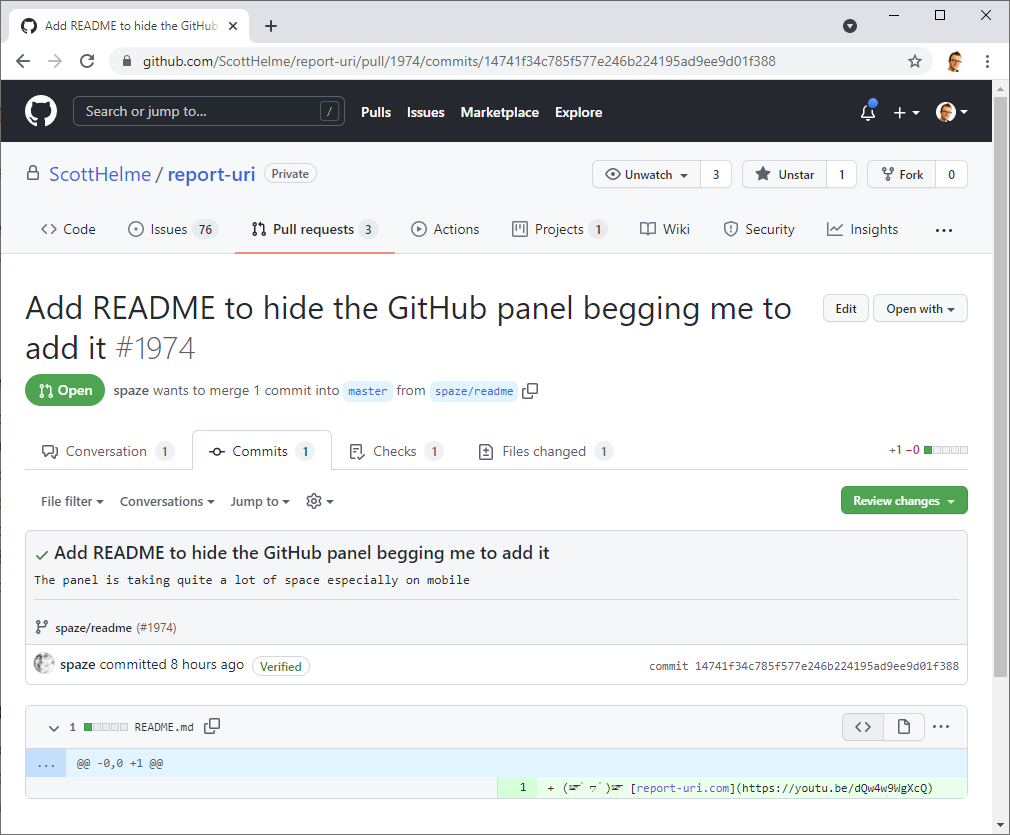
🚨🚨🚨 5 minutes until the Let's Encrypt R3 intermediate expires 🚨🚨🚨
29 September 2021 19:21:40 UTC
29 September 2021 19:21:40 UTC
TANGO DOWN 😅
Are we still here?
I just refreshed the page on my Chrome/Windows 10 Pro install and it automatically built a new certificate chain around the expired intermediate! It's awesome when it works 😎 

The problem is clients that don't have this option available are now possible seeing certificate errors on connections. Let's see if any reports surface...
If something didn't already go kablam, the DST Root CA X3 expires in a little over 18 hours, then you're free and clear!
Sep 30 14:01:15 2021 UTC
Sep 30 14:01:15 2021 UTC
I'm getting reports of issues on devices where we didn't expect any problems... Please report any issues you're seeing on this thread 👍
A fix for Android versions >=7.1.1 if you're seeing errors for the expired R3 intermediate certificate is to kill your running apps and reboot the device.
I now have multiple reports that Bluecoat and Palo Alto proxies encountering the expired R3 intermediate will fail and refuse to connect. Even if you have a modern client behind one of these proxies that could otherwise work around the issue, those sites will be unreachable.
Unconfirmed: Cisco Umbrella Secure Gateway Web Proxy is currently reporting service issues that started ~the same time as the intermediate expiry. Looking for confirmation the two events are related: status.umbrella.com/#/detail/582
There are also many reports of iOS and macOS versions newer than expected seeing issues on sites serving the expired R3 intermediate. I've seen errors on iOS 11, 13 and 14 along with several macOS version only a few minor releases behind current. No fix on the client side yet.
🚨🚨🚨 14 hours until the IdenTrust DST Root CA X3 expires! 🚨🚨🚨
Sep 30 14:01:15 2021 UTC
Sep 30 14:01:15 2021 UTC
Issues likely being caused by bad certificate chains are starting to surface, Catchpoint have a incident open: status.catchpoint.com/incidents/f5yl…
The @guardianiosapp (Guardian Firewall) is currently experiencing an outage:
https://twitter.com/guardianiosapp/status/1443354919122051072
Although, the DST Root CA X3 hasn't expired yet. Presumably this is being caused by using the older R3 intermediate?
https://twitter.com/guardianiosapp/status/1443356011557908482
Also confirmed issues for @mondaydotcom serving the expired R3 in their chain:
https://twitter.com/mondaydotcom/status/1443367994499993601
Hints at impact in other applications:
https://twitter.com/cerb_ai/status/1443361390824071171
Issues in OPNsense require a manual patch and renew: github.com/opnsense/plugi…
I've created a test site to help identify issues with clients. If you can connect to expired-r3-test.scotthelme.co.uk then your client can handle being served the expired R3 Intermediate in the server chain! 

As you can see, my Chrome on Windows 10 is able to build an alternate trust path through the valid R3 Intermediate to the ISRG Root X1: 

Using openssl s_client or similar you can see that the sever is ending the expired R3 Intermediate in the chain: 

Of course, @ssllabs is also detecting that my chain is invalid and showing the alternate, valid chain that can be built: ssllabs.com/ssltest/analyz… 

Is this thing on?
Anyone seeing issues with Google Up Time Check?
I've now had several reports of GCP monitoring reporting down across the board.
OVH also having issues: travaux.ovh.net/?do=details&id…
I've seen a few providers pointing to problems with Auth0 services too, still looking for more solid confirmation.
Shopify have now joined that chorus with an incident: shopifystatus.com/incidents
Also Xero, not yet confirmed as related, but the timing is right: status.xero.com
And yes, I'm also nervously watching my own status page 😅 status.scotthelme.co.uk
Problems with apt would be not good, can anyone else confirm?
https://twitter.com/maxnystrom/status/1443598456820355073
It seems that Fortinet are also having issues with Fortigate (the Next Generation Firewall) old.reddit.com/r/fortinet/com…
Many reports of issues connecting to Heroku API endpoints, but status pages doesn't seem to indicate any but metrics is broken right now: status.heroku.com
InstaPage also has an active incident where the timeline fits for it to be certificate related: status.instapage.com
Get serious when it hits the crypto(currency)! Possible related:
https://twitter.com/Ledger_Support/status/1443590881957789696
Can @Netlify confirm if this is related to the root expiration? netlifystatus.com/incidents/l6rk…
Seems to be the same issue that @Cloudflare pages are having? cloudflarestatus.com
It seems to be: answers.netlify.com/t/ways-to-work…
I didn’t flag this earlier, but this is a good result:
https://twitter.com/statuscaketeam/status/1443618660824887296
MailGun too: status.mailgun.com/incidents/brl5…
Bad day for email too, not just the Web.
https://twitter.com/sparkpost/status/1443630706060636160
If I see one more support article that contains some variation of "disable certificate warnings" I'm going to cry... 😥
Seems like a small issue at Facebook too:
https://twitter.com/spazef0rze/status/1443656911950385155
The Ghost of Christmas Past: kb.fortinet.com/kb/documentLin…
To clarify, I understand people needing to do this now to make stuff work, it's how many people will forget to change the setting back that worries me.
OpenBSD 6.8 and 6.9 have dropped patches to “Compensate for the expiry of the DST Root X3 certificate”.
openbsd.org/errata68.html
openbsd.org/errata69.html
h/t @juhasaarinen
openbsd.org/errata68.html
openbsd.org/errata69.html
h/t @juhasaarinen
The Slack outage was unrelated to this event in the end:
https://twitter.com/eastdakota/status/1443675709260582913
Slack update: status.slack.com/2021-09/06c1e1…
OPNsense have release a hotfix to patch their issue:
https://twitter.com/opnsense/status/1443575966635216905
Sophos SG UTM impacted: support.sophos.com/support/s/arti…
That's a pretty big error message from cPanel! support.cpanel.net/hc/en-us/artic… 

Another big one on AWS too: status.aws.amazon.com 

They got DigitalOcean 😥 status.digitalocean.com/incidents/rbdc… 

PostMan app had issues also: github.com/postmanlabs/po…
Voluminous devices also need an update “due to expired certificate”: community.volumio.org/t/volumio-chan…
• • •
Missing some Tweet in this thread? You can try to
force a refresh