[thread] Did you know that ssh tries to authenticate with stored keys BEFORE the key specified with -i in the command line ? I just noticed this, the hard way 😐.
Let's imagine you have more than 5 keys loaded in your ssh agent. When authenticating to a remote server, you get:
Let's imagine you have more than 5 keys loaded in your ssh agent. When authenticating to a remote server, you get:
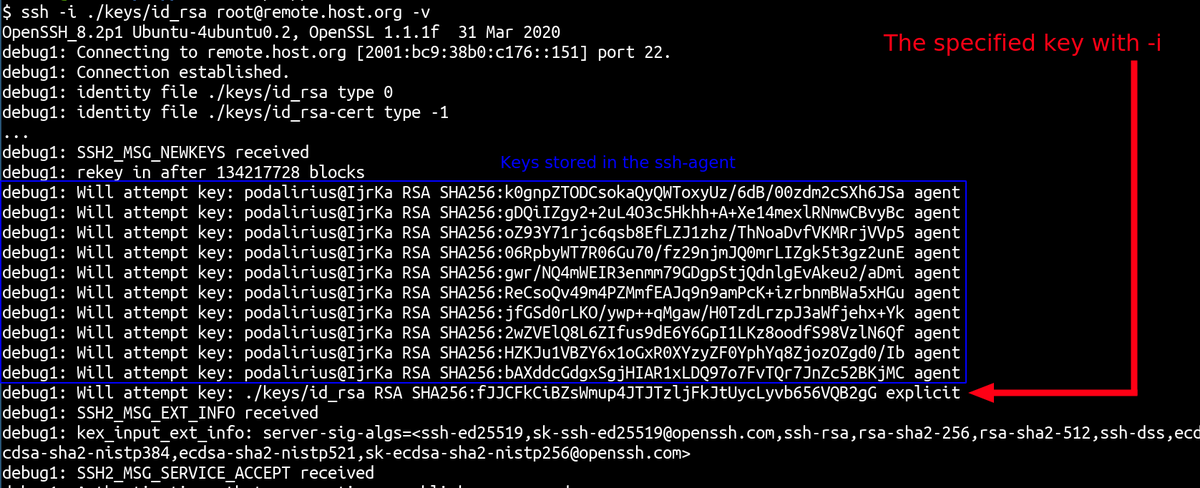
After this message, ssh tries to authenticate with the keys in the order listed above. Why is that a problem ?
Because most servers have a default configuration with MaxAuthTries set to 6. After 6 tries, you will get a "Too many authentication failures" error.
Because most servers have a default configuration with MaxAuthTries set to 6. After 6 tries, you will get a "Too many authentication failures" error.

So, ssh tries to authenticate with the keys in the order listed above, but gets disconnected after 6 tries. This means that if your agent has more than 6 stored keys, the key specified with -i is never used. This means you can't login to a remote server and you might not know why 

If you really want to use only your key without these default behaviors, you need to specify an option. (weird right?)
➡️ -o IdentitiesOnly=true
➡️ -o IdentitiesOnly=true

ssh -i ./keys/id_rsa root@remote.host.org -v -o IdentitiesOnly=true
And now it works as expected. This option can also avoid generating 5 failed logins in the server logs each time you login.
And now it works as expected. This option can also avoid generating 5 failed logins in the server logs each time you login.

It seems very strange and counterintuitive that SSH tries to authenticate with stored keys first when the user explicitly gave SSH a key to login with -i.
Let's just say that this default behavior wasted a lot of my time this weekend.
Let's just say that this default behavior wasted a lot of my time this weekend.

• • •
Missing some Tweet in this thread? You can try to
force a refresh