Reminder: Bitcoin is NOT private. Bitcoin CAN be traced. The ways to link onchain tx's and ultimately tie them to your IRL identity are increasingly sophisticated and the efforts are increasingly led by US agencies. The blockchain is forever.
But.....
But.....
As far as I can tell the tracing of on-chain BTC transactions played ~zero part in tracking down/confirming Bitcoin Fog's alleged operator's id.
The narrative the govt, Wired, etc are pushing on this (that bitcoin is not anonymous) is true. But it's also pretty irrelevant here.
The narrative the govt, Wired, etc are pushing on this (that bitcoin is not anonymous) is true. But it's also pretty irrelevant here.
The reality is that w/o 4 separate, centralized, key data sources the govt wouldn't have been able to track him down. Only one of those data sources came from a lawful subpoena: Google.
The rest came from Mt Gox + Liberty Reserve + BTC-E data that the IRS-CI just...has?
The rest came from Mt Gox + Liberty Reserve + BTC-E data that the IRS-CI just...has?
Its worth noting the Google subpeona probably relied exclusively on that same data from Mt Gox, Liberty Reserve, and BTC-E.
Now I'm not a lawyer but...is it okay that the govt is using seized data from separate, past investigations to find other crimes/criminals/"kingpins"?
Now I'm not a lawyer but...is it okay that the govt is using seized data from separate, past investigations to find other crimes/criminals/"kingpins"?
We all know the SDNY has a history of overstepping and being incredibly problematic, esp. under Preet Bharara 😒
But at least with Liberty Reserve the size, scope, duration, the US '̶s̶ ̶l̶o̶n̶g̶ ̶l̶o̶n̶g̶ ̶l̶o̶n̶g̶ ̶a̶r̶m̶ coordinating with 17 different countries for years...
But at least with Liberty Reserve the size, scope, duration, the US '̶s̶ ̶l̶o̶n̶g̶ ̶l̶o̶n̶g̶ ̶l̶o̶n̶g̶ ̶a̶r̶m̶ coordinating with 17 different countries for years...

...they have gone thru the processes. On top of multiple convictions, theres a pile of restraining orders/injunctions and seizure warrants around money, bank accounts, domain names, servers, etc.
Much insights: sherloc.unodc.org/cld/uploads/re…
Like, yes, domain name!=server
Much insights: sherloc.unodc.org/cld/uploads/re…
Like, yes, domain name!=server

The one exception with regards to Liberty Reserve is the little detail that give credibility to those who spout "taxation is theft!"
The IRS(-CI?) still holds fuckloads of Liberty Reserve users' money. (lol. but not really lol.)
krebsonsecurity.com/2020/02/a-ligh…
The IRS(-CI?) still holds fuckloads of Liberty Reserve users' money. (lol. but not really lol.)
krebsonsecurity.com/2020/02/a-ligh…
In the case of BTC-E though, the US has NOT secured a conviction and didn't even win extradition—France did.
That means all the forfeitures that happen UPON CONVICTION are moot at this point in time.
That means all the forfeitures that happen UPON CONVICTION are moot at this point in time.

With BTC-E, the US has only unsealed the a few docs. And only did that bc the clusterfuck of alphabet agencies wanted to throw a massive circlejerk party around said indictment. Any seizures, other affidavits, etc are still sealed.
justice.gov/usao-ndca/pr/r…
justice.gov/usao-ndca/pr/r…

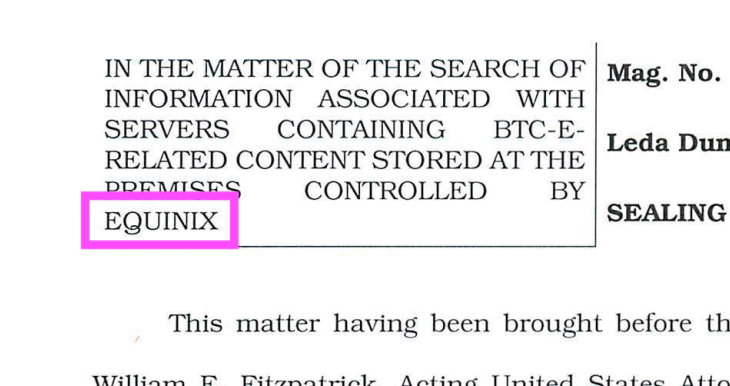
The last page of that doc DOES reference a July '17 warrant for BTC-E info on Equinix servers.
In New Jersey.
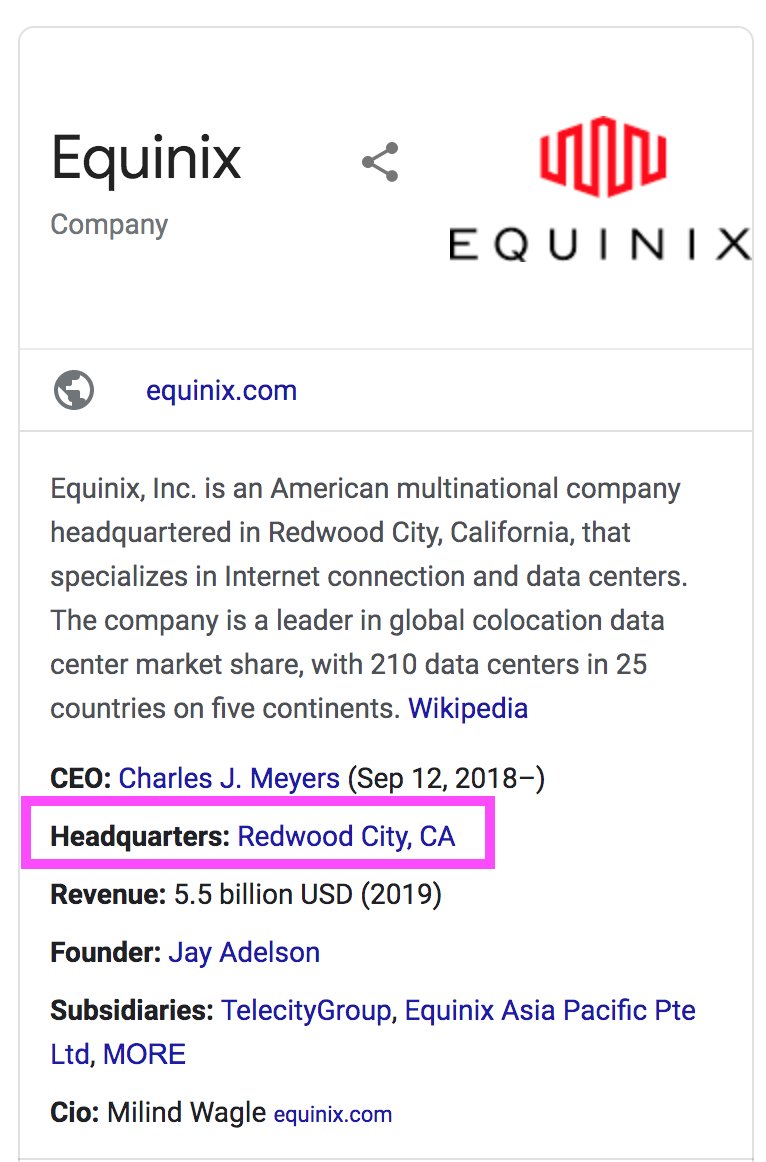
For info housed by a company HQ'd in Northern District of CA.
For a case indicted in May '16 and January '17 by Northern District of CA.
🤔
justice.gov/usao-ndca/pres…



In New Jersey.
For info housed by a company HQ'd in Northern District of CA.
For a case indicted in May '16 and January '17 by Northern District of CA.
🤔
justice.gov/usao-ndca/pres…


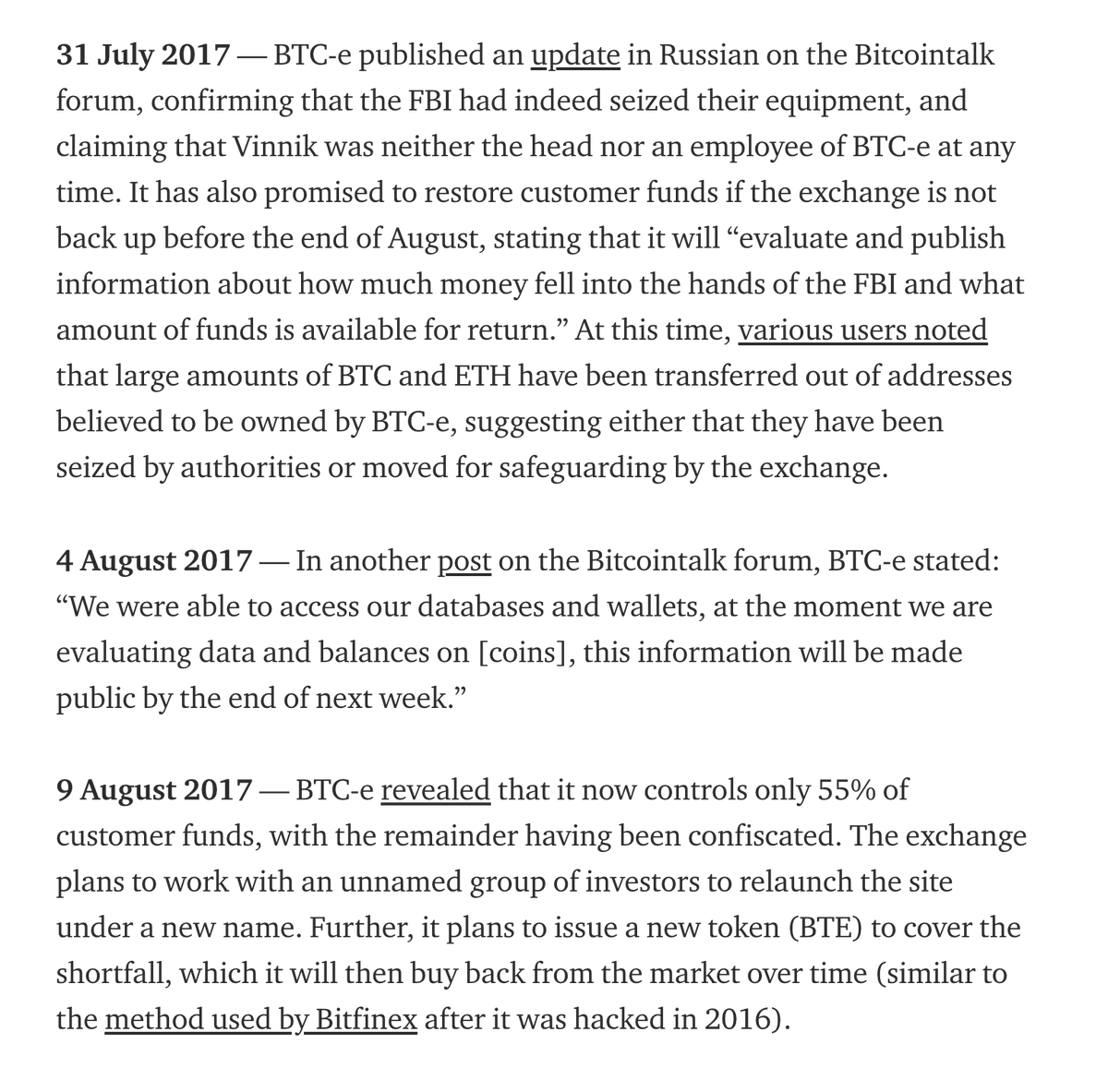
Normally I don't consider the posts on BitcoinTalk from operators of a shady exchanges to be reliable. But in this case it all lines up (especially timing)
It may have been a different three-letter agency and they probably copied the data instead of running off w the machines.
It may have been a different three-letter agency and they probably copied the data instead of running off w the machines.
But they got the important bits.
And if we ignore any problems w the validity of the search (which are heavily discussed bc rule 41 is fucked), it's far more interesting and far less discussed to look at what happens *after* the govt has, say, lawfully seized digital records.
And if we ignore any problems w the validity of the search (which are heavily discussed bc rule 41 is fucked), it's far more interesting and far less discussed to look at what happens *after* the govt has, say, lawfully seized digital records.
So ask your lawyer friends to slide into the public replies of this tweet, please.
Assuming a valid search/seizure of digital financial transactions and user records from an (illegal money laundering) exchange...
What happens to the PII afterwards? Names, BTC addresses, etc?
Assuming a valid search/seizure of digital financial transactions and user records from an (illegal money laundering) exchange...
What happens to the PII afterwards? Names, BTC addresses, etc?
Is it allowed to just float around the IRS, HSI, and FBI offices and searched to connect people/txs in other cases? Spawn new cases? Years later?
If info was obtained bc COMPANY is money laundering, can info be used against AN INDIVIDUAL CUSTOMER OF COMPANY who sells drugs?
If info was obtained bc COMPANY is money laundering, can info be used against AN INDIVIDUAL CUSTOMER OF COMPANY who sells drugs?
Because that's def what's happening and they aren't even really attempting to hide it or play deep parallel construction games. It just seems...hinky. To me. But I'm not a lawyer. Or a special agent. 🤷
attached: USA v KARLSSON, 2019 and USA v. STERLINGOV, 2021


attached: USA v KARLSSON, 2019 and USA v. STERLINGOV, 2021



Lastly, just because THIS CASE doesn't rely on actual blockchain analysis doesn't mean blockchain analysis isn't a thing.
Bitcoin CAN be traced on-chain. The ways to link onchain tx's and ultimately tie them to your IRL identity are increasingly sophisticated.
Bitcoin CAN be traced on-chain. The ways to link onchain tx's and ultimately tie them to your IRL identity are increasingly sophisticated.
If you want to see what it looks like when they do use serious on-chain and even cross-chain tracking and check out:
USA v Schemey COVID Terrorists: justice.gov/opa/press-rele…
USA v Crypto stolen by North Korean hackers from South Korean exchanges justice.gov/opa/press-rele…
USA v Schemey COVID Terrorists: justice.gov/opa/press-rele…
USA v Crypto stolen by North Korean hackers from South Korean exchanges justice.gov/opa/press-rele…
So yeah. Interesting stuff. Curious to know if I'm alone in thinking this is fucked. 🤷
PS: this is not the first mixer to be taken down you lazy fucking "journalists." It's been a year since Helix was taken down. Google is a thing. Use it. 🤦♀️ justice.gov/opa/press-rele…
PS: this is not the first mixer to be taken down you lazy fucking "journalists." It's been a year since Helix was taken down. Google is a thing. Use it. 🤦♀️ justice.gov/opa/press-rele…
Oh fuck I forgot to share my theory on the "why now?" from the original thread
Theory: agents, mostly but not limited to IRS-CI agents associated around the Northern District of CA, have the BTC-E databases and are using it like its going out of style.
Theory: agents, mostly but not limited to IRS-CI agents associated around the Northern District of CA, have the BTC-E databases and are using it like its going out of style.
https://twitter.com/tayvano_/status/1387300831347703808?s=19
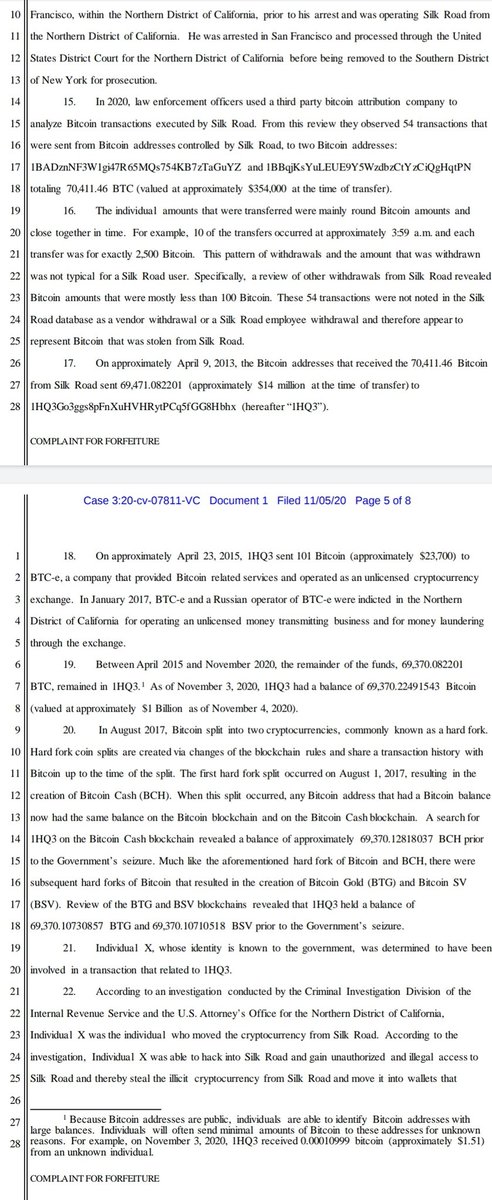
There are some key similarities between this and the Nov 2020 forfeiture of 69,000 2013-era BTC (justice.gov/usao-ndca/pr/u…)
Besides the time period, we have same agencies, jurisdiction, and a single understated mention of BTC-E hiding in piles of parallel construction fluff.

Besides the time period, we have same agencies, jurisdiction, and a single understated mention of BTC-E hiding in piles of parallel construction fluff.

Just a theory. 😉
• • •
Missing some Tweet in this thread? You can try to
force a refresh