
ICYMI, @PwC_UK’s 2020 #threatintel Year in Retrospect report is out now! All team contributed but h/t to @KystleM_Reid! :fire: You can check it out here: pwc.to/2ZPx7fo In this thread, I will summarise some of what I thought were key findings: 🧵👇 1/n
#Ransomware has become the most significant cyber security threat faced by organisations, irrespective of industry/location. TTPs have pivoted to mass data exfiltration prior to encryption, along with leaks & extortion. S/o to @andyp346 for all your work countering this.🙏 2/n 
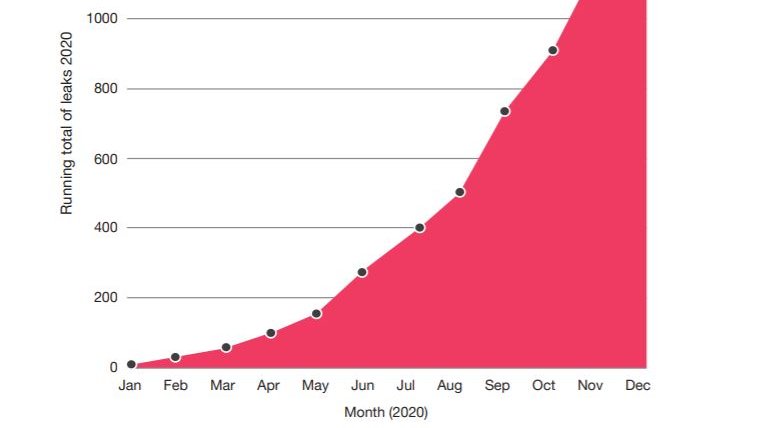
In 2020, 86% of the incidents that PwC’s Incident Response team responded to were attributable to cyber criminals. 79% of leaks happened in 2nd half of 2020. Our data sees Manufacturing, TMT, & Professional Services most impacted. 3/n 

Malware delivery systems play a central role. From #Emotet & #Qakbot (leading to Egregor, Prolock, DoppelPaymer) to #Trickbot & #Bazar (leading to Ryuk). Shoutout to We don’t work together, but h/t to @wanna_VanTa & @x04steve the Ryuk smashers! Go read their work too🔥 4/n
Ransomware destroys companies & lives. It devastates hospitals, harms schools. It profits off others’ disgrace (& abuses their RDP conns & VPN creds). Small-medium orgs, critical infra, charities, need more help. 5/n
#CobaltStrike EVERYWHERE. Most crime & ransomware chains deploy CobaltStrike to burrow deeper into networks (e.g. #Nefilim, #Qakbot), but APTs also (e.g. Scarlet Ioke, Red Lich). It’s so versatile and widely used that efforts detecting CobaltStrike are well spent, imo. 6/n
#BEC: do NOT underestimate it. It’s costly to orgs & ruins individuals' lives. Domain spoofing, vendor email compromise, phishing kits... Now, BEC groups also use commodity malware. It's a threat. @iHeartMalware’s & @AgariInc's work on BEC live rent-free in my head. 7/n
We continue to observe a growing trend of #espionage motivated #APT's also performing financially-motivated activity - moonlighting (e.g. Red Kelpie; Yellow Geryon; Green Havildar’s subset Gorgon Group/Aggah) or to support national strategic goals (e.g. Black Artemis). 8/n
While not new, hacker-for-hire ops also blur lines b/w espionage & economic gain, targeting orgs & individuals. Several have been exposed this year, including Orange Abtu, #DeathStalker, #CostaRicto. Also great reports by @citizenlab, @Securelist, @BlackBerry on these 🔥 9/n 

Re:COVID-19, PwC's #threatintel team did not observe significant lapses in threat actors’ operations - but both #APT's & cyber criminals used COVID-19-themed lures. Several threat actors (e.g. #WellMess; Yellow Garuda; Black Artemis) targeted vaccine & treatment research. 10/n
#APT's & cyber criminals used COVID-19 themes for #phishing: from WHO-branded lures (e.g. Red Orthrus) to impersonating WHO (e.g. Black Banshee) / attempting to cred phish WHO staff (Yellow Garuda); from COVID numbers reports (Trickbot), to spoofing financial aid schemes. 11/n
Of course, we see continued alignment b/w #cyberthreats & geopolitical events. Areas fraught with conflict/tension (India-China border, Nagorno-Karabakh, Iran, Hong Kong, Tibet) & minorities (like in Xinjang, or China-based Catholics) are in the crosshairs of #APT campaigns. 12/n
Our #threatintel Year in Retrospect report's “Intelligence gathering” section (pwc.to/2ZPx7fo) details cyber-enabled military/industrial espionage & civilian surveillance by threat actors based in DPRK, China, Russia, Iran, Turkey, Pakistan, India, Vietnam & more. 13/n
Some of my favourite insights:
- continued tool-sharing among China-based #APT's (#RoyalRoad, #ShadowPad, #PlugX);
- Yellow Nix stepping up its game + quickly moving to exploit newly-released vulnerabilities POCs;
- role of private intelligence companies in espionage ops. 14/n
- continued tool-sharing among China-based #APT's (#RoyalRoad, #ShadowPad, #PlugX);
- Yellow Nix stepping up its game + quickly moving to exploit newly-released vulnerabilities POCs;
- role of private intelligence companies in espionage ops. 14/n

Information operations also continue unabated (many great reports this year, incl. by @Graphika_NYC) – incl. Iran- & Russia-based threat actors sowing unrest ahead of the November 2020 US election, & threat actors pushing COVID-19 vaccine disinformation targeting Europe. 15/n
#Supplychain compromise has been relevant for years. Many forms of compromise: digital trust (certificates); trusted infra (websites/web apps); software (trojanising files, malicious plugins, fake apps like #AppleJeus); 3rd party compromise.
VPNs & web apps – ever more relevant in a remote work environment. #APT's including Red Kelpie, Yellow Nix, Blue Kitsune, + ransomware groups (e.g. Cl0p, Nefilim), have been exploiting VPN vulnerabilities & web infrastructure like OWA & Microsoft Exchange. 17/n
Rise of the defenders: In all this, in 2020, several public entities went more public on #threatintel attribution. The European Council imposed its 1st round of sanctions re cyber threats. The private sector took legal action. And let’s not forget the Emotet disruption! 18/n 

So, what to expect in #threatintel in 2021? @KrystleM_Reid wrote a brilliant blog post on this: pwc.to/2ZPx7fo I only have 2 adds:
1) Orgs, PWEASE review assets & prioritise patches as per your threat model…
2) Thank you, #cyber defenders. You’re my heroes. 🔥💕19/19
1) Orgs, PWEASE review assets & prioritise patches as per your threat model…
2) Thank you, #cyber defenders. You’re my heroes. 🔥💕19/19
• • •
Missing some Tweet in this thread? You can try to
force a refresh


