
I'm really excited to share that our newest online class, Detection Engineering with Sigma, is open this morning. You can learn more and register at learnsigmarules.com.
The course is discounted for launch until next Friday.
The course is discounted for launch until next Friday.

If you're not familiar with @sigma_hq, you should be! It's the open standard detection signature format for logs. Said another way, Sigma is for logs what Snort/Suricata are for network traffic and YARA is for files.
Perhaps the best thing about Sigma is that you can easily convert its rules into LOTS of other formats using the Sigmac tool. Things like Elastic, Splunk, Graylog, NetWitness, Carbon Black, and so on. 
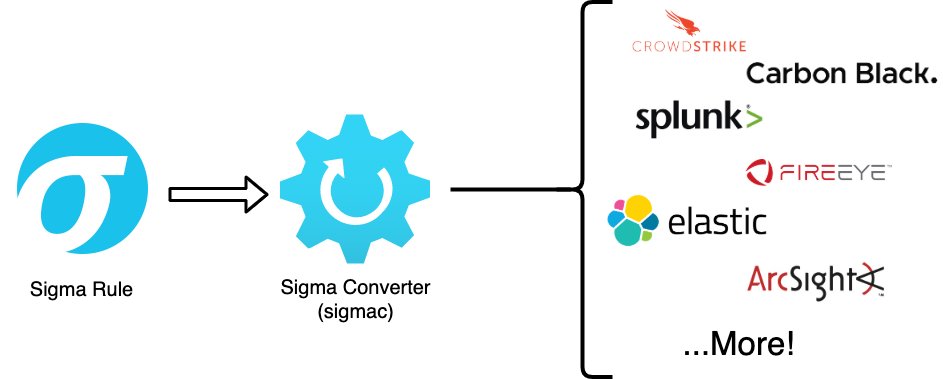
With that conversion ability, you can easily add Sigma signatures to whatever detection tools you use, quickly jump into investigations when you get alerts from your rules, or use the rules for hunting input.
In this course, you learn about Detection Engineering, which is the process of researching threats and then building and tuning tools that find them. You'll start with a detection gap and go through the steps to build and test detection rules that fill them.
You'll deep dive into Sigma syntax and eventually complete several real world case studies using a variety of log sources. We give you a VM with the logs on them so you can practice developing and tuning your rules.
You'll also learn about Sigma in production. We'll show you how to manage a rule set with Git, how to interact with Sigma on the command line, some Sigma integrations, and how to contribute rules to the public Sigma repository (once you're comfortable with that).
The primary instructor for this course is @DefensiveDepth, who also worked with on the @NetworkDefense Osquery course. I think he did a great job building a super accessible detection engineering course that the industry needs.
My favorite aspect of this course is that there are lots of opportunities for FEEDBACK. When you write and submit rules, Josh will help you refine them as necessary to ensure you're on the right track. You're not alone.
You can read more about the Detection Engineering with Sigma course here: learnsigmarules.com. The course is discounted for launch until next Friday. We're looking forward to seeing you there.
The analyst in me is most excited that this course will help spread the adoption of @sigma_hq. It's grown a lot over the past few years and I think that's been a really positive thing for the detection and investigation side of our industry.
• • •
Missing some Tweet in this thread? You can try to
force a refresh



