NEW: Chicago police used CIA-backed Oracle software to surveil protesters and mine their Twitter feeds.
Oracle then peddled that same software for police work in China.
I bring you a tale of global surveillance. 1/ theintercept.com/2021/05/25/ora…
Oracle then peddled that same software for police work in China.
I bring you a tale of global surveillance. 1/ theintercept.com/2021/05/25/ora…
CPD used Oracle's software, which was funded by CIA venture capital firm In-Q-Tel, to surveil protesters during the 2012 NATO summit in Chicago.
The software purportedly mined thousands of tweets an hour, flagged "negative" tweets, and kept them even if deleted. 2/
The software purportedly mined thousands of tweets an hour, flagged "negative" tweets, and kept them even if deleted. 2/

Oracle documents boast that the CIA-backed software, Endeca, could help police sift through data in search of unknown threats (what Donald Rumsfeld famously called "unknown unknowns").
Civil liberties advocates have something to say about that. 3/ theintercept.com/2021/05/25/ora…
Civil liberties advocates have something to say about that. 3/ theintercept.com/2021/05/25/ora…
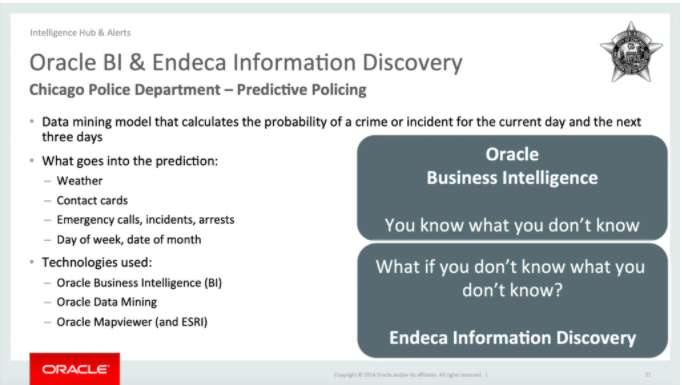
People have compared Endeca to Palantir Gotham. Like Palantir, it's used extensively by government agencies - including at Guantánamo. A full list of GTMO awards is here, thanks to @tech_inquiry. techinquiry.org/explorer/searc… 4/
After marketing the software to US police, Oracle took it overseas and promoted it for invasive surveillance work in China. 5/ theintercept.com/2021/05/25/ora…
Oracle documents marked "CONFIDENTIAL" peddle Endeca and other software for use by Chinese public security entities - for behavioral and language analysis, for example. 6/ theintercept.com/2021/05/25/ora… 

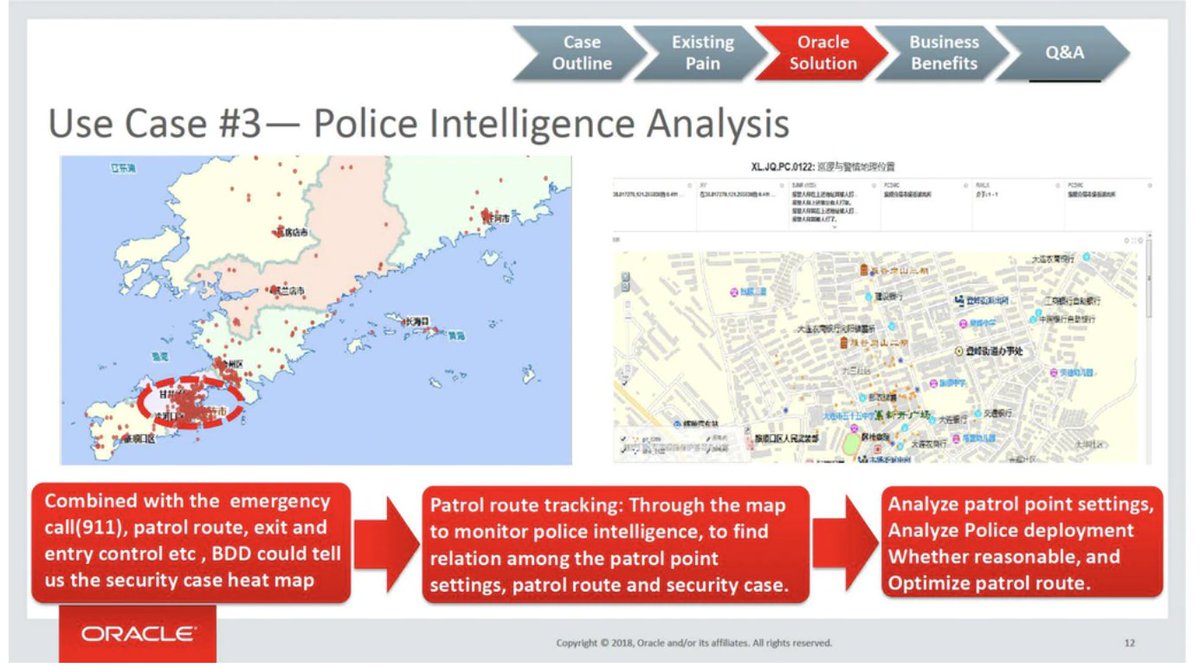
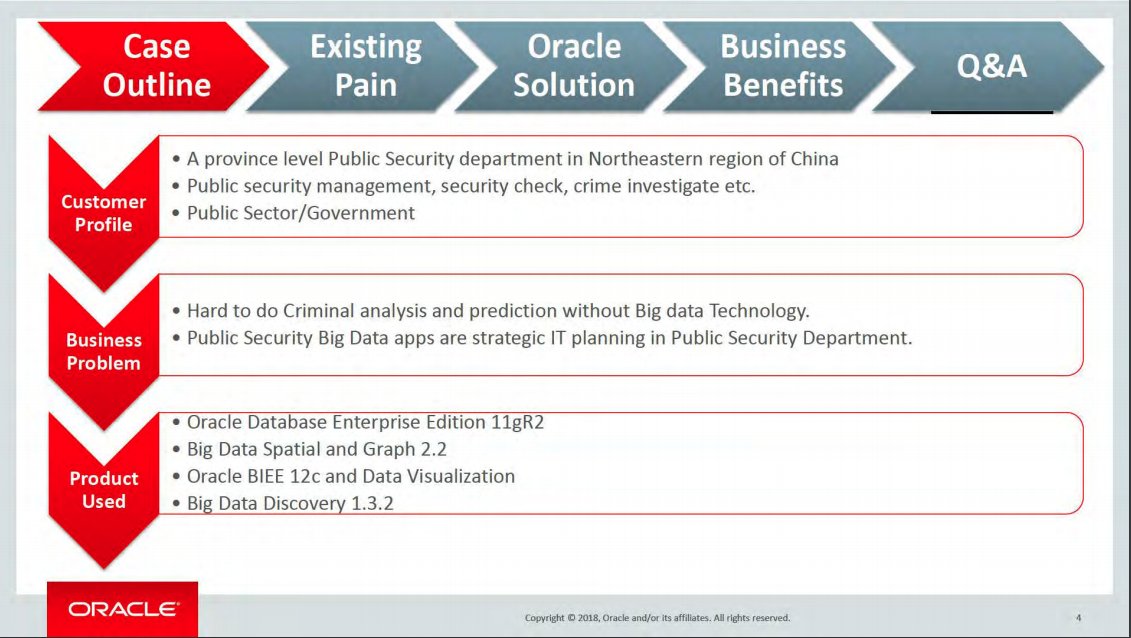
Oracle later rolled Endeca functionality into Big Data Discovery. A slide deck given at a 2018 conference in California says police in Liaoning province used Big Data Discovery to do crime analysis and create heat maps. 7/ theintercept.com/2021/05/25/ora… 
Please read the story! And if you missed our earlier coverage of Oracle's policing tech, it is collected here. 8/ theintercept.com/collections/or…
If you have worked with Oracle or have details about how its products are used by police, ping me on Signal at +1 651-400-7987 or write me securely at marahv at protonmail. You can remain anonymous. ⌨️ 9/
• • •
Missing some Tweet in this thread? You can try to
force a refresh