Even @VitalikButerin can't escape the monsters of the dark forest
Twitter wasn't the only party watching Vitalik's wallet. As always bots were ready to extract what value they could from his pending transactions.
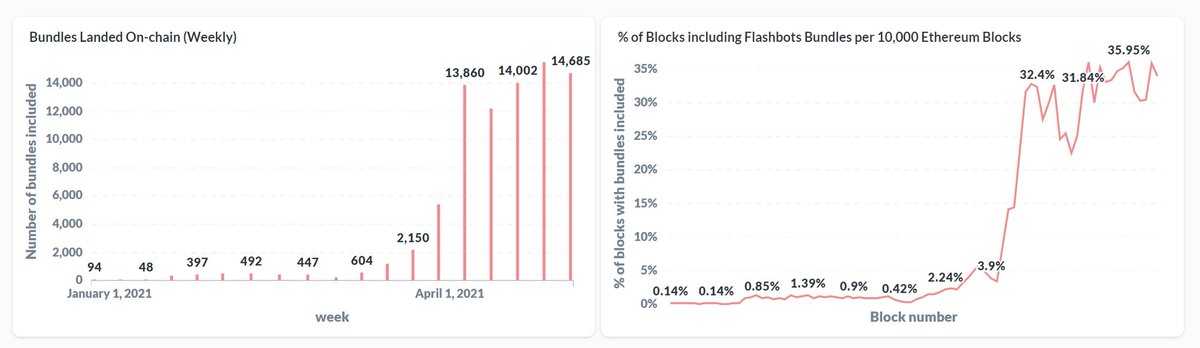
Brief recap of those bots and what Vitalik did
Twitter wasn't the only party watching Vitalik's wallet. As always bots were ready to extract what value they could from his pending transactions.
Brief recap of those bots and what Vitalik did
Earlier today Vitalik sold his Shibu on Uniswap, and @FrankResearcher documents that adventure well
https://twitter.com/FrankResearcher/status/1392532831889395713
Normally when you swap on Uniswap the transaction is publicly relayed through nodes until it reaches miners. Due to this anyone who wants to can see the transaction before it is mined.
Bots watch for these transactions before they are mined and try to extract money from them.
This is how "sandwich bots" find their victims.
This is how "sandwich bots" find their victims.
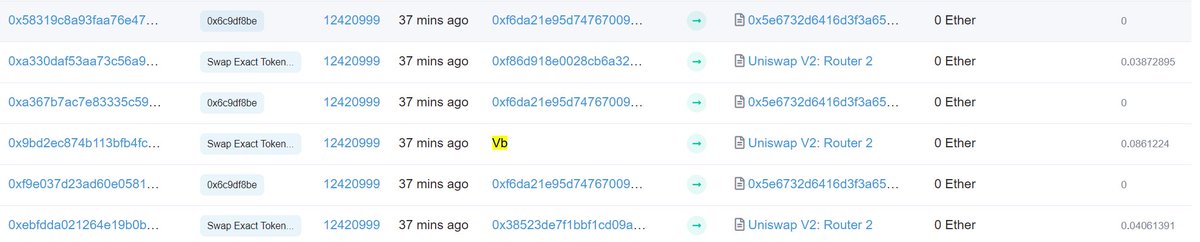
Here's what a sandwiched transaction looks like:
🥪 gets ahead of it, buying up a token to raise the price for the victim
Victim executes their swap, now getting less tokens but raising the price more
🥪 sells their tokens at the elevated price, pocketing a profit
🥪 gets ahead of it, buying up a token to raise the price for the victim
Victim executes their swap, now getting less tokens but raising the price more
🥪 sells their tokens at the elevated price, pocketing a profit

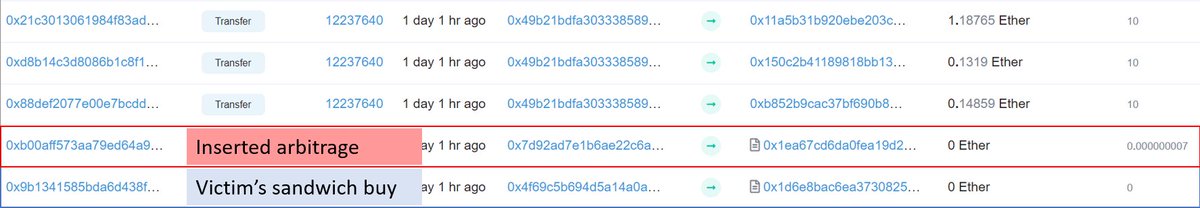
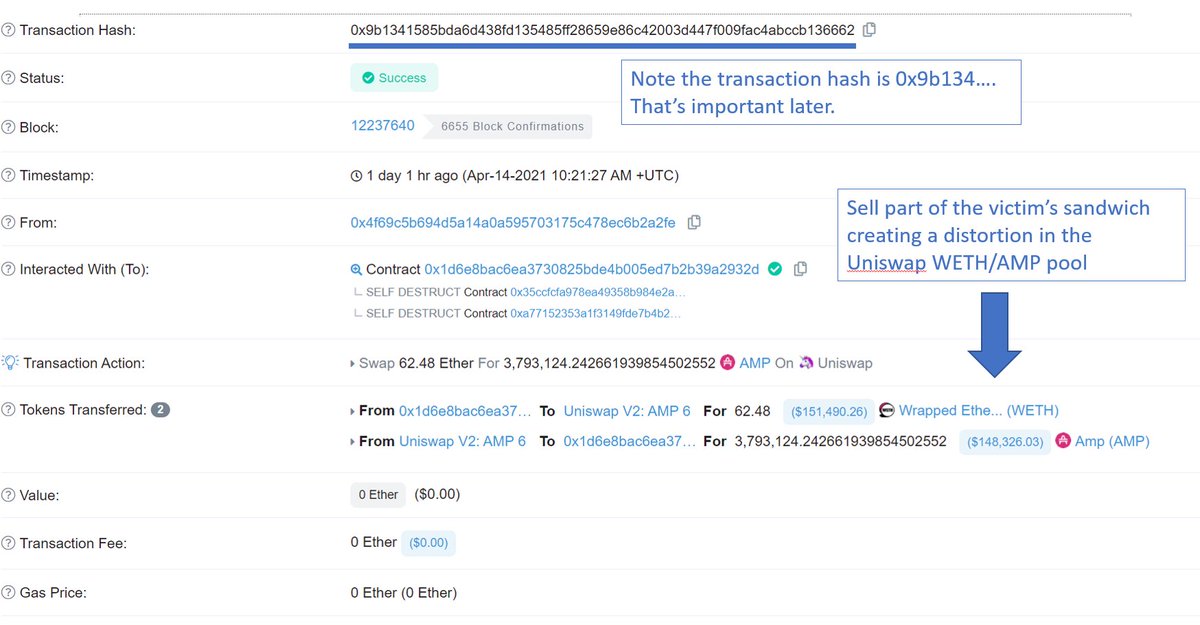
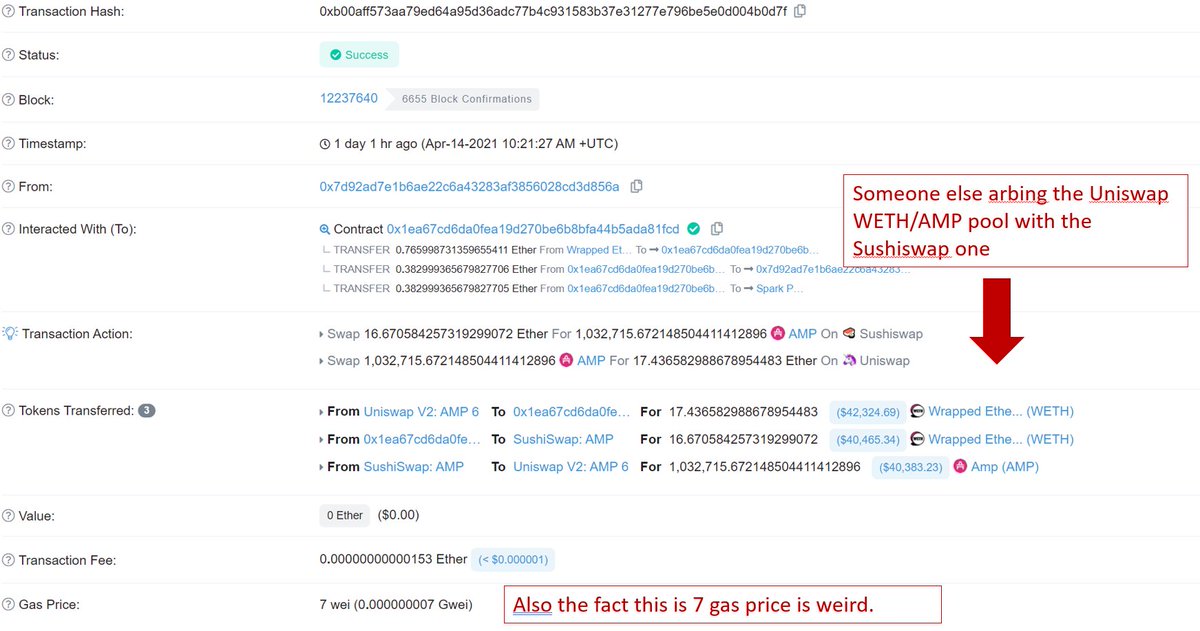
Alternatively in some cases it makes sense for bots to land right behind a pending transaction and arbitrage away any profit made from potential distortions.
Ethermine's backrunning bot landed an impressive 3 arbs this way, including behind Vitalik's tx
Ethermine's backrunning bot landed an impressive 3 arbs this way, including behind Vitalik's tx
https://twitter.com/bertcmiller/status/1392548862146007046
Vitalik had 4 transactions fail at an eye watering ~1000 gwei gas price and was probably mindful of the aforementioned sandwich bots that could making be making his transactions fail.
So what did he do about it?
So what did he do about it?

Recall that bots watch for pending transactions while they are in flight to miners. In order to sandwich a trade it needs to be made public.
So what if transactions were sent directly to miners instead of through full nodes where anyone could see them?
So what if transactions were sent directly to miners instead of through full nodes where anyone could see them?
That is the basic premise behind new products like Flashbots, Taichi, MistX, or ArcherSwap: provide a direct line to miners so users can't be frontrun.
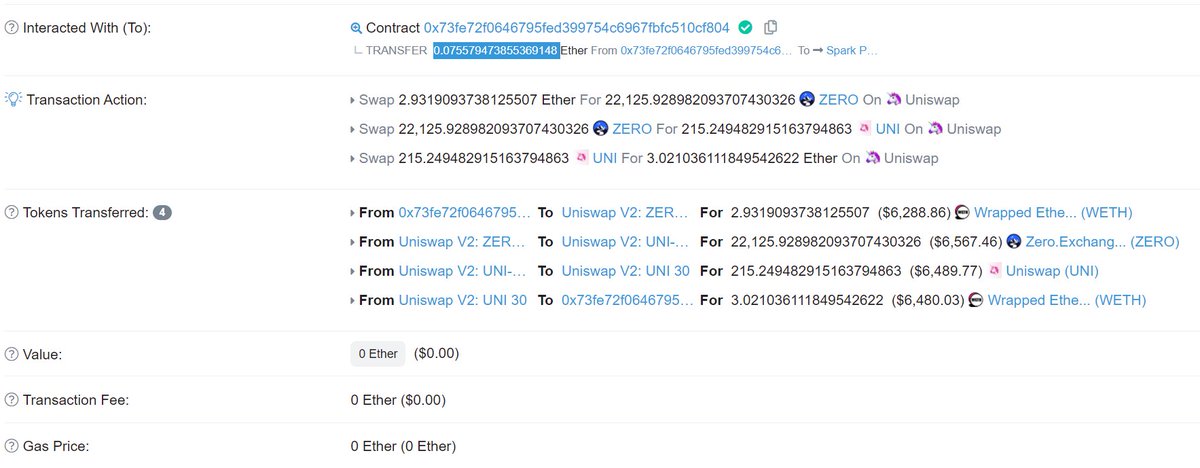
Vitalik used ArcherSwap to sell some of his Shibu earlier, and his transaction then succeeded where they had previously failed.
Read more about ArcherSwap in @calebsheridan's tweets below
etherscan.io/tx/0x11730fc49…
Read more about ArcherSwap in @calebsheridan's tweets below
etherscan.io/tx/0x11730fc49…
https://twitter.com/calebsheridan/status/1384811452402442240
ArcherSwap is built using a fork of MEV-Geth and MEV-Relay - two codebases from Flashbots Research.
ArcherSwap routes trades to miners on the Archer Network, which in this case was mined 2miners.
etherscan.io/block/12421138
ArcherSwap routes trades to miners on the Archer Network, which in this case was mined 2miners.
etherscan.io/block/12421138
At Flashbots we're super excited by innovation like this that provides better experiences (e.g. frontrunning protection and creative use cases) and outcomes (better prices) for users.
To get involved check out our Github and Discord here:
github.com/flashbots/pm
To get involved check out our Github and Discord here:
github.com/flashbots/pm
Lastly, as @mevalphaleak points out, Vitalik got backrun and not 🥪ed because of how 🥪 ing works.
Since Vitalik was selling Shibu a 🥪 bot would have needed to be holding a ton of Shibu to 🥪 him. As a result, only backrunning was possible.
Since Vitalik was selling Shibu a 🥪 bot would have needed to be holding a ton of Shibu to 🥪 him. As a result, only backrunning was possible.
https://twitter.com/mevalphaleak/status/1392555062367563777
• • •
Missing some Tweet in this thread? You can try to
force a refresh