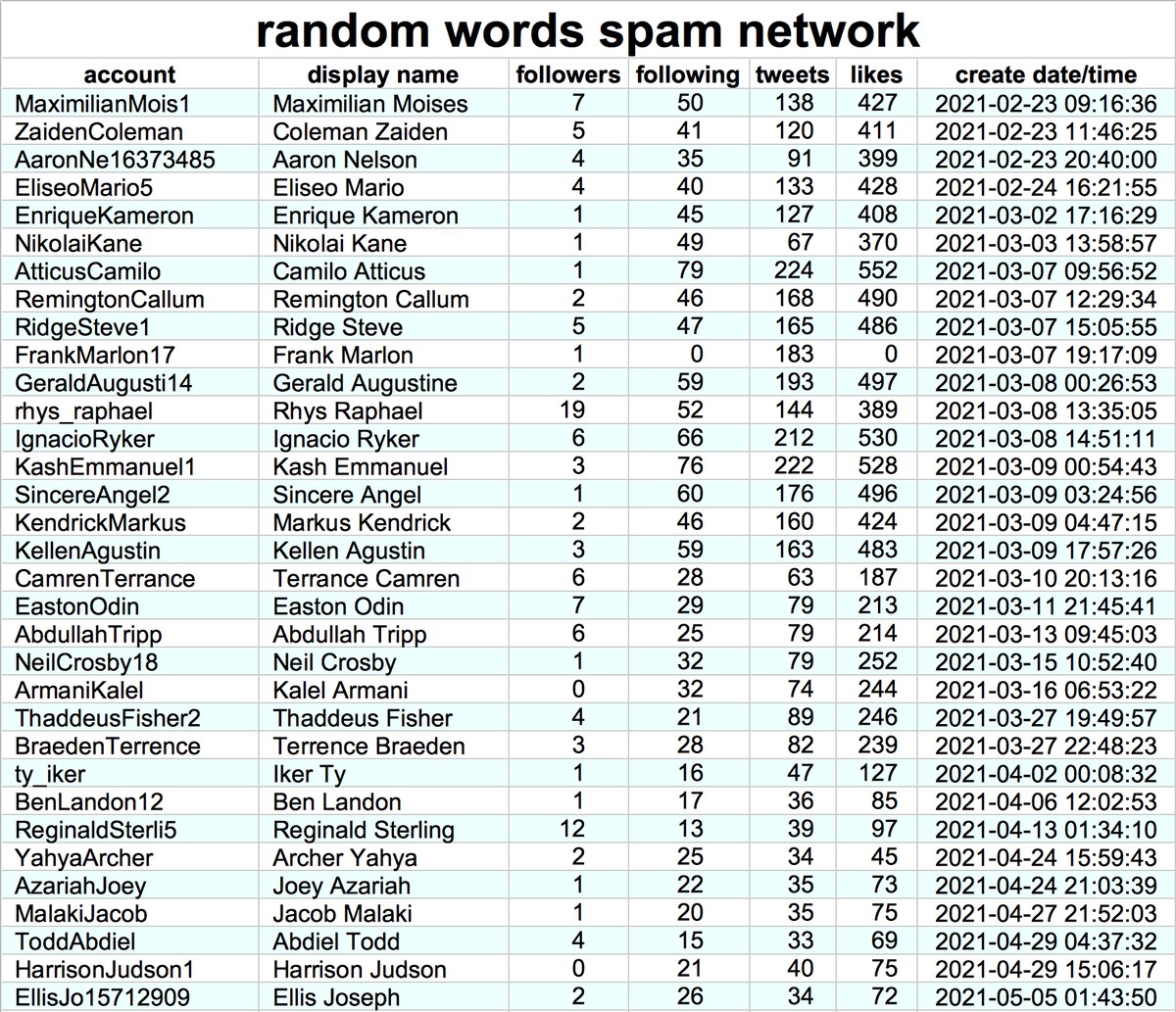
It's a Monday afternoon, which is the perfect time to look at a pornbot network with a penchant attaching random emoji to its repetitive tweets. Also, it spam-followed a rather odd lineup of accounts. #MondayMotivation #Spamtastic
cc: @ZellaQuixote
cc: @ZellaQuixote

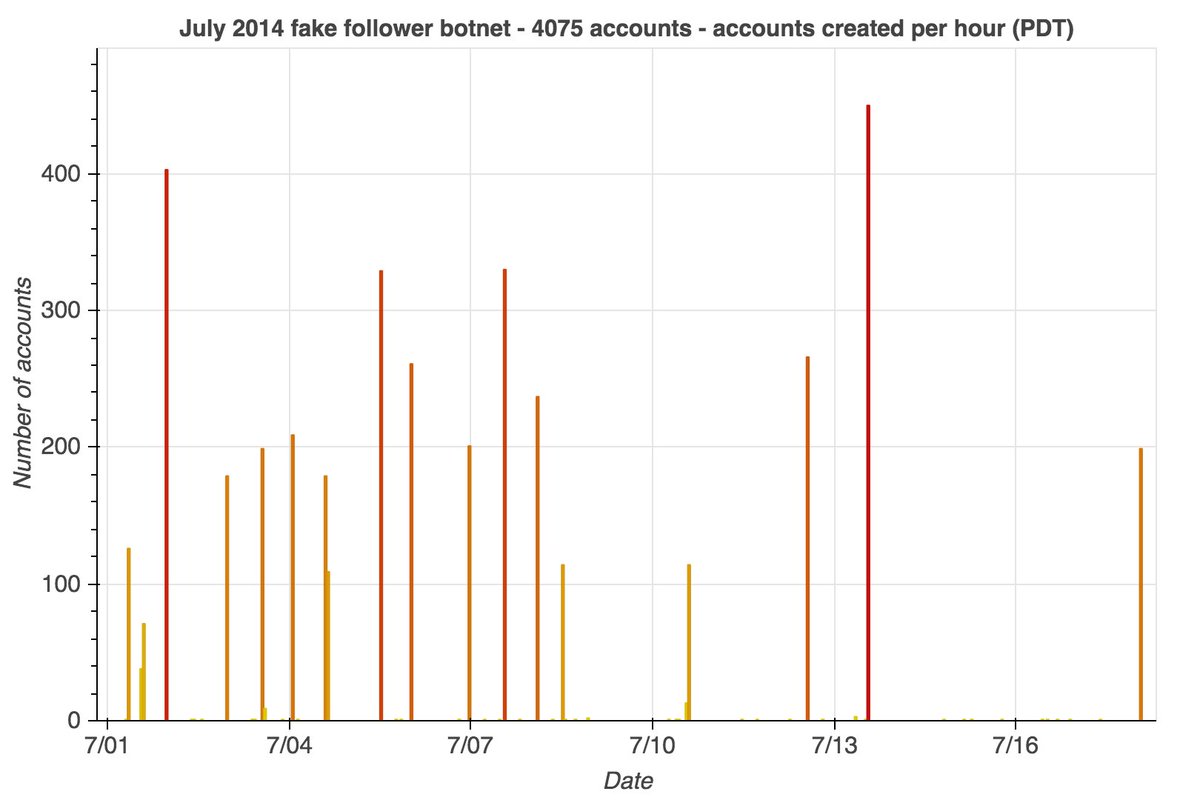
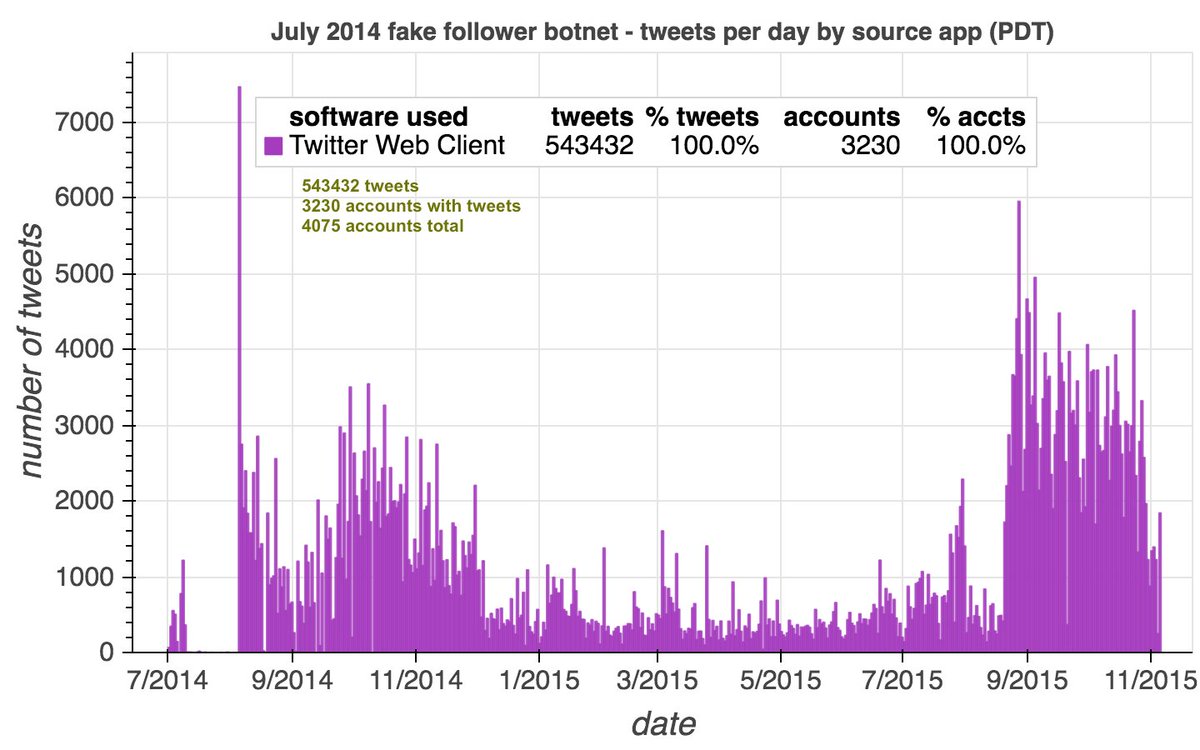
This network consists of (at least) 27745 Japanese-language accounts, created in batches between June 1st and July 25th, 2010. All tweets posted by these accounts so far were (allegedly) sent via the Twitter Web App. None has ever liked a tweet. 




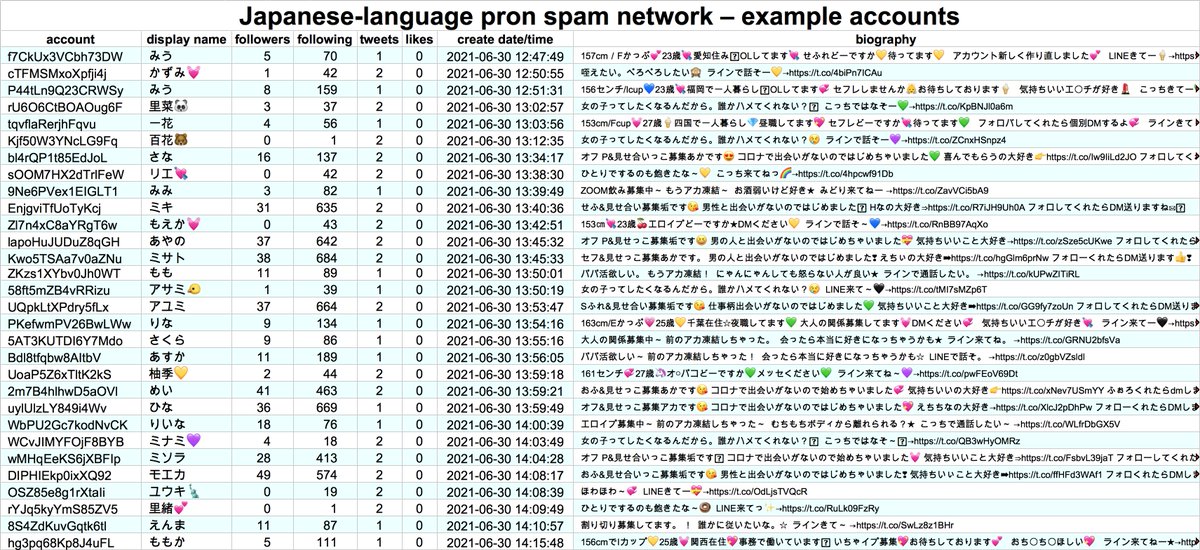


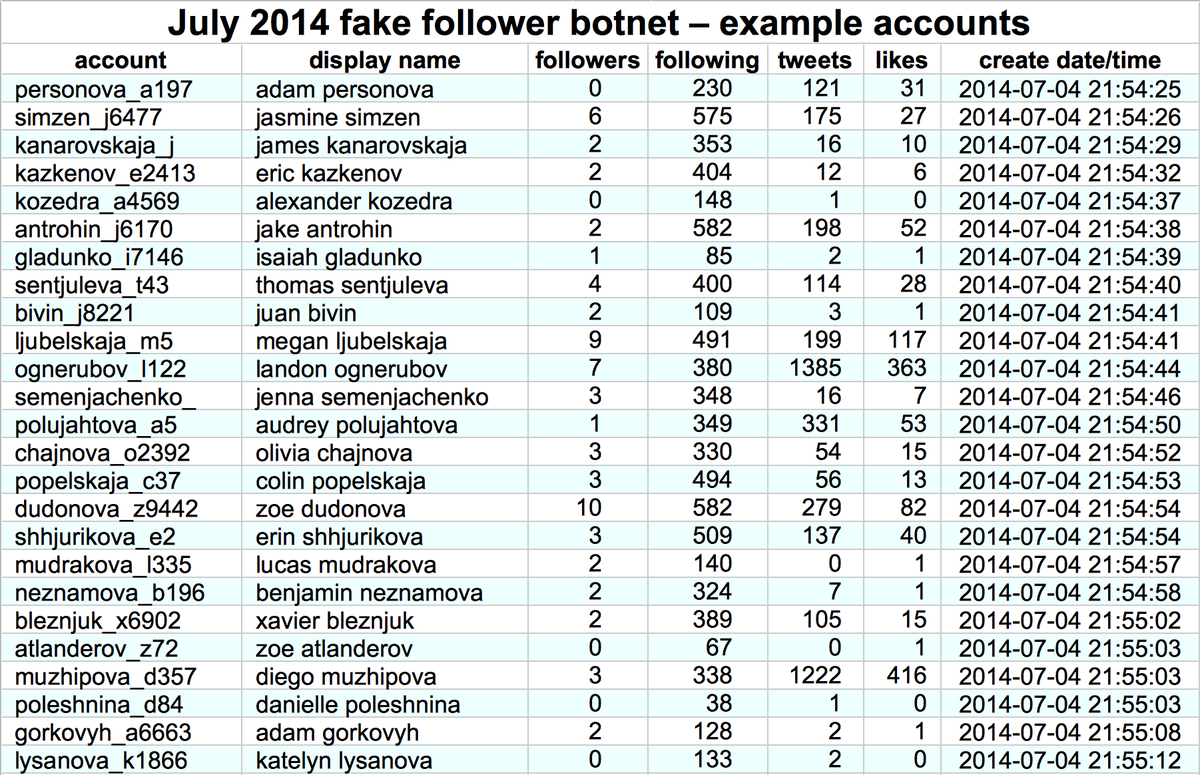
The accounts in this network are extremely repetitive, with the same tweets frequently duplicated verbatim (other than emoji) by dozens of accounts. The accounts' biographies generally include an invitation to chat with unknown parties on the LINE messaging app. 



We've seen botnets that attempt to invite people to chat on the LINE app before:
https://twitter.com/conspirator0/status/1285721234072887299
This botnet reuses profile pics across accounts (4697 unique images for 27745 accounts), with the most common image appearing on 97 different accounts. The images are, unsurprisingly, stolen. 



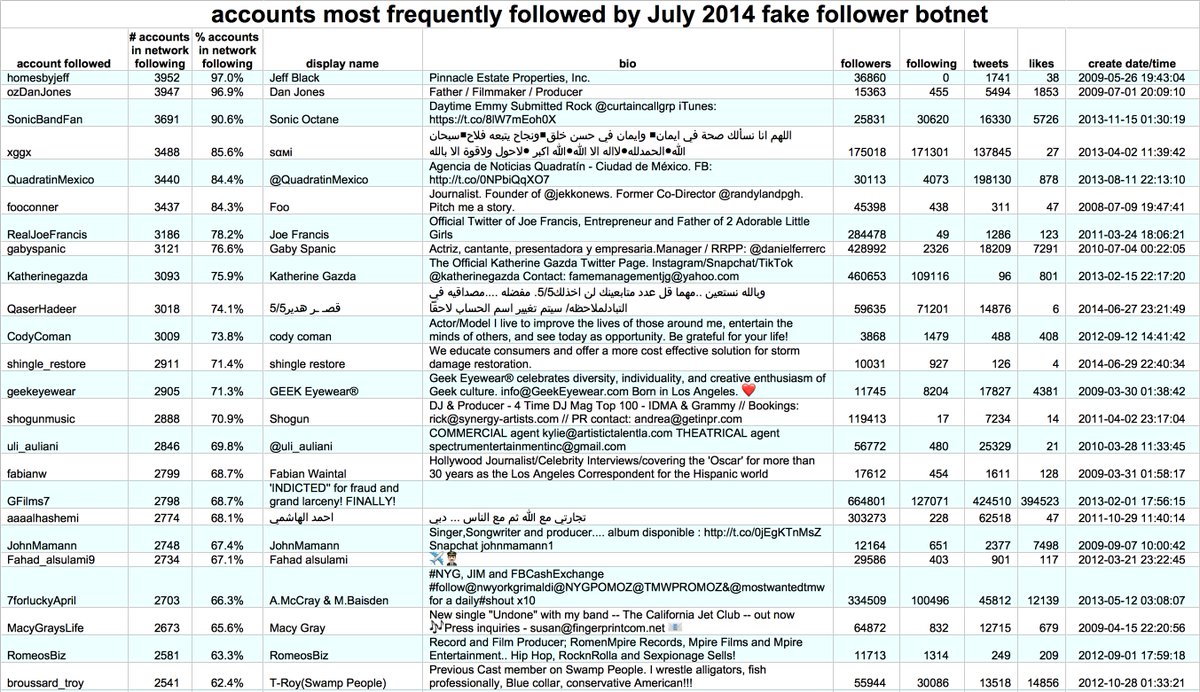
In addition to tweeting repetitive porn spam, this network also followed four accounts en masse: former Belarusian presidential candidate @viktar_babaryka (presently imprisoned), Lithuanian politician @GLandsbergis, @gypsynkov, and @neural_machine (mostly AI-generated tweets). 

• • •
Missing some Tweet in this thread? You can try to
force a refresh