
What is Cyber Security?
Cybersecurity is a way of protecting the network, computers, and other electronic gadgets from cybercriminals. The Malicious attackers might delete, modify or leak confidential information posing a huge threat to a business or an individual.
Cybersecurity is a way of protecting the network, computers, and other electronic gadgets from cybercriminals. The Malicious attackers might delete, modify or leak confidential information posing a huge threat to a business or an individual.

What is Cyber Crime?
Here are some examples of Cyber Crime:
1. Identity Theft
2. Online Predators
3. BEC ("Business Email Compromise")
4. Ransomware
4. Stealing of sensitive intellectual property
Here are some examples of Cyber Crime:
1. Identity Theft
2. Online Predators
3. BEC ("Business Email Compromise")
4. Ransomware
4. Stealing of sensitive intellectual property
Who are Cyber Criminals?
1. State-sponsored groups targeting organizations in other countries
2. Hacking Groups out to target companies to make them pay ransom
3. Kids in their rooms doing illegal hacking
1. State-sponsored groups targeting organizations in other countries
2. Hacking Groups out to target companies to make them pay ransom
3. Kids in their rooms doing illegal hacking

Cyber Security Branches -
1. Network security
Network security refers to a set of rules and configurations to protect network traffic and data. They prevent data theft by monitoring network connections.
1. Network security
Network security refers to a set of rules and configurations to protect network traffic and data. They prevent data theft by monitoring network connections.

2. System security
Safeguard d system & OS from malicious intrusion, modification, & Virus.
3. Application security
Protects apps from being hijacked.
4. Information security
Secures sensitive info from unauthorized access & prevents misuse, disclosure, or destruction of data.
Safeguard d system & OS from malicious intrusion, modification, & Virus.
3. Application security
Protects apps from being hijacked.
4. Information security
Secures sensitive info from unauthorized access & prevents misuse, disclosure, or destruction of data.
5. Web security
Protects a web application from security breaches from unauthorized personnel.
6. Mobile security
Protection of all gadgets associated with wireless computing like smartphones tablets and laptops.
Protects a web application from security breaches from unauthorized personnel.
6. Mobile security
Protection of all gadgets associated with wireless computing like smartphones tablets and laptops.
Cyber Criminals and their types -
1. Script kiddies
These are thrill-seekers and enthusiasts who want to be a hacker but lack technical expertise.
2. Spammers
These criminals spam your inbox with bulk messages. They try to steal your data and perform fraudulent activities.
1. Script kiddies
These are thrill-seekers and enthusiasts who want to be a hacker but lack technical expertise.
2. Spammers
These criminals spam your inbox with bulk messages. They try to steal your data and perform fraudulent activities.
3. Hacker groups
These are Informal communities that work anonymously with the same motive of breaking the security of a target.
4. Phishers
Phishers try to gain personal details like usernames and passwords. They present themselves as trustworthy entities to obtain this info.
These are Informal communities that work anonymously with the same motive of breaking the security of a target.
4. Phishers
Phishers try to gain personal details like usernames and passwords. They present themselves as trustworthy entities to obtain this info.
5. Insiders
Disloyal individuals within an org who r willfully stealing, damaging or exposing internal data of an org.
6. Advanced Persistent Threat (APT) Agents
They perfectly execute organized crimes against a target by a longterm presence on a nw to mine highly sensitive data
Disloyal individuals within an org who r willfully stealing, damaging or exposing internal data of an org.
6. Advanced Persistent Threat (APT) Agents
They perfectly execute organized crimes against a target by a longterm presence on a nw to mine highly sensitive data
7. Identity Thieves
They steal the identity of another person without their knowledge to commit fraud like making financial transactions.
They steal the identity of another person without their knowledge to commit fraud like making financial transactions.
Types of Cyber Threats/Attacks -
Based On the attacker’s motivation cyber attacks can be classified into two types.
A. Passive attack
The attacker’s motivation is to gain confidential information without affecting the system resources or threatening the victim.
Based On the attacker’s motivation cyber attacks can be classified into two types.
A. Passive attack
The attacker’s motivation is to gain confidential information without affecting the system resources or threatening the victim.
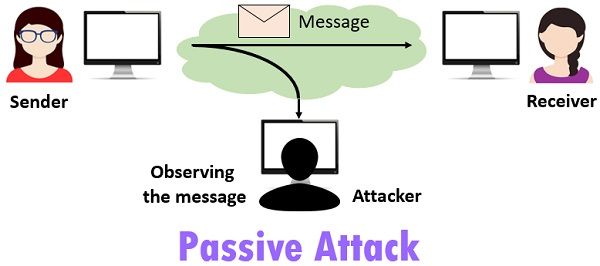
B. Active attack
The attacker modifies the information and causes a threat to system resources causing damage to the integrity of the system.
The attacker modifies the information and causes a threat to system resources causing damage to the integrity of the system.

Types/methods employed by cybercriminals to breach security -
1. Malware
Malware is malicious software made by the hacker to damage a genuine user’s system. It usually spreads when you install rogue software or click an infected link or email.
1. Malware
Malware is malicious software made by the hacker to damage a genuine user’s system. It usually spreads when you install rogue software or click an infected link or email.
The different types of malware are:
A. Virus
A virus is a self-replicating computer program that spreads through the computer system infecting other clean files.
A. Virus
A virus is a self-replicating computer program that spreads through the computer system infecting other clean files.

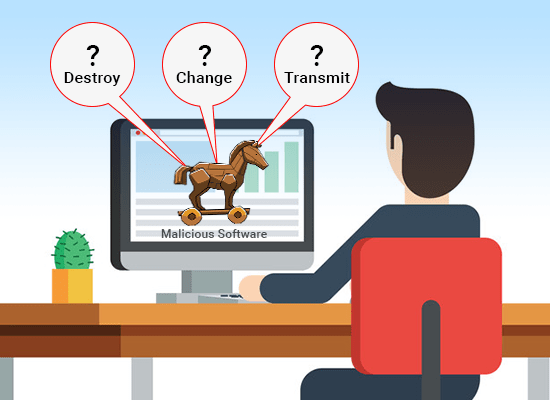
B. Trojan horse
A Trojan horse, or Trojan, is a type of malicious code or software that looks legitimate but can take control of your computer. A Trojan is designed to damage, disrupt, steal, or in general inflict some other harmful action on your data or network.
A Trojan horse, or Trojan, is a type of malicious code or software that looks legitimate but can take control of your computer. A Trojan is designed to damage, disrupt, steal, or in general inflict some other harmful action on your data or network.
C. Spyware
A code that secretly captures user activities like internet usage data and makes use of the tracked information for fraud purposes.
A code that secretly captures user activities like internet usage data and makes use of the tracked information for fraud purposes.

D. Ransomware
Ransomware is malware that employs encryption to hold a victim's information at ransom.
A user or organization's critical data is encrypted so that they cannot access files, databases, or applications.
A ransom is then demanded to provide access.
Ransomware is malware that employs encryption to hold a victim's information at ransom.
A user or organization's critical data is encrypted so that they cannot access files, databases, or applications.
A ransom is then demanded to provide access.

E. Botnets
Botnets are devices connected over the internet. It is used for Launching Distributed Denial of Service (DDoS) on the user’s website or to steal data.
Botnets are devices connected over the internet. It is used for Launching Distributed Denial of Service (DDoS) on the user’s website or to steal data.

2. SQL injection
SQL injection runs a Structured Query Language code in the database of a website to access sensitive data like private customer details.
SQL injection runs a Structured Query Language code in the database of a website to access sensitive data like private customer details.

3. Phishing
Method where cybercriminals steal user data like login credentials and credit card numbers by duping like a trusted party. It is simply launched via email or a text message.
Method where cybercriminals steal user data like login credentials and credit card numbers by duping like a trusted party. It is simply launched via email or a text message.

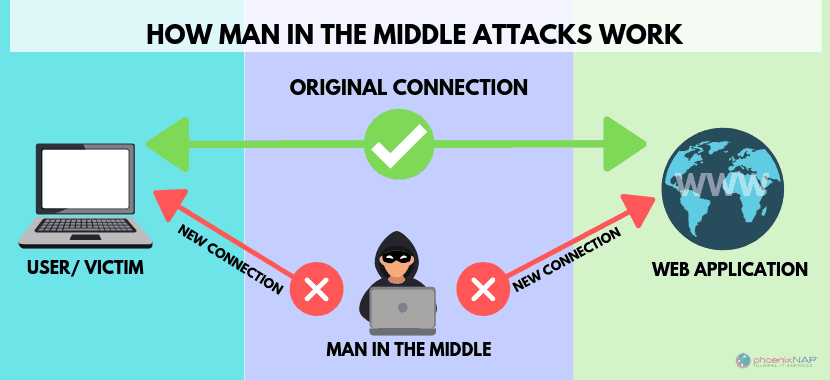
4. Man-in-the-middle attack
MitM attack is of eavesdropping nature, where the unauthorized third party secretly intercepts the communication between two parties.
MitM attack is of eavesdropping nature, where the unauthorized third party secretly intercepts the communication between two parties.
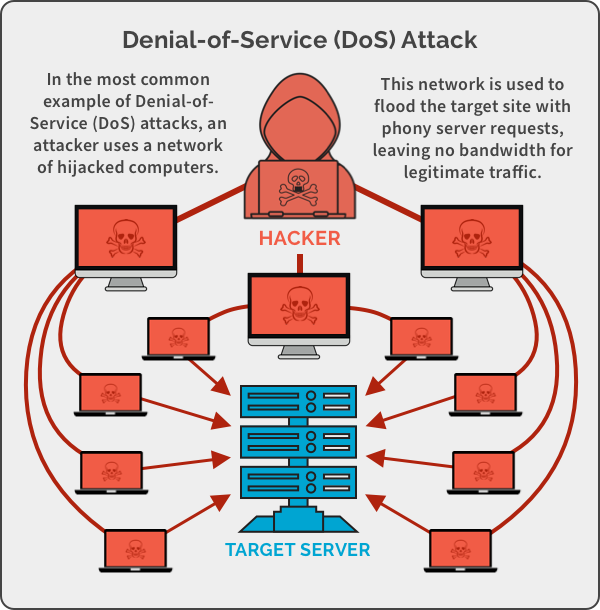
5. Denial-of-service attack
The attacker cuts down all messages directed to a specific destination. This is done by disrupting a whole network or overloading it with messages to degrade performance.
The attacker cuts down all messages directed to a specific destination. This is done by disrupting a whole network or overloading it with messages to degrade performance.
6. Scareware
D attacker scares d user & tricks him into purchasing an anti-virus. Once installed by d user, it starts throwing msgs on d screen that ur system is under fire & throws d victim into a panic. Den it redirects a victim to a bogus website to shop for an anti-virus.
D attacker scares d user & tricks him into purchasing an anti-virus. Once installed by d user, it starts throwing msgs on d screen that ur system is under fire & throws d victim into a panic. Den it redirects a victim to a bogus website to shop for an anti-virus.

7. Keylogger
Keylogger is a code that downloads the log of all the keystrokes of the system. It is sent to the hacker’s computer, to access sensitive information like user ids and passwords.
Keylogger is a code that downloads the log of all the keystrokes of the system. It is sent to the hacker’s computer, to access sensitive information like user ids and passwords.

What is RISK?
Risk refers to the calculated assessment of potential threats to an organization’s security and vulnerabilities within its network and information systems.
Risk refers to the calculated assessment of potential threats to an organization’s security and vulnerabilities within its network and information systems.
What is THREAT ?
Threat is what an organization is defending itself against.
Few examples - malware that plants dangerous executables in your software and ransomware that locks up your systems to specially targeted hacker attacks.
Threat is what an organization is defending itself against.
Few examples - malware that plants dangerous executables in your software and ransomware that locks up your systems to specially targeted hacker attacks.
What is Vulnerability?
Vulnerabilities are the gaps or weaknesses that undermine an organization’s IT security efforts, e.g. a firewall flaw that lets hackers into a network.
Vulnerabilities are the gaps or weaknesses that undermine an organization’s IT security efforts, e.g. a firewall flaw that lets hackers into a network.
How to safeguard against all this ?
Cyber Security Methods -
1. Data Loss Prevention (DLP)
DLP software spots data breaches by ensuring end users do not send sensitive information outside the corporate network.
Cyber Security Methods -
1. Data Loss Prevention (DLP)
DLP software spots data breaches by ensuring end users do not send sensitive information outside the corporate network.
2. Cloud Security
Protection of data stored in cloud platforms.
3. Intrusion Detection Systems (IDS) or Intrusion Prevention Systems (IPS)
Monitors the network to identify potentially malicious activity and reports to the management.
Protection of data stored in cloud platforms.
3. Intrusion Detection Systems (IDS) or Intrusion Prevention Systems (IPS)
Monitors the network to identify potentially malicious activity and reports to the management.
4. Identity and Access Management (IAM)
Set of policies for managing the access privileges for the individual users in the network.
5. Encryption
Process of encoding raw data into unreadable form to prevent theft in transit.
Set of policies for managing the access privileges for the individual users in the network.
5. Encryption
Process of encoding raw data into unreadable form to prevent theft in transit.
6. Antivirus/anti-malware
Software that finds and removes viruses and malware from the system.
7. Proxies
It is a hub between the user and the internet. It allows the user to conceal the network id by hiding the user’s IP address.
Software that finds and removes viruses and malware from the system.
7. Proxies
It is a hub between the user and the internet. It allows the user to conceal the network id by hiding the user’s IP address.
8. Firewall
Uses a set of predefined rules to set barriers against untrusted networks.
9. Cyber Liability Insurance
Covers financial losses and operational liability from data theft or breaching.
Uses a set of predefined rules to set barriers against untrusted networks.
9. Cyber Liability Insurance
Covers financial losses and operational liability from data theft or breaching.
• • •
Missing some Tweet in this thread? You can try to
force a refresh











