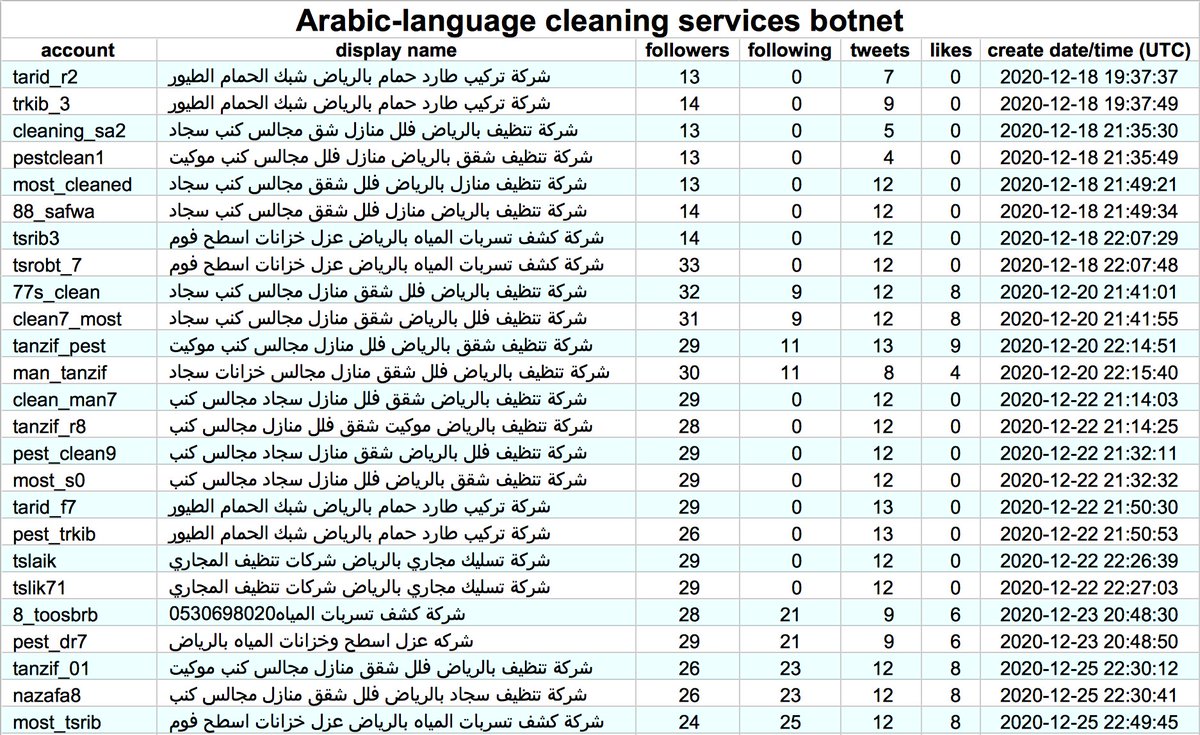
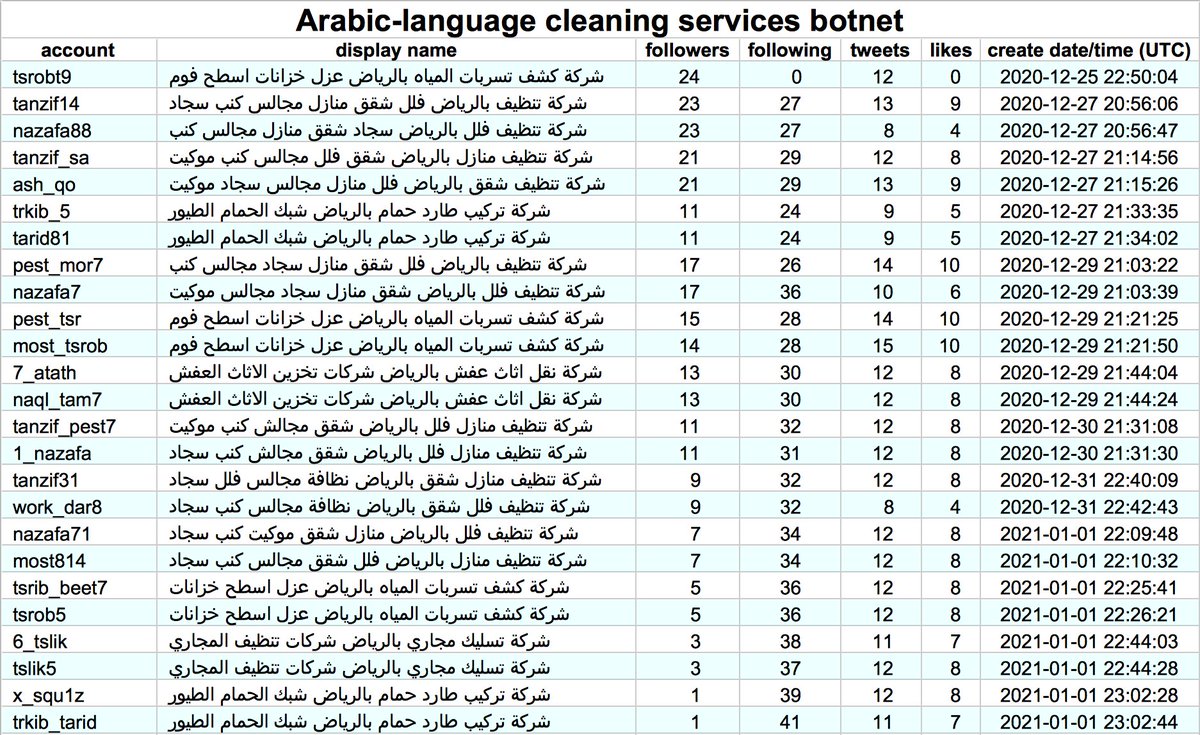

The accounts in this botnet follow other members of the botnet, and most of them follow several. The follow relationships are somewhat structured by account creation date, with the December 22nd and 23rd batches having the most follows from other bots in the network. 

The bots in this network are grouped into pairs created on the same day that exclusively retweet one another. There are a few cases where a bot retweeted a member of the network other than its "partner", and two (@cleaning_sa2 and @pestclean1) have yet to retweet anything. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh