Read the latest in our efforts to help provide new details around child exploitation cases.
New from @Mabl2K bellingcat.com/news/2021/04/3…
New from @Mabl2K bellingcat.com/news/2021/04/3…
@Mabl2K In 2015, the #FBI released images of John Doe 29. This individual is NOT accused of committing any abuse but may have critical information pertaining to the identity of a child victim in an ongoing sexual exploitation investigation 

@Mabl2K In 2020, FBI’s Endangered Child Alert Program (ECAP) added more images to the John Doe 29 case. But where in the world were these images taken? 

@Mabl2K We were able to identify the location where the victim was seated to a resort town in southern Turkey.
This is how we did it...
This is how we did it...

@Mabl2K We enhanced the FBI’s image labelled BB002 to reveal a small red object seen through the window in the background. It was an element that seemed to contain a key piece of information: a Turkish flag. 
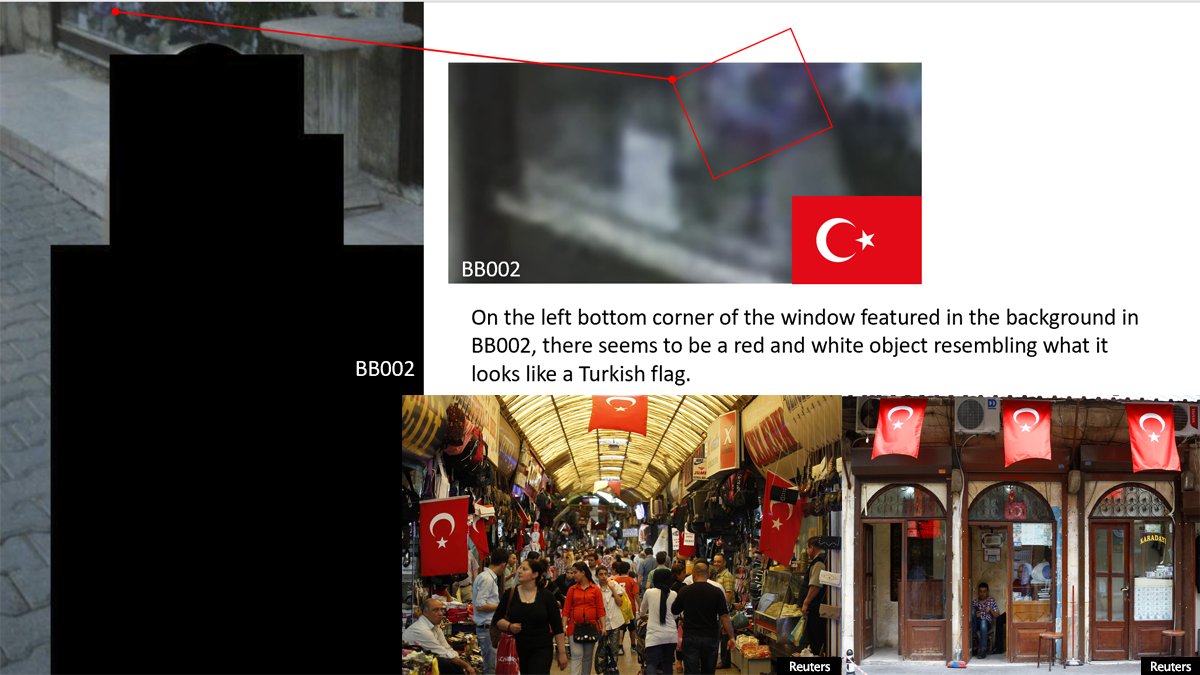
@Mabl2K After checking the top tourist destinations in Turkey, a virtual stop in the town of “Side” revealed matching façade and street elements featured in FBI’s image BB002: 

@Mabl2K Determined to find the pool, we roughly recreated the scene observed in the FBI’s other image (labelled BB001) by constructing a 3D model using @SketchUp. This helped us understand the layout and aim for the right spot in our hunt 

@Mabl2K @SketchUp We soon discovered a hotel facility on an online booking site. Although not a matching pool, this hotel used the same type of stainless steel litter bins seen in the FBI’s image BB001. The hotel belongs to a group which would lead us to the final location. 

@Mabl2K @SketchUp Close to the town of Side in Turkey we found a hotel where all the main elements seen in the FBI’s image BB001 were a match. We used publicly available pictures taken by guests to verify the location. 
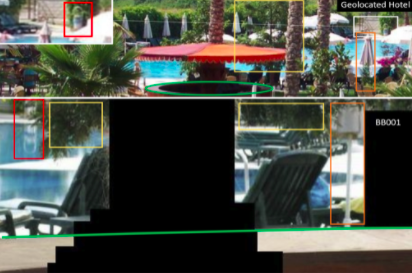
@Mabl2K @SketchUp In the FBI’s image BB001, we can see the victim was seated inside a cocktail bar by the pool. The colour, style, shape and position of the parasols as well as the trees and sun loungers are a match. 

@Mabl2K @SketchUp By tracking and analysing some of the physical elements around the pool, we determined the FBI’s image BB001 was taken in summer 2006. 

@Mabl2K @SketchUp Read the full article with further details on how this geolocation was made here bellingcat.com/news/2021/04/3…
• • •
Missing some Tweet in this thread? You can try to
force a refresh