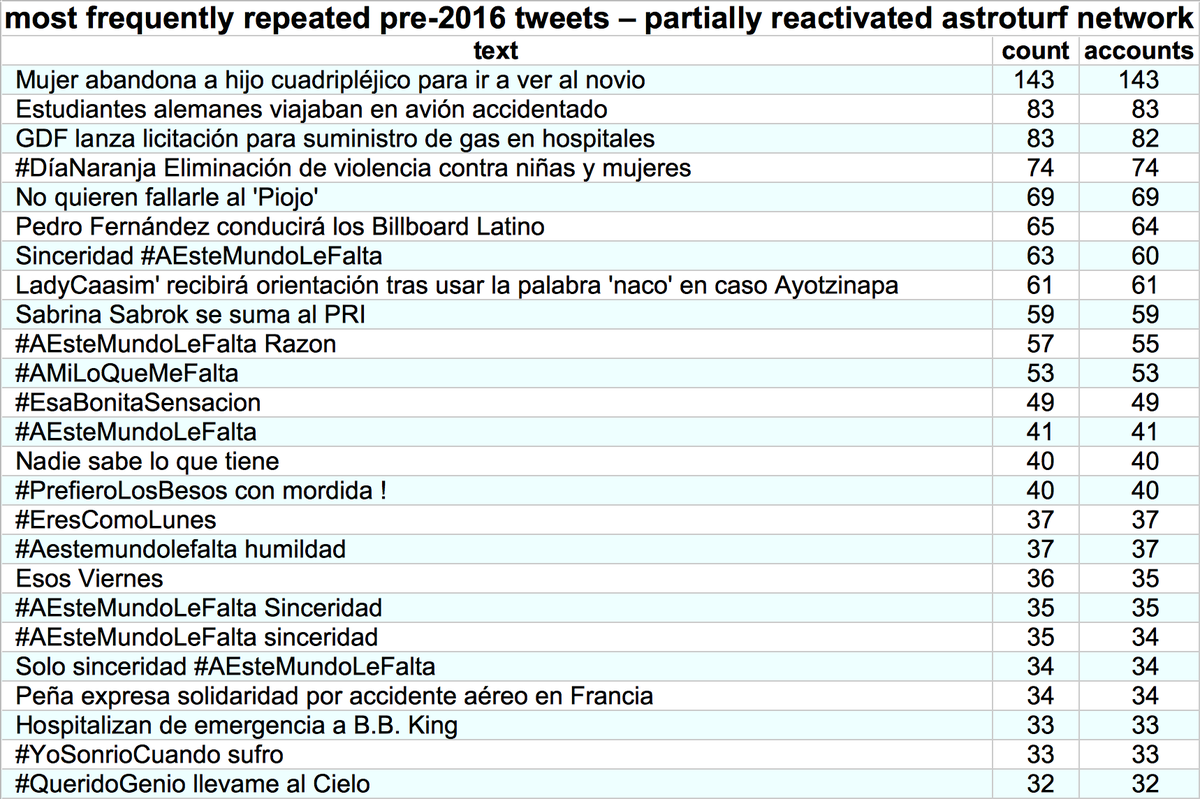
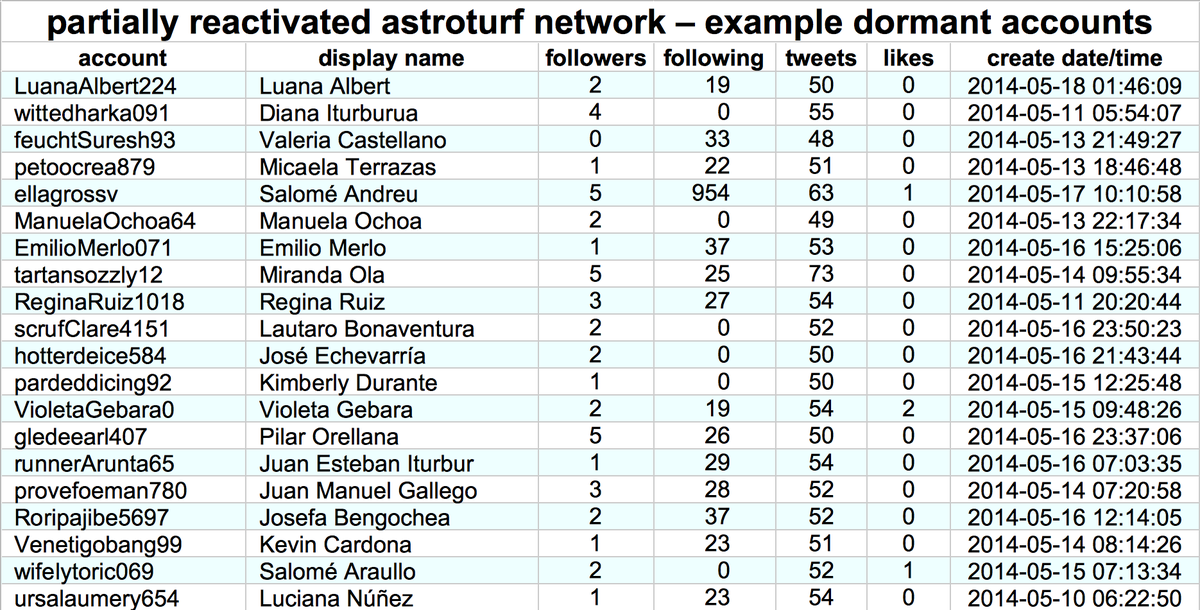
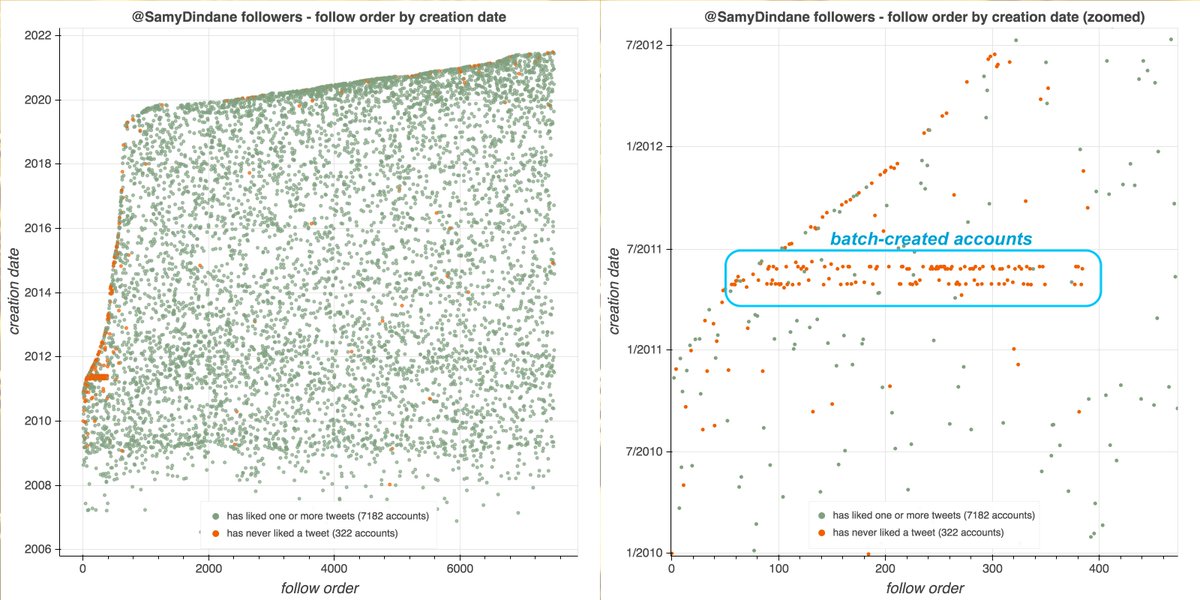
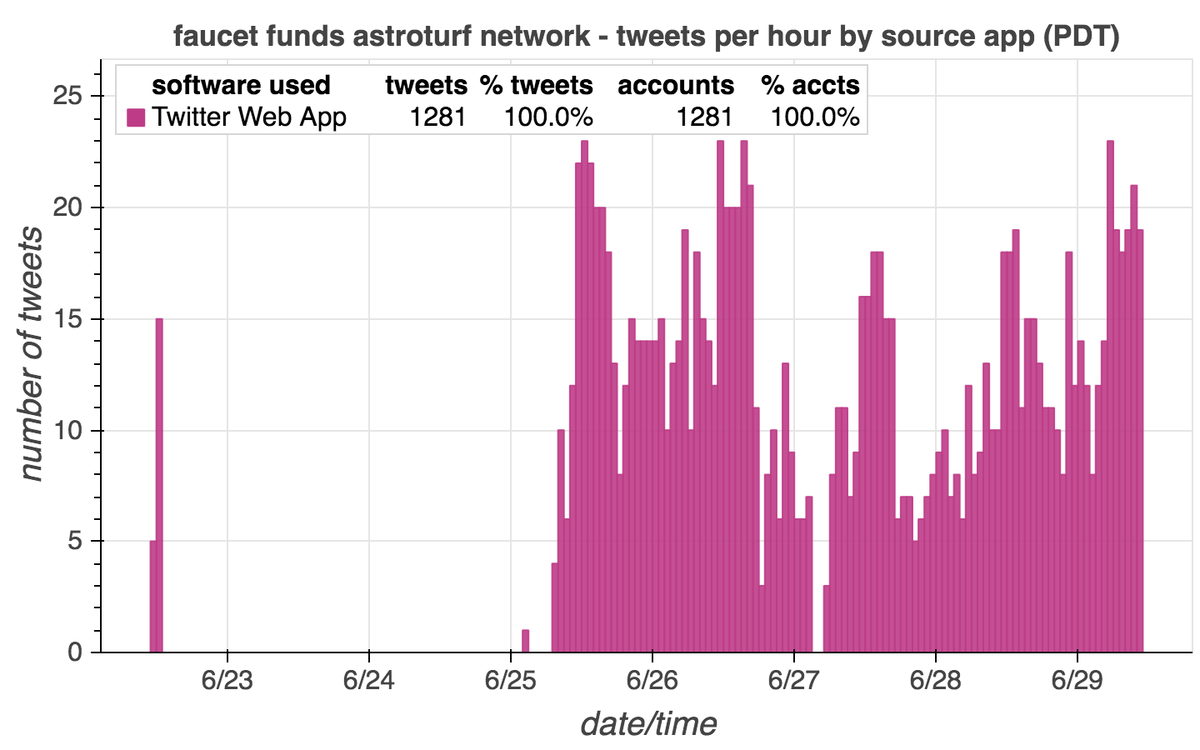
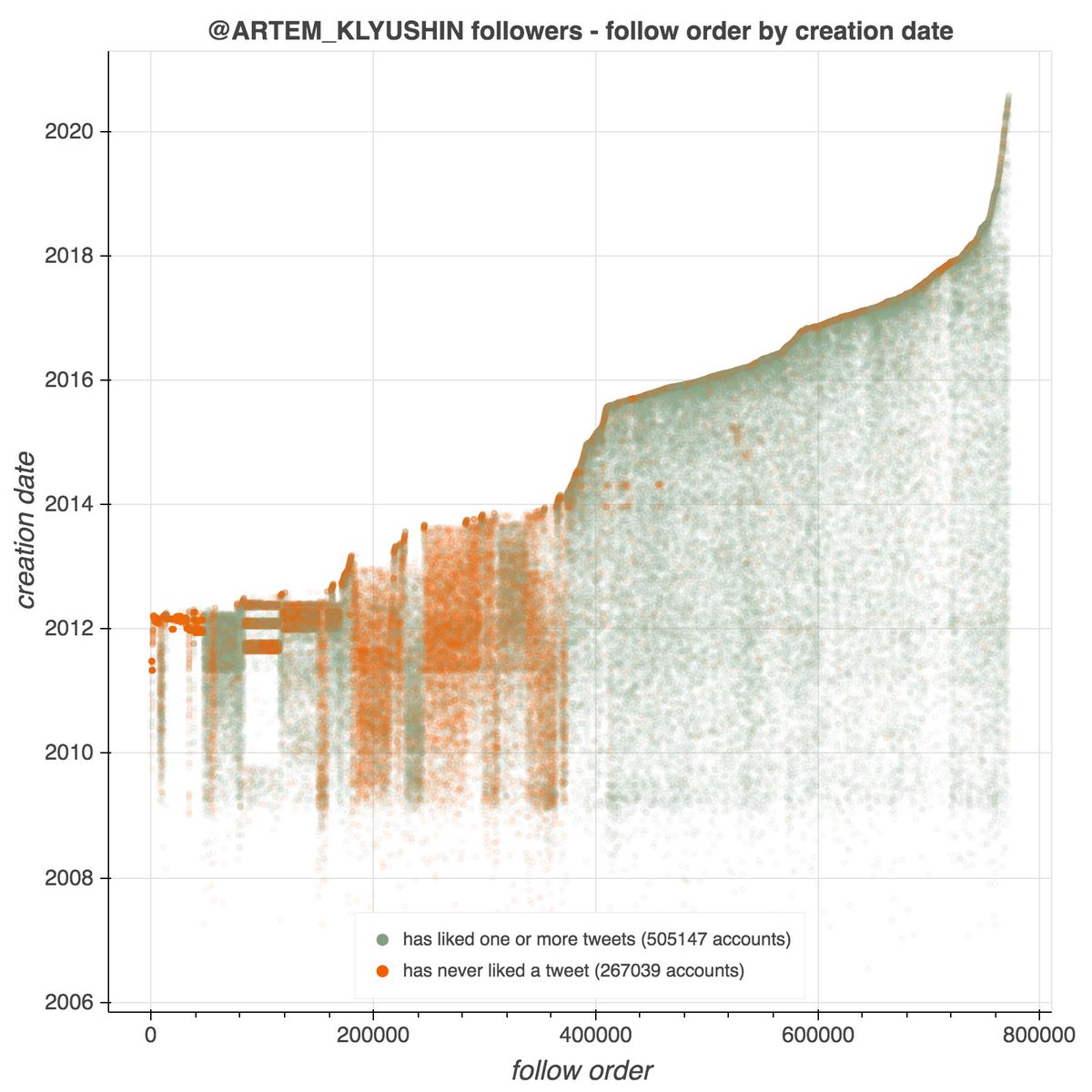
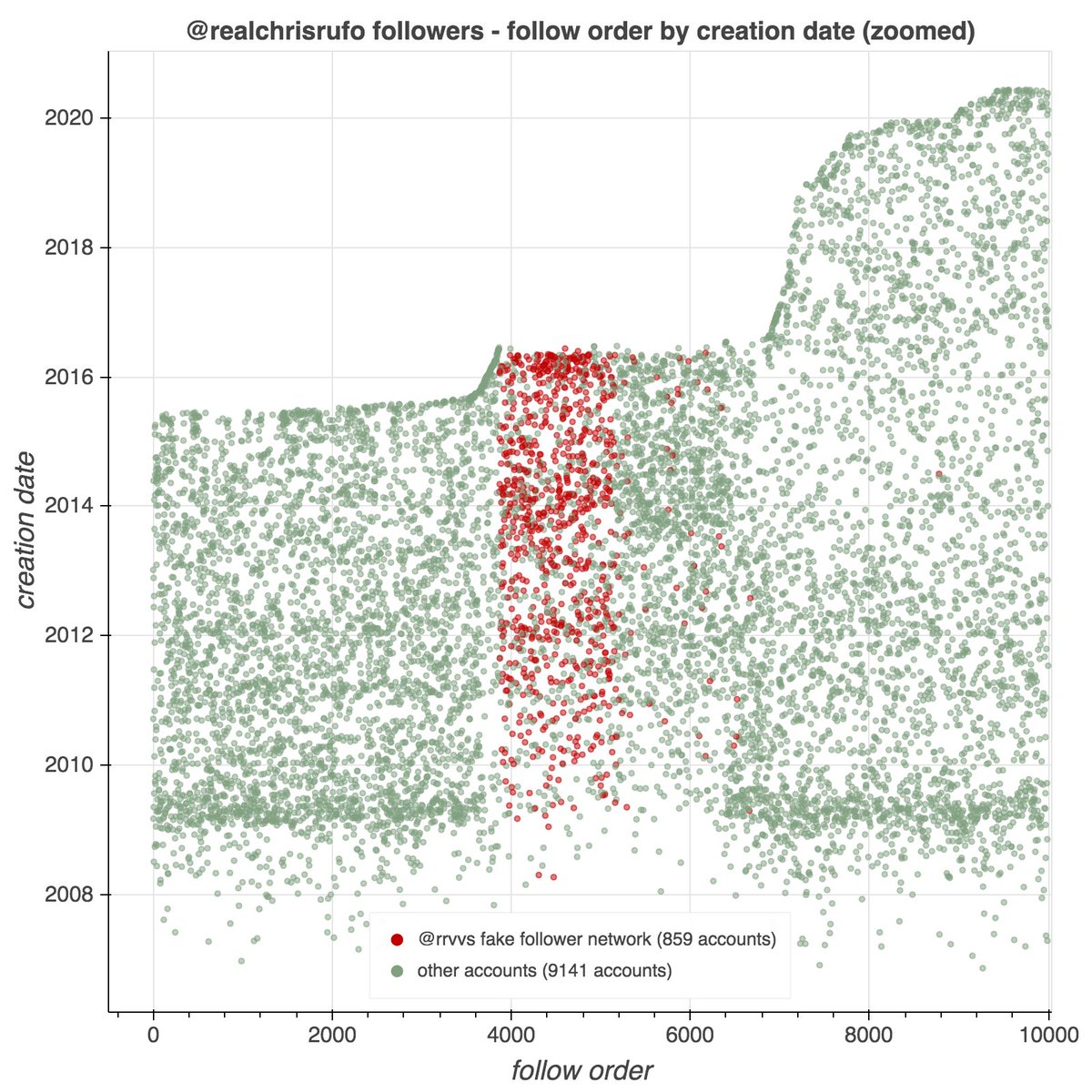
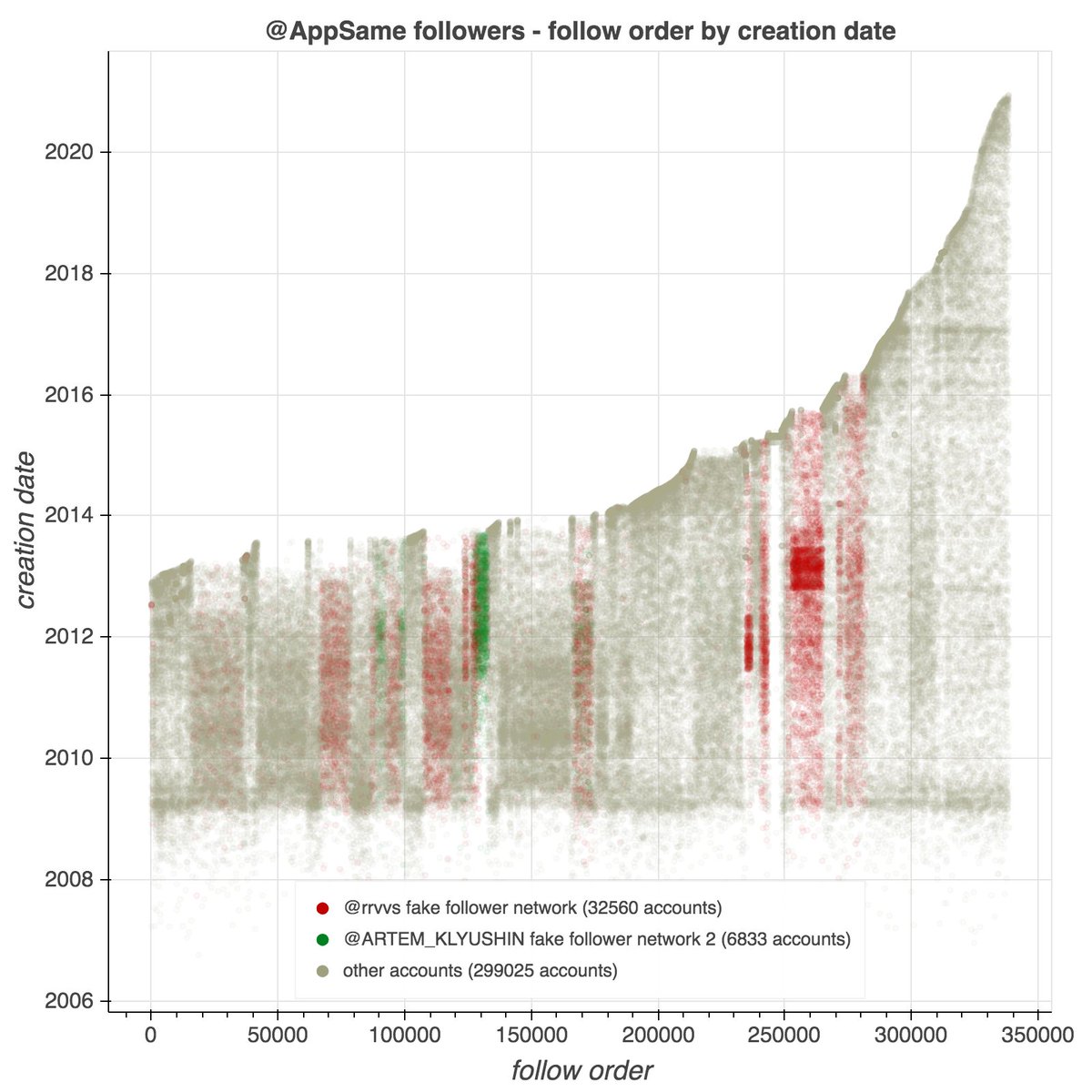
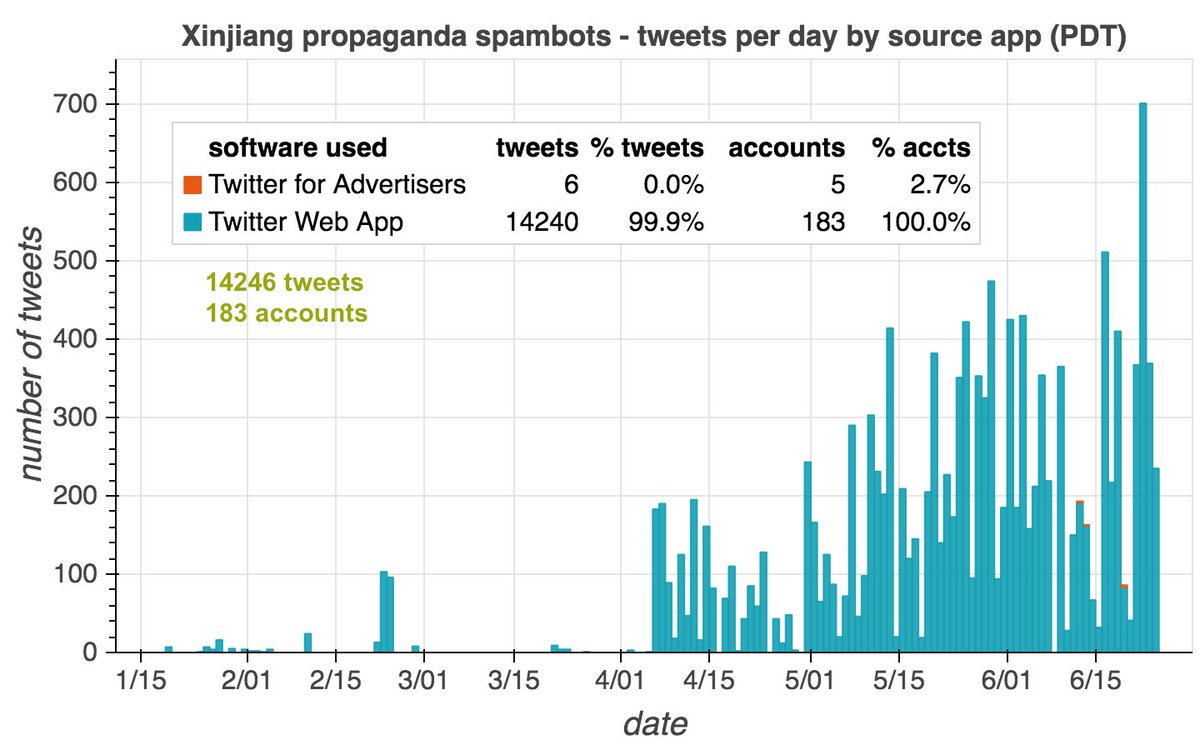
It's a day ending in "y", and a swarm of accounts with GAN-generated face pics is spamming utter nonsense. #YouWontSeeThesePhrasesOnWheelOfFortune #DictionaryShenaniGANs
(GAN = "generative adversarial network", the AI technique used by thispersondoesnotexist.com)
cc @ZellaQuixote
(GAN = "generative adversarial network", the AI technique used by thispersondoesnotexist.com)
cc @ZellaQuixote
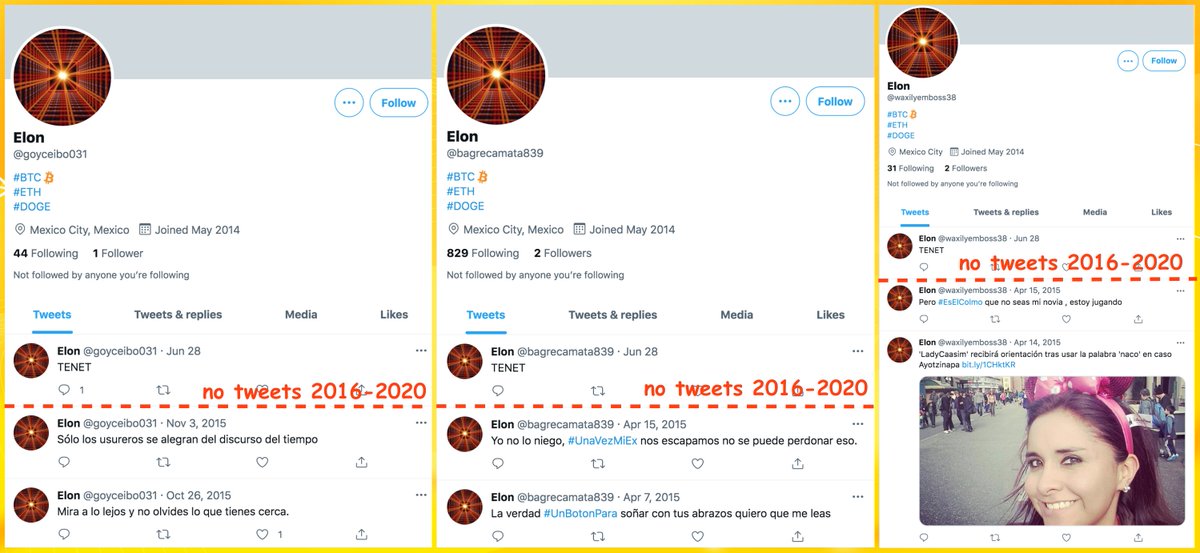
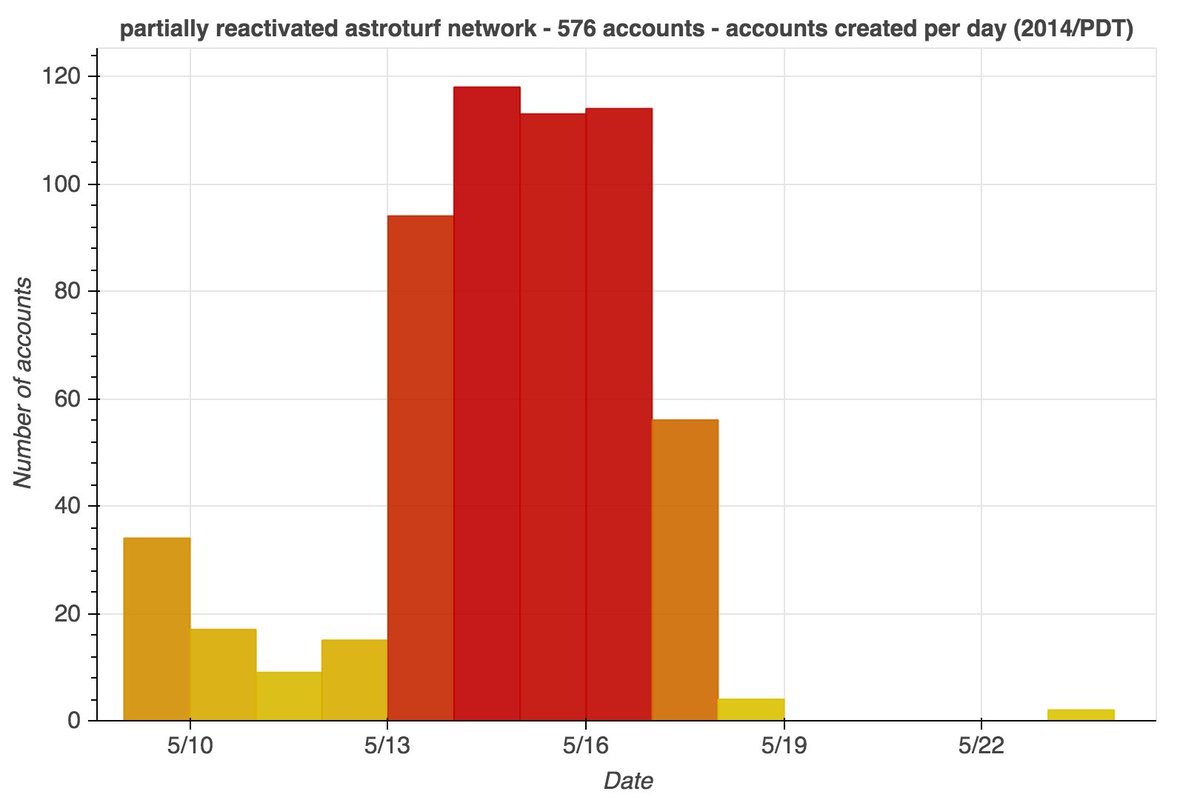
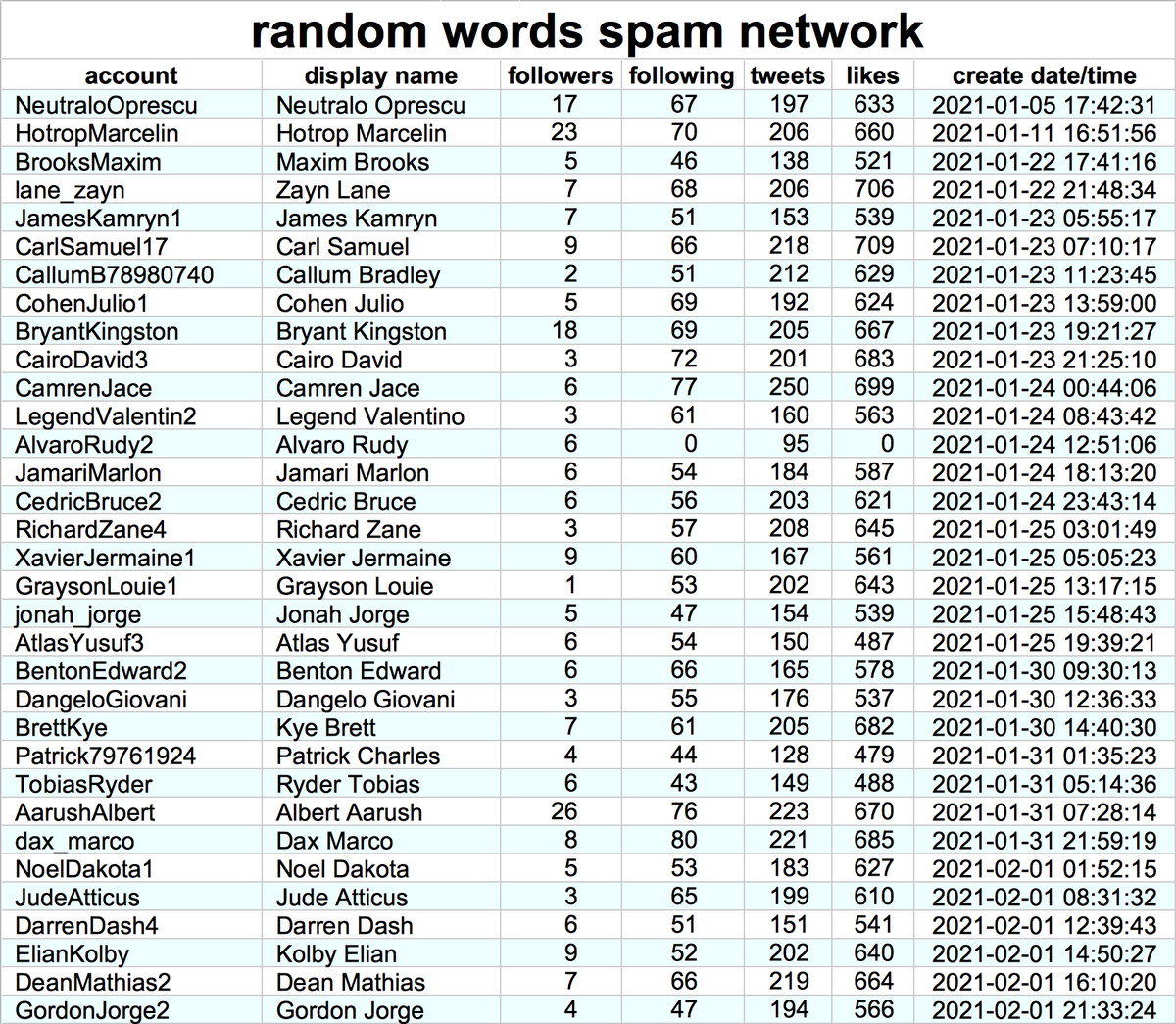
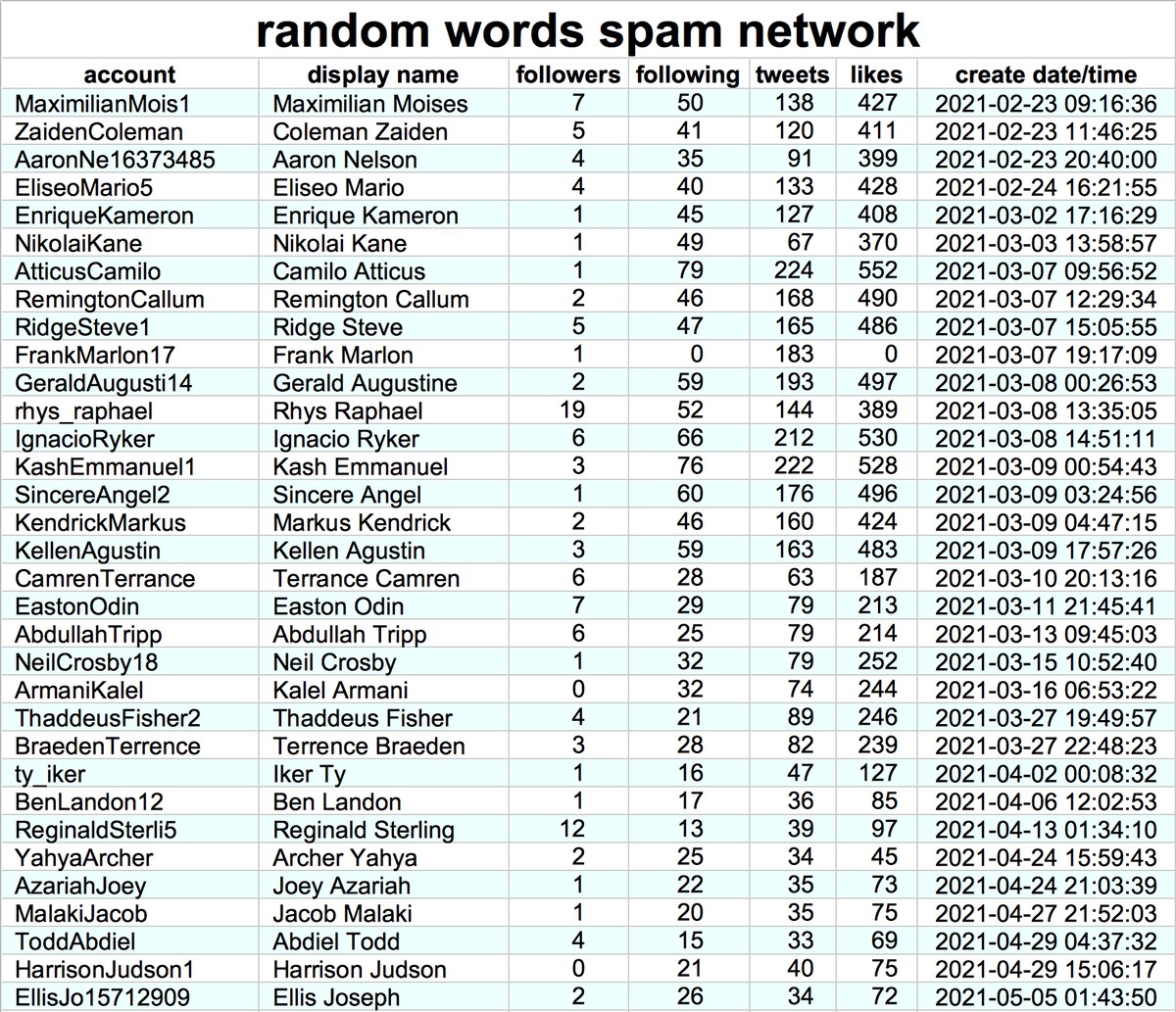
This network consists of 99 accounts, created between January and May 2021. All have first + last name combinations as their display name, handles that match their display names, and all have GAN-generated face images as their profile pics. 





As is the case with unmodified GAN-generated face pics (so far), the primary facial features (especially the eyes) are in the same location on all 99 images. This anomaly becomes obvious when one blends the images together.
More on GAN-generated images and their use on Twitter (and elsewhere) in this thread of threads:
https://twitter.com/conspirator0/status/1322704400226394112
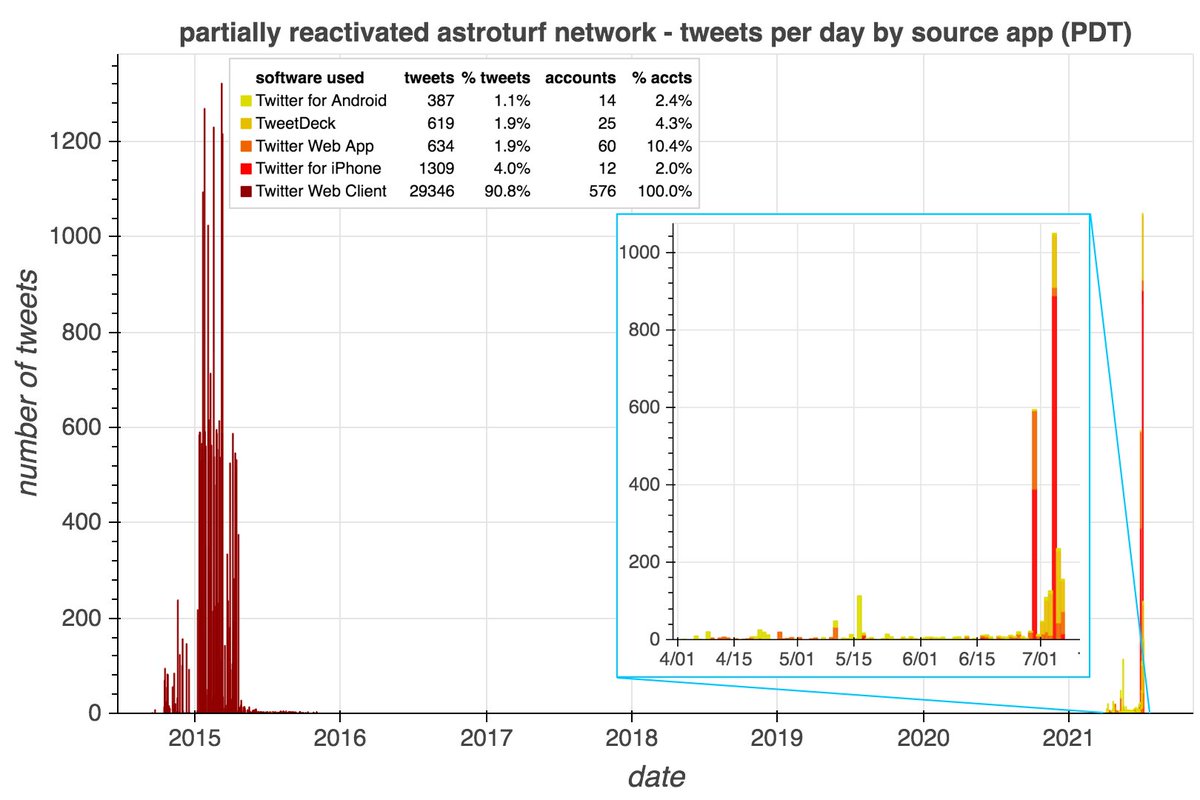
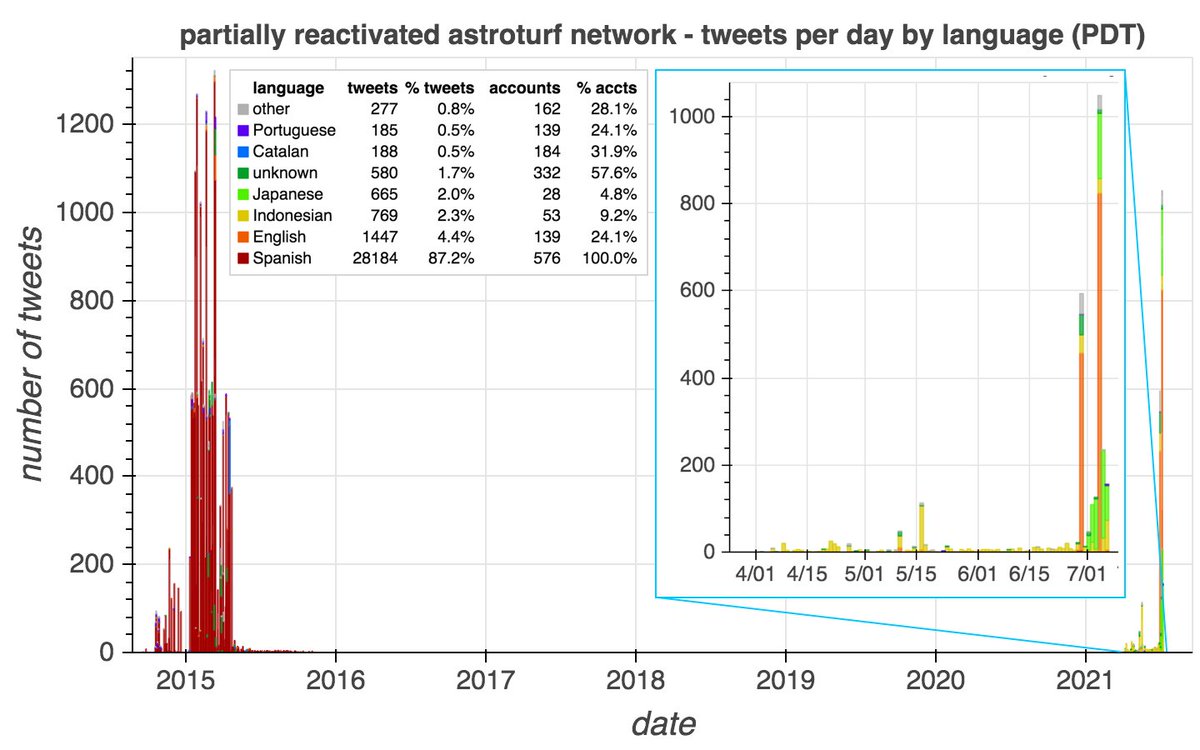
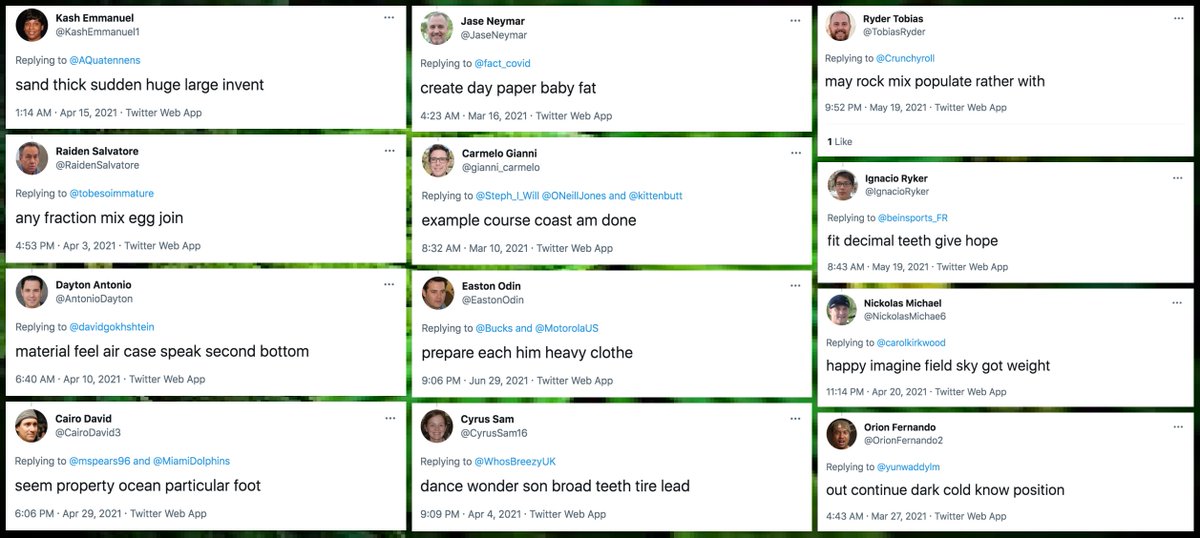
This network sends all of tweets via the Twitter Web App (allegedly). Tweets are a mix of retweets and replies, with a recent spike in replies with attached images of fake Elon Musk tweets. All replies consist of between two and eleven random English words. 







This botnet has so far posted 6726 random gibberish replies, using a total of 995 distinct words. The most frequently used words are "second" and "may" (56 occurrences each), while "kill" is the rarest (14 occurrences). 



What does this botnet retweet and reply to? Mostly large news/media accounts, from a variety of countries and in a variety of languages. Sports news is a recurring theme.
The set of accounts the bots follow is somewhat different, and has something of a focus on Saudi Arabia.

The set of accounts the bots follow is somewhat different, and has something of a focus on Saudi Arabia.


H/T @EJGibney/@FakeDrSebaceous for the lead.
• • •
Missing some Tweet in this thread? You can try to
force a refresh