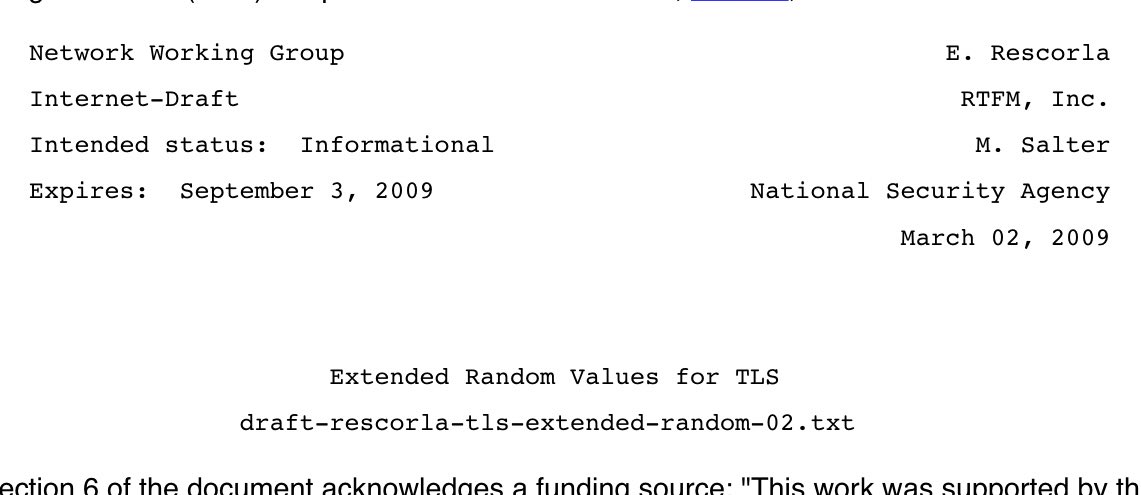
Not to criticize good lists like these (go Apple!) but goddamn it we invented computers precisely to automate tasks like this.
Why isn’t each of these a button in the iPhone UI?
Why isn’t each of these a button in the iPhone UI?
https://twitter.com/filosottile/status/1363158595622297604
Ok so let’s try these checklists out and see what it’s like to lock a phone down. I assume I’m concerned about someone else accessing my iCloud account as well as apps being evil.
Here’s step 1.
Here’s step 1.

(Obviously the problem here is that I need to turn off Find My iPhone.) But that’s obvious to me as someone who deals with iPhone crap a lot. Not sure it’d be obvious to everyone.
Anyway let’s stick to the checklist. Step 2 is about re-enabling some apps which I’ll skip.
Anyway let’s stick to the checklist. Step 2 is about re-enabling some apps which I’ll skip.

Step 3 says we can stop sharing locations with specific people. Ok yeah, I want to do that.
But here’s the thing: I already turned off the big “Location Services” button in step 1. So is this new step *in addition*, or is it an *alternative* to step 3?
But here’s the thing: I already turned off the big “Location Services” button in step 1. So is this new step *in addition*, or is it an *alternative* to step 3?

My first hint is on the top menu of “Location Services”. Even though I switched off the big master button, there’s a sub-menu called “Share My Location” that says I’m still sharing my location! So let’s go in there. 



Inside the “Share my Location” tab is actually a page called “Find My”, which is weird. It has two options, one of which is to “Share My Location” and the other is “Find My”. They’re different, I guess. The instructions tell me to turn off both. 

Instead of a master button for all of this I see this insane screen which frankly scares me. Are these separate options I need to turn off individually or is one a master button? 

Fooling around a little, it appears that the bottom two are independent and the top one is the master switch that turns the others off. Why isn’t there a visual indication of this?
Anyway, these come with various degrees of scary warnings.

Anyway, these come with various degrees of scary warnings.


(I can’t blame Apple for asking for a password to disable Find My. I know they do that for anti-theft reasons. That’s a reasonable balance but it’s still a little bit intimidating.)
Ok now we get to Step 4. Frankly I don’t even know if I need to do this. Didn’t I turn off location sharing in Step 3?
Is this an alternative or do I *also* need to do this to make sure I’m really not sharing my location?
Is this an alternative or do I *also* need to do this to make sure I’m really not sharing my location?

I really need to be sure I’ve turned off my location, so I’m doing step 4 even though I now have to switch out of Settings and use an app.
Inside that app there’s a list of people. Despite my best efforts to anonymize them you can safely infer they’re my family.
Inside that app there’s a list of people. Despite my best efforts to anonymize them you can safely infer they’re my family.

Clicking through any of them shows me this menu. It gives me the option to stop sharing my location with them.
So it appears I am still sharing my location — even though I turned this off in Step 3! (At least this is the obvious inference.)

So it appears I am still sharing my location — even though I turned this off in Step 3! (At least this is the obvious inference.)


(I’ve got to be honest that if one of these people wishes me harm, it would *not* make me feel very good to find out that I’m still “sharing my location” with them after step 3, even if this is a UI misunderstanding.)
The only indication I get that my master switch (from Step 3) is being respected occurs when I try to *re-enable* location sharing with an individual. I get this hot little dialog box. 

I am never going to be able to undo any of this.
Ok, nearly there. All that remains is Step 5, which is fortunately unnecessary because I disabled Location Services in Step 1 (although the text doesn’t indicate this, so frankly it’s still confusing.)
To do step 5 I have to re-enable Location Services, which I’ll do.
To do step 5 I have to re-enable Location Services, which I’ll do.

That gives me this insane list of every app on my phone (AKA every app I’ve downloaded since July 2008) sorted alphabetically, and showing me their location permissions.
My this is a big list. It would be nice to have the option to sort this list differently.
My this is a big list. It would be nice to have the option to sort this list differently.

The actual information I want from this list is “which apps are spying on my location”. Finding this out is like trying to spot a stranded hiker from a helicopter. I propose a button called “Sort by Location Access” that puts the nosier apps at the top. But whatever.
Ok I’m sorry for this long thread so let me sum up.
I have a PhD in CS with a focus in crypto/privacy (probably cuts against me, frankly) and I bought one of the first iPhones to roll off the assembly line. I am the closest thing to an “expert”. And I still found this confusing.
I have a PhD in CS with a focus in crypto/privacy (probably cuts against me, frankly) and I bought one of the first iPhones to roll off the assembly line. I am the closest thing to an “expert”. And I still found this confusing.
I also want to address something a person told me recently: don’t criticize security people who are doing good things just because they didn’t get it perfect. So I want to say that Apple’s privacy *and* this checklist is relatively awesome.
But it could be improved.
But it could be improved.
How should it be improved:
Better master settings: switches that turn it all off.
No conflicting redundancy: if there are two switches, show me if one is the “master breaker” or if either switch being “on” can hurt me.
Better feedback: if things are off, say so clearly.
Better master settings: switches that turn it all off.
No conflicting redundancy: if there are two switches, show me if one is the “master breaker” or if either switch being “on” can hurt me.
Better feedback: if things are off, say so clearly.
I don’t get the feeling Apple puts these privacy settings through the same testing and review that they would give, say, their “new phone activation” workflow or the App Store. There are little rough edges that indicate this.
As an example (mentioned above): the menu item labeled “Share My Location” takes me to a screen labeled “Find My”. Which in turn takes me to the *real* “Find My iPhone” screen. Maybe this is on purpose! But it feels sloppy, like a loose screw in a brand new iPhone. 





Overall I get the feeling that the Apple privacy settings “accreted” into their current form, rather than being designed. This is why we need 6-item checklists.
Maybe it’s time to forget the entire thing and start from scratch. //
Maybe it’s time to forget the entire thing and start from scratch. //
Ah, a great point here. When it’s important to have settings that “just turn everything off” Apple really knows how to do this.
https://twitter.com/falkvinge/status/1363442080681451521
• • •
Missing some Tweet in this thread? You can try to
force a refresh