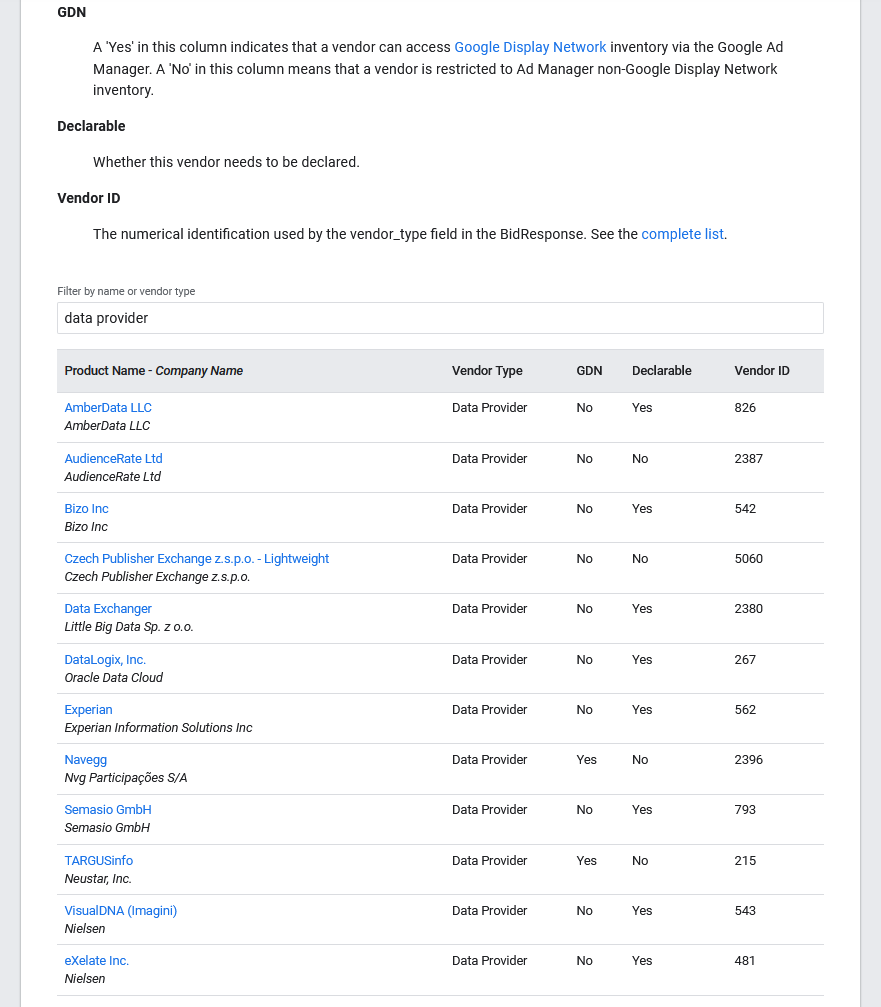
Anomaly 6, another firm run by ex-military and location industry veterans, sold location data secretly sourced from ordinary smartphone apps to SOCOM/SOCAFRICA, a US military unit tasked with counterterrorism, counterinsurgency and special reconnaissance: vice.com/en/article/z3v…
SOCOM states the contract was about evaluating the "feasibility of using Anomaly 6 telemetry services in an overseas operating environment"
As the WSJ reported in August, Anomaly 6 tracks "the movements of hundreds of millions of mobile phones world-wide" wsj.com/articles/u-s-g…
As the WSJ reported in August, Anomaly 6 tracks "the movements of hundreds of millions of mobile phones world-wide" wsj.com/articles/u-s-g…
Once again, the way our digital (app) economy currently works, built and optimized for uncontrolled marketing surveillance, treating personal data as just another mass commodity, is directly feeding into the most invasive forms of government surveillance.
In 2020, member of parliament André Hahn was asking the German government whether services by Anomaly 6 are being used by German authorities.
The government's "neither deny nor confirm" response is so specific that it suggests yes.
Original in German:
andre-hahn.eu/app/uploads/20…
The government's "neither deny nor confirm" response is so specific that it suggests yes.
Original in German:
andre-hahn.eu/app/uploads/20…

"Disclosure of details of knowledge of the software in question from the U.S. company Anomaly Six would allow far-reaching, direct conclusions to be drawn about the working methods and ... about the technical equipment and reconnaissance potential of the intelligence services"
"information... concerning possible knowledge and use of the software of the U.S. company Anomaly Six affects such evident secrecy interests [of the Federal Republic of Germany] requiring protection that even the slight risk of the information becoming known ... must be avoided"
"In weighing up the parliamentary right to information of the members of parliament on the one hand and the interests in secrecy justified by the welfare of the state on the other, the parliamentary right to information must therefore exceptionally take a back seat"
Babel Street, a similar company providing both social media surveillance and commercial location data, has sold to nearly every major defense and intelligence agency in the US, and to governments including in the UK and in Germany, according to the WSJ: wsj.com/articles/acade… 

Ich finde, es muss dringend geklärt werden, ob dt. Behörden kommerzielle Standortdaten kaufen, die zwielichtige Firmen wie Anomaly 6 von ahnungslosen Smartphone-App-NutzerInnen absaugen.
/cc @UlrichKelber @EskenSaskia @andre_meister @annalist @sonstso_sk @PatrickBeuth @jbruehl
/cc @UlrichKelber @EskenSaskia @andre_meister @annalist @sonstso_sk @PatrickBeuth @jbruehl
Hier nochmal die -doch sehr erstaunlich formulierte- Antwort von Staatssekretär Richter auf die schriftliche Frage von MdB André Hahn in Bezug auf die Nutzung der Dienste der US-Standortdatenhandelsfirma Anomaly 6 durch dt Behörden:
andre-hahn.eu/app/uploads/20…
dipbt.bundestag.de/extrakt/ba/WP1…
andre-hahn.eu/app/uploads/20…
dipbt.bundestag.de/extrakt/ba/WP1…
• • •
Missing some Tweet in this thread? You can try to
force a refresh