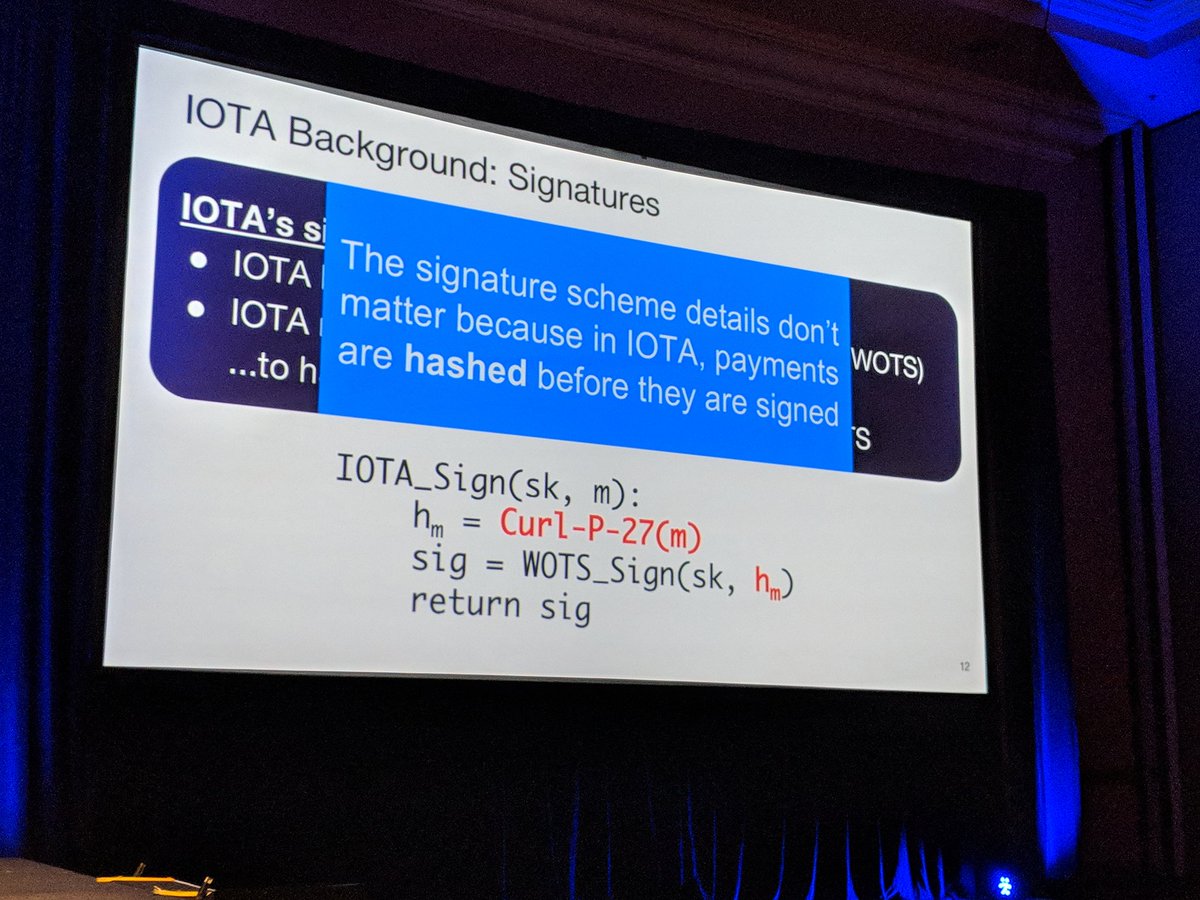
A: They are rotating at the same time.
Reliable time is handy like that.
#realworldcrypto
A: Not all, there are some requirements
#realworldcrypto
A: Those reports are considered outliers and are filtered out (?)
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
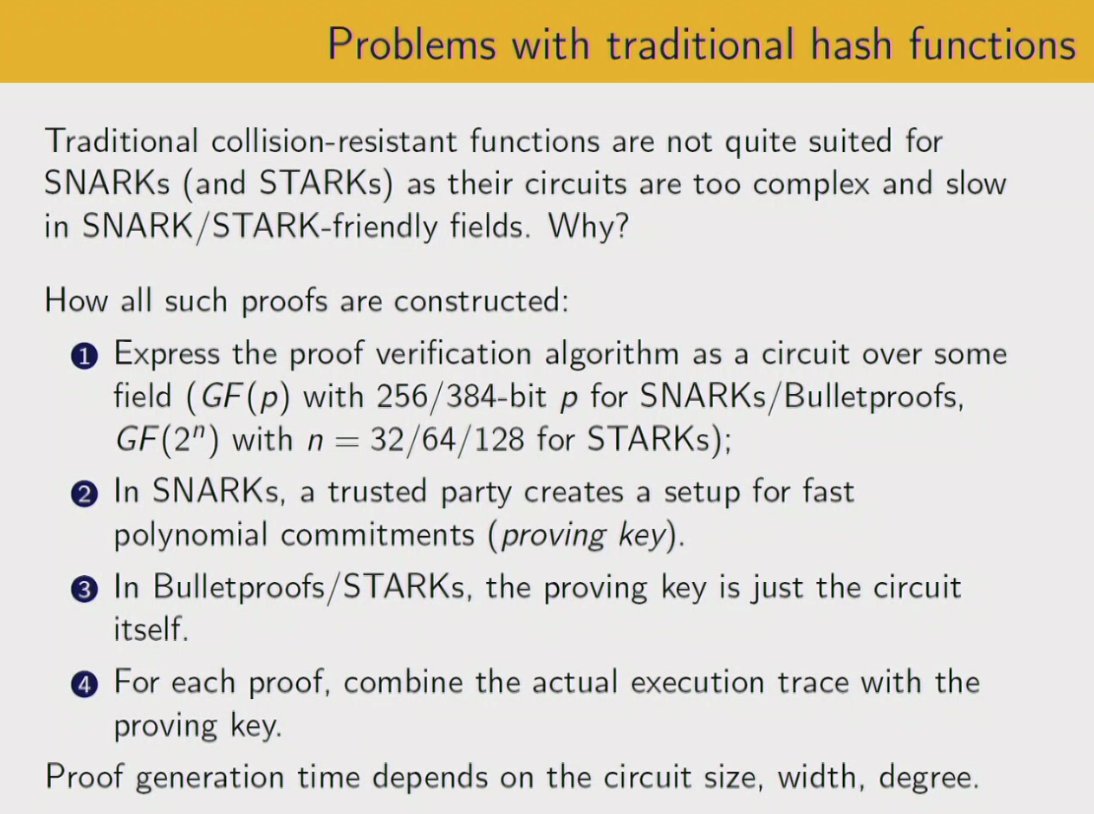
#realworldcrypto
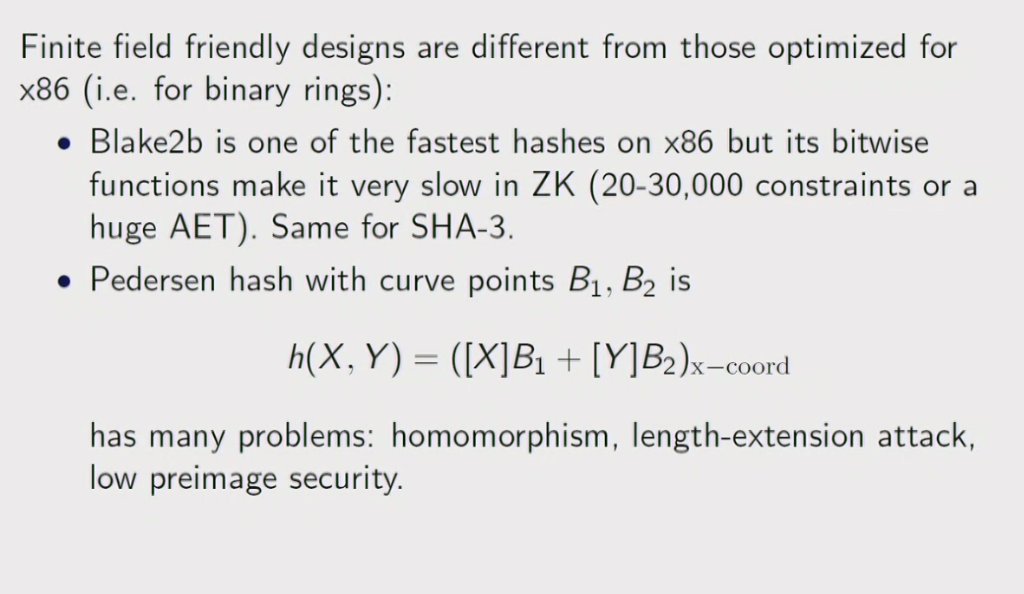
#realworldcrypto
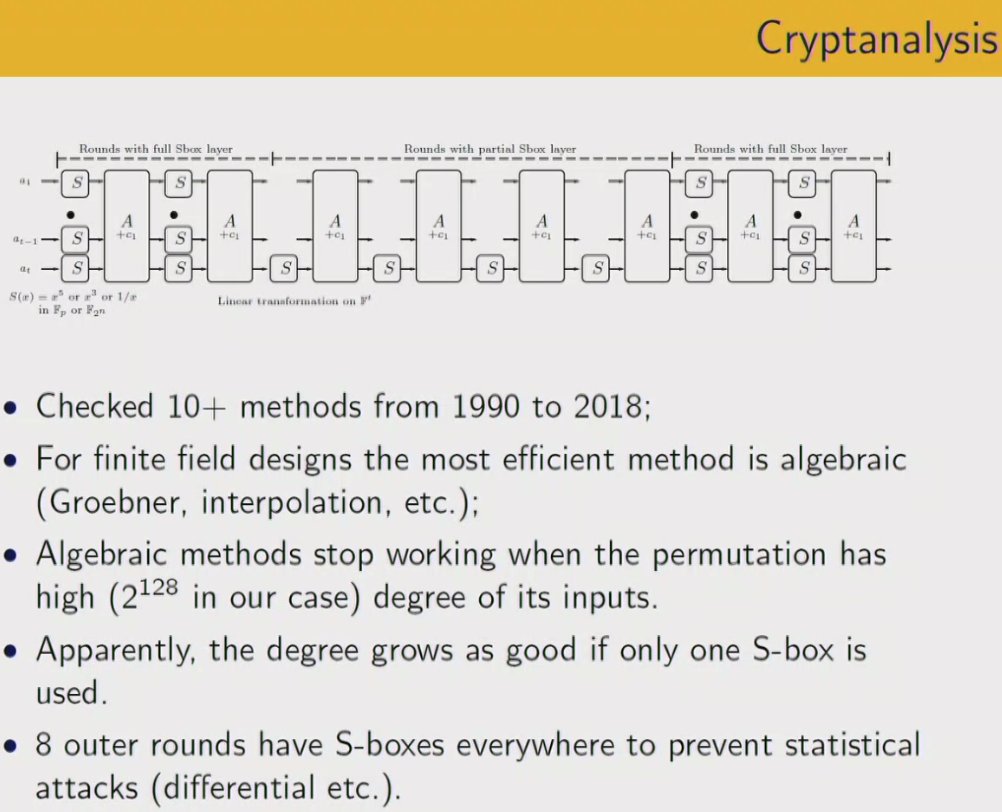
#realworldcrypto

#realworldcrypto
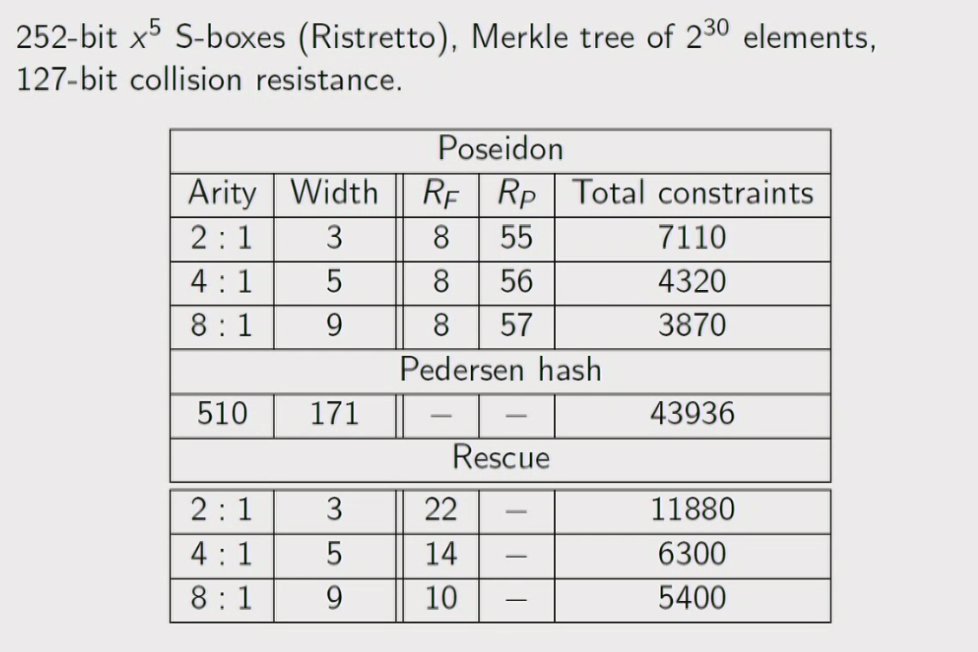
A: Didn't benchmark, got it from the Zcash spec 🦓
#realworldcrypto
#realworldcrypto
* maybe not in speed but in cost, space, etc
#realworldcrypto

More consistent security margins across primitives.
Better nomenclature for better understanding.
#realworldcrypto
A: Agreed. Also I'm not responsible for any damage as a result of this talk. 😆
#realworldcrypto
GIT GIT GIT
#realworldcrypto
#realworldcrypto
#realworldcrypto
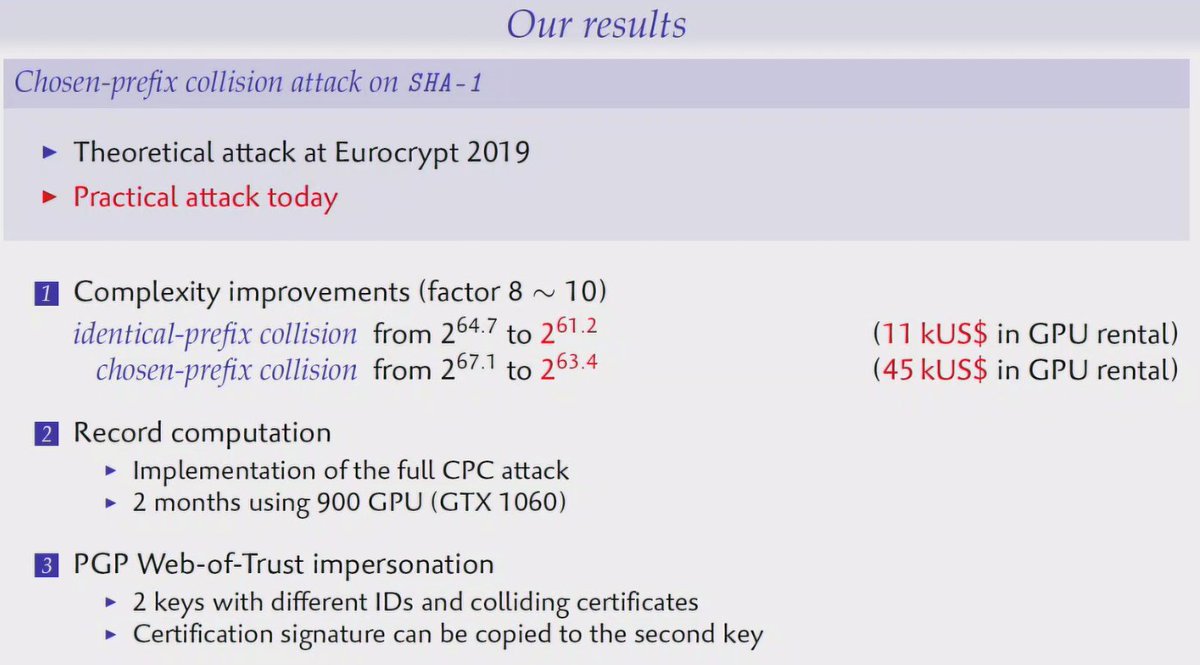
#realworldcrypto

#realworldcrypto
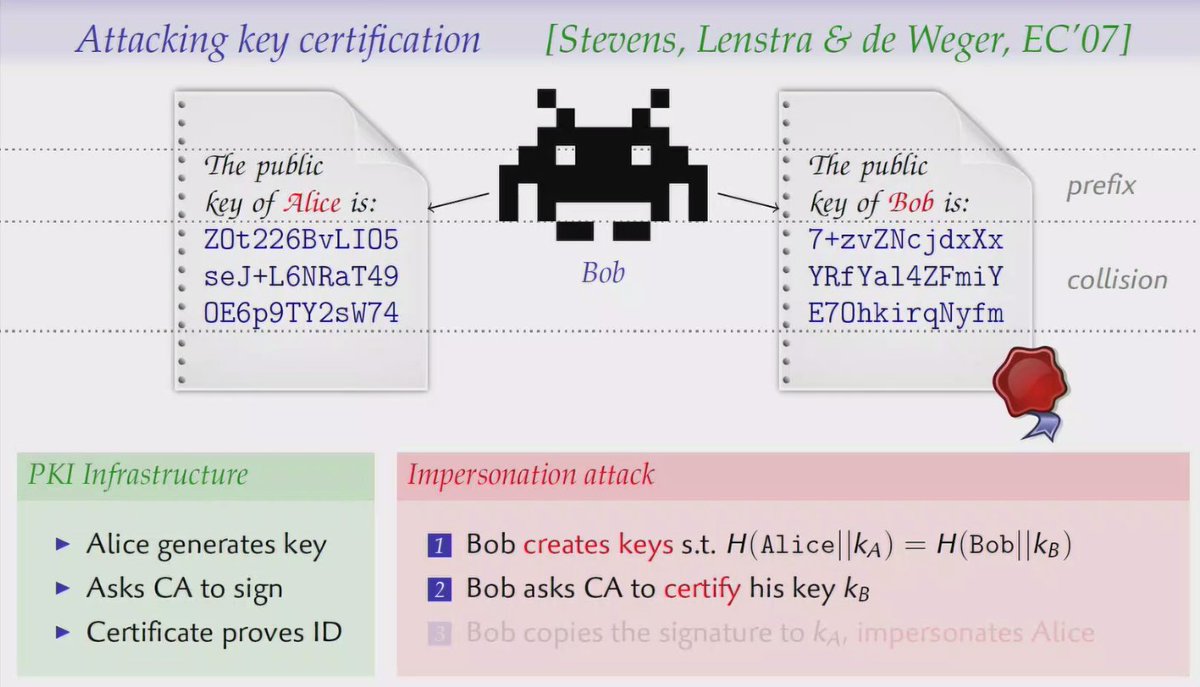
A: Correct no known attacks on HMAC, but why keep using SHA-1 there or anywhere else? I wouldn't recommend using HMAC-MD5 either.
// @SchmiegSophie
#realworldcrypto
github.com/freedomofpress…
sunder.readthedocs.io/en/latest/
#realworldcrypto
#realworldcrypto
#realworldcrypto
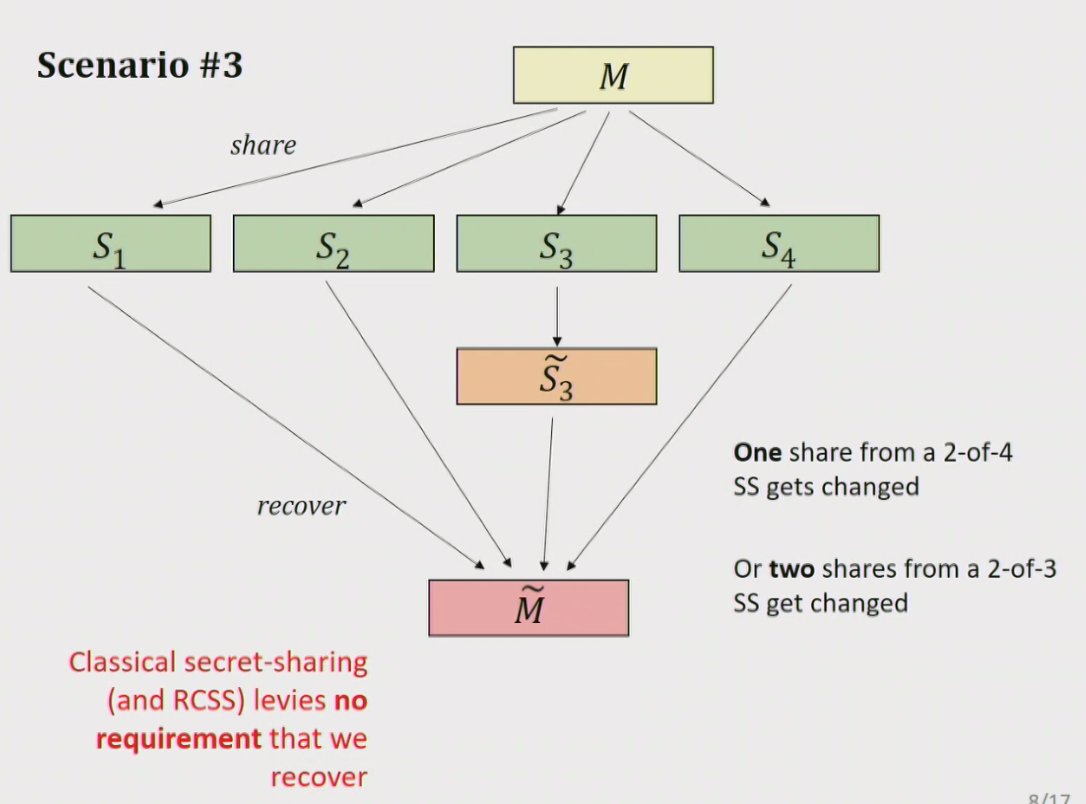
#realworldcrypto

#realworldcrypto
#realworldcrypto
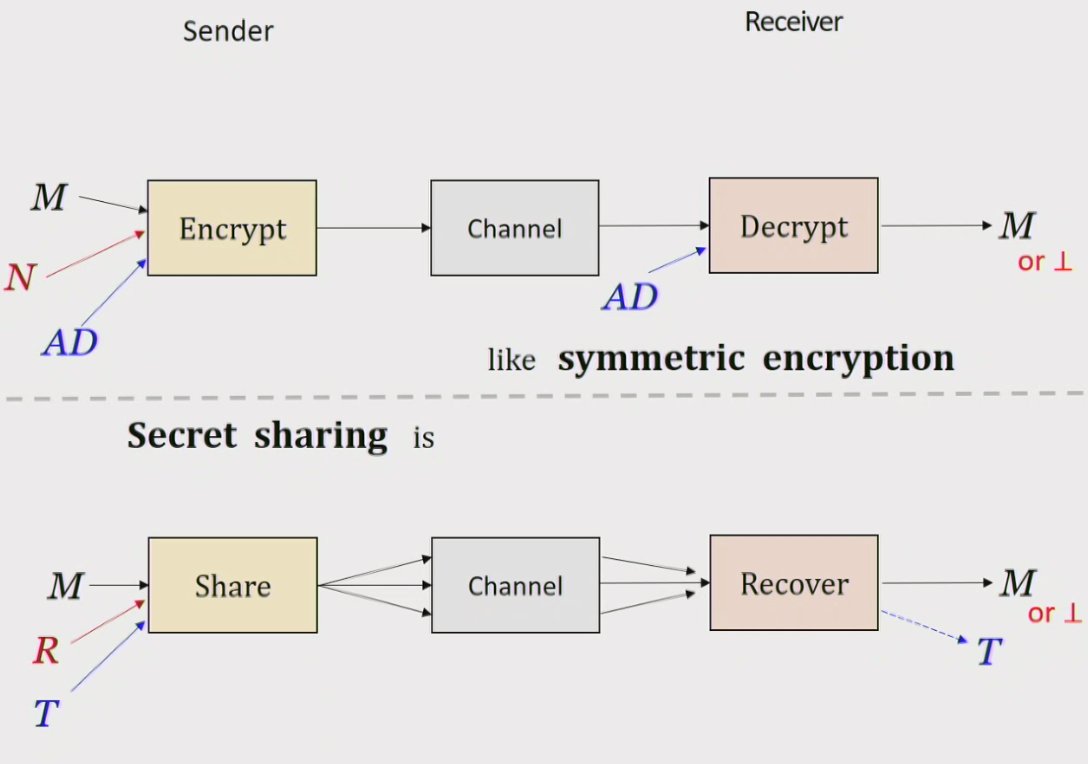
#realworldcrypto
#realworldcrypto
#realworldcrypto
github.com/BLAKE3-team/BL…
#realworldcrypto
github.com/str4d/rage
github.com/FiloSottile/age
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
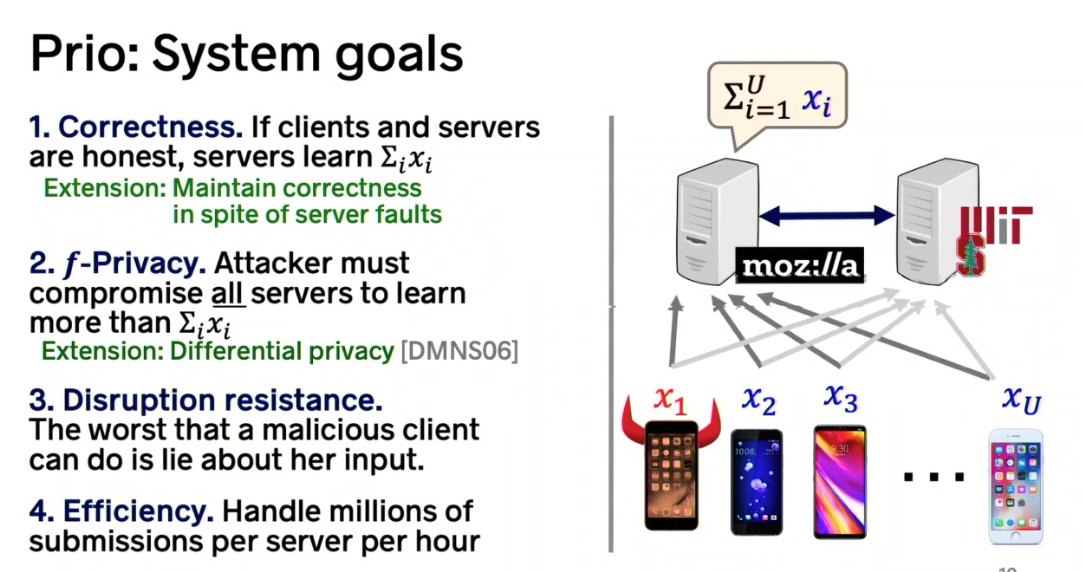
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
A: Server keys in the browser on the client.
#realworldcrypto
A: The variance grows with the square root of the number or reporters, and the noise will wash out the signal in the data
#realworldcrypto
A: Mozilla already has a system for the regular telemetry reporting to protect against sybil attacks. 👍
#realworldcrypto
#realworldcrypto
A: If we change the timestamp range we can do that, the current scheme has kept it to 15 minutes.
#realworldcrypto
#realworldcrypto
#realworldcrypto

#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto

#realworldcrypto
#realworldcrypto

- patch everything
- TEST YOUR PATCHES
- did you actually test them???
#realworldcrypto

- isolate your agent to a single _physical_ core on Intel CPUs
- harden your agents with SLH if you can afford it
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
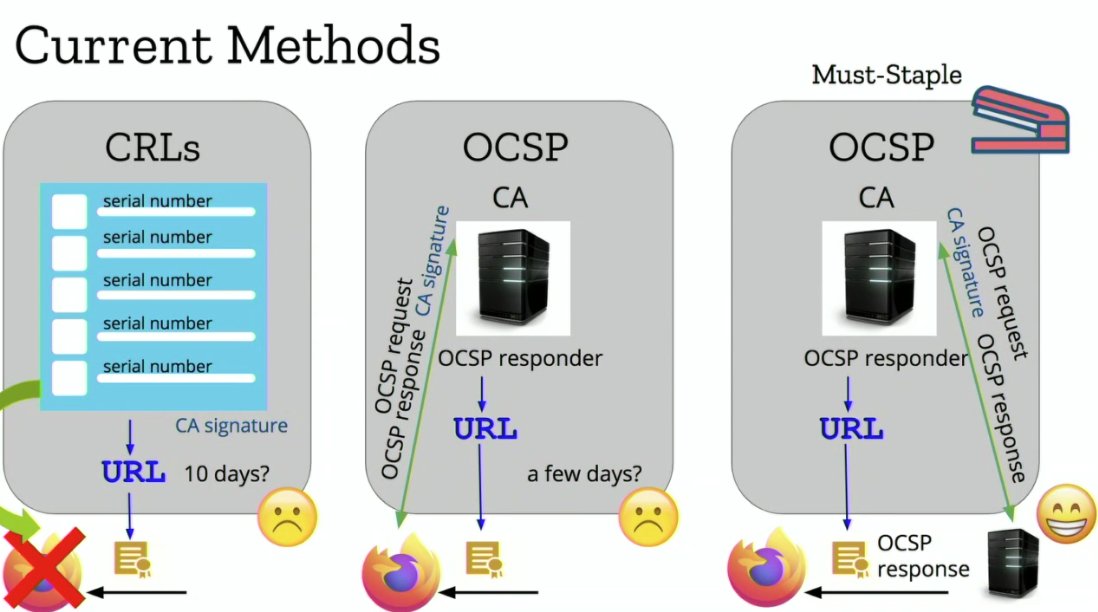
0.04ms to check a cert, <8ms to check a whole chain
#realworldcrypto
#realworldcrypto
A: The paper we were implementing suggested them, but it did mention other options like hashing
#realworldcrypto
A: OCSP-must staple is an idea that's been around for a while without much adoption, we think CRLite is a replacement.
#realworldcrypto
#realworldcrypto
#realworldcrypto
#realworldcrypto
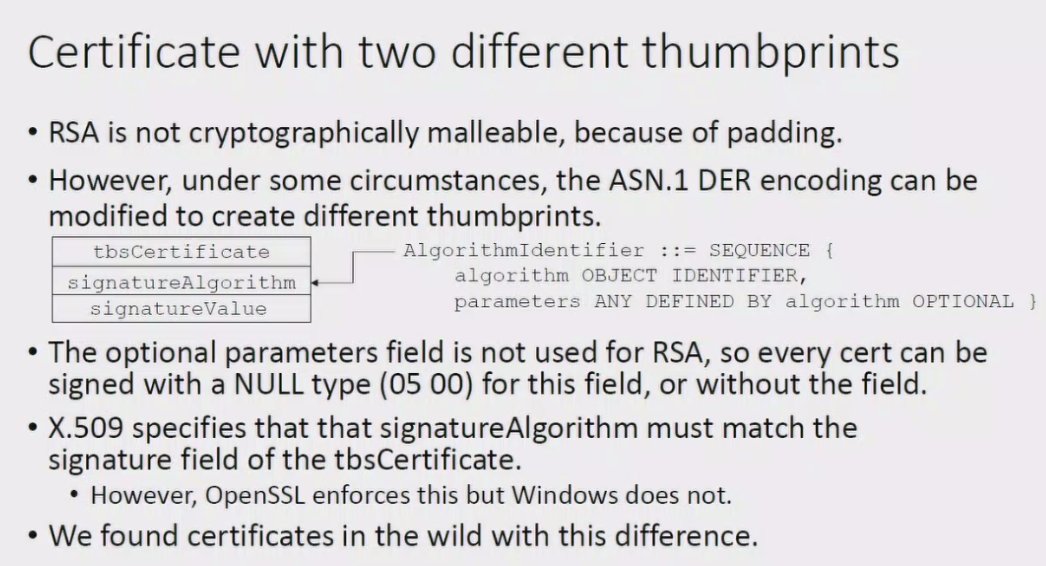
#realworldcrypto

- If that's too long, truncate the stronger hash instead
- PKI like CT should scan for MD5 and SHA-1 thumbprints w/ collision detection
- be wary
#realworldcrypto
A: While computing an mD5 or SHA-1 hash, check for diffs in input blocks while hashing (i'm a little confused by this)
#realworldcrypto
#realworldcrypto
- very painful
- expensive
- "know where all your crypto is" oooof for some orgs this is _not_ feasible
#realworldcrypto
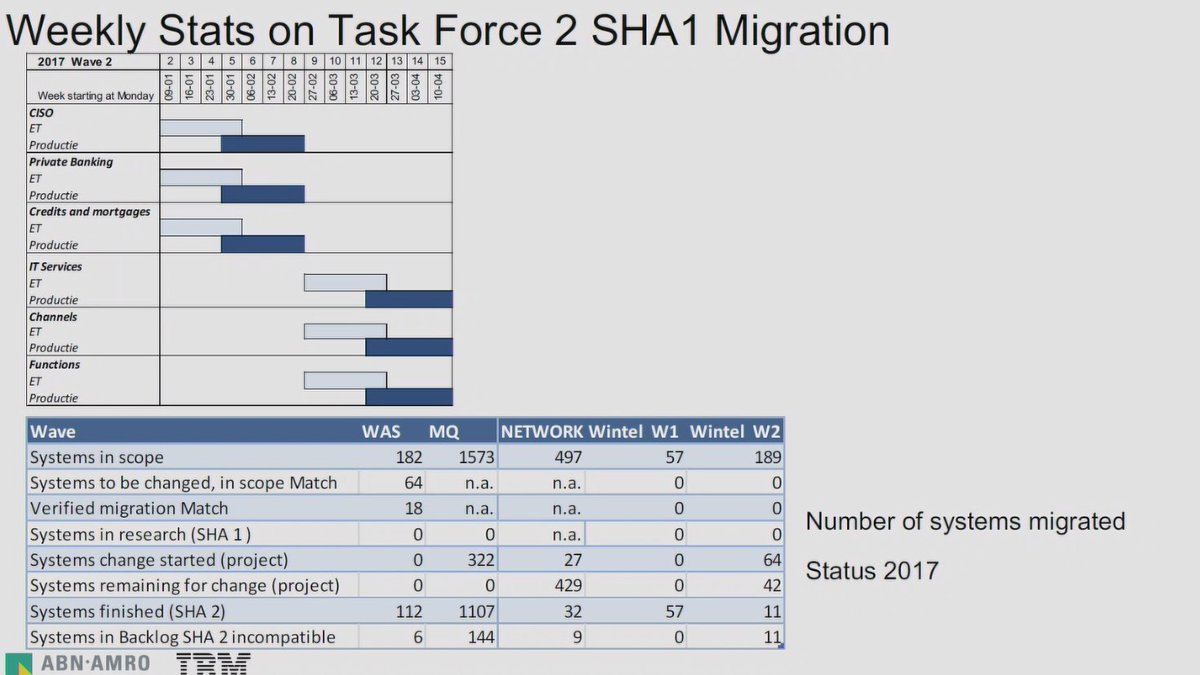
#realworldcrypto
#realworldcrypto
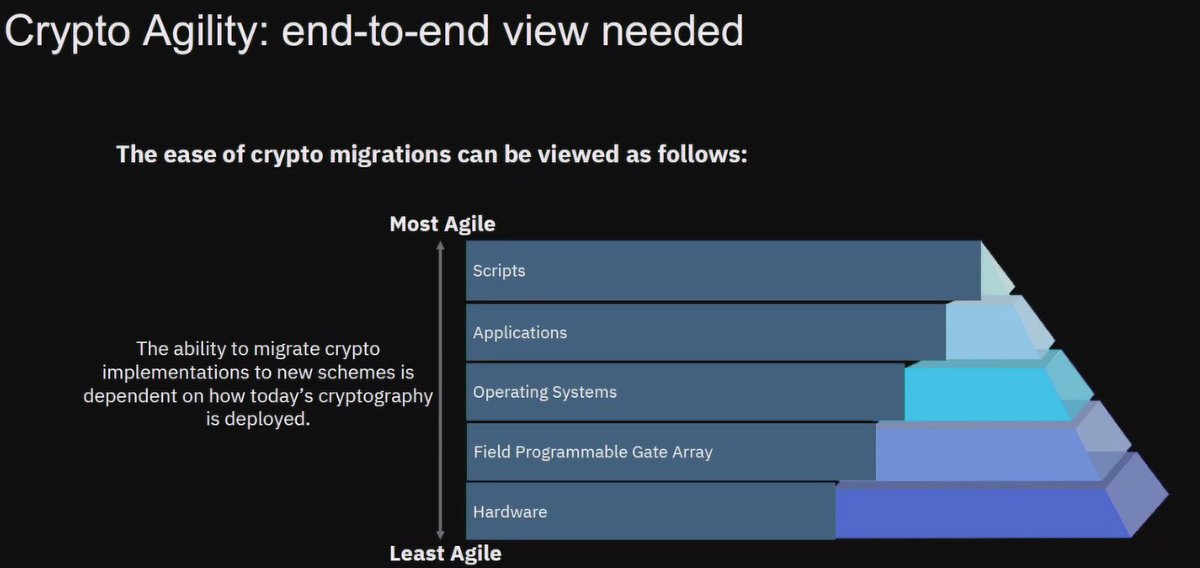
#realworldcrypto
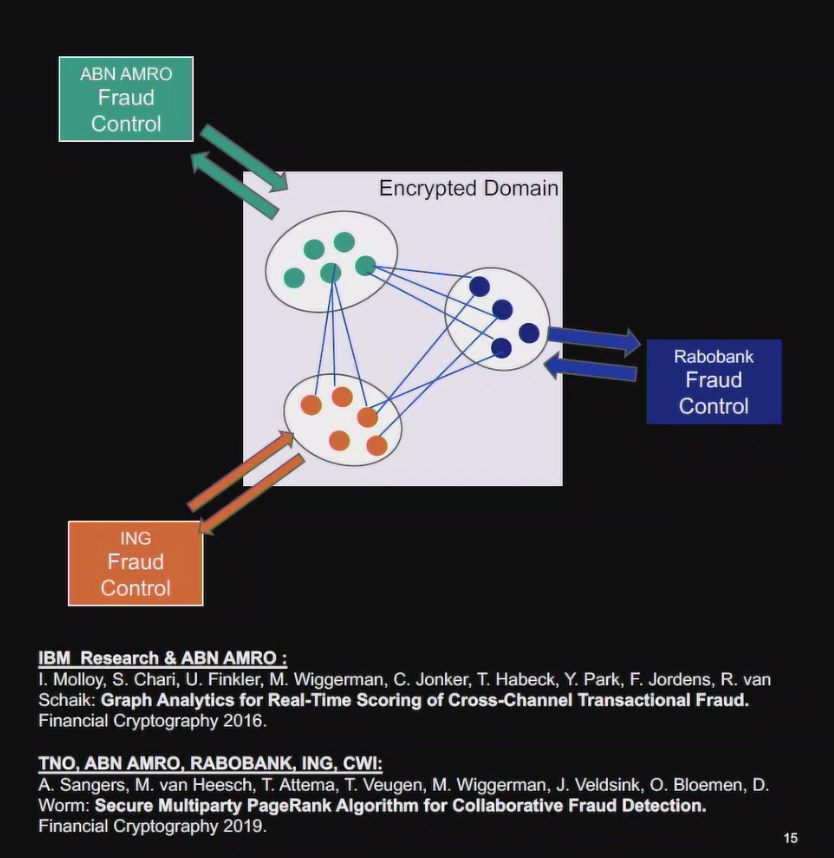
A: Need inventory of all your current usage, waiting for asymmetric standards (NIST), can double symmetric keys sizes today.
#realworldcrypto
#realworldcrypto
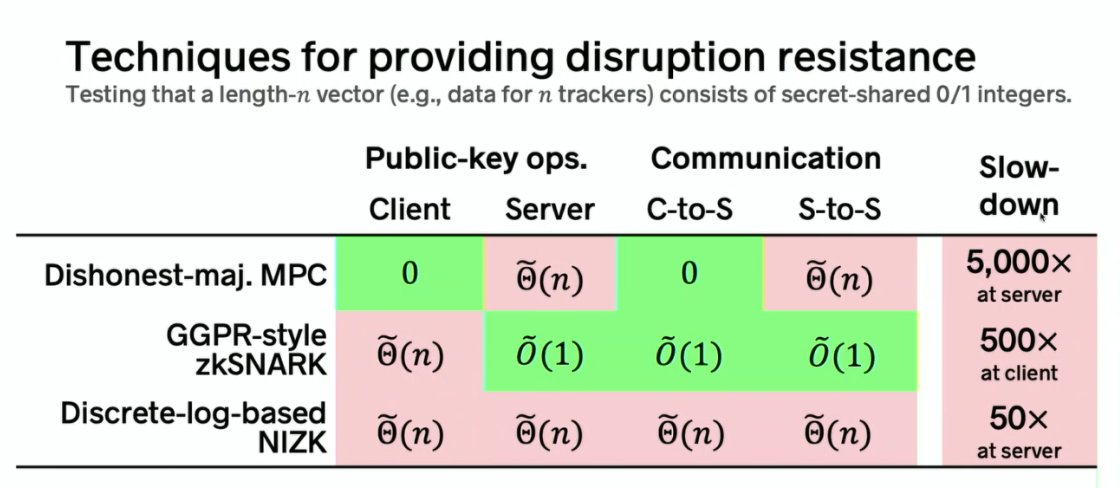
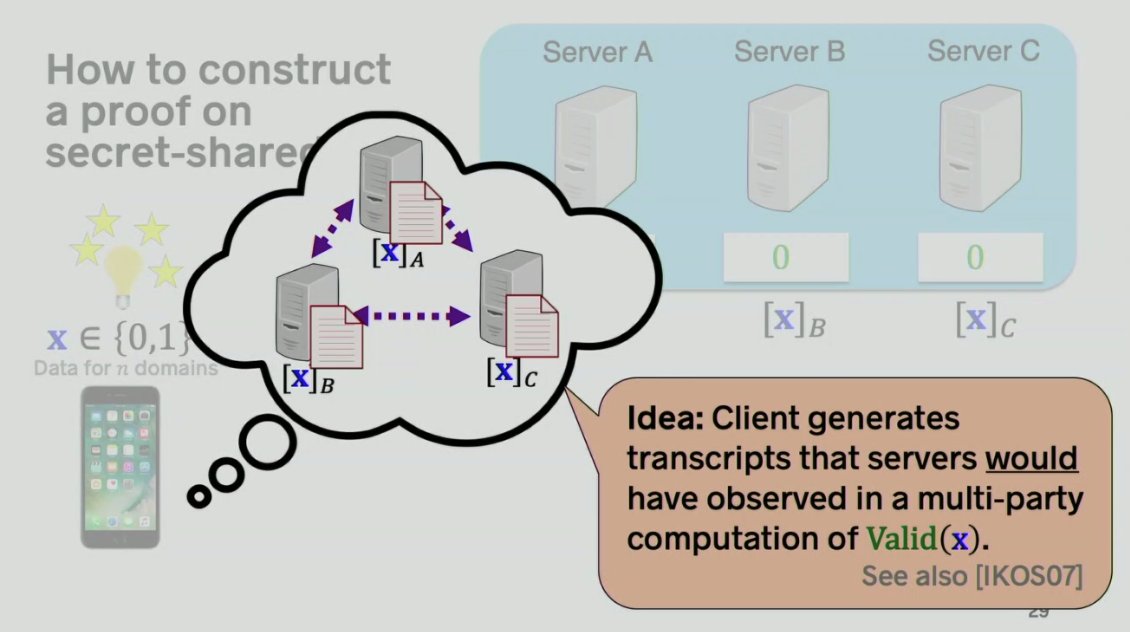
No need to recombine as in secret sharing
Better performance than MPC
#realworldcrypto

#realworldcrypto
#realworldcrypto
- minimal API
- connection broker
Avoiding single points of failure and mitigating attack surface
#realworldcrypto
Security people, what do you think about this strategy?
#realworldcrypto
A: Not yet, we would not necessarily do this for every project
#realworldcrypto