Microsoft had a call for #PrintNightmare where they repeatedly said "Disable Point and Print"
without actually saying how one would do so.
I cannot find evidence that "Point and Print" itself is a thing that can be disabled.
MS seems to really want someone to hold their beer!
🍺
without actually saying how one would do so.
I cannot find evidence that "Point and Print" itself is a thing that can be disabled.
MS seems to really want someone to hold their beer!
🍺
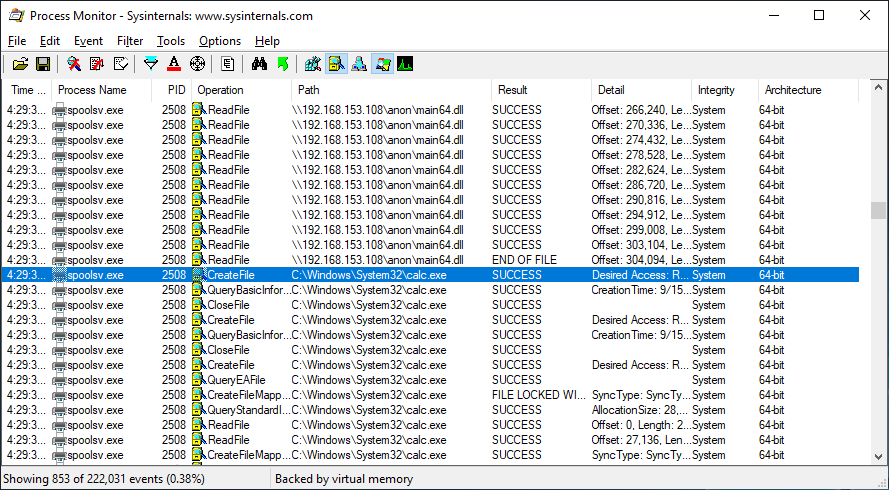
https://twitter.com/TheRyanDallas/status/1412848563483295747
Is "Disable Point and Print" a thing that people can do? And if so, how?
Otherwise, I'll attribute this all to an unfortunate game of telephone.
Otherwise, I'll attribute this all to an unfortunate game of telephone.
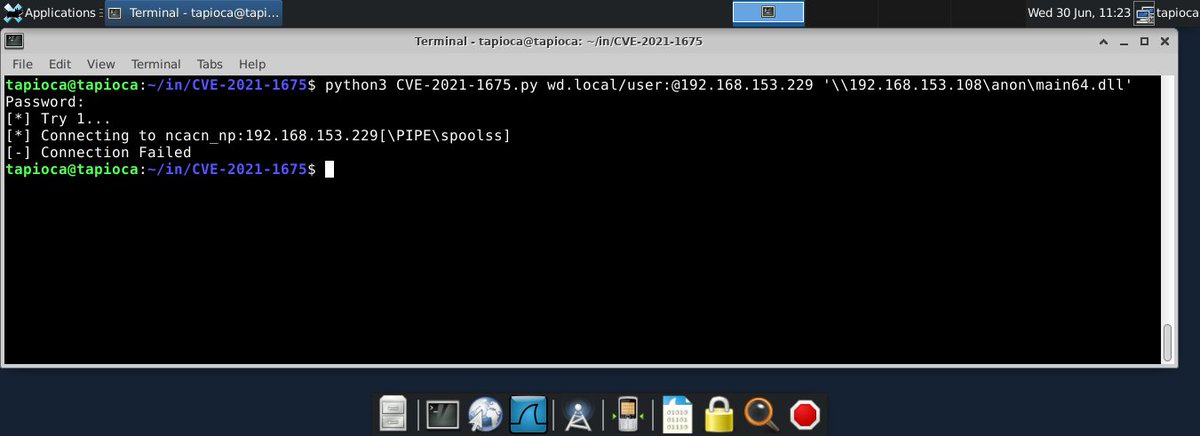
More along the lines of Microsoft confusion:
"NoWarningNoElevationOnUpdate" isn't a term that existed until Microsoft published their CVE-2021-34527 advisory on July 6.
The registry value actually associated with updating drivers is called UpdatePromptSettings



"NoWarningNoElevationOnUpdate" isn't a term that existed until Microsoft published their CVE-2021-34527 advisory on July 6.
The registry value actually associated with updating drivers is called UpdatePromptSettings




This is my current understanding of the #PrintNightmare exploitability flowchart.
There's a small disagreement between me and MSRC at the moment about UpdatePromptSettings vs. NoWarningNoElevationOnUpdate, but I think it doesn't matter much as I just have both for now.
There's a small disagreement between me and MSRC at the moment about UpdatePromptSettings vs. NoWarningNoElevationOnUpdate, but I think it doesn't matter much as I just have both for now.

I've made a few changes to this flowchart to make it more clear, and also add some more boxes. Because of course.
I also added it to the CERT/CC vulnerability note for #PrintNightmare VU#383432 CVE-2021-34527
kb.cert.org/vuls/id/383432
I also added it to the CERT/CC vulnerability note for #PrintNightmare VU#383432 CVE-2021-34527
kb.cert.org/vuls/id/383432

It seems like the disagreement between MSRC and me has been resolved.
It turns out that it's indeed UpdatePromptSettings, and not NoWarningNoElevationOnUpdate.
NoWarningNoElevationOnUpdate was never a registry value, and no reference to it existed before July 6.
Apology accepted
It turns out that it's indeed UpdatePromptSettings, and not NoWarningNoElevationOnUpdate.
NoWarningNoElevationOnUpdate was never a registry value, and no reference to it existed before July 6.
Apology accepted

For anybody who was watching the recent flurry of incorrect (and now deleted) tweets:
What confused me was that clicking "Apply" on any individual page in gpedit causes EVERY policy to get applied. Not just the current one.
It's still PointAndPrint that is the bypass here.
What confused me was that clicking "Apply" on any individual page in gpedit causes EVERY policy to get applied. Not just the current one.
It's still PointAndPrint that is the bypass here.
• • •
Missing some Tweet in this thread? You can try to
force a refresh