1/7: @NSWElectoralCom statement on today's Internet voting meltdown.
elections.nsw.gov.au/About-us/Media…
It says disenfranchised voters won't be fined, but doesn't say whether the election results are expected to stand.
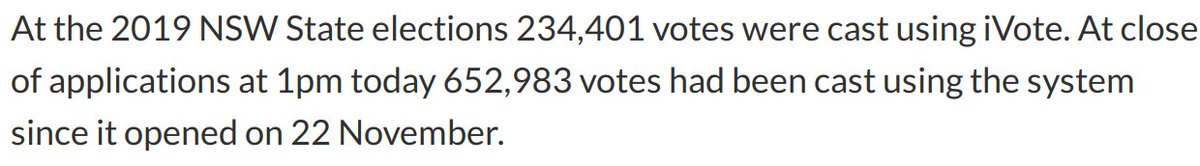
More than 650,000 votes were received, which may be a world record.
elections.nsw.gov.au/About-us/Media…
It says disenfranchised voters won't be fined, but doesn't say whether the election results are expected to stand.
More than 650,000 votes were received, which may be a world record.
2/7: Apologises to voters not able to vote as a result of the outage; no apology to candidates who may or may not have failed to get elected as a consequence of their supporters being excluded.
3/7: It's unclear how many people were excluded from voting - when we know how many paper ballots were received we'll be able to make an estimate, assuming (without much evidence) that the 650k came from eligible NSW electors.
4/7: It's also not clear how many tried to verify, or how many verifications succeeded. In 2015, we know that more than 10% of verification attempts failed to retrieve any vote. These will be important questions.
5/7: NSW local govt election details vary, but many use STV to allow a few thousand electors to choose a council of several people. Margins can be very small.
arxiv.org/abs/1611.02015
arxiv.org/abs/1611.02015
6/7: And of course the really important point is: where is the evidence of eligible voter intent in any of those 650,000 votes, when we know the system that received them had serious IT problems? We may simply not have enough information to determine who deserved to be elected.
7/7: Every serious investigation of iVote found serious problems:
- 2015 arxiv.org/abs/1504.05646
- 2017 arxiv.org/abs/1708.00991
- 2019 dial.uclouvain.be/pr/boreal/obje…
including the one commissioned by NSWEC this year:
elections.nsw.gov.au/NSWEC/media/NS…
What happened today should surprise nobody.
- 2015 arxiv.org/abs/1504.05646
- 2017 arxiv.org/abs/1708.00991
- 2019 dial.uclouvain.be/pr/boreal/obje…
including the one commissioned by NSWEC this year:
elections.nsw.gov.au/NSWEC/media/NS…
What happened today should surprise nobody.
• • •
Missing some Tweet in this thread? You can try to
force a refresh