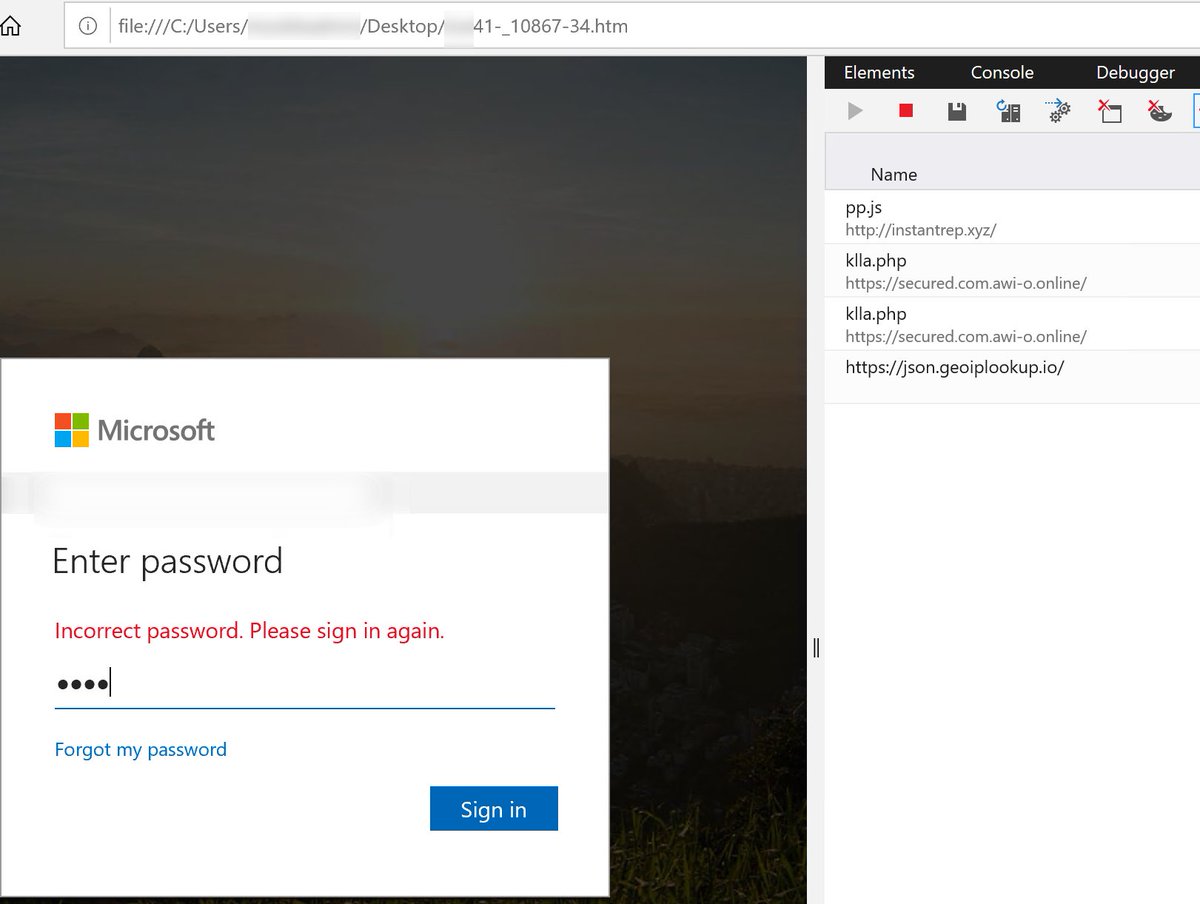
(1/x) M365 changes to be aware of
1) End-users can purchase PowerBI on their on personal credit cards to bypass IT
2) End-users can purchase Windows 365 Cloud PC VMs on their own personal credit cards to bypass IT
3) End-users can create security groups (even if you disabled it)
1) End-users can purchase PowerBI on their on personal credit cards to bypass IT
2) End-users can purchase Windows 365 Cloud PC VMs on their own personal credit cards to bypass IT
3) End-users can create security groups (even if you disabled it)
4) End-users were automatically enrolled into Bing Search Rewards which indexes corporate data into Bing Search
5) Bing Search now collects data in Microsoft Word for the "Reuse Files" feature
6) Teams Recordings now expire after 60 days
5) Bing Search now collects data in Microsoft Word for the "Reuse Files" feature
6) Teams Recordings now expire after 60 days
7) The only way to prevent account lockouts from brute force is to create an Authentication policy (globally in web interface) or for selected users with PowerShell new-AuthenticationPolicy
8) End to End encryption for Teams Calling is off by default
8) End to End encryption for Teams Calling is off by default
9) AAD Default access token lifetime is no longer static 60 minutes, and is now 60 to 90 minutes effective 5/31/2021
10) Windows 10 version 1809 stopped receiving security updates on 5/11/2021
10) Windows 10 version 1809 stopped receiving security updates on 5/11/2021
11) QR-code sign-in rolled out on by default, to disable:
set-organizationConfig -MobileAppEducationEnabled $false
12) Guest access in Teams is now on by default as of 2/8/2021
13) Autoforwarded emails are now disabled by default
set-organizationConfig -MobileAppEducationEnabled $false
12) Guest access in Teams is now on by default as of 2/8/2021
13) Autoforwarded emails are now disabled by default
14) Any new conditional access policy created after August 2020 includes legacy auth by default (previously you had to explicitly target legacy auth)
15) Legacy auth protocols are now being disabled randomly unless they are being actively used techcommunity.microsoft.com/t5/exchange-te…
15) Legacy auth protocols are now being disabled randomly unless they are being actively used techcommunity.microsoft.com/t5/exchange-te…
16) If you are using the custom notification feature in Intune, all users must remove and re-add the Intune Company portal app portal.microsoft.com/Adminportal/Ho…
17) M365 dropped support for IE11 on 8/17/2021
18) On 11/1/2021 M365 will drop support for older Outlook clients
17) M365 dropped support for IE11 on 8/17/2021
18) On 11/1/2021 M365 will drop support for older Outlook clients

19) Microsoft TODO enabled external sharing ON by default as of 9/25/2020
20) Windows 10 version 2004 will stop receiving security updates on December 14th 2021 docs.microsoft.com/en-us/lifecycl…
20) Windows 10 version 2004 will stop receiving security updates on December 14th 2021 docs.microsoft.com/en-us/lifecycl…
21) AIP Scanner can now find rogue file shares - including shares that are open to Everyone/Authenticated Users/Domain Users techcommunity.microsoft.com/t5/security-co…
22) Defender for Endpoint can be used to find rogue endpoints on your network zdnet.com/article/micros…
• • •
Missing some Tweet in this thread? You can try to
force a refresh