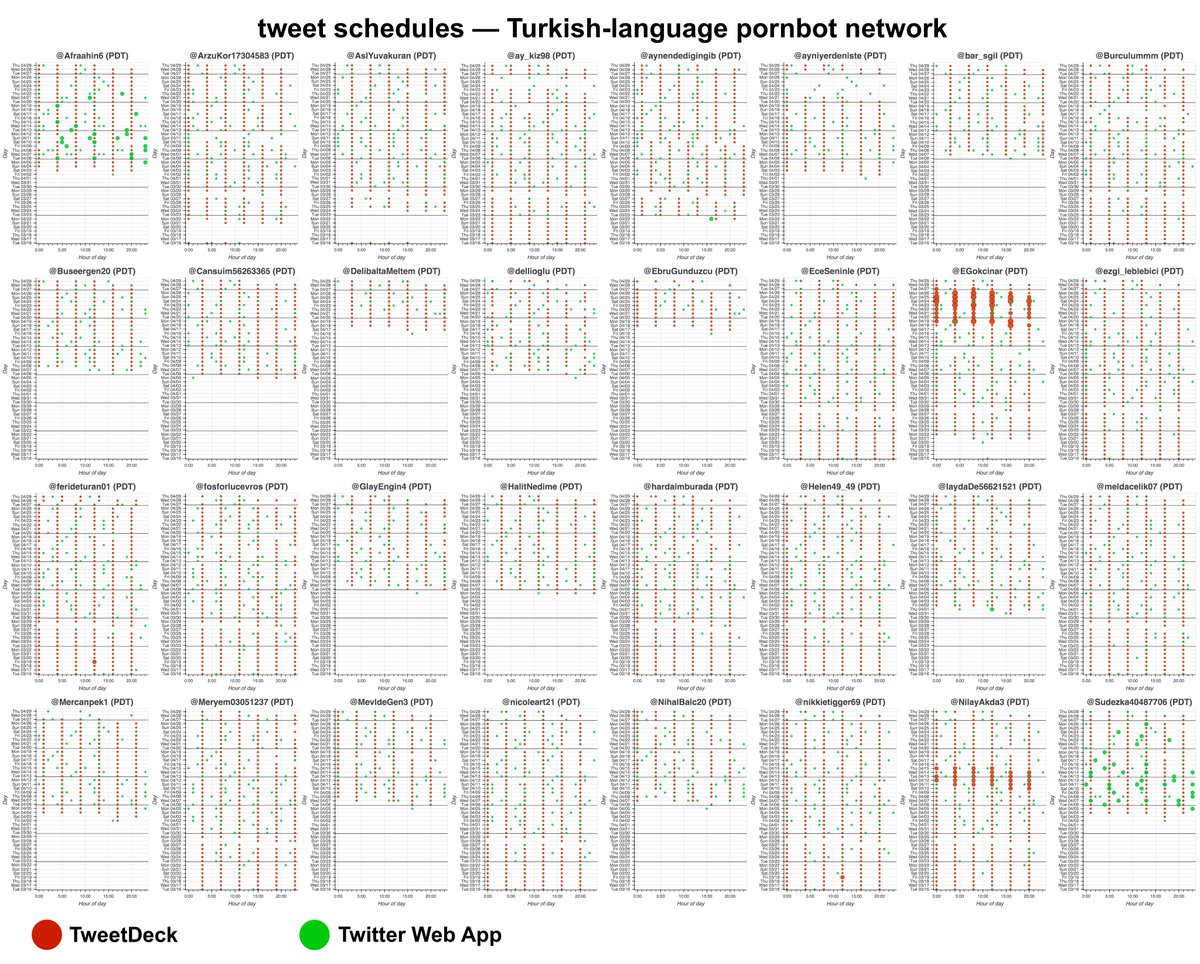
Here's an interesting account: @Right_n_Aware. Almost all of this account's tweets (177 of 193) have the curious property that they are duplicated verbatim on other accounts. #SpamTastic
cc: @ZellaQuixote
cc: @ZellaQuixote
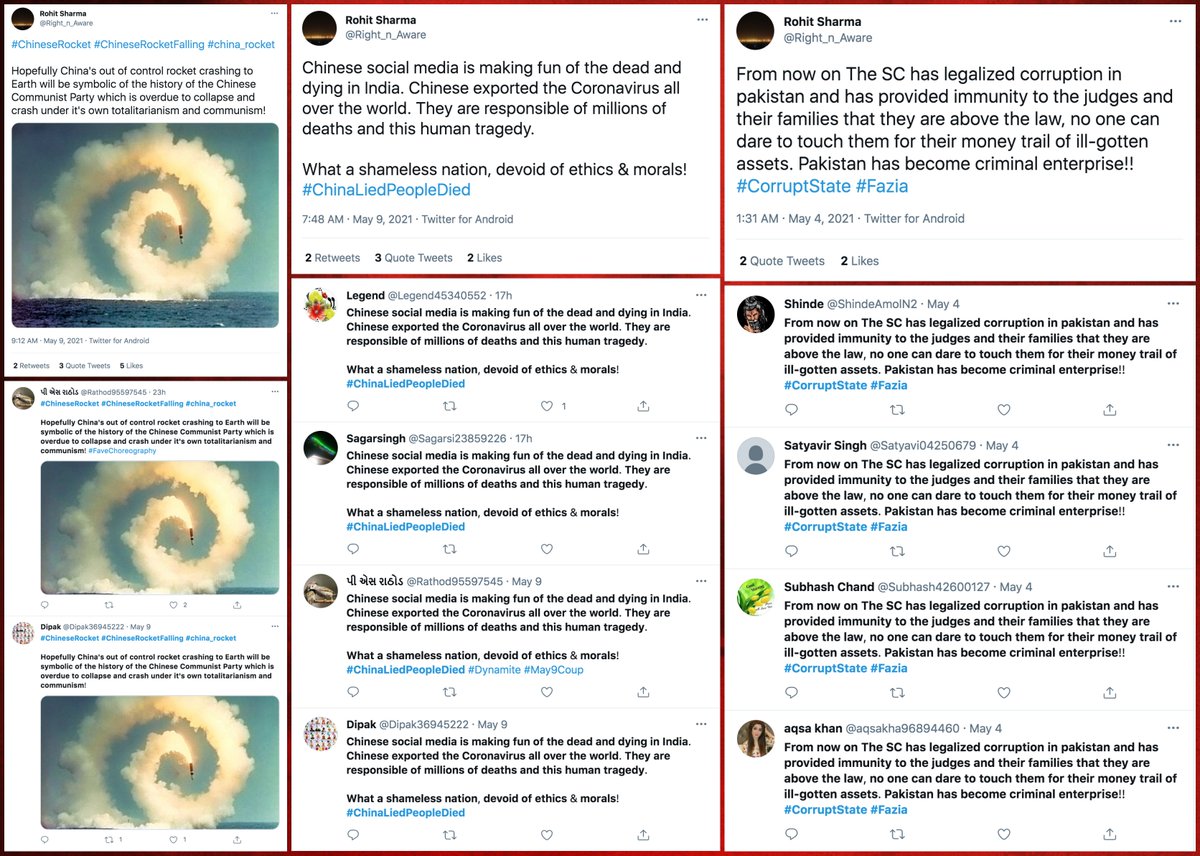
We found a total of 78 accounts (including @Right_n_Aware) that frequently tweet the same tweets verbatim. Almost all were created in 2020 or 2021, and almost all have more tweets than likes. They post the majority of their tweets via "Twitter for Android". 






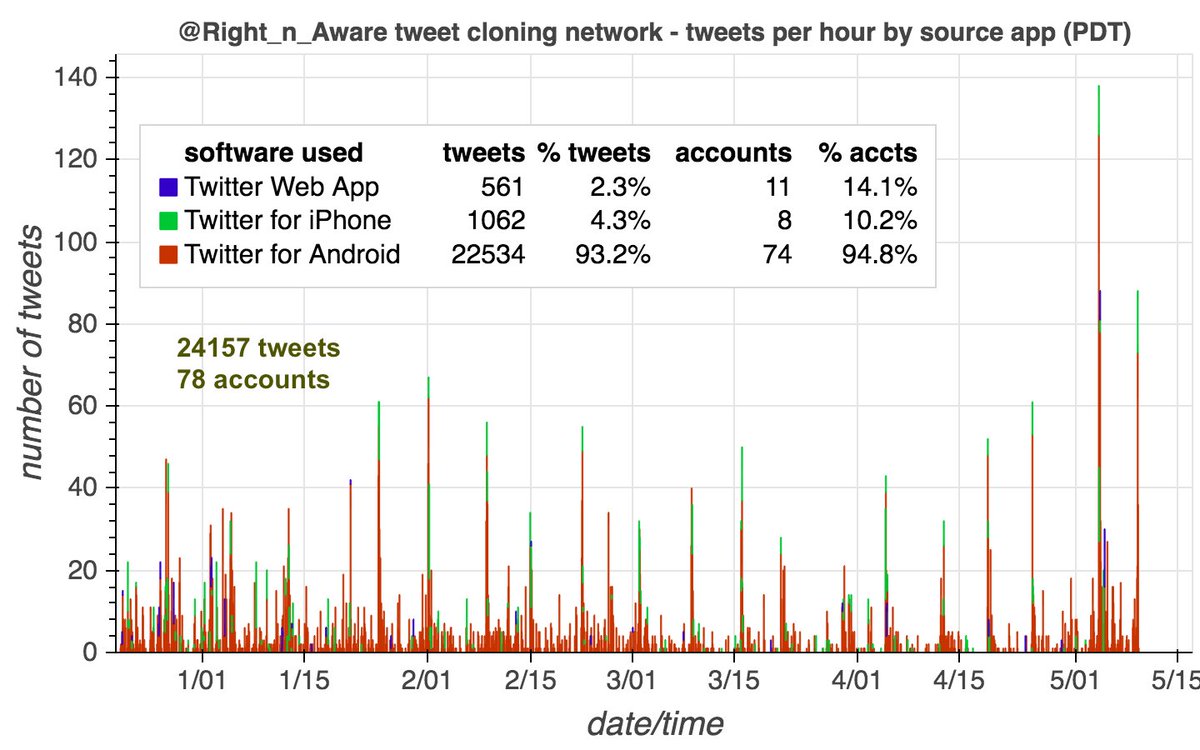
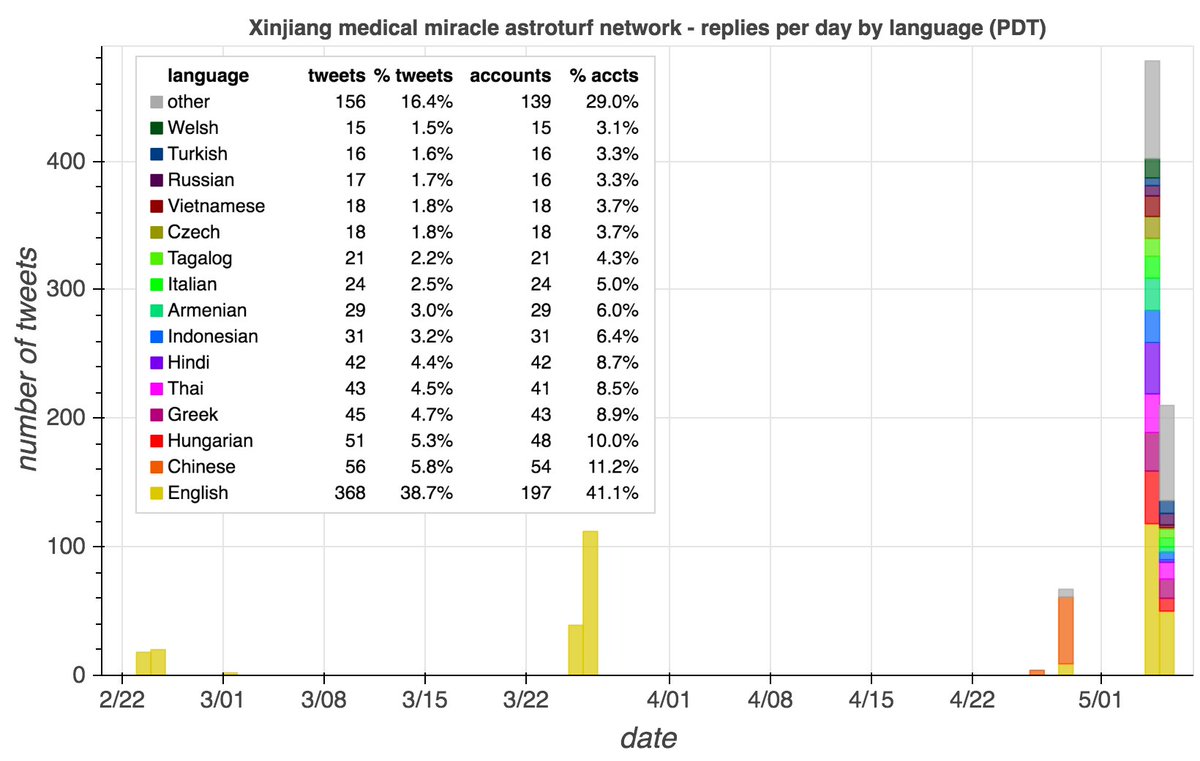
This network's duplicate tweets are almost all political in nature, with criticism of the governments of China and Pakistan as the primary themes. Most of the duplicated tweets were tweeted first by either @Right_n_Aware or @ProwessSilent. 

The majority of this network's content is cloned tweets - 10428 of 16884 tweets (62.5%) are duplicates, and 4690 (28.1%) were tweeted verbatim by at least 10 accounts. The copies of a given tweet are generally all tweeted within a few hours of one another. 

In addition to tweeting the same tweets, the accounts in this network also all have follow relationships with other members of the network (generally multiple). While we can't tell whether the tweet duplication is automated or human activity, it does appear coordinated. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh