GAN-generated profile pics (such as those produced by thispersondoesnotexist.com) have become quite popular among botnets promoting cryptocurrency blogs/websites. Here's a look at one such botnet that was mostly made just before Christmas. #HolidayShenaniGANs
cc: @ZellaQuixote
cc: @ZellaQuixote
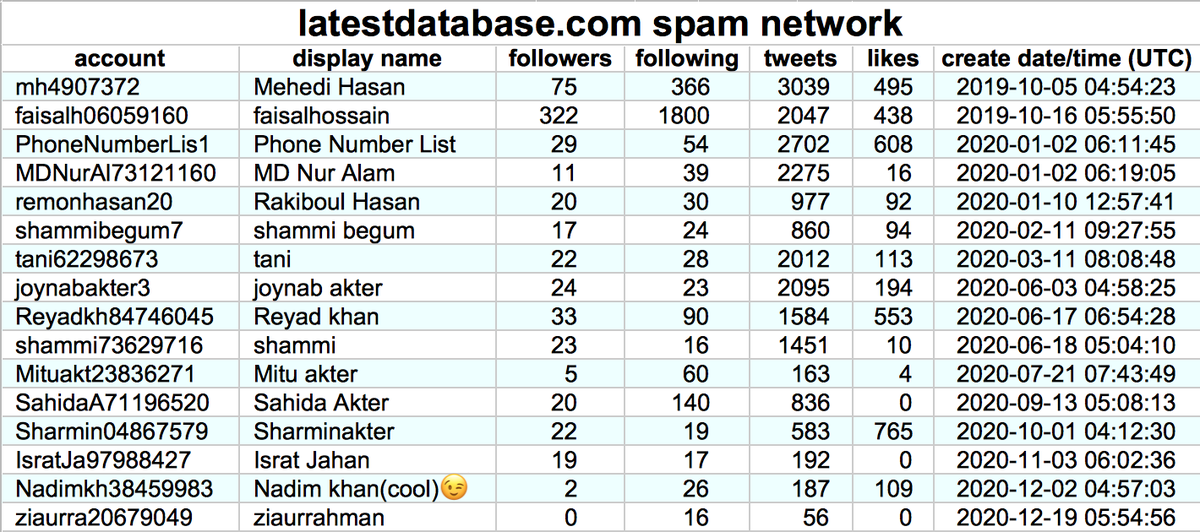
We found a group of 12 accounts with GAN-generated profile pics linking cryptocurrency-themed websites and blog posts. All but one of these accounts was created between December 22nd and 25th, 2020. 

Here are the profile pics of all 12 bots in the network. When overlaid, one can see that the major facial features (particularly the eyes) are in the same location on each image. The images contain other artifacts too: the metallic droplet on @SwiftAlene's forehead, for example. 

These accounts link to a variety of cryptocurrency/blockchain-themed websites and blogs, with the most common being blockgeeks(dot)com. Their tweets are repetitive (which isn't surprising, since they're mostly verbatim copies of article titles). 



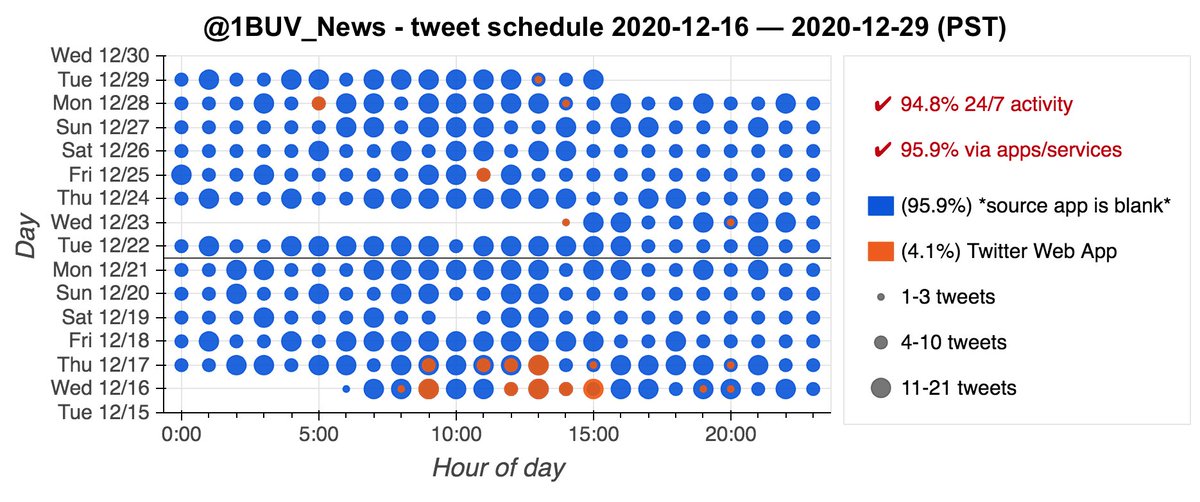
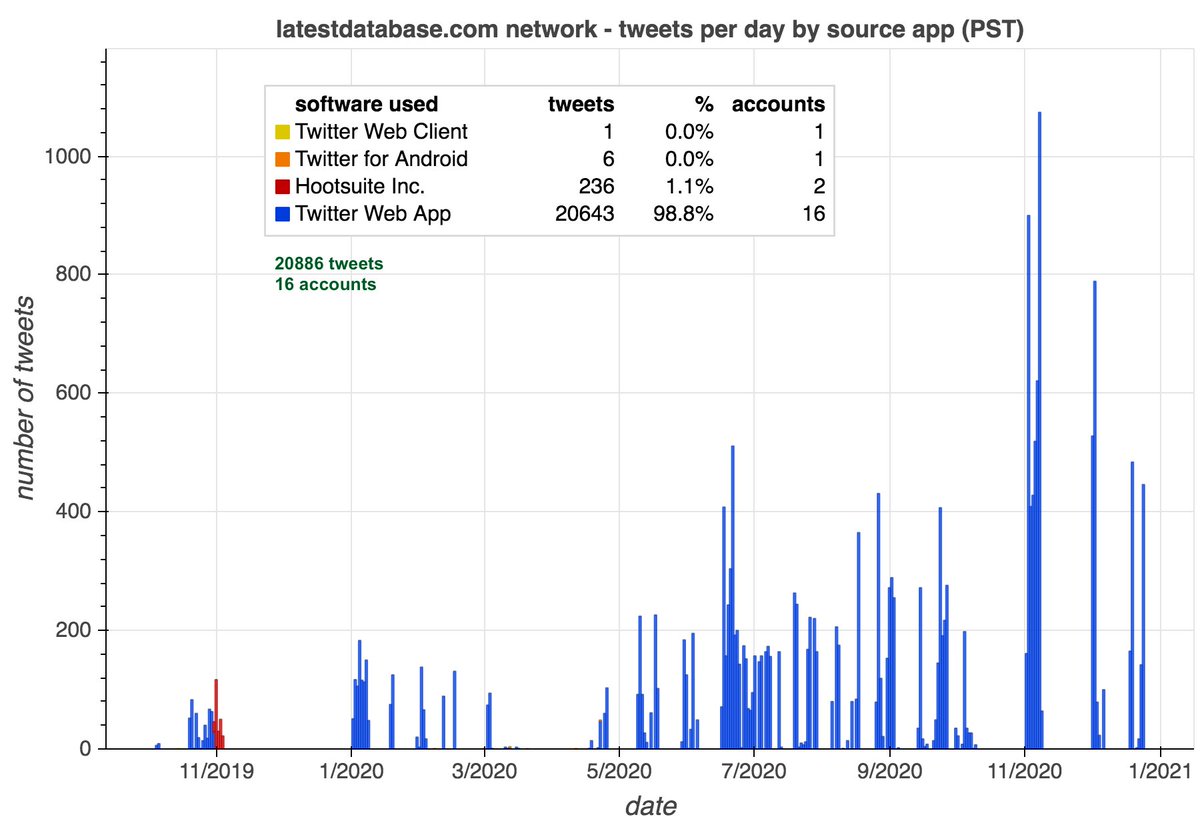
The majority of the tweets posted by these bots are sent via an app called Socialchief. The tweet schedule is quite regular: 6 batches of tweets per day, with the first posted at 1 AM Pacific time and subsequent batches posted at 2-hour intervals. 



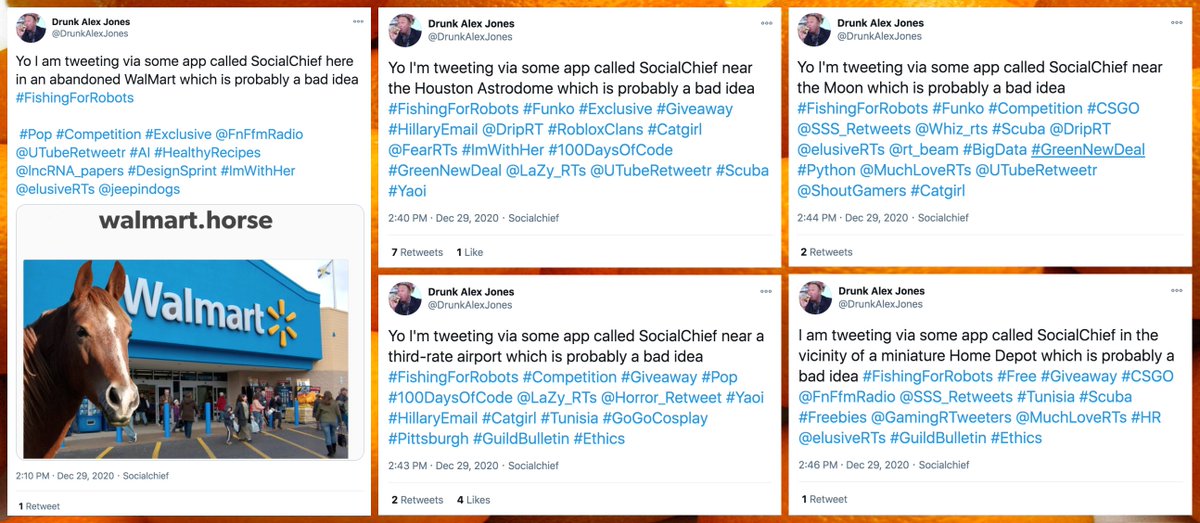
We enlisted @DrunkAlexJones to find out more about the Socialchief app. The app is a social media scheduling service for Twitter, Facebook, and LinkedIn. Its default behavior is to post six times a day at two hour intervals, which explains the botnet's schedule. 







Unlike most free tweet scheduling apps we've experimented with, Socialchief allows bulk scheduling of tweets via CSV import, which might be part of its appeal to the operators of the botnet we found. We had @DrunkAlexJones schedule a few tweets via CSV (results shown in collage). 




• • •
Missing some Tweet in this thread? You can try to
force a refresh