We have been made aware of "scary" emails sent in the last few hours that purport to come from the FBI/DHS. While the emails are indeed being sent from infrastructure that is owned by the FBI/DHS (the LEEP portal), our research shows that these emails *are* fake.
These fake warning emails are apparently being sent to addresses scraped from ARIN database. They are causing a lot of disruption because the headers are real, they really are coming from FBI infrastructure. They have no name or contact information in the .sig. Please beware!
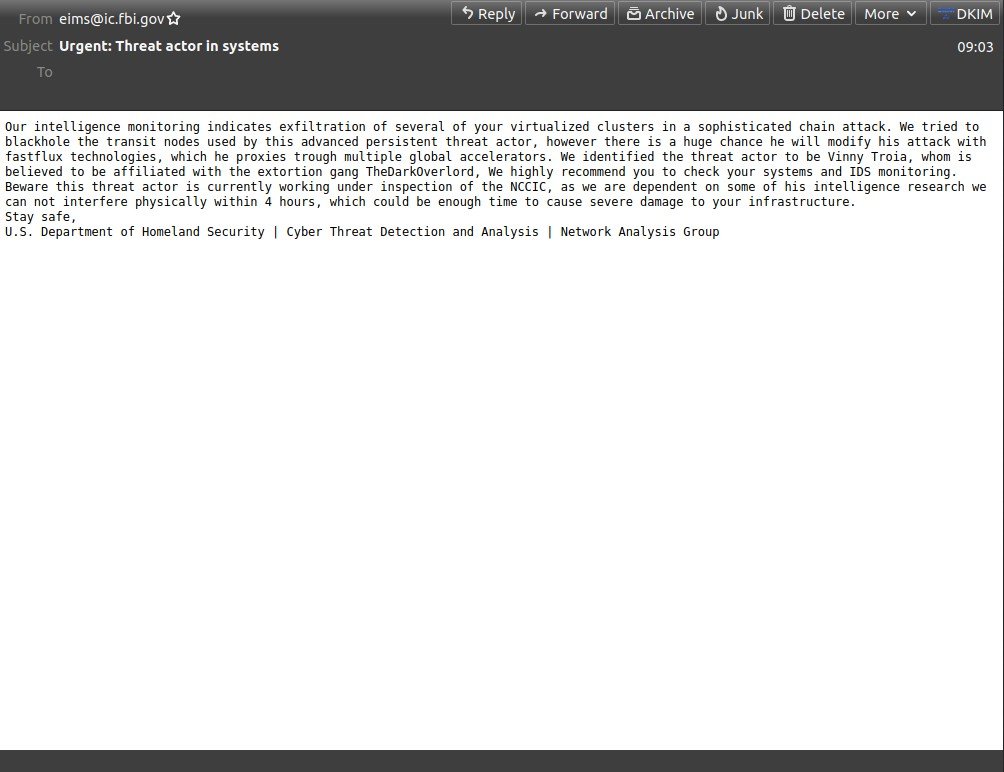
These emails look like this:
Sending IP: 153.31.119.142 (mx-east-ic.fbi.gov)
From: eims@ic.fbi.gov
Subject: Urgent: Threat actor in systems
Sending IP: 153.31.119.142 (mx-east-ic.fbi.gov)
From: eims@ic.fbi.gov
Subject: Urgent: Threat actor in systems
• • •
Missing some Tweet in this thread? You can try to
force a refresh






