
Crowdstrike says SolarWinds hackers used component it's calling "Sunspot" to inject backdoor in Orion software. It sat on developer systems waiting for build commands to execute, checked if it was Orion software being built, then injected backdoor. Sunspot likely built 2.20.2020.
"SUNSPOT was identified on disk with a filename of taskhostsvc.exe (SHA256 Hash: c45c9bda8db1d470f1fd0dcc346dc449839eb5ce9a948c70369230af0b3ef168), and internally named taskhostw.exe by its developers." crowdstrike.com/blog/sunspot-m…
SolarWinds has updated the attack timeline. It now says hackers accessed SolarWinds network Sept. 4, 2019 and began their test run (which I wrote about here yahoo.com/now/hackers-la…) on Sept. 12, 2019. They ended test run on Nov. 4, 2019. The backdoor was compiled Feb. 20, 2020. 
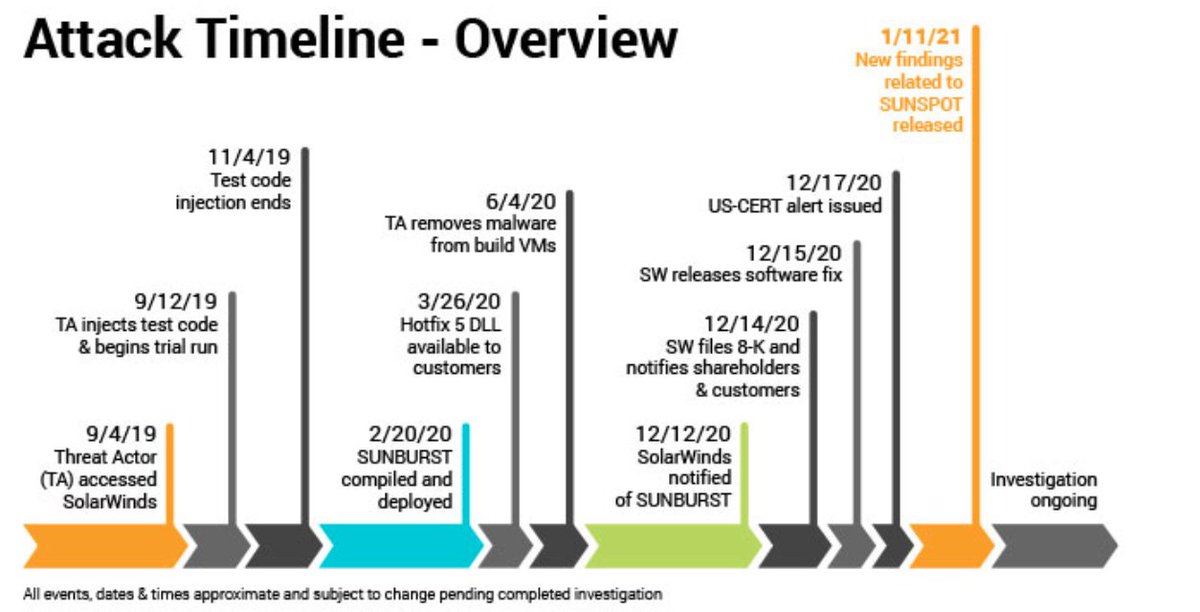
I should note that the Sept 4, 2019 date is just the earliest that investigators have found evidence of the attackers' presence in the SolarWinds network. They may have been in the network earlier than this, but no evidence of that yet.
I wrote in 1st tweet that SUNSPOT was compiled Feb. 20. But SolarWinds timeline says the SUNBURST backdoor (which SUNSPOT injected into the SW software) was compiled Feb. 20. Don't know if they were both compiled same day or if timeline is wrong. Here's Crowdstrike on SUNSPOT: 

Also, my original tweet has confused some people, since I wrote that SUNSPOT was placed on "developer systems". I meant on the build servers that developers use, not on the personal computers of individual developers. Sorry for the confusion.
• • •
Missing some Tweet in this thread? You can try to
force a refresh


